AWS Virtual Private Cloud
 Rajendra Thapa
Rajendra Thapa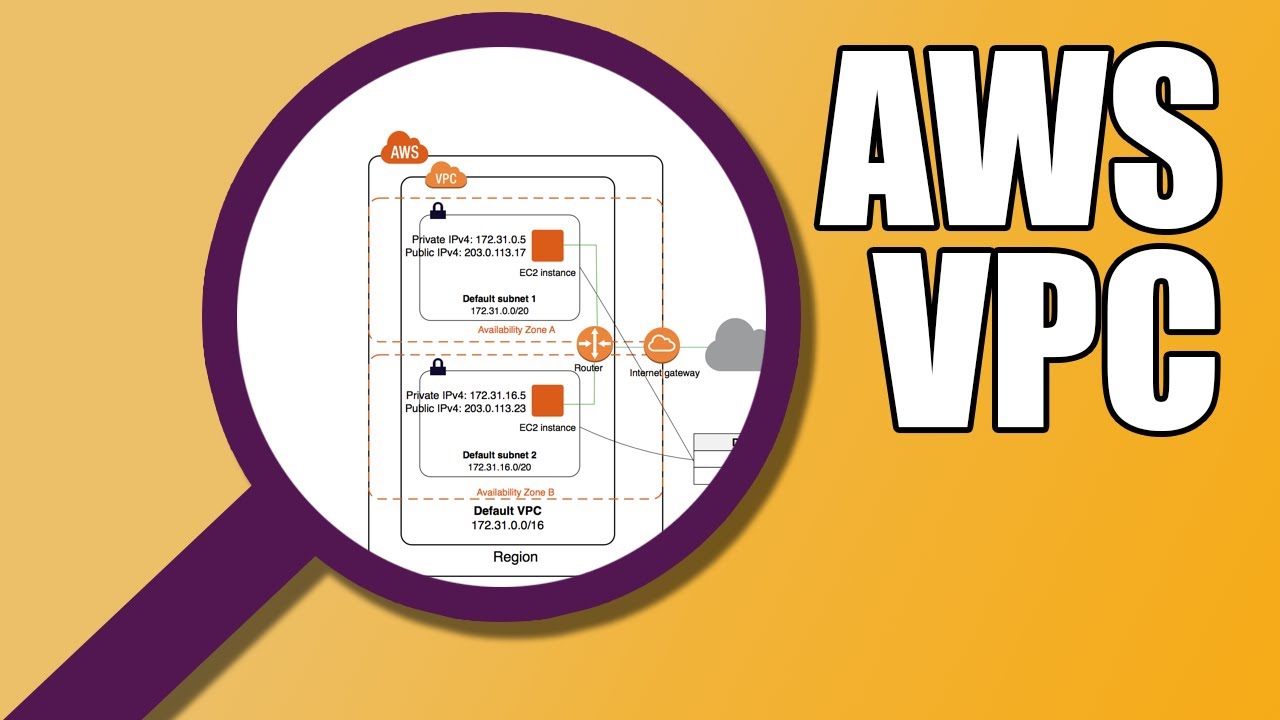
What is Amazon VPC (Public-Private Subnet)
AWS VPC stands for Amazon Virtual Private Cloud. It is a virtual network service provided by Amazon Web Services (AWS) that allows you to create a logically isolated section of the AWS cloud where you can launch AWS resources, such as Amazon EC2 instances, RDS databases, and more.
With AWS VPC, you have control over your virtual networking environment, including IP address ranges, subnets, route tables, and network gateways. It allows you to define and configure your own virtual network topology, enabling you to establish private network connectivity, control network access, and secure your resources.
Key features and components of AWS VPC include:
Subnets: VPC allows you to divide your virtual network into multiple subnets, each located in a specific Availability Zone. Subnets help you isolate and organize your resources.
Internet Gateway: It provides a connection between your VPC and the internet, allowing resources within the VPC to access the internet or be accessed from the internet.
NAT Gateway: Network Address Translation (NAT) Gateway allows instances within your private subnets to access the internet while blocking inbound traffic from the internet.
Route Tables: They control the traffic between subnets and determine where the traffic is directed. You can define the routing rules to control the flow of traffic within your VPC.
Security Groups and Network ACLs: These are used to control inbound and outbound traffic at the instance and subnet levels. Security groups act as a virtual firewall for your instances, while Network ACLs provide network-level access control.
