Exploring Misconfigured S3 Buckets through Diverse Enumeration tools Part 2.
 Goodycyb
Goodycyb
INTRODUCTION
In the previous lab, we effectively set up both a secure and vulnerable S3 bucket. By conducting penetration testing, we obtained valuable insights into the vulnerabilities that can result from misconfigured AWS S3 buckets. The testing played a crucial role in identifying and highlighting cases of misconfiguration.
Lab objective
The lab series focuses on performing S3 bucket enumeration using a variety of S3 bucket enumeration tools, enabling ethical hackers and penetration testers to gather information effortlessly during the enumeration process.
Disclaimer
The S3 bucket enumeration tools provided in this lab are intended for educational purposes only and should not be utilized for illegal activities or unauthorized access to buckets or websites.
Things you for this lab
The following prerequisites are needed:
A Parrot Security virtual machine
Web browsers with an active Internet connection
Administrator privileges for executing the tools.
In this lab, you can utilize any of the two publicly accessible misconfigured buckets.
flaws.cloud cloud security challenge game (Check Challenge Walkthrough)
CEH publicly available S3 bucket
For this lab, our target domain for enumeration is flaws.cloud and CEH
Enumerate S3 buckets using lazys3
Lazys3 is a Ruby script utility designed for performing brute-force attacks on AWS S3 buckets through various permutations. With this tool, you can identify publicly accessible S3 buckets and conduct targeted searches on specific companies' S3 buckets by providing the company name.
- Download and install lazys3 (GitHub) on your Linux system using the following command:
git clone https://github.com/nahamsec/lazys3.git
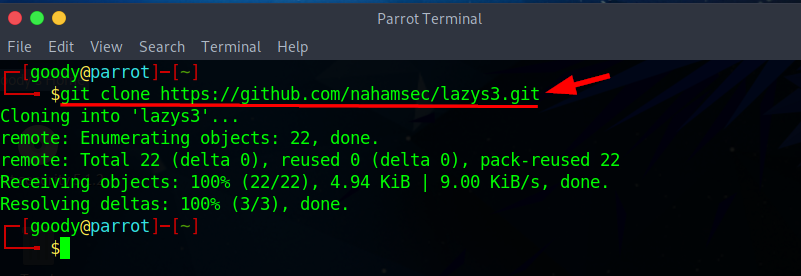
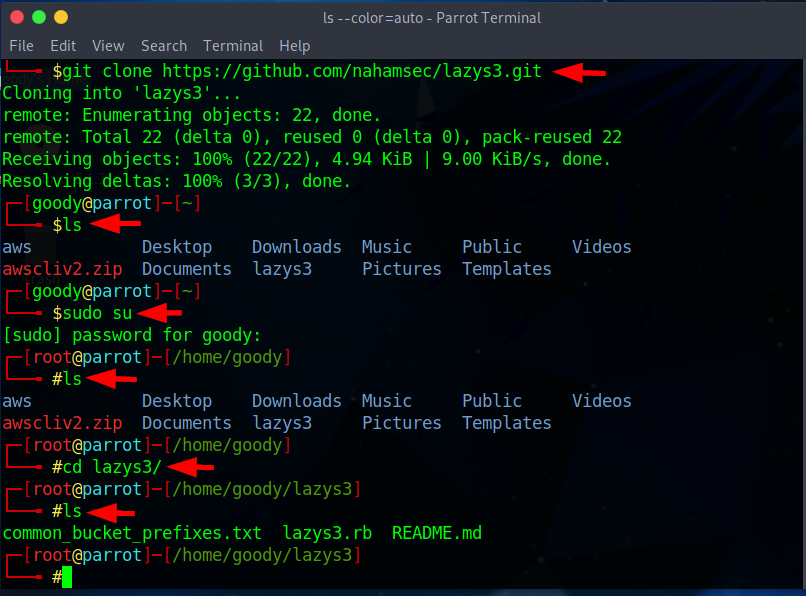
- Navigate to lazys3.rb in the lazys3 folder using the command.
