Password Hashing, Salting and Peppering
 Yash Pandya
Yash PandyaTable of contents
Hashing Password
Password hashing is a cryptographic method that transforms a password into a unique value known as a hash. This hash value, and not the actual password, is then saved in a database. When a user signs in, their password is hashed and compared to the database hash value. The user is authorized if the two hashes match.
The hash function used to hash passwords must be one-way. This implies that reversing the hash function and recovering the original password from the hash value is computationally impossible. Many different hash algorithms may be used for password hashing.
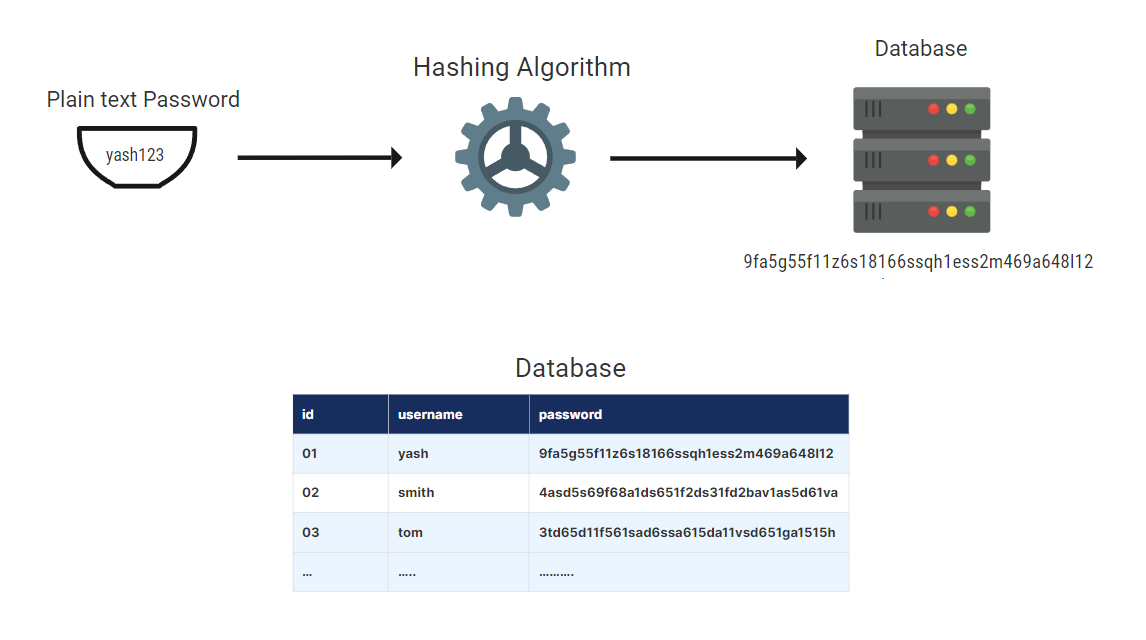
Example of Hashing Password:
<?php
// Creating a function to hash the password so that it can be called whenever required
function passwordHash($password) {
// Generate a secure, salted password hash
// password_hash is a built in function in php
// password_hash(your password, algorithm name)
$hashedPassword = password_hash($password, PASSWORD_DEFAULT);
// Return the hashed password
return $hashedPassword;
}
// Example
$password = "yash123";
$hashedPassword = passwordHash($password);
echo "Your Original password: " . $password . "\n";
echo "Hashed password: " . $hashedPassword . "\n";
?>
The algorithms used for hashing passwords are (PHP):
PASSWORD_DEFAULT
PASSWORD_BCRYPT
PASSWORD_ARGON2I
PASSWORD_ARGON2ID
Visit PHP Manual to read more about these algorithms.
Salting Password
Salting is a method of adding a random value to a password before hashing it. This makes it more difficult for attackers to use rainbow table attacks to break passwords. A rainbow table is a pre-calculated table containing password hashes and passwords. The attacker would need to generate a distinct rainbow table for each unique salt value whenever they used salt.
The salt value is kept in the database alongside the hash value. When a person signs in, their password is hashed using the same salt value that was initially used to hash the password. This assures that an attacker, even if they had a rainbow table for a certain salt value, will be unable to break the password for that user.