VPC Peering: It allows you to connect two VPCs, enabling direct communication between resources in different VPCs using private IP addresses.
AWS VPC provides a flexible and scalable way to create isolated network environments within the AWS cloud, giving you full control over your network configuration and security settings. It allows you to build complex architectures and deploy your applications securely in the cloud.
Steps to Create VPC in AWS
Log in to the AWS Management Console at https://console.aws.amazon.com.
Navigate to the AWS VPC service by searching for "VPC" in the AWS Management Console search bar.
In the VPC dashboard, click on "Create VPC" to start creating a new VPC.
Provide a name and an IPv4 CIDR block for your VPC. The CIDR block defines the range of IP addresses that will be available for your VPC.
Configure additional settings such as IPv6 CIDR block (optional) and tenancy (default or dedicated). Tenancy determines whether your instances run on shared hardware or dedicated hardware.
Click on "Create" to create your VPC.
Once the VPC is created, you can create subnets within it. Subnets are segments of the VPC's IP address range that you can allocate to different availability zones.
In the VPC dashboard, click on "Subnets" and then "Create subnet."
Provide a name for the subnet, select the VPC you created in the previous step, choose the availability zone, and specify the subnet's IPv4 CIDR block.
Click on "Create" to create the subnet.
You can create additional subnets in the same way to meet your requirements.
These steps provide a basic outline for creating a VPC in AWS. However, there are more advanced configurations and options available within the AWS VPC service, such as configuring route tables, internet gateways, security groups, and more, depending on your specific needs.
It's important to note that creating and configuring a VPC requires appropriate permissions and familiarity with networking concepts. Make sure to review the AWS documentation and best practices for detailed instructions and guidance.
Now you can create an instance and attach your own VPC while launching
AWS Project Used In Production Complete Implementation
