Level -6: "Auditing misconfigured IAM Account”
 Goodycyb
Goodycyb
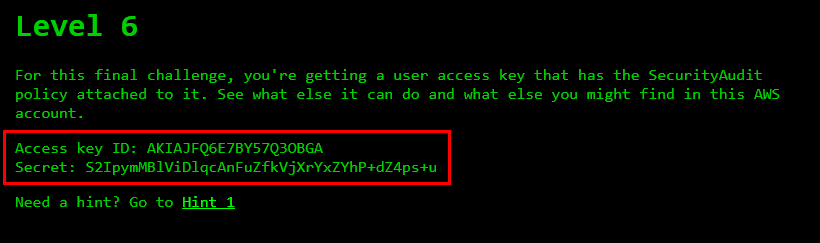
In this final challenge, we are provided with a user access key that has the Security Audit policy attached to it. We are tasked with exploring the capabilities of this access key and uncovering any additional information or resources within the AWS account.
Access key: Access key ID: AKIAJFQ6E7BY57Q3OBGA
Secret key: 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
TASK:
Using these access key credentials, you can authenticate and access various AWS services and resources associated with the account. Take this opportunity to investigate the account thoroughly and discover any other interesting findings.
Task Explained
To accomplish this task, let's begin by adding the access key details to the
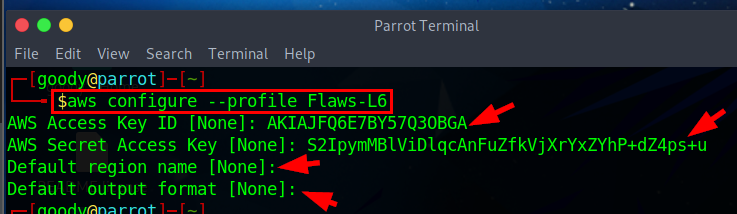
~/.aws/credentialsfile to create an AWS profile.Open your Linux terminal and type the command:
aws configure --profile Flaws-L6then supply the given access key details.NB: For this Lab, the profile name is
- Check if the profile was successfully created using the command
cd /.aws/credentials/
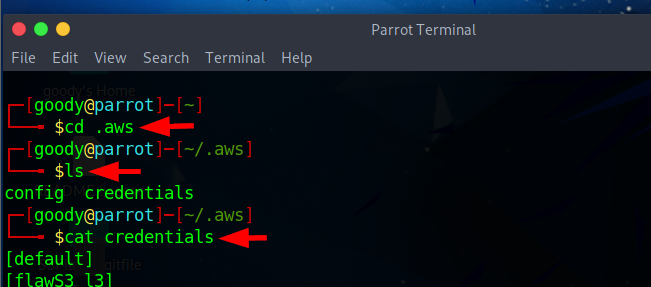
When scrolling down to the end, you will observe that Flaws-L6 appears after the Token we added in Level 5.