# switch user using
$sudo su
$ls
$cd lazys3
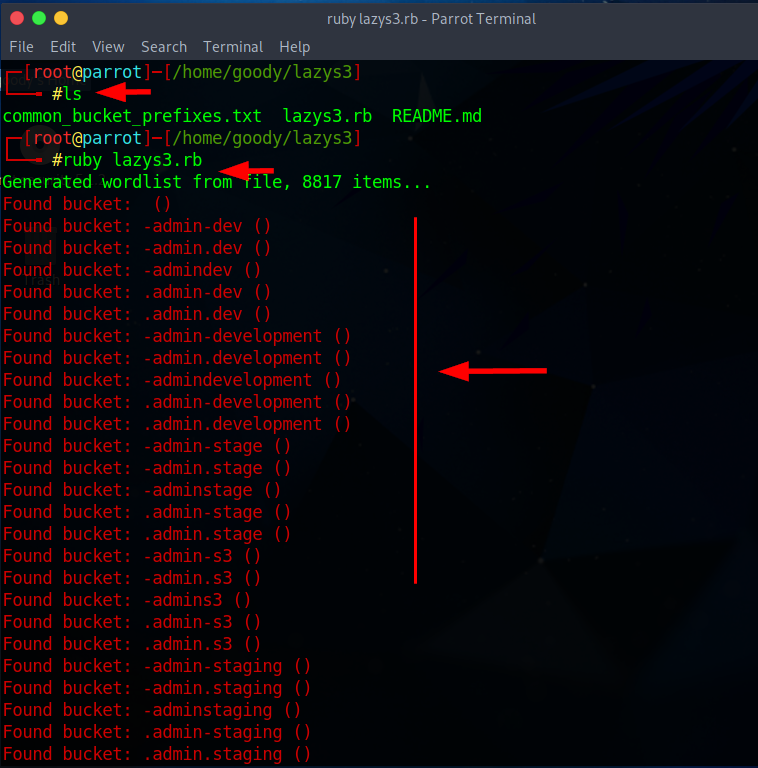
Now type
ruby lazys3.rband press Enter.A list of public S3 buckets is displayed, as shown in the screenshot.
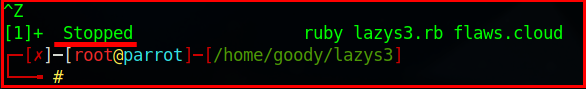
Press Ctrl+Z to stop the script.
- You can search the S3 buckets of a specific company. To do so, type ruby
lazys3.rb [Company]and press Enter.
Note: Here, the target company name is flaws.cloud; you can enter the company name of your choice.
ruby lazys3.rb flaws.cloud
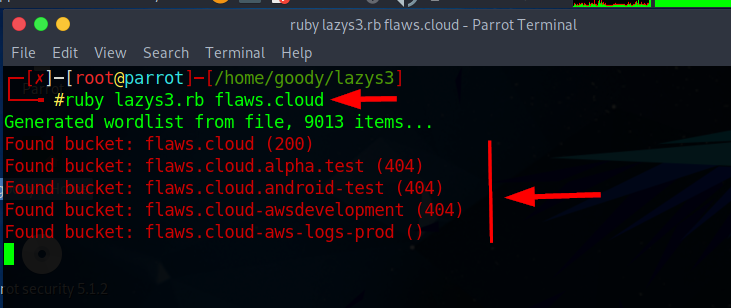
Note: It will take some time to obtain a complete list of the available S3 buckets.
- Press Ctrl+Z to stop running the script.
Enumerate S3 Buckets using S3Scanner
S3Scanner is a utility designed to identify accessible S3 buckets and extract their contents. It operates by taking a provided list of bucket names as input and outputs the discovered S3 buckets into a file. Additionally, the tool offers the capability to locally dump or list the contents of these "open" buckets.
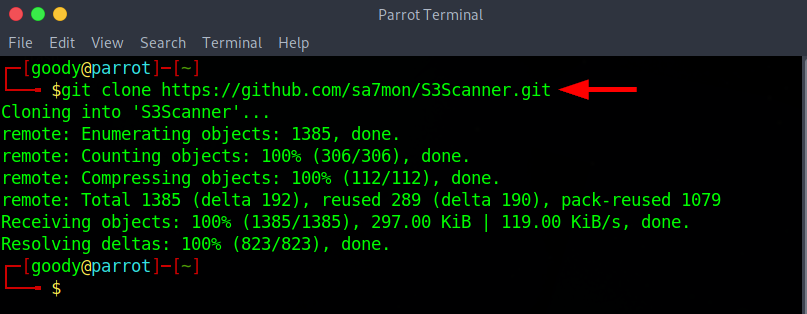
- Download S3Scanner (Github) using the following command:
git clone https://github.com/sa7mon/S3Scanner.git
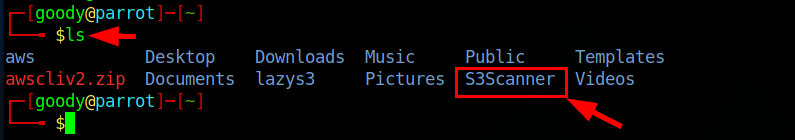
- Type the following command to navigate to the cloned repository:
Note: By default, the tool is cloned to your current working directory.