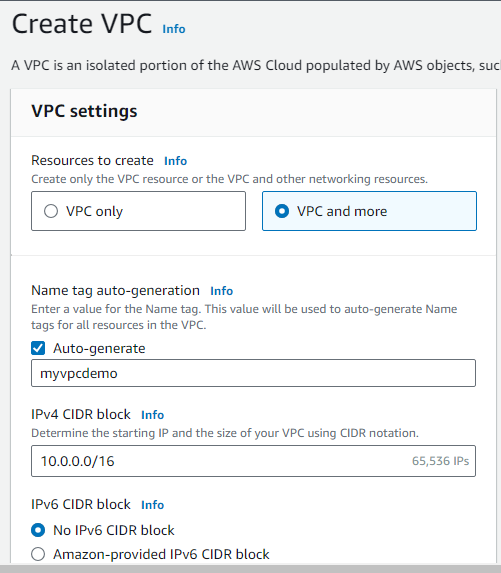
VPC Creation
Login to VPC and click on Create VPC
-Select VPC more (it creates VPC, subnet everything for you)
-Provide the name for your VPC, CIDR Block and no IPV6
-Set the Tenancy as Default and select 2 availability zones for more availability
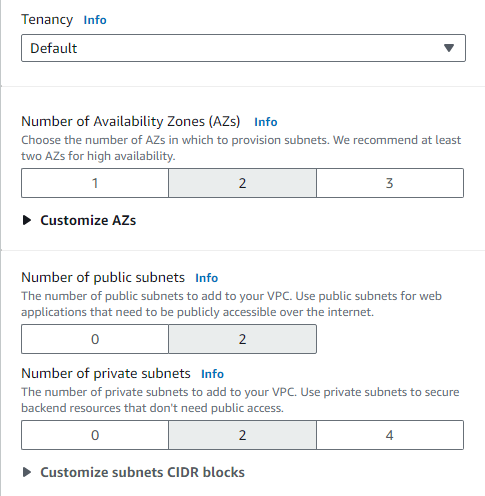
-Also set NAT gateways as 1 per AZ
Preview of our VPC
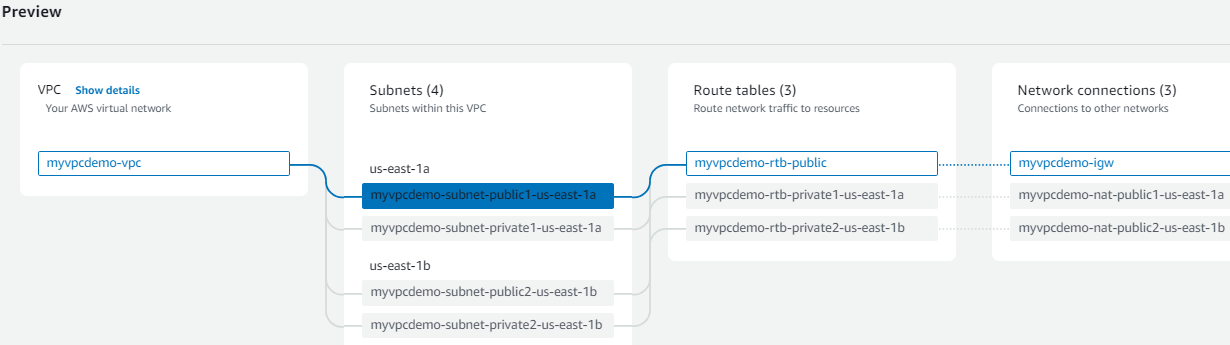
Click on Create VPC
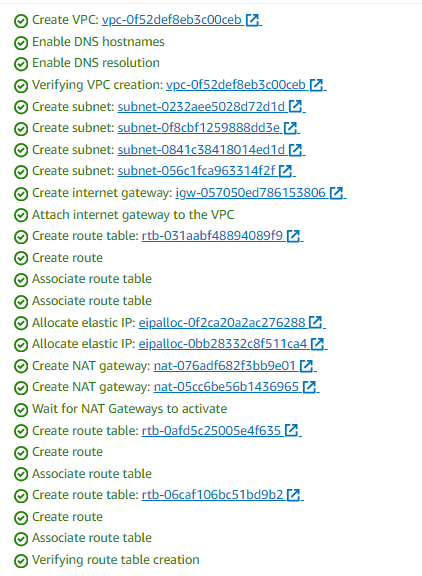
VPC is created successfully
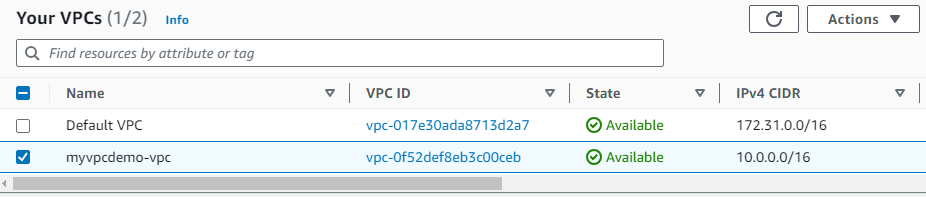
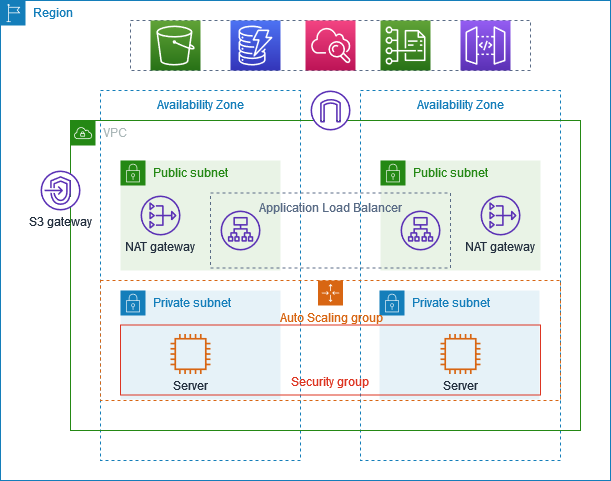
Autoscaling Group
Let's Create an Autoscaling group with EC2 instances
Navigate to EC2 and search for Autoscaling Groups

Click on Create Auto Scaling group
-Provide a name and create a launch template (if not created already)
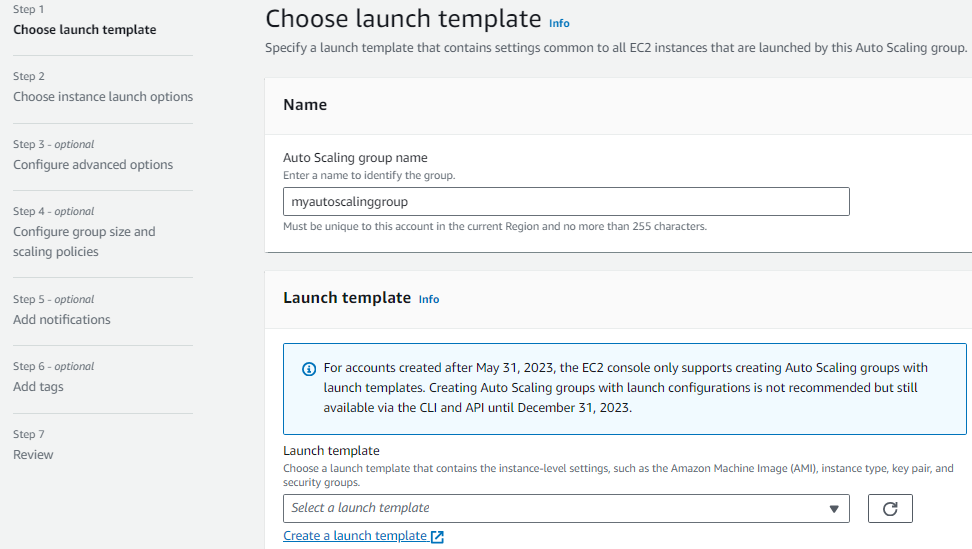
Creating a launch template

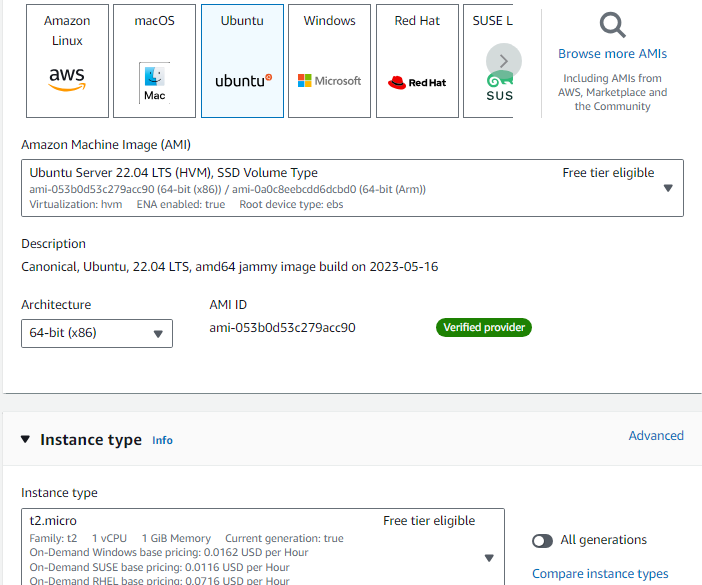
Choose the AMI and instance type and provide the aws pem key pair
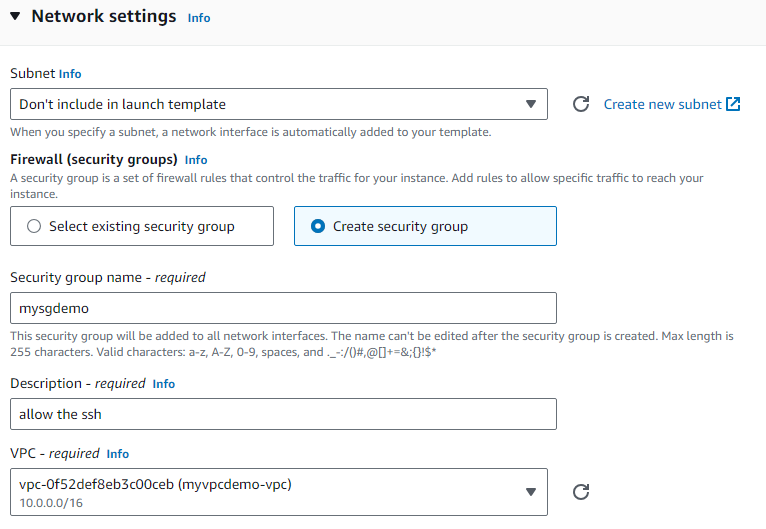
Create a new SG and allow the inbound, do not set and subnet.
