Understanding SQL Injection for Software QA Engineers! 🕵️♀️💻
 Mejbaur Bahar Fagun
Mejbaur Bahar Fagun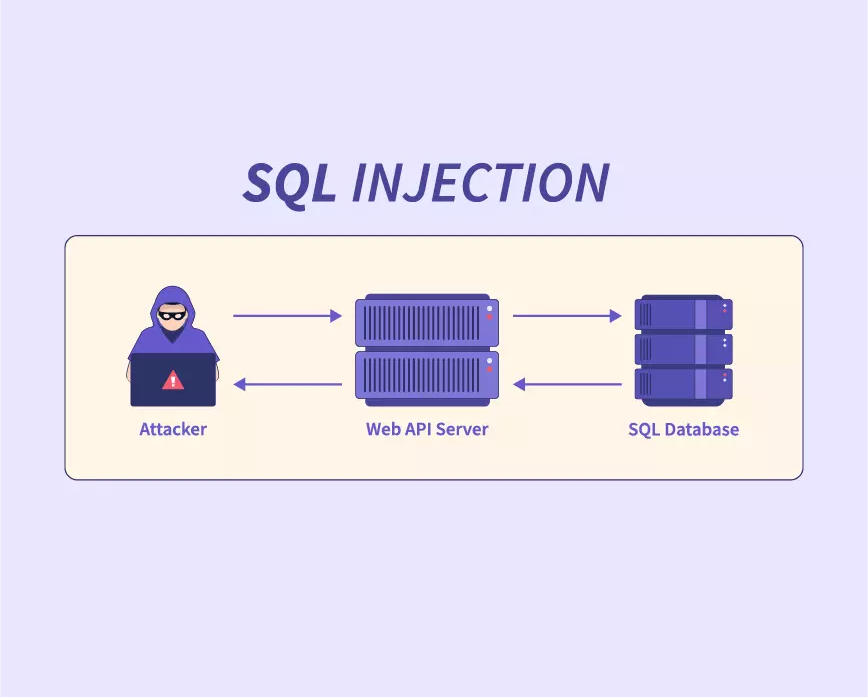
Introduction:
As a Software Quality Assurance (QA) Engineer, your role is crucial in ensuring the security and reliability of software applications. One area that demands your attention is SQL injection. 🚨 In this article, we will dive into the world of SQL injection, explore its impact on software systems, and discuss how you can effectively test for and prevent this vulnerability. Let's get started! 🚀
- What is SQL Injection? 🤔
SQL injection is a common web application vulnerability that occurs when an attacker inserts malicious SQL code into a query via user input fields. The application, without proper validation or sanitization of the input, inadvertently executes the injected SQL code. This can lead to unauthorized access, data breaches, and even the complete compromise of the application and the underlying database. 😱
2. Impact and Consequences of SQL Injection:
The repercussions of a successful SQL injection attack can be severe. Here are some potential consequences:
Unauthorized access to sensitive data, including personally identifiable information (PII) or financial records.
Data manipulation or deletion, causes integrity issues within the database.
Denial of Service (DoS) attacks, where the database becomes overwhelmed with malicious queries, rendering the application unusable.
They are exposing system vulnerabilities, enabling further exploitation by attackers.
Understanding these potential risks emphasizes the need for robust testing and preventive measures. 🔒
3. Testing for SQL Injection Vulnerabilities: 🕵️ ♂️
As a QA Engineer, it's crucial to identify and mitigate SQL injection vulnerabilities during the software testing phase. Here are some effective testing techniques to consider:
Input Validation: Ensure that user inputs are validated and sanitized. Reject any input that contains potentially harmful characters or SQL code.
Boundary Testing: Test for potential SQL injection scenarios by providing inputs that exceed expected lengths or include special characters.
Error Handling: Test how the application handles erroneous or malicious inputs. The application should gracefully handle such inputs without disclosing sensitive information or displaying error messages that may aid attackers.
Database Security Configuration: Verify that the database server is correctly configured with limited permissions for the application. Avoid using default or generic user credentials.
4. Preventive Measures and Best Practices: ✅
To prevent SQL injection vulnerabilities in software applications, follow these best practices:
Parameterized Queries: Utilize prepared statements or parameterized queries, which separate SQL code from user inputs. This prevents SQL injection by treating inputs as data rather than executable code.
Least Privilege Principle: Implement the principle of least privilege by granting minimal permissions to the application's database user. Restrict access to only the necessary tables, procedures, and functions.
