Level 1:- Enumerating Flaws.cloud Domain (AWS)
 Goodycyb
GoodycybTable of contents
Welcome to Level 1. For this level, we are challenged to find the first sub-domain associated with flaws.cloud
NB: You can click Hint 1 to view more details on how to solve the challenge. I recommend you follow the steps below before viewing the HINT page
Let's see ways in which we can solve this challenge🎌.
Before we start, let's create the Domain Report Table which we will update as we progress in this challenge🚩.
Flaws Cloud Domain Report
Domain Name: flaws.cloud
IP address: ? (IP address change due to several reasons)
Number of subdomains found: ?
NS(Name Server): ?
Hosting company: ?
There are different ways to discover sub-domains. First, let's start by identifying the IP address of the domain flaws.cloud.
Finding the IP Address of the Domain (flaws.cloud)
On Windows or Linux OS (Parrot), navigate to Command Prompt(CMD)/ Terminal and ping flaws.cloud
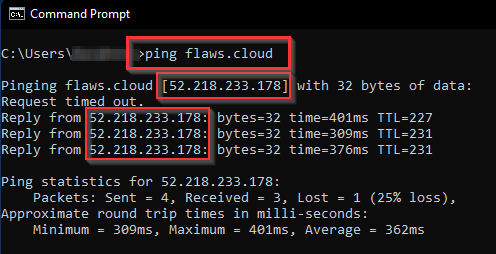
The ping reply on CMD, we got the IP for flaws.cloud domain as [52.218.233.178]
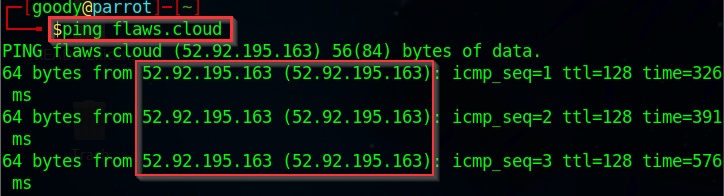
The ping reply on the Linux terminal, we got the IP for flaws.cloud domain as [52.92.195.163]
You will notice that the IP address on Windows (CMD) differs from that on Linux (Parrot OS terminal). . . WHY ?
There are several reasons why the IP address associated with a domain changes. To summarize, IP addresses can change for various reasons, such as load balancing techniques, DNS resolution, dynamic IP allocation, the presence of a CDN (Content Delivery Network), or the implementation of techniques like Anycast. These factors are utilized to improve performance, reliability, and scalability when managing internet traffic.
If you want more explanation ASK CHATGPT “why IP address associated with a domain change when I ping it or click HERE to view the explanation”
Alternatively, we can use the Dig command on Linux terminal to find associated IP addresses with our target domain (flaws.cloud). On any Linux Distro, open your terminal and type the command “dig flaws.cloud” as shown below:
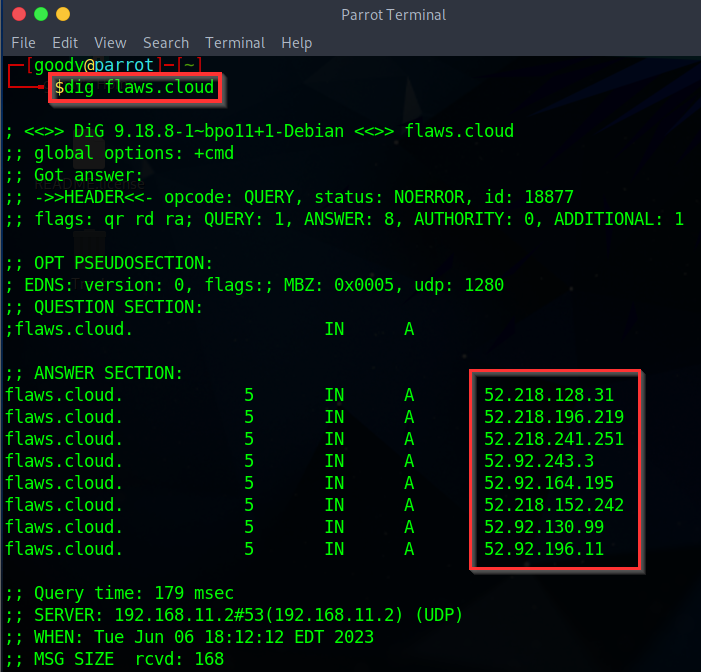
Under the ANSWER SECTION, we get the list of domain “A” records of IPv4 addresses. When you copy any of the IPs and search on Google or any browser, they redirect to the AWS S3 bucket website.