Set the inbound rules for newly created SG i.e. SSH 20 to connect to the instance and 8000 for the Python application that we are going to deploy on these applications
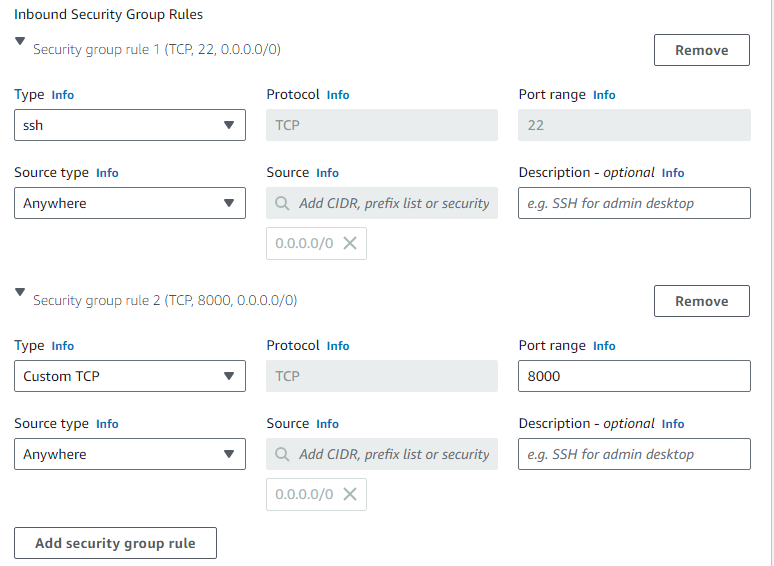
Leave the rest to defaults and create a Launch template

Now back to Auto Scaling Group and select the newly created launch template

Select the VPC and private subnets because we need our EC2 instance running in a private

No load balancer and no VPC LS
Set the Auto Scaling size for EC2 instances

Review and click on Create Auto Scaling group

By this, you will be creating 2 EC2 instances using Auto Scaling

