Connect to EC2 Instances using EC2 Instance Connect Endpoint without public IP
 Vipin Yadav
Vipin Yadav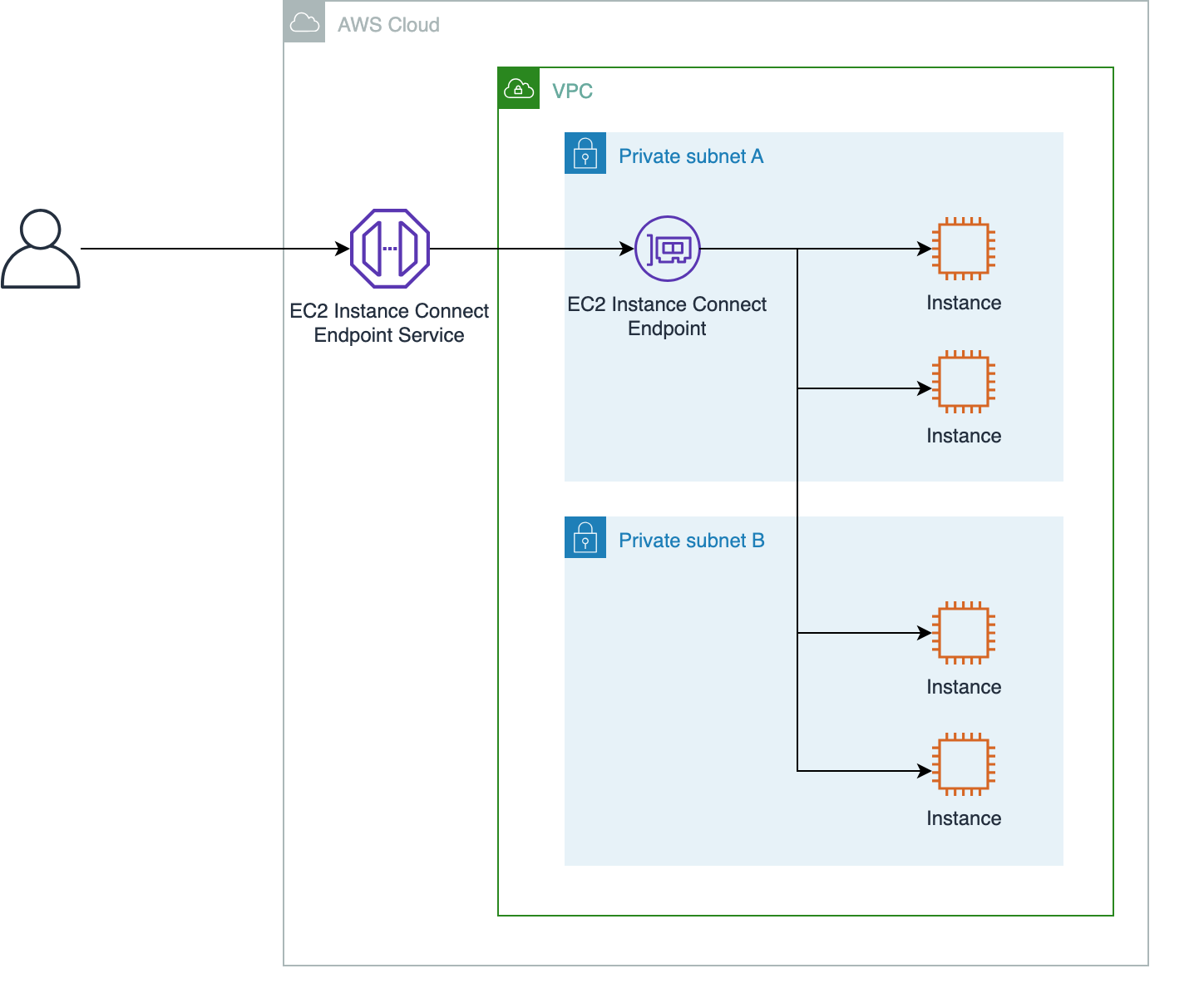
EC2 Instance Connect Endpoint allows you to connect to an instance via SSH or RDP without requiring the instance to have a public IPv4 address. Once you create an EC2 Instance Connect Endpoint in a subnet, you can use the endpoint to connect to any instance in any subnet in your VPC provided your VPC is configured to allow subnets to communicate. In this article, we are going to connect to an EC2 Instance using EC2 Instance Connect Endpoint.