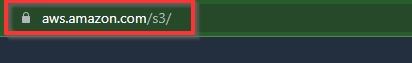
Hence, this shows flaws.cloud is hosted on an S3 bucket.
NOTE: We can use the publicly available domain database websites to get details about the domain flaws.cloud. Websites such as Netcraft and Whois-lookup. These websites won’t exactly give you subdomains associated with flaws.cloud but they will give you more details about the domain, especially Netcraft.
Key details we can get from Netcraft include: (Updated Flaws Cloud Domain Report)
Hosting company: Amazon - US West (Oregon) datacenter
IPv4 address: 52.218.168.90
DNS admin: awsdns-hostmaster@amazon.com
Nameserver: ns-1890.awsdns-44.co.uk
IP delegation
Hosting History Etc. READ MORE: HERE
Now, let's try the Host command on linux terminal. The command Host retrieves various types of information associated with domain names, such as IP addresses or other DNS records. Type “Host 52.218.168.90”.
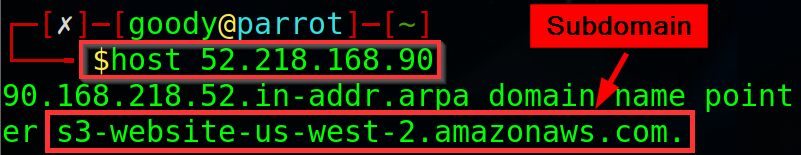
NOTE: if you try using the “Host command” with the IP address gotten from using the DIG and PING commands as illustrated above, you are likely to get error messages because they are dynamic IPs. Thus, we use the IP address gotten from Netcraft because it is a Domain DB and it works.
NB: you are likely to encounter the same error message, but keep trying the IPs out, One of them will surely bring a result.
As shown in the above image, the domain name pointer for the site reveals s3-website-us-west-2.amazonaws.com as a subdomain. Thus, S3 Bucket address translation http://flaws.cloud.s3-website-us-west-2.amazonaws.com/ .
URL break Down
- Domain:
flaws.cloud
This is the primary domain name.
- S3 bucket endpoint:
[s3-website-us-west-2.amazonaws.com](http://s3-website-us-west-2.amazonaws.com)
the subdomain
s3-website-us-west-2.amazonaws.comis used as the endpoint for an Amazon S3 (Simple Storage Service) bucket. Amazon S3 is a cloud storage service provided by Amazon Web Services (AWS), and it allows users to store and retrieve data.
- Region: “us-west-2”
The
us-west-2part of the subdomain indicates the AWS region where the S3 bucket is located. In this case, it refers to the US West (Oregon) region.
Discovering subdomains associated with Flaws.cloud can be achieved through various methods.
METHOD 1
Manual Enumeration: This involves searching for subdomains manually using search engines like Google, Bing, or DuckDuckGo.
Here we are going to use Google Advanced Search Operators called “Google Dorking”.
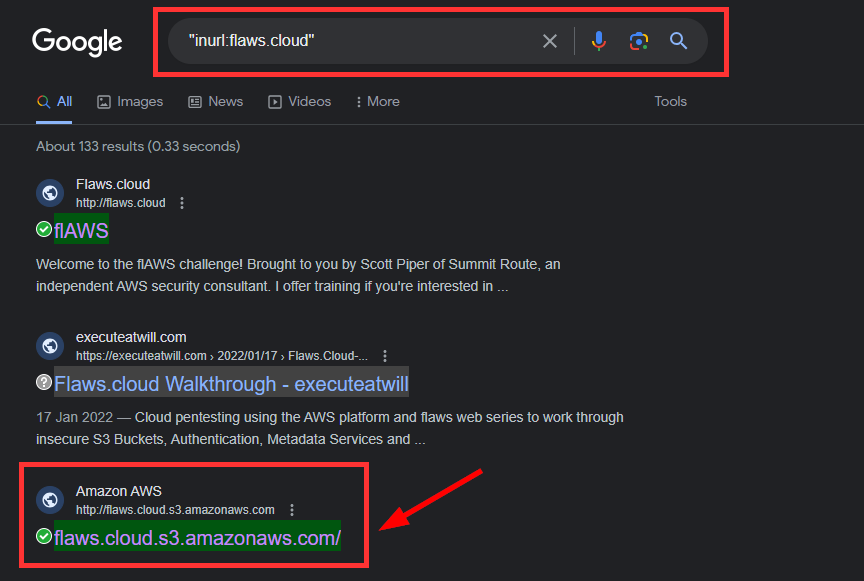
⇒ Navigate to your Google browser and type the following and Search "inurl:flaws.cloud”
The result of the search shows other websites associated with the flaws.cloud domain. When you click on the third link, it will redirect you to the domain http://flaws.cloud.s3.amazonaws.com/ as shown in the image below.
