FortiOS RCE Vulnerability - How to update FortiGate firmware
 Kaleb McGaugh Mohr
Kaleb McGaugh Mohr
In this article, I will be demonstrating how to update the FortiOS firmware version, on your FortiGate firewall. This article can assist in the mitigation of the RCE vulnerability affecting SSL VPN services on FortiOS v7.2.4, as outlined in CVE-2023-27997.
Security Disclaimer
If your Fortinet FortiGate is running FortiOS firmware version 7.2.4, 6.0.16, 6.2.1.4, 6.4.13, or 7.0.11, then you have a severe vulnerability in your firewall, and it should be patched immediately. The vulnerability allows for remote code execution on FortiGate's SSL VPN interface, allowing for unauthorized remote access to your corporate internal resources.
Why is this bad?
If an attacker gains successful access to your SSL VPN, they can remotely connect to your corporate internal network. SSL VPNs are not like ZTNA, or identity-based access control mechanisms - whatever is defined in the trusted subnets will be what the attacker will have access to, so, if your security policy is designed to where you have remote teleworkers connecting to your network via SSL VPN, to access internal servers, then an attacker could breach this policy, and break into your network, and do lots of damage. For example, once the attacker exploits the vulnerability, and connects to the network, they could inject ransomware payloads across your servers, leaving your network in a catastrophic state.
Mitigating your FortiGate
The process to mitigate your FortiGate is to upgrade its firmware version to FortiOS v7.2.5. I will now provide a demonstration of how to upgrade the firmware below.
Configuration Backup
Before performing the firmware upgrade, you should backup your configuration. FortiGate may automatically backup the configuration; however, I have run into some deployments where the backup doesn't contain any data, so it is best to manually backup the configuration before upgrading.
Step One
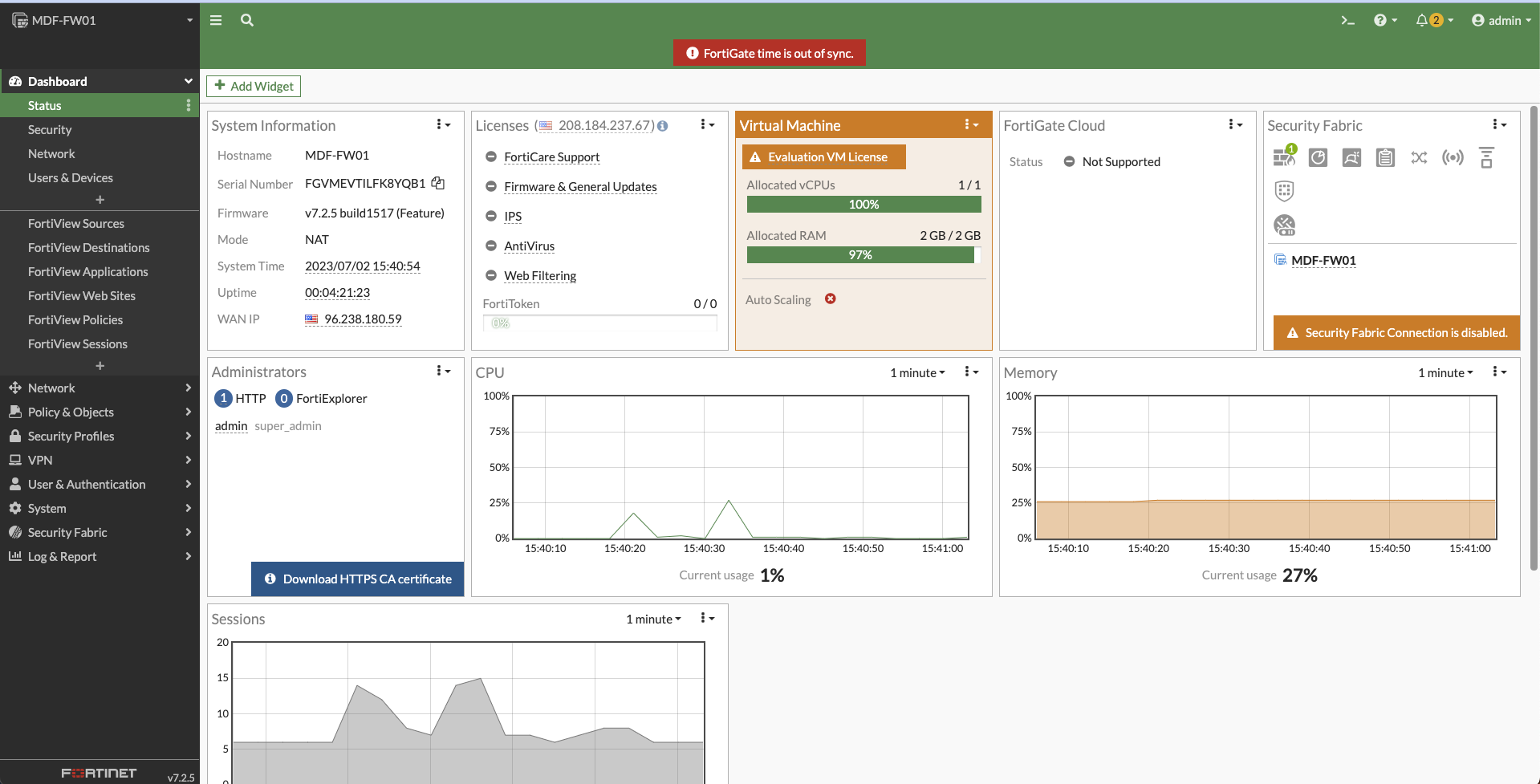
Log into your FortiGate's web interface. (Yes, I know my time is out of sync. I'm using a lab FortiGate. Ignore it.)
