COMPUTER NETWORKING, Day - 4
 Vrishni Shree V B
Vrishni Shree V B
INTRODUCTION:
In this comprehensive blog post, we will explore key network devices such as routers, switches, load balancers, and proxy servers. Not only will we uncover their roles and configurations, but we will also dive into their integration within the network infrastructure. By the end, you will have a solid understanding of these devices and their significance in building a robust and efficient network environment in the DevOps realm.
Task - 1: Introduce key network devices like routers, switches, load balancers, and proxy servers.
Here's an introduction to key network devices:
1) ROUTER:
A router is a networking device that connects multiple networks and forwards data packets between them. It operates at the network layer (Layer 3) of the OSI model and uses routing tables to determine the best path for data transmission. Routers are essential for interconnecting networks across the internet and play a crucial role in directing network traffic.
2) Switch:
A switch is a networking device that connects multiple devices within a local area network (LAN). It operates at the data link layer (Layer 2) of the OSI model and uses MAC addresses to forward data packets to the appropriate destination. Switches provide high-speed, dedicated connections between devices and enable efficient data transmission within a LAN.
3) Load Balancer:
A load balancer distributes incoming network traffic across multiple servers in a server farm or data centre to ensure optimal resource utilization and improve performance. It acts as an intermediary between clients and servers, distributing requests based on factors like server capacity, response time, and current load. Load balancers help prevent the overloading of individual servers and improve the scalability, availability, and reliability of applications.
4) Proxy Server:
A proxy server acts as an intermediary between clients and servers, forwarding client requests to the appropriate server and returning responses to the clients. It can provide various functionalities such as caching, filtering, and anonymizing client requests. Proxy servers enhance security, privacy, and performance by controlling access to resources, optimizing network traffic, and masking the client's identity.
Let's understand them deeply:
Task -2: Explain their roles, configurations, and integration within the network infrastructure.
1) ROUTER:
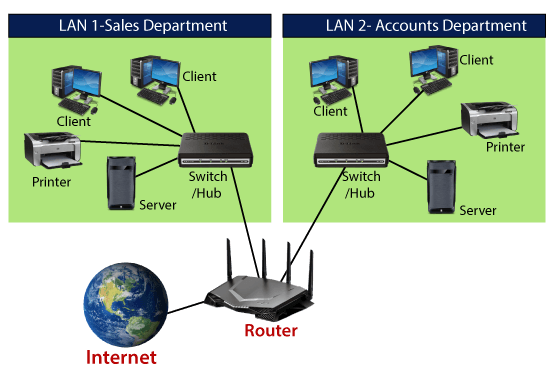
Role: Routers connect multiple networks, enabling data communication between them. They determine the best path for data transmission based on routing tables and protocols like Border Gateway Protocol (BGP) or Open Shortest Path First (OSPF).
Configuration: Routers require configuration of network interfaces, IP addresses, routing protocols, and security settings. This involves setting up routing tables, defining access control lists (ACLs), and configuring network address translation (NAT) if needed.
Integration: Routers are typically deployed at the network perimeter or at the core of the network infrastructure. They facilitate connectivity between different networks, such as LANs, WANs, or the Internet. Routers can be integrated with other network devices like switches, firewalls, and intrusion detection systems to provide a comprehensive network architecture.
Example: In a home network, a router connects multiple devices (computers, smartphones, smart TVs) to the internet. It acts as the gateway for internet access, allowing devices to communicate with each other within the network and access online services.