Salt = Hash (Password + Salt)
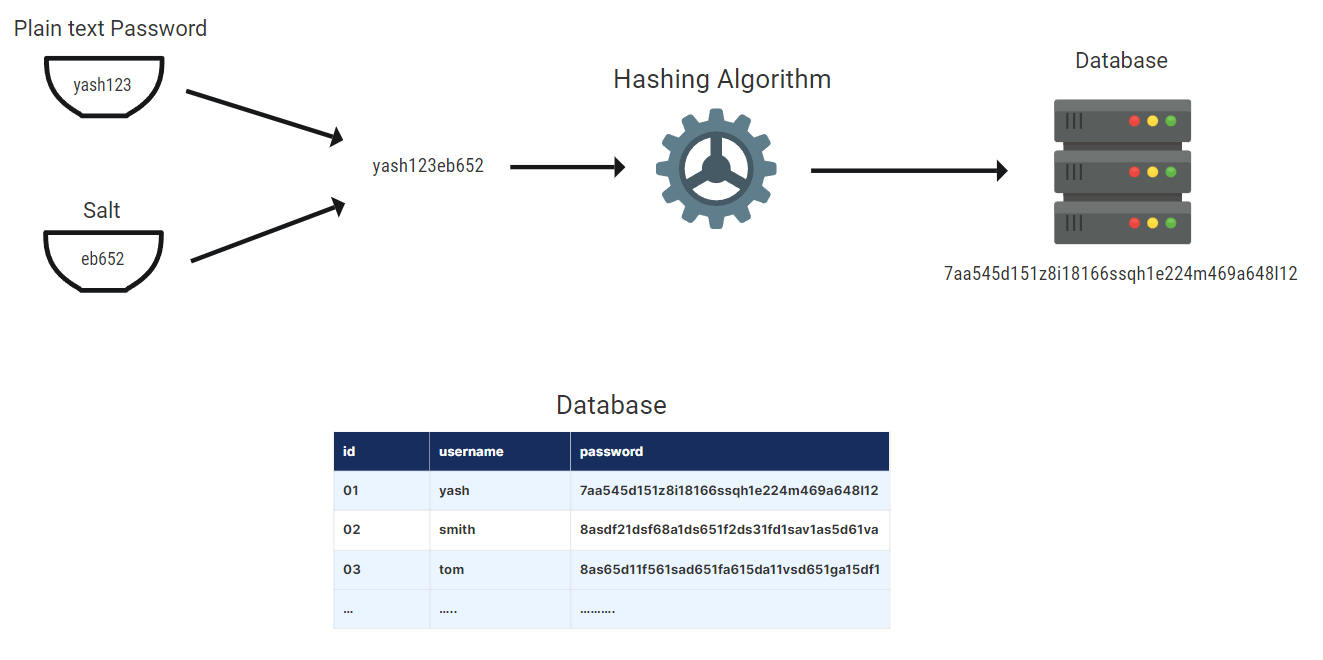
Example of Salting Password:
<?php
function passwordHash($password) {
// Salt value (static)
$salt = "eb652";
// Combine the password and salt
$saltedPassword = $password . $salt;
// A secure salted password hash is generated
$hashedPassword = hash('sha256', $saltedPassword);
// Return the hashed password
return $hashedPassword;
}
// Example usage
$password = "yash123";
$hashedPassword = passwordHash($password);
echo "Original password: " . $password . "\n";
echo "Hashed password: " . $hashedPassword . "\n";
?>
Peppering Password
Peppering is the process of adding a secret value to a password before it is salted and hashed. This makes cracking passwords much more difficult for attackers. The pepper is usually a lengthy, random string that is kept hidden. This implies that even if an attacker has the salt and hash values for a password, they still need to know the pepper value to crack it.
In most cases, the pepper value is saved separately from the salt and hash values in the database. This is done to prevent an attacker from guessing the pepper value based on the salt and hash values.
Thus, both salting and peppering work for better password security. Salting adds a random value to each user's hashed password to make it unique, as peppering adds a secret value to further safeguard the passwords. In most cases, salting is saved alongside the hashed password, but peppering is kept secret and stored separately. To provide good password security, both salting and peppering should be used in conjunction with a strong hashing technique.
Subscribe to my newsletter
Read articles from Yash Pandya directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Yash Pandya
Yash Pandya
hello I am a learning developer and I write blog as my passion is to provide information to the people/students in need.