Authenticated Origin Pulls (mTLS) between Cloudflare and Ingress Nginx
 Sreejith P S
Sreejith P SAuthenticated Origin Pulls help ensure requests to your origin server come from the Cloudflare network, which provides an additional layer of security on top of Full or Full (strict) encryption modes.
This authentication becomes particularly important with the Cloudflare Web Application Firewall (WAF). Together with the WAF, you can make sure that all traffic is evaluated before receiving a response from your origin server.
Explanation
When visitors request content from your domain, Cloudflare first attempts to serve content from the cache. If this attempt fails, Cloudflare sends a request — or an origin pull — back to your origin web server to get the content.
Authenticated Origin Pulls make sure that all of these origin pulls come from Cloudflare. Put another way, Authenticated Origin Pulls ensures that any HTTPS requests outside of Cloudflare will not receive a response from your origin.
Cloudflare enforces authenticated origin pulls by adding an extra layer of TLS client certificate authentication when establishing a connection between Cloudflare and the origin web server.
Zone-level authenticated origin pulls
When you enable Authenticated Origin Pulls for a zone, all proxied traffic to your zone is authenticated at the origin web server.
Make sure your zone is using an SSL/TLS encryption mode of Full or higher.
Upload certificate to origin
First, upload a certificate to your origin.
To use a Cloudflare certificate (which uses a specific CA), download the .PEM file and upload it to your origin.
Configure origin to accept client certs
It can be done in two ways in Nginx ingress
Configure it in each ingress resource.
Create a Kubernetes secret cloudflare-origin with Cloudflare certificate. secret key should be ca.crt and the value should be the content of the certificate.
ubectl create secret generic cloudflare-origin --from-file=ca.crt=cloudflare-origin.pemAdd below annotation to each ingress resource
nginx.ingress.kubernetes.io/auth-tls-secret: cloudflare-origin nginx.ingress.kubernetes.io/auth-tls-verify-client: "on"
Configure in the Nginx ingress controller if all the domains are configured in Cloudflare.
To configure in the nginx-ingress controller
Create a secret in the same namespace where nginx ingress controller is located
kubectl create secret generic cloudflare-origin --from-file=cloudflare-origin.pem -n ingressAdd the following keys into
values.yamland upgrade release:controller: extraVolumes: - name: origin-pull-certificate secret: secretName: cloudflare-origin extraVolumeMounts: - name: origin-pull-certificate mountPath: /var/lib/certificates/cloudflare config: server-snippet: | ssl_client_certificate /var/lib/certificates/cloudflare/cloudflare-origin.pem; ssl_verify_client on;After this, all ingresses will demand an SSL client certificate.
Enable Authenticated Origin Pulls (globally)
Enable Authenticated Origin Pulls as an option for your Cloudflare zone.
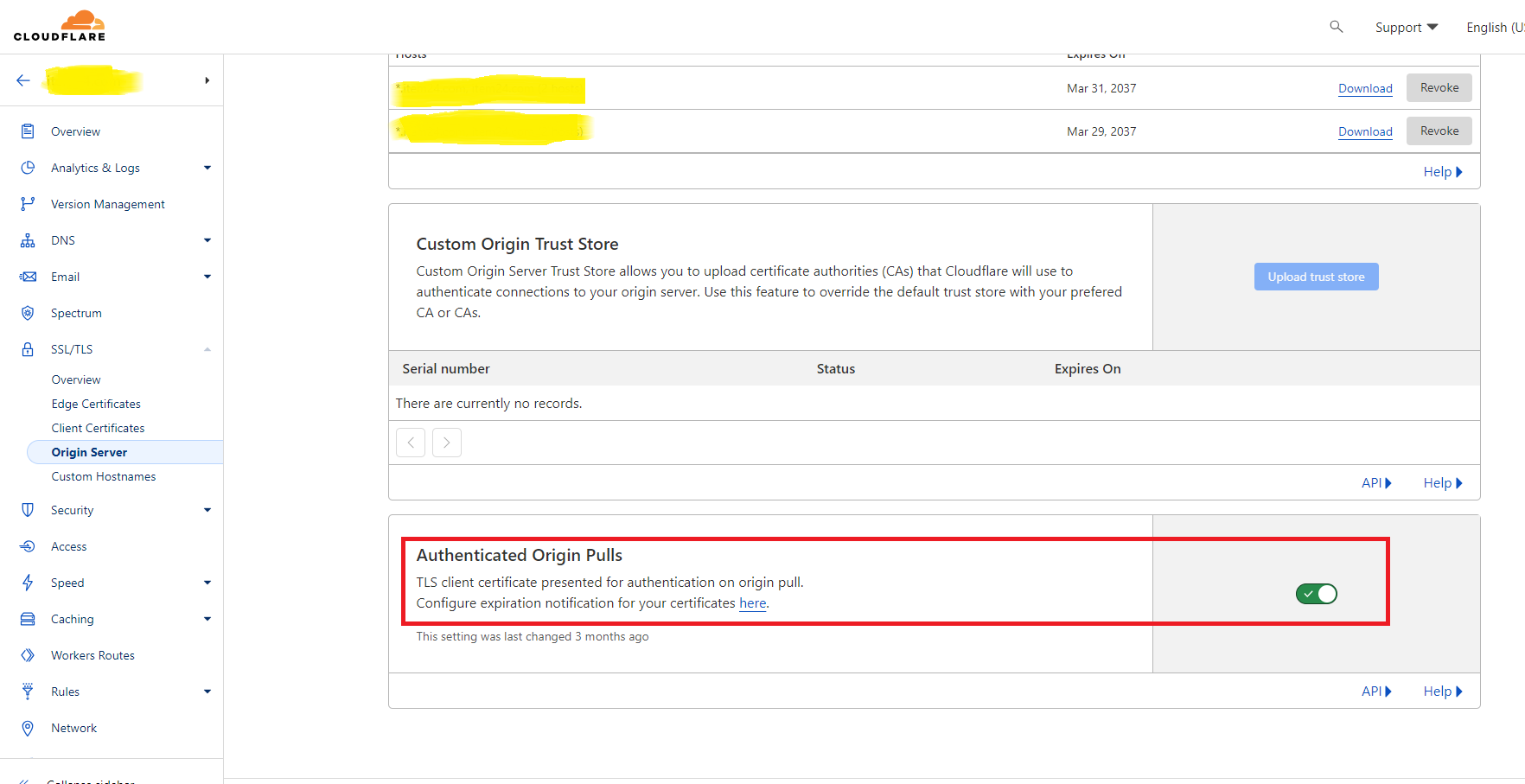
To enable Authenticated Origin Pulls in the dashboard:
Log in to your Cloudflare accountOpen external link and go to a specific domain.
Go to SSL/TLS > Origin Server.
For Authenticated Origin Pulls, switch the toggle to On.
Subscribe to my newsletter
Read articles from Sreejith P S directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