Step Two
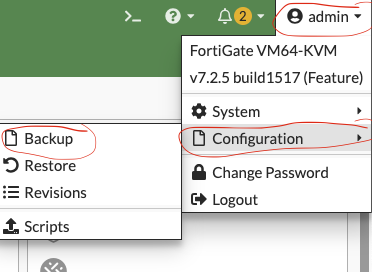
Click on your profile in the upper right, then go to Configuration > Backup.
Step Three
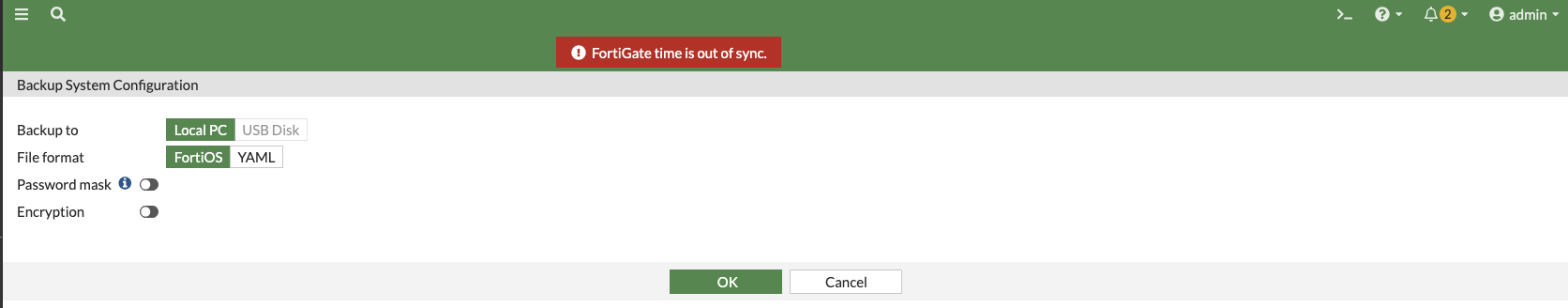
Choose local backup and set the file format to FortiOS. It is up to you whether or not you want to use a password mask & encryption. Click "ok" and a config file will download to your system.
Step Four
Verify that the full configuration is present in the .conf file. I use my terminal to do so. If you're on a Windows device, you can open the file via Notepad, as it is just a plaintext file.
On the FortiGate you can run a show full-configuration and compare the two configs to make sure nothing is missing.
At this point, you're ready to move on to the next steps.
Upgrading Firmware
If your FortiGate is affected, you will have an immediately available option on your system to upgrade its firmware to v7.2.5. I will now demonstrate the process to upgrading your firmware.
Step One
Go to System > Fabric Management. You will see your FortiGate listed. If you use the security fabric, and have any FortiAPs and FortiSwitches controlled through FortiLink, then they will also show up here.
