Understanding Hash: The Basics
 James Mathenge
James Mathenge
Introduction
This article serves as the introduction to our hashing series. Throughout this series, we'll study the interesting realm of hash functions and their importance in computer science. Hashing is a fundamental concept that plays a vital role in ensuring data integrity, security, and efficient data retrieval.
Hashing is widely used in computer science, cryptography, and data integrity verification. It provides a way to securely store passwords, detect data tampering, and enable efficient data retrieval in large databases.
What exactly is hashing?
Simply said, hashing is the process of converting any input, such as a file, a password, or other data, into a fixed-length string of characters. This transformed output is what is known or referred to as the hash value, hash code, or simply hash.
Technologically, hashing is a mathematical operation where inputs (any kind of data) are taken and complex algorithms are applied to transform the inputs into a fixed-size output, usually represented as a sequence of characters or numbers. The resulting hash value is unique to the input data, such that even a small alteration in the input produces a different hash value.
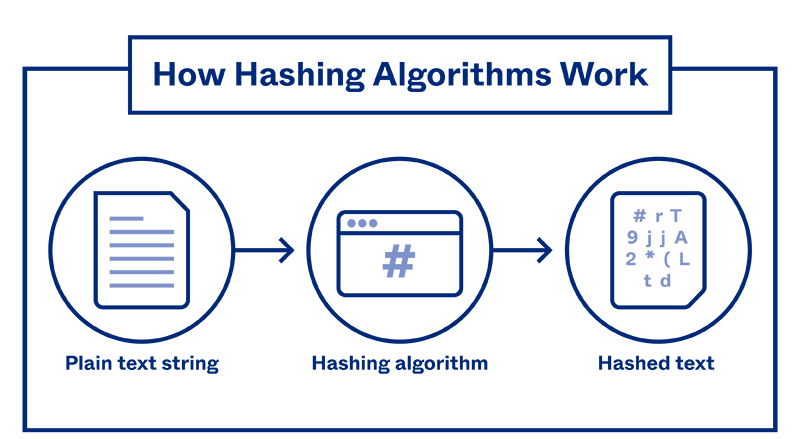
The fundamental building block of hashing is a hash function. Hash functions are specifically designed algorithms that take an input, such as a file, a password, or any other data, and process it to generate a unique fixed-size hash value.
Now you might be wondering, why we need hashing in the first place.
Hashing offers several benefits:
Data Integrity Verification: By creating a distinct hash value for each input, hashing makes it easier to check the accuracy of data. In case there is suspicion of data tampering or alteration, one can compare the hash values before and after the transmission or storage of data. The deterministic nature of hash functions ensures that even a small alteration in the input produces a completely different hash value, thus providing a reliable means of ensuring data integrity.
Password Security: Hashing is essential for safe password archiving. Systems save password hash values rather than the actual passwords themselves. When a user enters their password in a computer system, the
user's password is hashed and compared against the hash value that has been previously stored. This strategy improves security since the actual passwords are difficult to retrieve, even if the password database is stolen.
Efficient Data Retrieval: Data structures like hash tables and hash maps employ hashing to enable and facilitate effective data retrieval. Data may be stored and accessed using hash functions based on a determined hash value that acts as an index. This drastically improves search and retrieval times, making hash-based data structures ideal for applications that require fast data access.
Data Privacy: Hashing provides a way to anonymize sensitive data. Instead of storing personally identifiable information (PII) directly, such as names or identification numbers, a hash value can be generated and stored. This permits data processing and analysis without the disclosure of private information ensuring the preservation of privacy and the adherence to data protection laws.
Digital Signatures and Authentication: Digital signatures and authentication systems both depend on hashing as a key building block. By generating hash values of digital documents or messages and encrypting them with a private key, a unique signature is created. Verifying the signature using the corresponding public key and comparing the generated hash value ensures the authenticity and integrity of the digital content.
In the upcoming blog posts, we'll explore the properties of hash functions, delve into real-world examples, and uncover the many applications of hashing.
Continue Reading About Hashing
Subscribe to my newsletter
Read articles from James Mathenge directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

James Mathenge
James Mathenge
A highly skilled professional dev who possesses a unique combination of expertise in both Finance and Software Development