# cd S3Scanner/
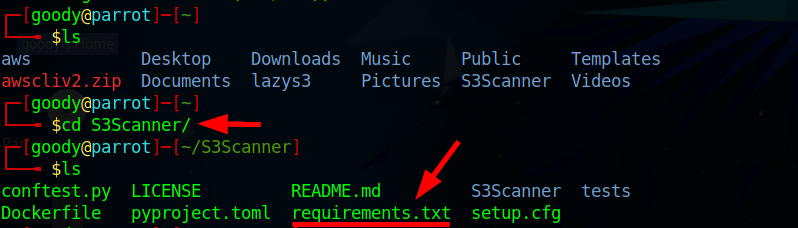
In your S3Scanner folder, type and press Enter to install the required dependencies.
pip3 install -r requirements.txt
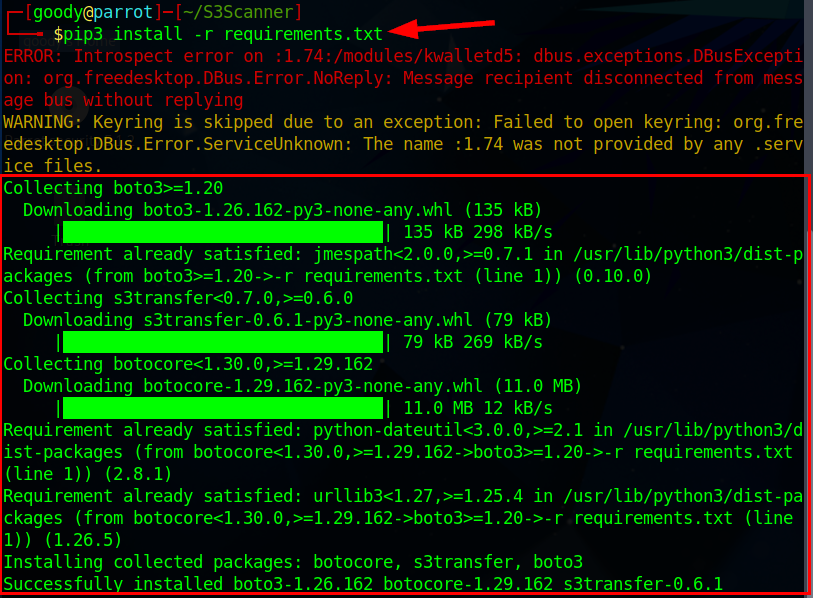
After the successful installation of the dependencies, run the command to check the access permissions for flaws.cloud
python3 -m S3Scanner scan --bucket flaws.cloud
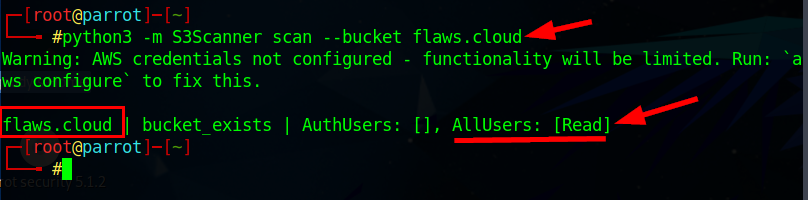
Here, flaws.cloud bucket exists with READ access to All users (Everyone via the internet)
Next, create a directory called S3Dump and execute the command to dump (download) content from the flaws.cloud bucket.