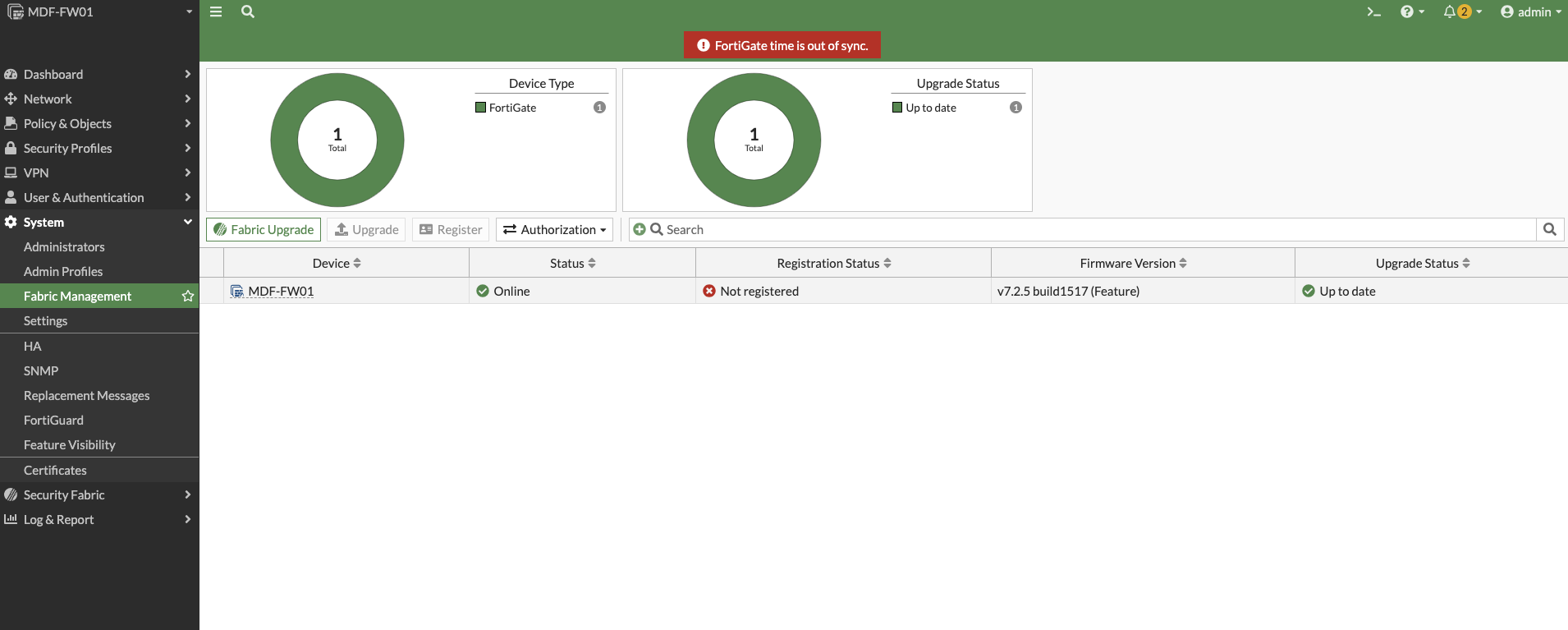
Step Two
Click on your FortiGate, then click "Upgrade". Choose "latest" or "all upgrades" to see a list of available upgrades.

My FortiGate unit is upgraded to the latest version. The above picture depicts an update available on this FortiGate, however, it is not the latest version. You should look for "FortiOS v7.2.5build1517(GA)" as the option.
Click on the firmware version, then click next.
If your FortiGate is a few firmware versions behind, you may get a prompt similar to below:

You will want to choose "follow upgrade path" if that is the case. Otherwise, if you choose "directly update to v7.2.5", then you run the risk of completely wiping your FortiGate's configuration. Some features may also not work correctly if you skip firmware versions.
Step Three
Click "confirm and backup config". Yes, we have already backed up the config; however, we did that as a preventative measure. Again, I have ran into some FortiGates where there is no data in the .conf file at this step, so be redundant with backing up your configurations.
Once the configuration is backup is taken, the FortiGate will begin the upgrade process. Once the device reboots, you should then be running FortiOS version 7.2.5
Step Four
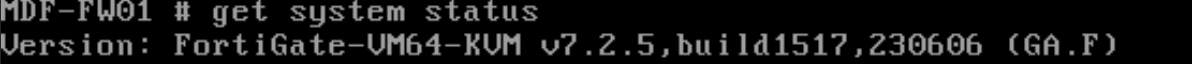
Finally, after your firmware upgrade completes, you should log into you FortiGate and ensure that it is running FortiOS version 7.2.5 - the web interface will immediately show you.
You can also check through the command line if you prefer. Run get system status and it will be the first line.
Conclusion
To mitigate your FortiGate against the RCE vulnerability (CVE-2023-27997), you should upgrade your FortiGate to firmware version 7.2.5 - this article demonstrated the procedure for upgrading your FortiGate's firmware.
Subscribe to my newsletter
Read articles from Kaleb McGaugh Mohr directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Kaleb McGaugh Mohr
Kaleb McGaugh Mohr
Network Engineer. Passionate for routing and switching, automation, resiliency, cybersecurity, cloud computing, and data center infrastructure.