Sensitive Data Exposure Through Password Reset Functionality - Bug Bounty
 Ramesh
Ramesh
Hi there 👋,
Hope you're doing well.
Today, I'm excited to share one of my interesting discoveries in bug hunting.
WHO AM I ?🎭
My self Ramesh. I am a security researcher, moreover certified ethical hacker(CEH), bug bounty hunter and CTF player. Dedicated security researcher specializing in threat analysis and vulnerability assessment and penetration testing.
Sensitives Data Exposure
Sensitive data exposure vulnerability refers to a security weakness or flaw in a system that could potentially expose sensitive or confidential information to unauthorized individuals or entities. This vulnerability typically arises when appropriate security measures are not in place or when there are flaws in the system's design or implementation.
Come to the real scenario…
Typically, I utilize Google dork to find targets🎯 For additional information, you can refer to the “google-hacking-database”
Recently, I focused on a particular target 🎯, but I'm unable to reveal its actual name due to their policy. Let's refer to it as "target.com" for now. Once i selected a target, my initial step involves identifying the technology being used, such as the framework, CMS, CDN, programming language, and database using "Wappalyzer". Concurrently, I run automated bash scripts in the background to discover subdomains, hidden parameters, and perform directory brute force analysis.
“Accurate timing plays a crucial role in bug hunting.”
Simplify and accelerate⏱️ target🎯 information gathering. Here are some tools for you assetfinder, amass, sublist3r, subfinder, waybackurls, httprobe, gau, nuclei etc..