Type the following command as shown in the image below:
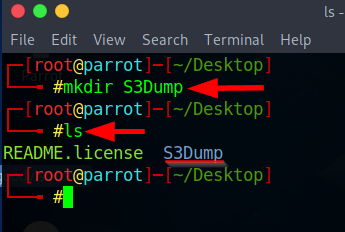
On your terminal, type the following command and press Enter:
NB: Replace <with a name of your choice> ~/Desktop/*******/
In this lab, S3Dump is the name of the Folder or Directory created on the Desktop.python3 -m S3Scanner dump --bucket flaws.cloud --dump-dir ~/Desktop/S3Dump/
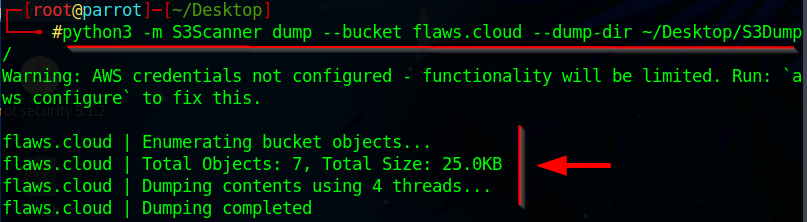
- Navigate to the S3Dump directory or folder
$cd S3Dump
$ls
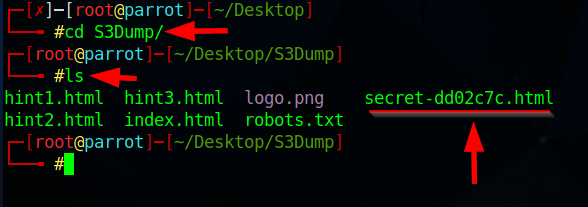
Additionally, there are various tools available for S3 bucket enumeration, including:
s3recon (https://github.com)
Mass3 (https://github.com)
Bucket Finder (https://digi.ninja)
S3Inspector (https://github.com)
s3-buckets-bruteforcer (https://github.com)
You can check out the GitHub Read.Me file for the above tools to see how to perform S3 bucket enumeration.
These tools can be utilized to conduct S3 bucket enumeration for a specific website or organization.
Enumerate S3 Buckets using Google Chrome Extension
The Google Chrome extension called S3BucketList captures S3 buckets identified in requests and provides a list that includes their permissions. This tool enables us to determine the public or private status of an S3 bucket. In this case, we will employ the S3BucketList Google Chrome to discover S3 buckets associated with a specific website target.
S3BucketList Installation
https://github.com/AlecBlance/S3BucketList/tree/master#installation
Download the S3BucketList zip
Extract
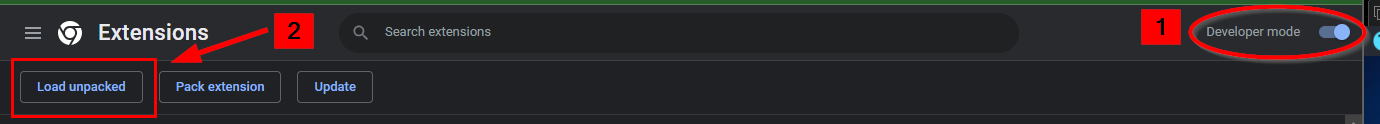
Go to Google Chrome's Settings (icon > Tools > Extensions).
Enable Developer Mode ( toggle button in the top-right corner )
Click "Load unpacked" and locate the extracted zip from the previous step
- Download the tool .zip file from GitHub
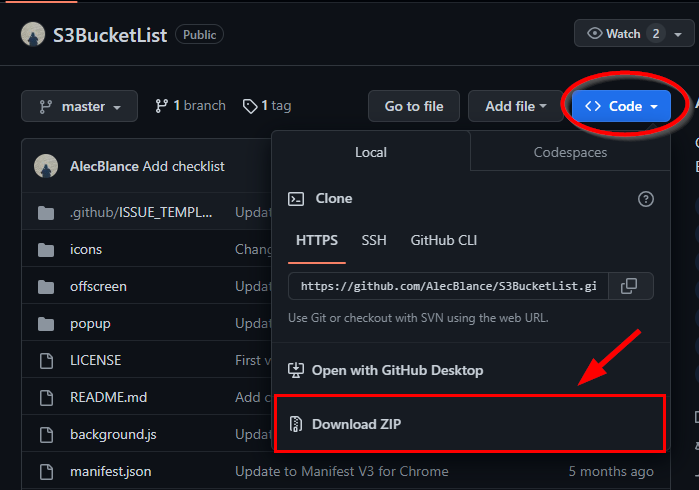
- Go to Google Chrome's Settings - icon > Tools > Extensions
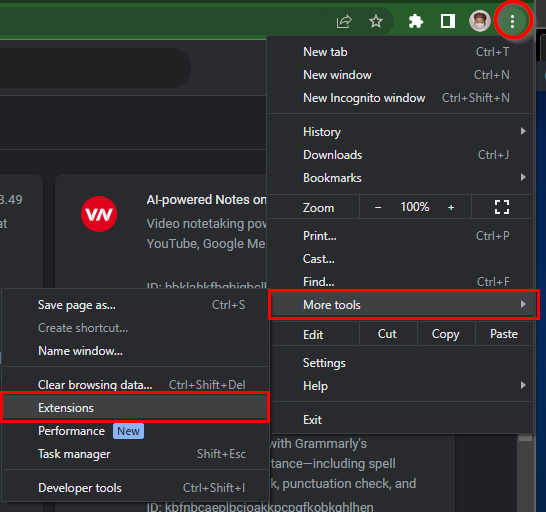
- Enable Developer Mode ( toggle button in the top-right corner )
- Click "Load unpacked" then locate the extracted zip from the previous step and select it.