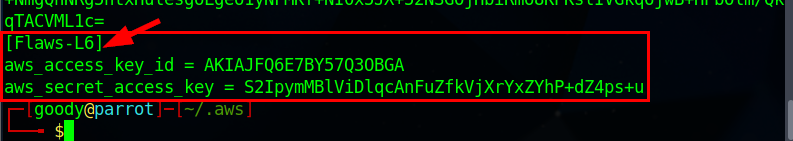
Retrieving information from the user associated with the given Access key
Now, Let's retrieve information about the current user associated with the given Access key by using the command: aws --profile "your-created-name" iam get-user
For this lab, the profile name created is
Flaws-L6(Replace with the profile name you created)
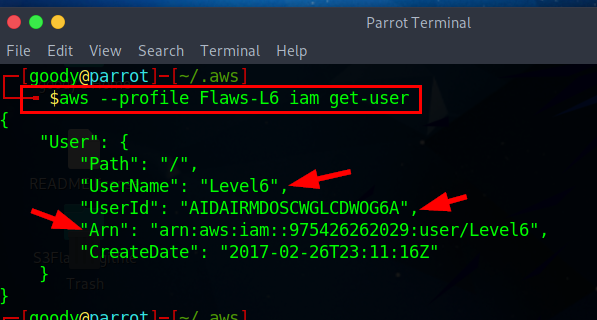
Listing policies attached to the user
Now that we have user details associated with the Access key, let's List policies attached to the user using the command :
aws --profile "your-created-name" iam list-attached-user-policies --user-name Level6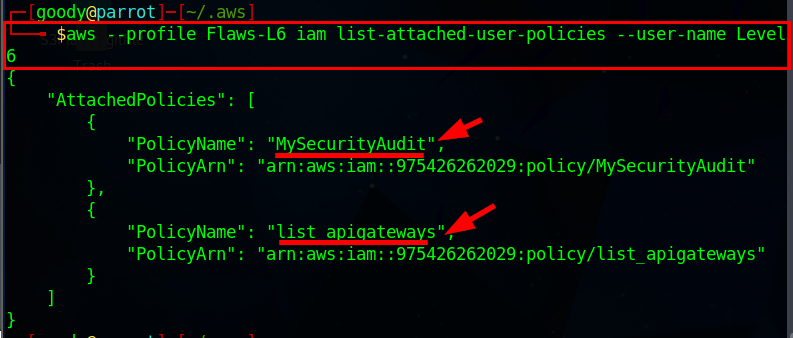
From the Output of the command, it indicates that the user or entity has two policies attached to it. The policies, namely "MySecurityAudit” and "list_apigateways”.
Let’s delve deeper into the policies by examining the details of the "list_apigateways" policy using its ARN. You can use the following command, replacing "your-created-name" with the appropriate profile name:
aws --profile "your-created-name" iam get-policy --policy-arn arn:aws:iam::975426262029:policy/list_apigateways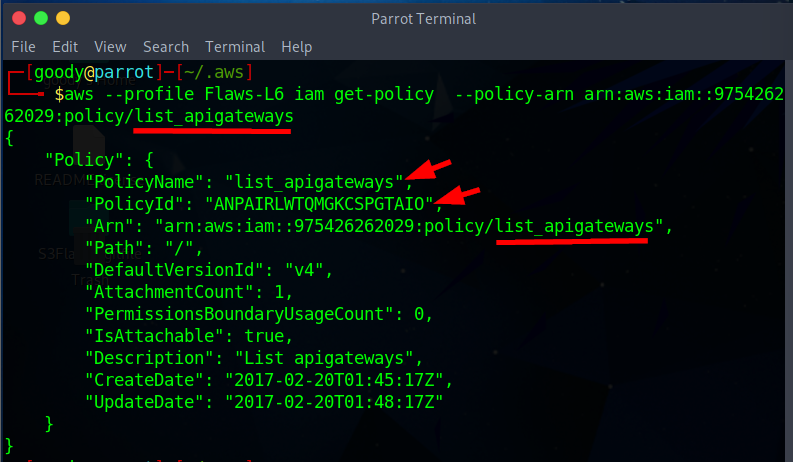
Please note that you can use the same command to view the details of the "MySecurityAudit" policy by modifying the ARN code mentioned above to