Regular Security Audits: Perform regular security audits to identify and address any potential vulnerabilities promptly.
Security Education and Awareness: Train developers, QA engineers, and other stakeholders about SQL injection risks and best practices to ensure everyone understands their role in maintaining secure software systems.
Here are some free and open-source tools with their corresponding URLs that can be used for testing SQL injection vulnerabilities:
SQLMap is a powerful and widely-used tool for automatic SQL injection and database takeover. It supports various databases and provides extensive features for detecting and exploiting SQL injection vulnerabilities.
- OWASP ZAP: https://www.zaproxy.org/
OWASP ZAP (Zed Attack Proxy) is a popular open-source web application security scanner. It includes a variety of security testing capabilities, including the ability to identify and test for SQL injection vulnerabilities.
Wfuzz is a flexible and feature-rich web application fuzzer. It can be used to test for SQL injection by sending customized payloads and analyzing the responses from the server.
4. Skipfish: https://tools.kali.org/web-applications/skipfish
Skipfish is an active web application security reconnaissance tool. While its primary focus is on discovering common vulnerabilities, it can help identify potential SQL injection vulnerabilities in web applications.
5. Nmap: https://nmap.org/
Nmap is a versatile network scanning tool that can be used for security assessments. It has various scripts and modules that can help identify SQL injection vulnerabilities in databases and web applications.
Remember to always use these tools responsibly and with proper authorization. Additionally, keep in mind that manual testing and verification are essential to supplement the automated scanning results for a comprehensive assessment.
- Tools Made by me: SQL Injection Scanner
Conclusion:
As a Software QA Engineer, understanding SQL injection vulnerabilities is essential to protect software applications from potential attacks. By implementing thorough testing techniques and following best practices, you can significantly reduce the risk of SQL injection and enhance the overall security posture of the software you test. Stay vigilant, stay updated, and always prioritize security! 🔒🔒
🔀 𝐂𝐨𝐧𝐧𝐞𝐜𝐭 𝐖𝐢𝐭𝐡 𝐌𝐞
𝐅𝐚𝐜𝐞𝐛𝐨𝐨𝐤: https://lnkd.in/dQhnGZTy
𝐅𝐚𝐜𝐞𝐛𝐨𝐨𝐤 𝐏𝐚𝐠𝐞: https://lnkd.in/gaSKMG2y
𝐈𝐧𝐬𝐭𝐚𝐠𝐫𝐚𝐦: https://lnkd.in/gid7Ehku
Hashnode: Mejbaur Bahar Fagun
𝐌𝐞𝐝𝐢𝐮𝐦: https://lnkd.in/gP6V2iQz
𝐆𝐢𝐭𝐡𝐮𝐛: https://github.com/fagunti
𝐘𝐨𝐮𝐓𝐮𝐛𝐞: https://lnkd.in/gg9AY4BE
#sqlinjection #softwareqa #securitytesting #webapplicationsecurity #sqlmap #owaspzap #wfuzz #skipfish #nmap #hashacking #sqlvulnerabilities #cybersecurity #sqlinjection101 #sqlinjectionvulnerabilities #securecoding #datasecurity #sqlinjectionprevention #webappsecurity #opensourcesecuritytools #securitytestingtools #cybersecurityawareness #informationsecurity #protectyourdata #qaengineers #softwaretesting #softwaresecurity #hashacking101 #sqlhacks #staysecure #cyberdefenses #opensecurity #sqlinjectiontesting #websecuritytesting #sqa #qaengineer #qa #qajobs
#qamanual #qaanalyst #qatesting #qaengineers #securitytesting #bugbounty #softwarequalityassurance #mejbaurbaharfagun
Subscribe to my newsletter
Read articles from Mejbaur Bahar Fagun directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Mejbaur Bahar Fagun
Mejbaur Bahar Fagun
With a strong background in both Software QA Engineering and Certified Ethical Hacking, I bring a unique and comprehensive skill set to my work. My expertise in manual and automated testing, along with my ability to design effective test frameworks from scratch, makes me a valuable asset to any software development team. My familiarity with both the Waterfall and Scrum methodologies of the SDLC ensure that I can operate seamlessly within any development process. I have a proven track record of effectively verifying software products, conducting thorough online form factor validations, and verifying complex algorithm designs through the use of Matlab scripts. Let me bring my technical expertise and commitment to ethical practices to your next project.