Open a new tab in the browser, in the address bar, type https://www.eccouncil.org and press Enter.
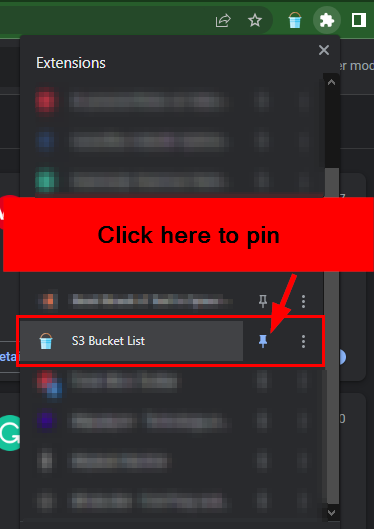
Click the S3 Bucket List icon present on the top-right of the browser window to view the recorded S3 buckets.
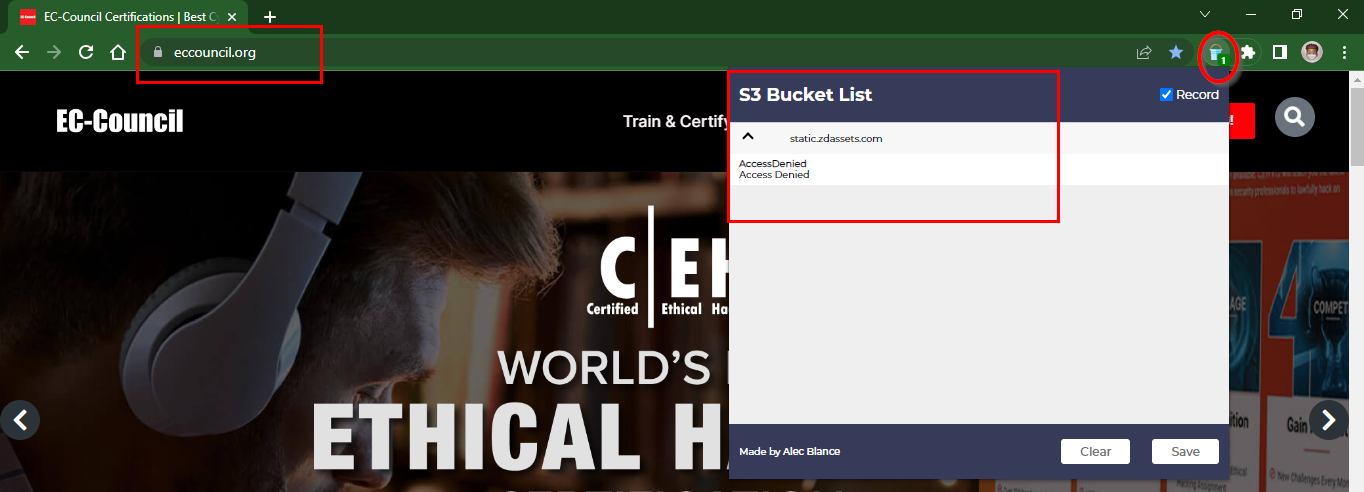
Based on the image provided, the denial of access indicates that either the domain eccouncil.org is not hosted in an S3 bucket, or the S3 bucket is properly configured.
- Open a new browser tab and type certifiedhacker1.s3.amazonaws.com in the address bar, and press Enter.
NOTE: An open S3 bucket named "certifiedhacker1" was established by Eccouncil, granting unrestricted public access to all users via the Internet.