Architecture
The high-level architecture provided by AWS is as follows.
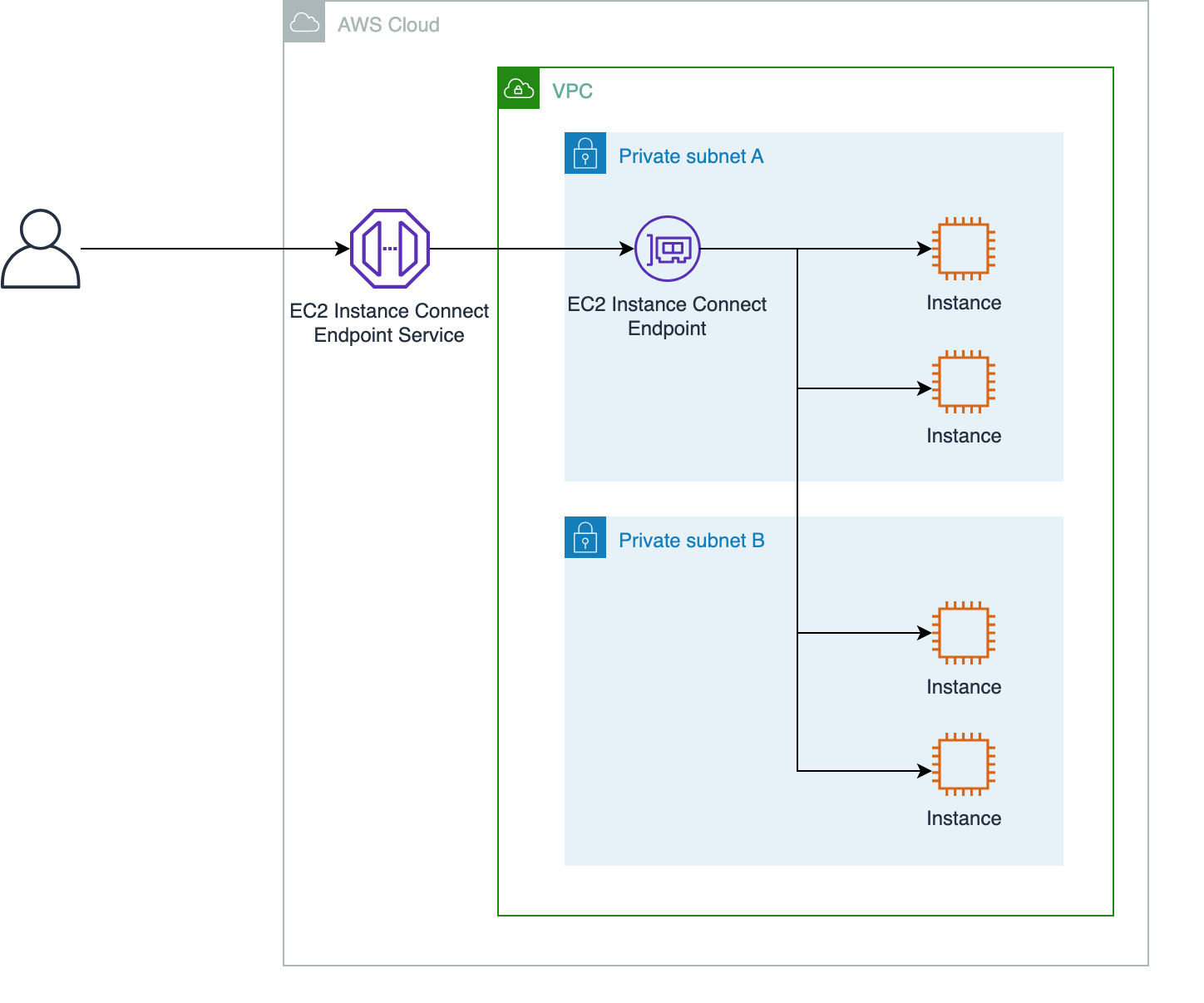
Credit — Amazon web service
Prerequisites
Before creating make sure you have an Amazon web service account and have the IAM permissions to create VPC, launch the EC2 machine and create an EC2 Instance Connect Endpoint.
Create a VPC
The first step is creating a VPC. Log into your AWS account, navigate to the VPC section and create a VPC with default settings.


Create an EC2 Instance Connect Endpoint
Once VPC is provisioned successfully, in the VPC pane choose Endpoint and Create an Endpoint with the following,


Optional) For Name tag, enter a name for the endpoint.