**"arn:aws:iam::975426262029:policy/MySecurityAudit.”**Now that we have viewed the details of the policy, let’s retrieve information about the specific version of the IAM policy name
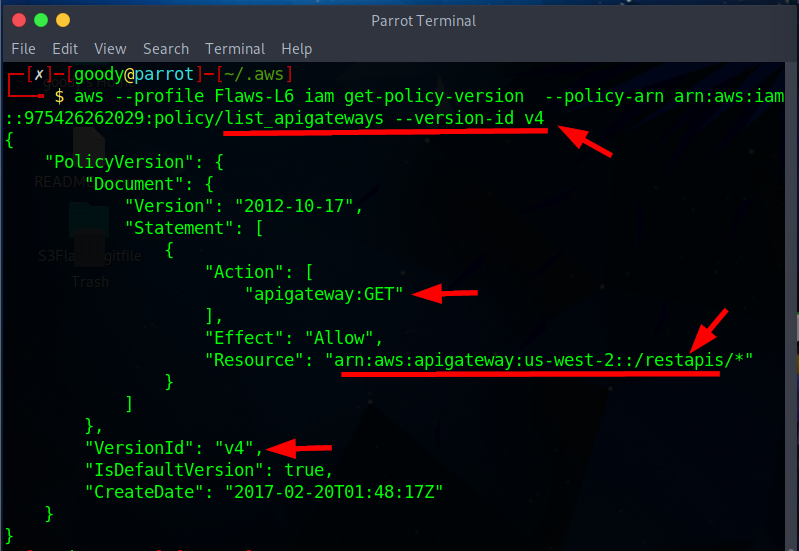
list_apigatewaysUsing the command.aws --profile "your-created-name" iam get-policy-version --policy-arn arn:aws:iam::975426262029:policy/list_apigateways --version-id v4
NOTE: By following the demonstrated approach used for
"list_apigateways"policy, you can obtain the version ID associated with the"MySecurityAudit"policy.
By executing the above command, we obtained information about the requested policy version, including its document, version ID, and other relevant details.
The "list_apigateways" policy is utilizing the "apigateway:GET" action on the "arn:aws:apigateway:us-west-2::/restapis/*" resource.
This indicates that the policy allows the user or entity associated with it to perform the "GET" action on any API Gateway resource under the "arn:aws:apigateway:us-west-2::/restapis/*" ARN.
Since the policy
list_apigatewaysallows user or entity associated with it to perform the "GET" action on any API Gateway resource using“arn:aws:apigateway:us-west-2::/restapis/*", Let’s use GET action to List Lambda Functions. Using the commandaws --region us-west-2 --profile "your-created-name" lambda list-functions
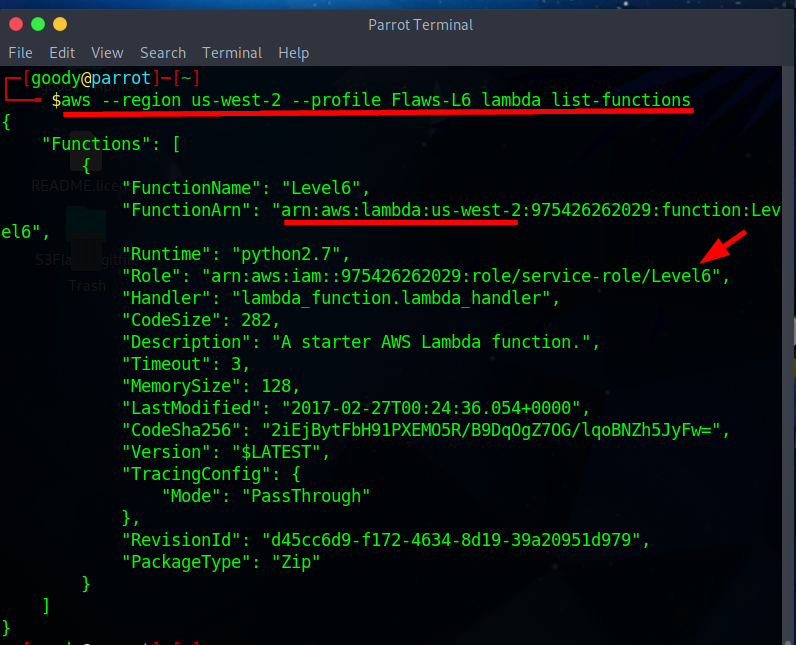
The output of the command provides a detailed overview of the Level-6 Lambda function.