Note: Analyse the inside functionality of the target it will give some ideas 💡 for further movement.
I attempt to identify common vulnerabilities such as XSS, HTML injection, SQL injection, SSRF, CSRF, Broken Access Control, and more. But unfortunately i didn’t get any interesting bugs 🥲
”Stay hopeful and never give up.”
In the end, I explored the "Forgot Password" functionality, where I examined common vulnerabilities such as Password Reset Poisoning, Host Header Injection, Session-related vulnerabilities, and more. Unfortunately, luck wasn't on my side as I couldn't find any vulnerabilities🥲. However, after a few attempts, I did observe a weak implementation 😁in their system

It is a common practice on most websites that when attempting to reset the password using the "Forgot Password" functionality, it prompts for the corresponding username or email associated with the account to receive the password reset link.
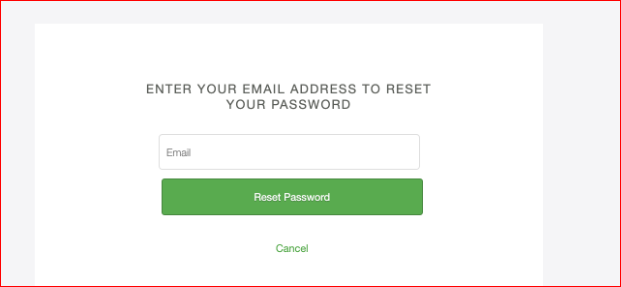
Weak Implementation: However, in this case, if we provide the email address of an existing user account, we receive the user's details in the response.
To accomplish this, we require a web proxy tool. "Burp Suite". Burp Proxy operates as a web proxy server between the browser and target applications. It enables you to intercept, inspect, and modify the traffic that passes in both directions.
Come here we will try to play with the weakness.
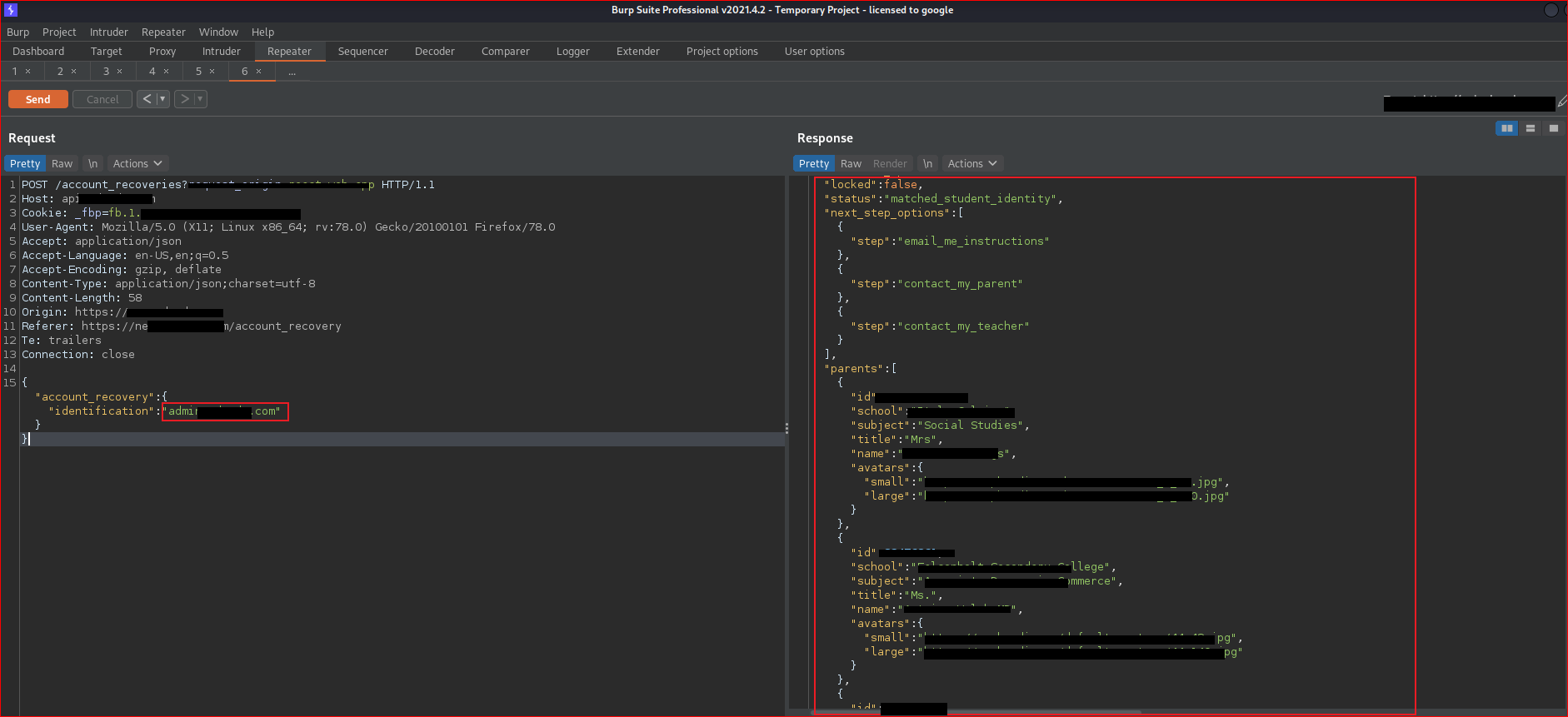
For testing purposes, I had already registered an account. I provided my email ID, captured the request on Burp Suite, and subsequently analyzed the response.
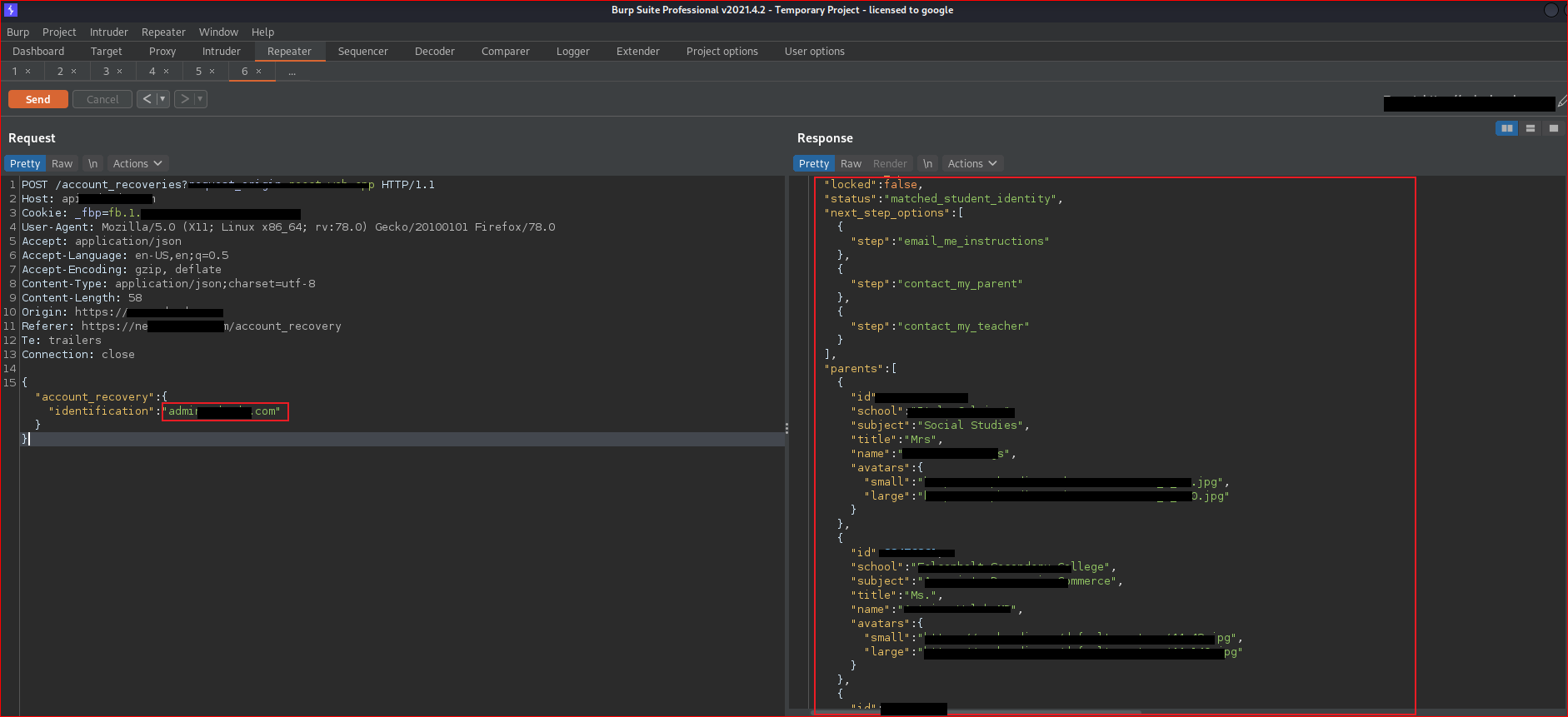
Wow🤩 I am able to view my details such as ID with JWT access token, email, and various other information.