On the redirected page, you will get a list of the sub-domain associated with flaws.cloud.
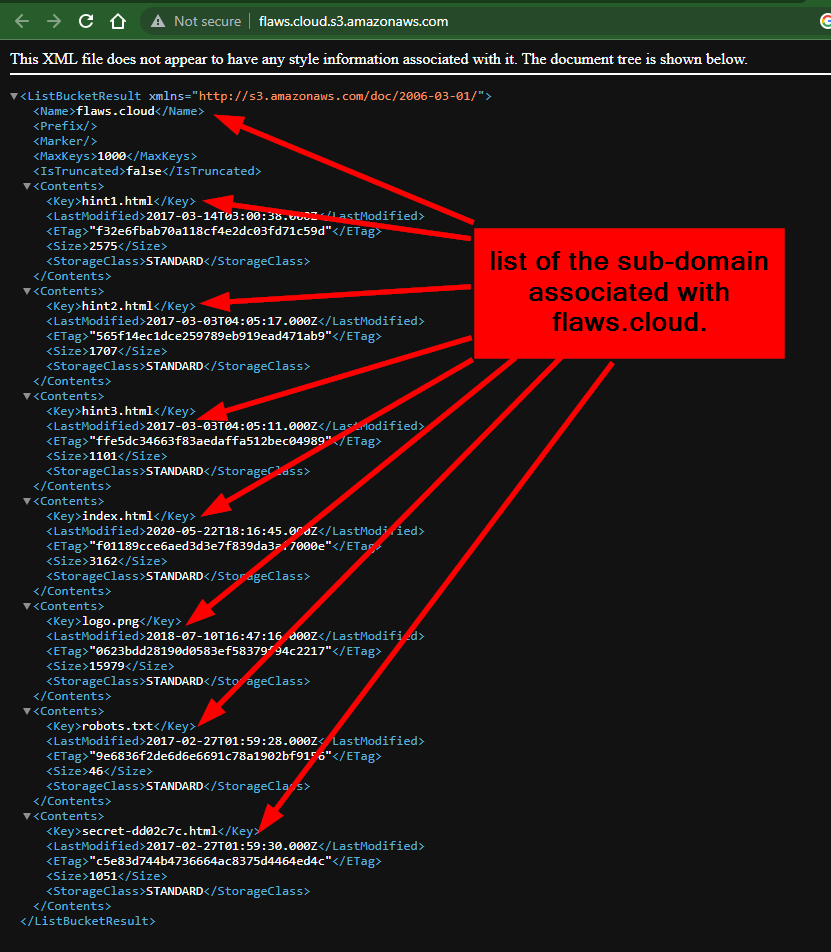
From the list of sub-domains listed, how can we tell they are sub-domains? Type: flaws.cloud/{any of the sub-domain above}
From the perspective of a threat actor, from the listed sub-domains found (last subdomain), one of them looks interesting to view, which is: ****.****/ secret-dd02c7c.html.
We will Preview the web page at the end of the lab, let's see how we can find the subdomain using another method
METHOD 2
Using the AWS CLI. The AWS Command Line Interface (AWS CLI) is a unified tool to manage your AWS services. Now that we know that the domain flaws.cloud is hosted on Amazon S3 bucket, We will use AWS CLI to Access the content in the bucket.
Click Here to download base on your PC Spec. Watch Here to see how to install on windows.