We don't have any public IP for this instance by default (if you want to create a Public IP we can choose in network settings in the launch template), so we just use Bastion or bash host to connect to these instances using private IP.
Bastion Host
It is a normal EC2 instance that is created within the same VPC with SSH access and the same PEM key
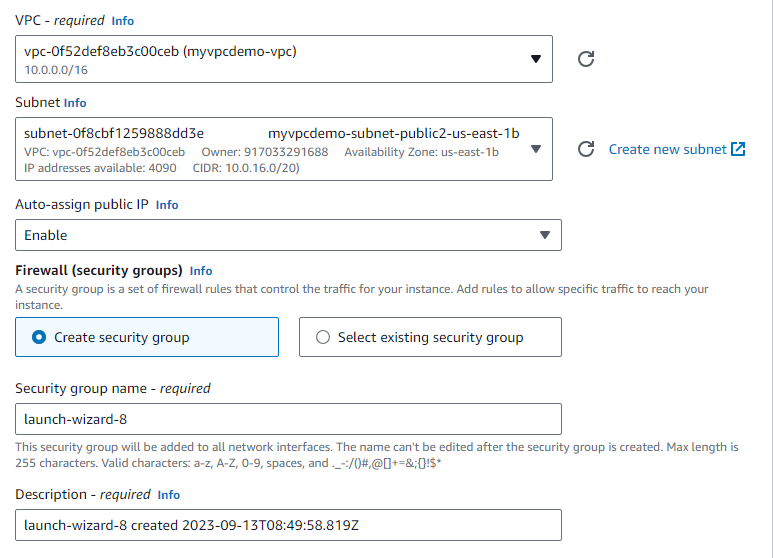
create an instance
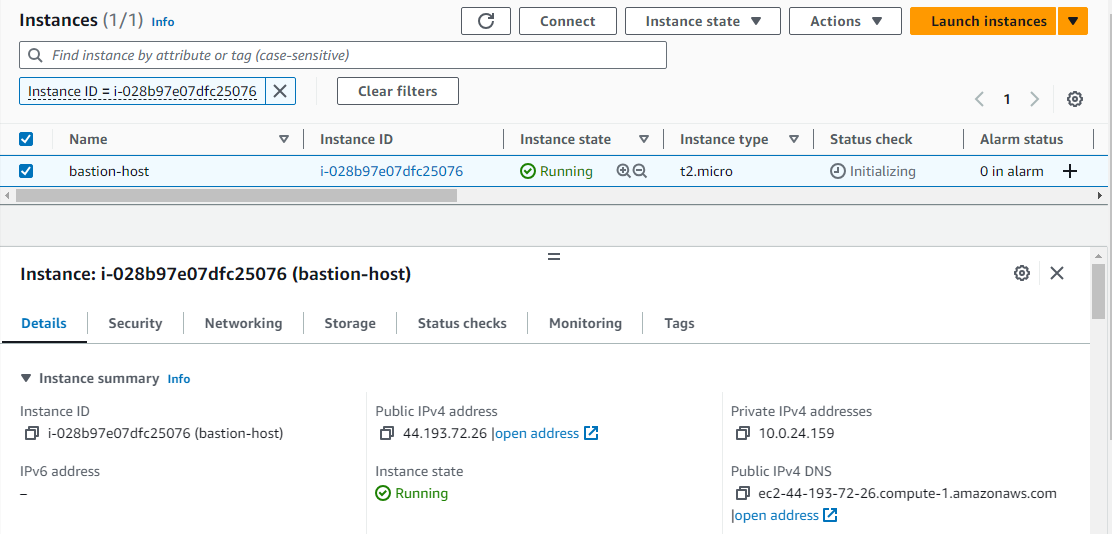
Now copy the pem file from the local to the EC2 instance using the scp command
scp -i "dontdelete.pem" "dontdelete.pem" ubuntu@ec2-44-193-72-26.compute-1.amazonaws.com:/home/ubuntu