2) Switch:
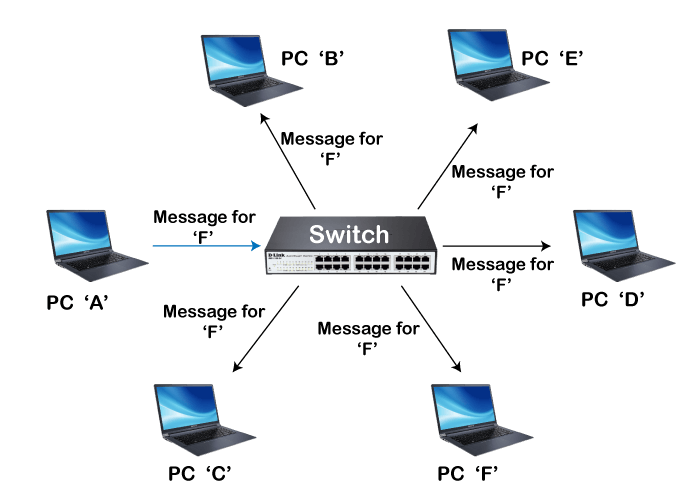
Role: Switches connect devices within a local area network (LAN) and facilitate the exchange of data between them. They forward data packets based on the destination MAC address, creating dedicated connections between devices.
Configuration: Switches need basic configuration, such as assigning IP addresses to management interfaces, setting up VLANs (Virtual LANs) for network segmentation, and configuring switch ports for specific purposes (e.g., access ports, and trunk ports).
Integration: Switches are commonly used in LAN environments, connecting computers, printers, servers, and other network devices. They can be integrated into larger network infrastructures by connecting them to routers, firewalls, and other switches to expand the network and improve performance.
Example: In a small office LAN, a switch connects computers, printers, and other devices. It enables devices to share files, access shared resources like printers, and communicate with each other within the local network.
3) Load Balancer:

Role: Load balancers distribute incoming network traffic across multiple servers to ensure even distribution of workload, optimize resource utilization, and enhance performance. They monitor server health, manage session persistence, and route traffic based on predefined algorithms (e.g., round-robin, least connections).
Configuration: Load balancers require the configuration of backend server pools, health checks, load balancing algorithms, and SSL/TLS termination if encryption is used. The configuration also involves defining virtual IP addresses and network interfaces.
Integration: Load balancers are typically deployed in front of web servers, application servers, or any server farm handling high-traffic loads. They are integrated into the network infrastructure by being placed between clients and servers, with traffic routed through the load balancer for efficient distribution.
Example: In a popular e-commerce website, a load balancer distributes incoming user requests across multiple servers. It ensures that the workload is evenly distributed, preventing any single server from being overwhelmed. This improves response times and the overall performance of the website.
4) Proxy Server:

Role: Proxy servers act as intermediaries between clients and servers, handling client requests on behalf of the server. They provide various functions such as caching, filtering content, and enhancing security by masking the client's IP address.
Configuration: Proxy servers require configuration of network settings, including defining listening ports, access control rules, and caching policies. They can also be configured for content filtering, SSL interception, and load balancing between multiple backend servers.
Integration: Proxy servers are typically deployed within an organization's network infrastructure. They can be integrated into web architectures as reverse proxies, intercepting and forwarding requests to backend web servers. Proxy servers can also be integrated with firewalls and authentication systems to enhance security and control access to resources.
Example: In a corporate network, a proxy server is deployed to control and monitor internet access. It acts as an intermediary between employees' devices and the internet. The proxy server can cache frequently accessed web content, filter malicious websites, and provide an additional layer of security for the organization's network.
Tomorrow we will learn about - Virtualization and Cloud Networking
Thank you so much for reading.
Follow me on LinkedIn to see interesting posts like this : )
Subscribe to my newsletter
Read articles from Vrishni Shree V B directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Vrishni Shree V B
Vrishni Shree V B
💻 Python | Docker | Jenkins | Networking | Git | Linux 💻 Passionate about leveraging technology to drive efficiency and deliver innovative solutions. Proficient in Python development, Docker containerization, Jenkins automation, computer networking, Git version control, and Linux administration. Skilled in collaborating with diverse teams to deliver high-quality software products. Proficient in AWS EC2 instance management and deployment. Seeking new opportunities to apply my expertise and contribute to impactful projects. Let's connect and explore how we can work together! Inter-personal Skills: Communication, Adaptability, Emotional intelligence, Active listening, Collaboration. Happy To Connect🔗😊 Feel free to reach me out😃@ --> vrishnishreevb531@gmail.com 📬