Then I thought if I could get the email ID of any user with an account in this, I would be able to retrieve the datas of users.
Now, I need to adopt a hacker's 🎭mindset. Yes, it happened! I suddenly had a thought about the admin email ID. "In many cases, the admin email ID for websites follows a common pattern such as admin@website.com. For example, admin@target.com."
I simply entered the admin email ID, Booom! I was able to retrieve all user and admin details.
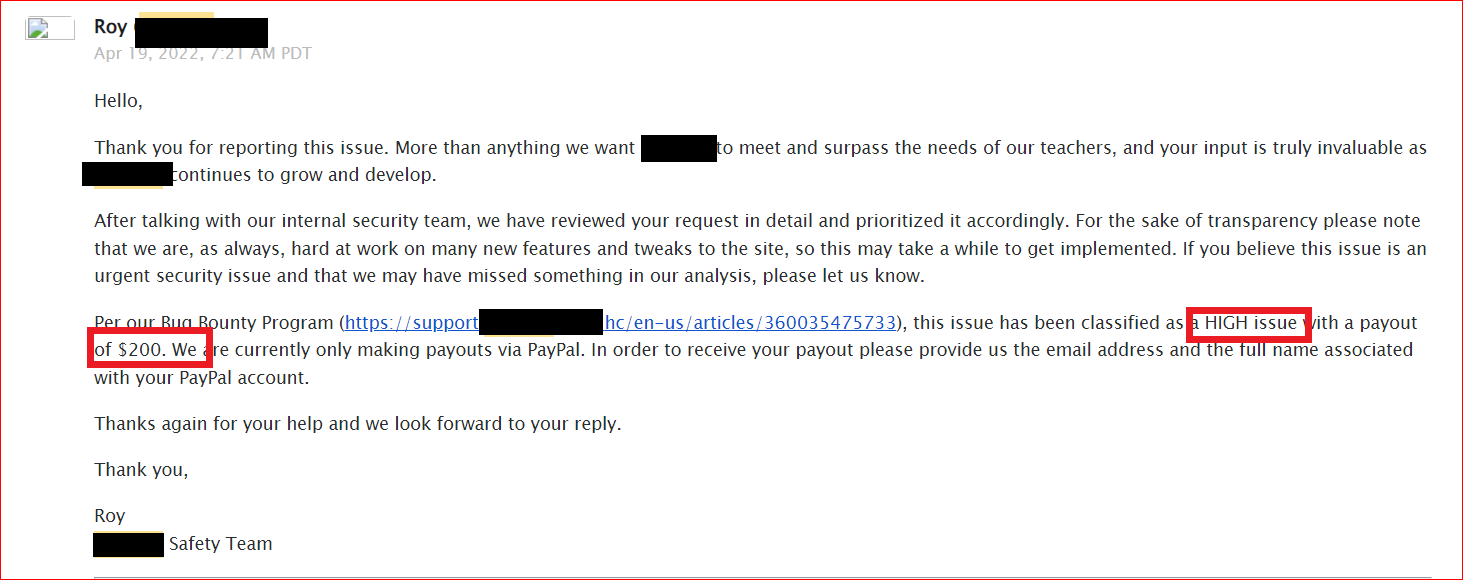
Finally, I reported the issue to the company, and within a week i received a confirmation email from them, along with a high severity rating assigned to it. Additionally, they also awarded me a bounty 💸for my findings🐞.
Your time spent reading my write-up is sincerely appreciated👏, and I will soon be publishing the next Vulnerability. Wishing you safety and well-being.
Subscribe to my newsletter
Read articles from Ramesh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ramesh
Ramesh
Passionate about the art of hacking and defending against cyber attacks