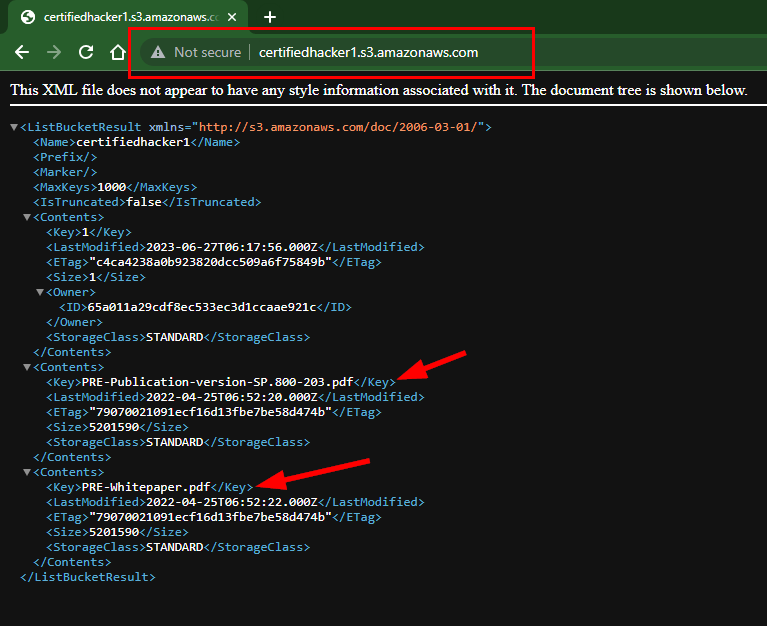
- Now, click on the S3 Bucket List icon to view its permissions.
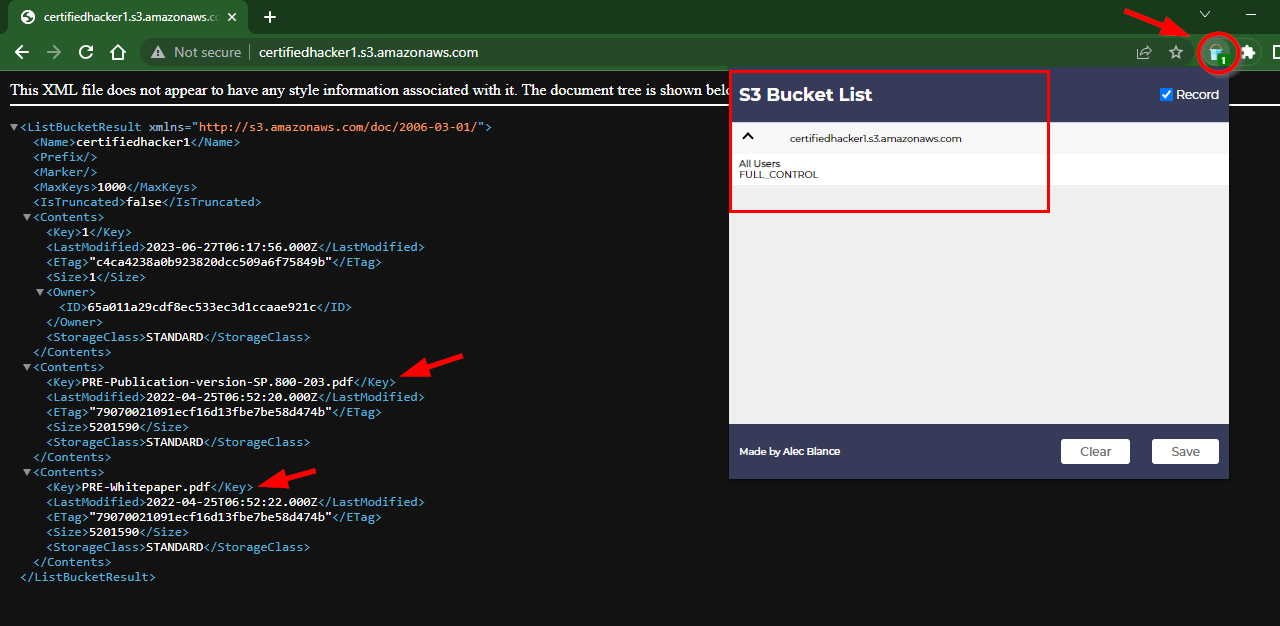
When S3 buckets are set to public, the content within them becomes accessible to any user on the internet. This misconfiguration can be exploited by attackers to their advantage.
Disclaimer: The tools provided in the lab for S3 bucket enumeration, as mentioned earlier, are intended solely for educational purposes. It is strictly prohibited to use these tools illegally or on unauthorized buckets or websites.
Subscribe to my newsletter
Read articles from Goodycyb directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Goodycyb
Goodycyb
Hey there! 👋🏾 I'm Goody, a Cloud Threat Researcher by Day 🌞 and a Cloud Security Content Engineer by Night🌜. Join me on my journey as I explore the realm of Threat Detection in Cloud Security.