For this lab, we will be installing AWS CLI via the Linux terminal
On any of your Linux Distro Terminal, Type: “
git clonehttps://github.com/aws/aws-cli.git“ and press Enter. Wait for it to install.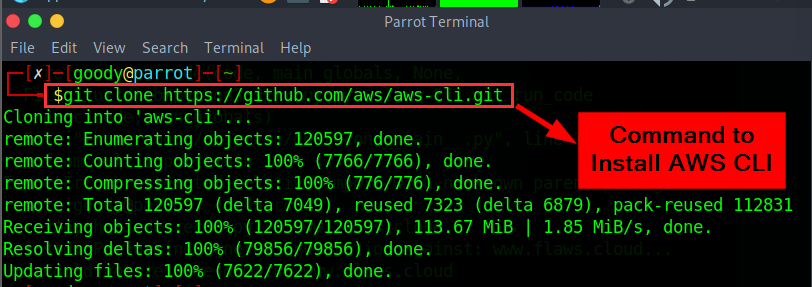
To confirm installation Type on your terminal:
awsand press Enter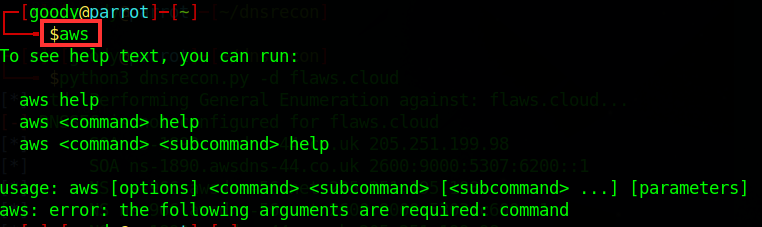
check the version installed Type: “
aws --version” and press Enter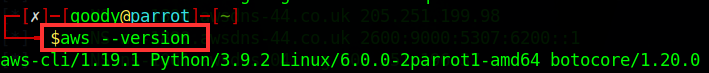
Access S3 Bucket with AWS CLI. Type: “
aws s3 ls s3://[flaws.cloud](http://flaws.cloud)/ --no-sign-request --region us-west-2”. This command will list out the content in the S3 bucket in flaws.cloud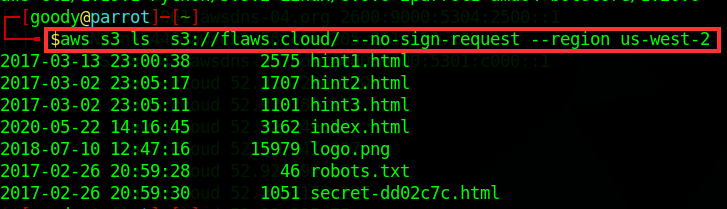
Now to the Fun Part🚩🕵️♂️
Among the listed files in the bucket, the path secret-dd02c7c.html looks interesting. (Similar to what we had at the End of Method 1)
Navigate to secret http://flaws.cloud/secret-dd02c7c.html
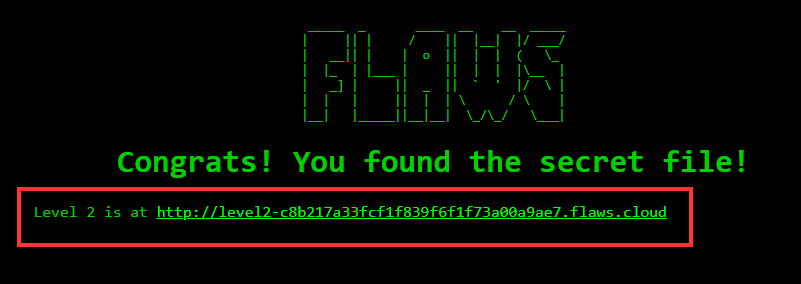
Lesson learned
The lesson learned is that on AWS, you have the ability to configure S3 buckets with various permissions and functionality, including using them to host static files. Unfortunately, many individuals inadvertently expose these buckets with overly permissive permissions. Similar to the importance of not enabling directory listings on web servers, it is crucial to avoid allowing bucket listings as well.
Examples of this problem
Directory listing of S3 bucket of Legal Robot (link) and Shopify (link).
Read and write permissions to S3 bucket for Shopify again (link) and Udemy (link). This challenge did not have read and write permissions, as that would destroy the challenge for other players, but it is a common problem.
Avoiding the mistake
By default, S3 buckets are private and secure when they are created. To allow it to be accessed as a web page, I had to turn on "Static Website Hosting" and changed the bucket policy to allow everyone "s3:GetObject" privileges, which is fine if you plan to publicly host the bucket as a web page. But then to introduce the flaw, the author of the game (Scott Piper @0xdabbad00) changed the permissions to add "Everyone" to have "List" permissions.