For Service category, choose EC2 Instance Connect Endpoint.
For VPC, select the new VPC.
Expand Additional settings, and for Preserve Client IP do one of the following:
Select the check box so that your client’s IP address is used as the source when you connect to an instance.
Note: When Preserve Client IP is turned on, your instance’s security group must allow traffic from your client IP address. For more information, see Instance security group rule.
Clear the check box so that the elastic network interface IP address is used as the source when you connect to an instance. When Preserve Client IP is turned off, you can connect to any IP address that’s routable from the VPC.
5. (Optional) For Security groups, select the security group to associate with the endpoint. If you don’t select a security group, the default security group for your VPC will be associated with the endpoint. For more information, see Security groups for EC2 Instance Connect Endpoint.
6. For Subnet, select the subnet in which to create the endpoint.
7. (Optional) To add a tag, choose Add new tag and enter the tag key and the tag value.
8. Choose Create endpoint.
Launch an EC2 Machine
While EC2 Instance Connect Endpoint is provisioning, head over to the EC2 section and launch an EC2 instance of type Amazon Linux, make sure you select the newly created VPC in the network setting section and Auto-assign public is disabled.
- In the security group attached to this instance make sure to add the rule to allow SSH traffic from the security group selected while provisioning the Endpoint.
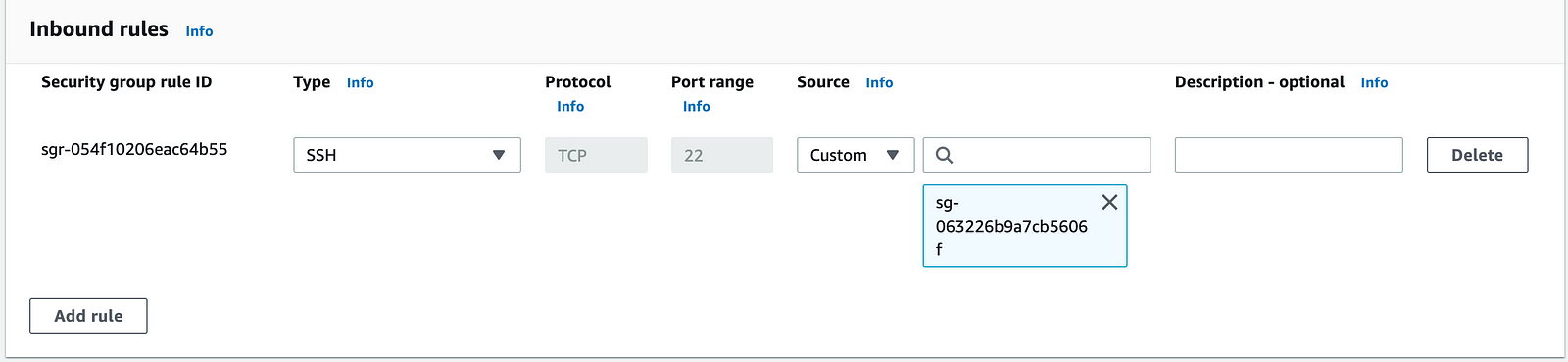
Connect to EC2 Instance using the Amazon EC2 console
Once the EC2 Instance Connect Endpoint is provisioned and is in an available state and the Instance is in the Running state, select the instance, choose Connect, and then do the following:

Choose the EC2 Instance Connect tab.
For Connection type, choose Connect using EC2 Instance Connect Endpoint.
For User name, verify the user name.
For Max tunnel duration (seconds), enter the maximum allowed duration for the SSH connection.
The duration must comply with the
maxTunnelDurationcondition specified in the IAM policy. If you don't have access to the IAM policy, ask your administrator to verify it. IfmaxTunnelDurationis not specified in the IAM policy, enter the default, which is 3600 seconds (1 hour).For EC2 Instance Connect Endpoint, choose the EC2 Instance Connect Endpoint in the instance’s VPC.
Choose Connect to open a terminal window.
A new terminal window will be created and you can connect to you EC2 machine.

That’s all about connecting to EC2 Instance using EC2 Instance connect Endpoint. Thanks for reading.
Subscribe to my newsletter
Read articles from Vipin Yadav directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Vipin Yadav
Vipin Yadav
I am DevOps/Full-Stack developer from India. I am currently learning and working on Kubernetes and FullStack Development.