Accessing Lambda Function
- Now, let's get policy details for the Lambda function name “Level 6” using the command
aws --region us-west-2 --profile "your-created-name" lambda get-policy --function-name Level6
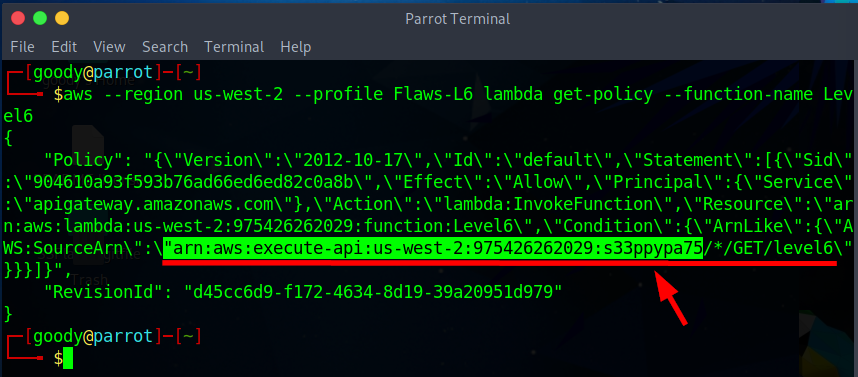
From the get lambda function policy output, you will notice an AWS API Gateway REST API resource in the "us-west-2" region with the ID "s33ppypa75". arn:aws:execute-api:us-west-2:975426262029:s33ppypa75
- Now that we have the API ID, Let’s obtain information about the stages associated with the specified API Gateway REST API. Using the command
aws --profile "your-created-name" --region us-west-2 apigateway get-stages --rest-api-id "s33ppypa75"
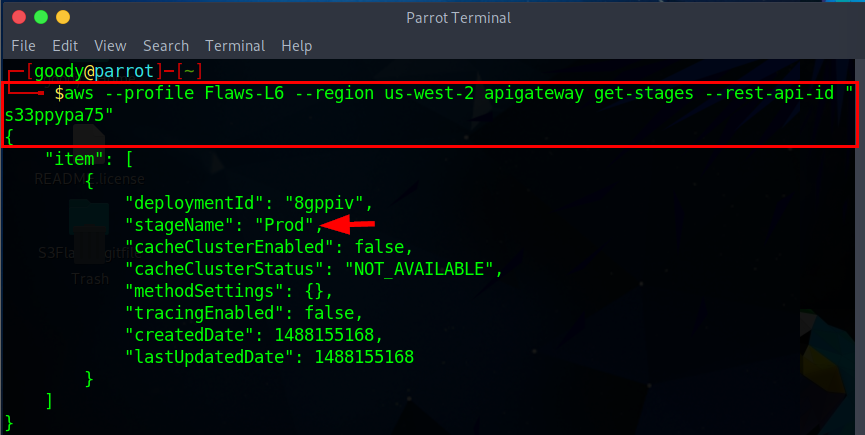
The stage name for the API Gateway REST API is "Prod". This stage consists of Lambda functions associated with the provided REST API ID, stage name, region, and resource.
The resource URL for the "Prod" stage is: https://s33ppypa75.execute-api.us-west-2.amazonaws.com/Prod/level6
By accessing this URL, you can interact with the Lambda functions deployed in the "Prod" stage of the API Gateway REST API, specifically for the "level6" resource.
Lesson learned
It is common to give people and entities read-only permissions such as the SecurityAudit policy. The ability to read your own and others' IAM policies can really help an attacker figure out what exists in your environment and look for weaknesses and mistakes.
Avoiding this mistake
Don't hand out any permissions liberally, even permissions that only let you read meta-data or know what your permissions are.



Watch out for Flaws2.cloud Walkthrough 🚀
Let’s connect on Linkedin || Twitter
Subscribe to my newsletter
Read articles from Goodycyb directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Goodycyb
Goodycyb
Hey there! 👋🏾 I'm Goody, a Cloud Threat Researcher by Day 🌞 and a Cloud Security Content Engineer by Night🌜. Join me on my journey as I explore the realm of Threat Detection in Cloud Security.