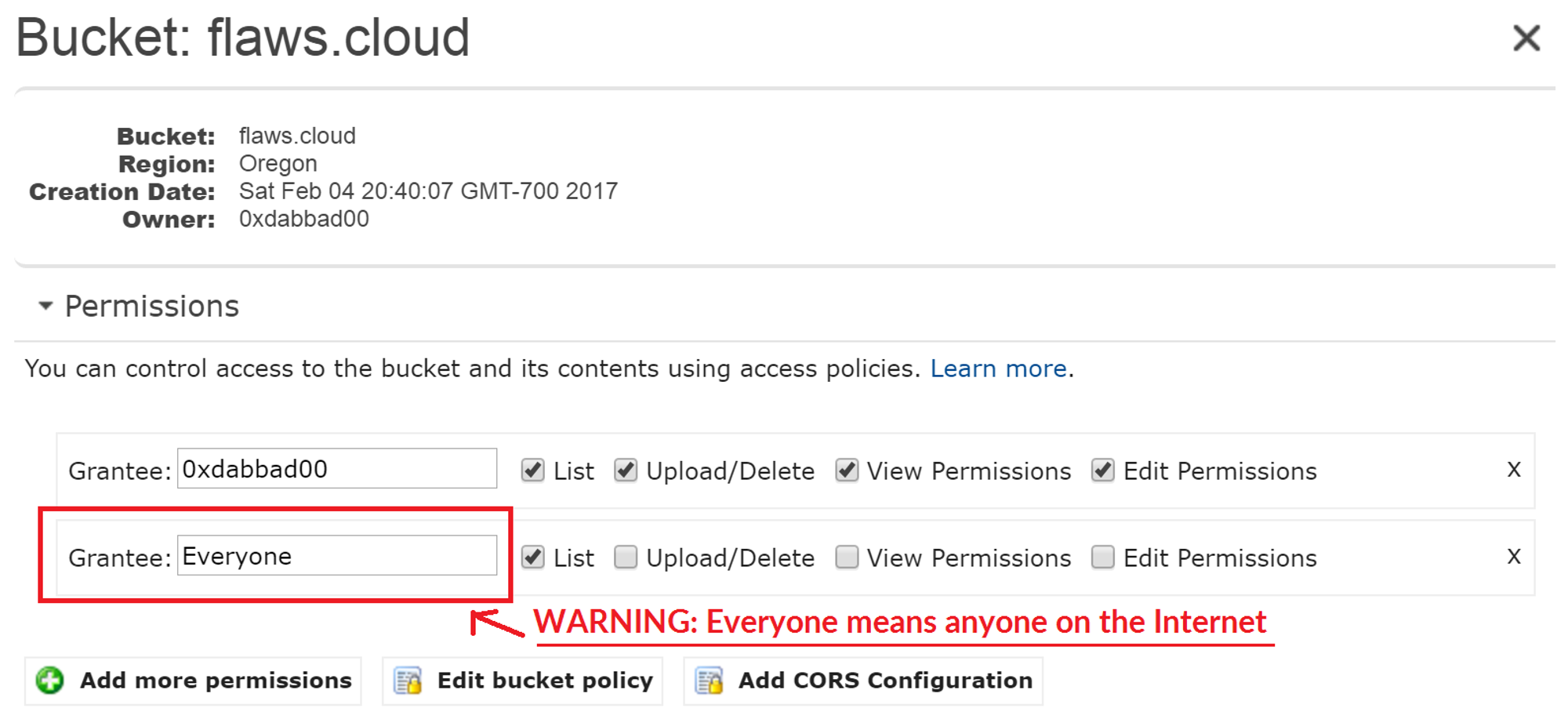
"Everyone" means everyone on the Internet. You can also list the files simply by going to http://flaws.cloud.s3.amazonaws.com/ due to that List permission.
Recall that when we used Google Dorking to find the list of sub-domains, this was because of the permissions configured in the bucket, making the content in it publicly available to anyone on the internet.

Level -2! See you there, 🚀
Subscribe to my newsletter
Read articles from Goodycyb directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Goodycyb
Goodycyb
Hey there! 👋🏾 I'm Goody, a Cloud Threat Researcher by Day 🌞 and a Cloud Security Content Engineer by Night🌜. Join me on my journey as I explore the realm of Threat Detection in Cloud Security.