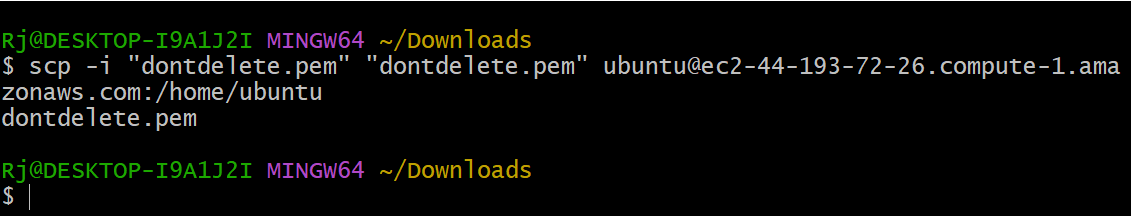
Connect to the Bastion instance and ssh to the other instances
chmod 400 <pemfile>
ssh -i <pemfile> ubuntu@privateip
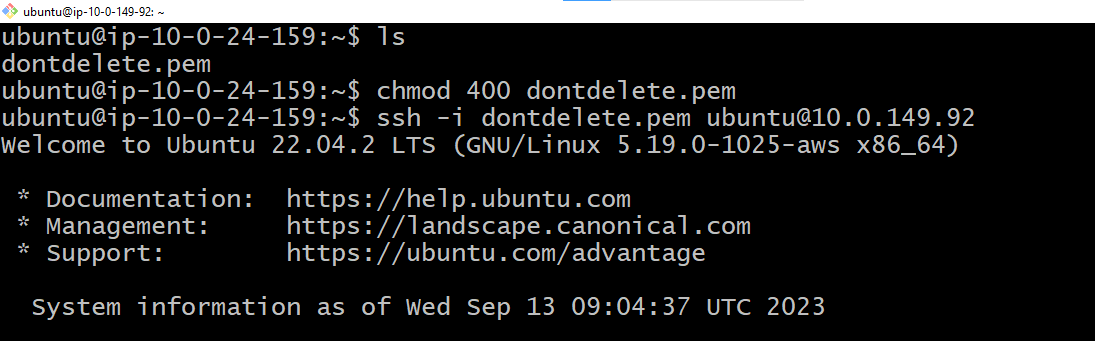
We have successfully connected to the instance with Private IP with ssh

Create an index.html file and install a simple Python application on port 8000

Now let's create a Load balancer to access the application
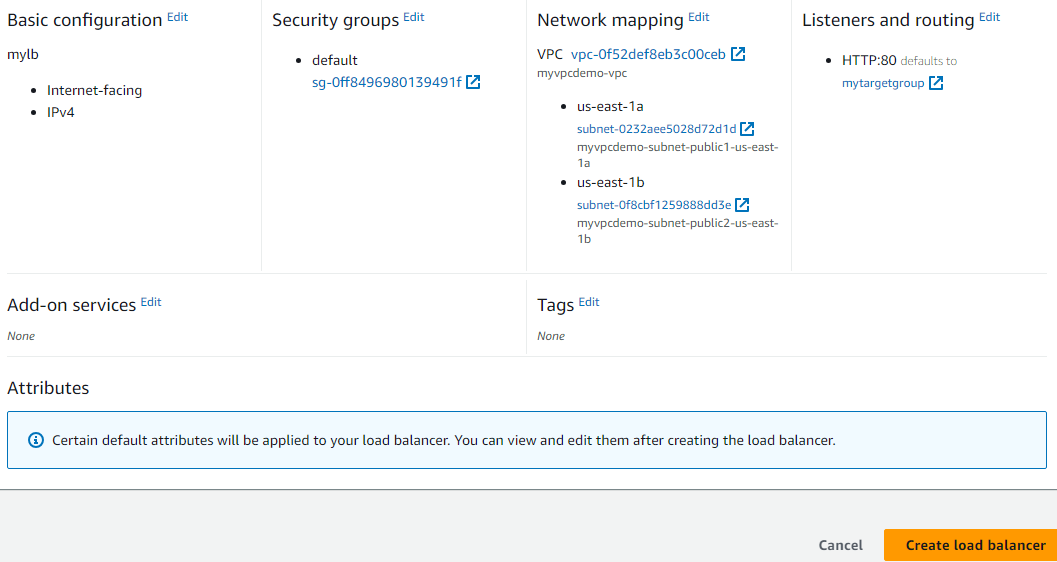
LoadBalancer > Application load balancer
Provide the name and scheme
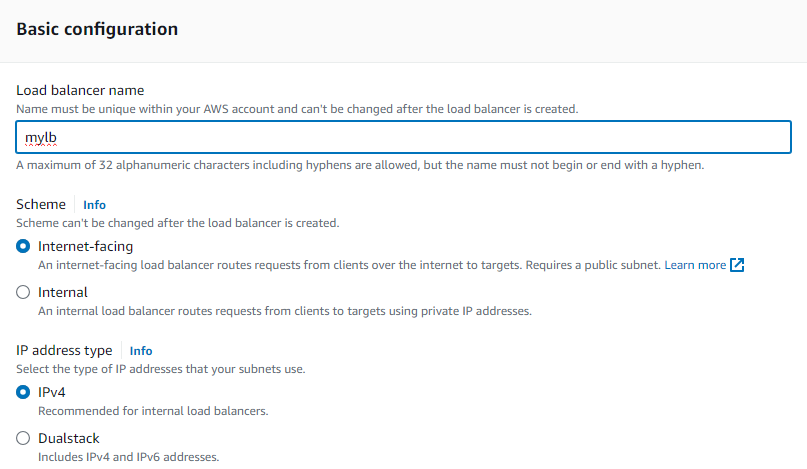
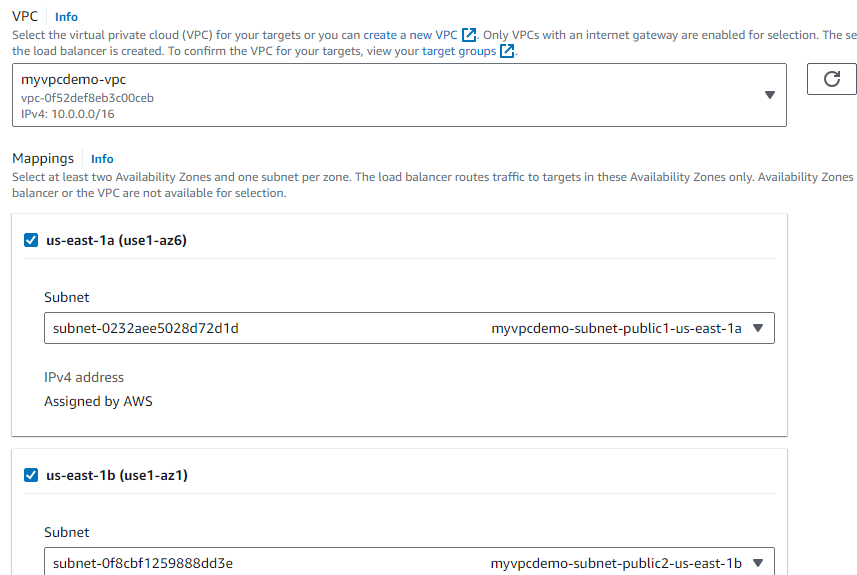
Choose the VPC with public subnets
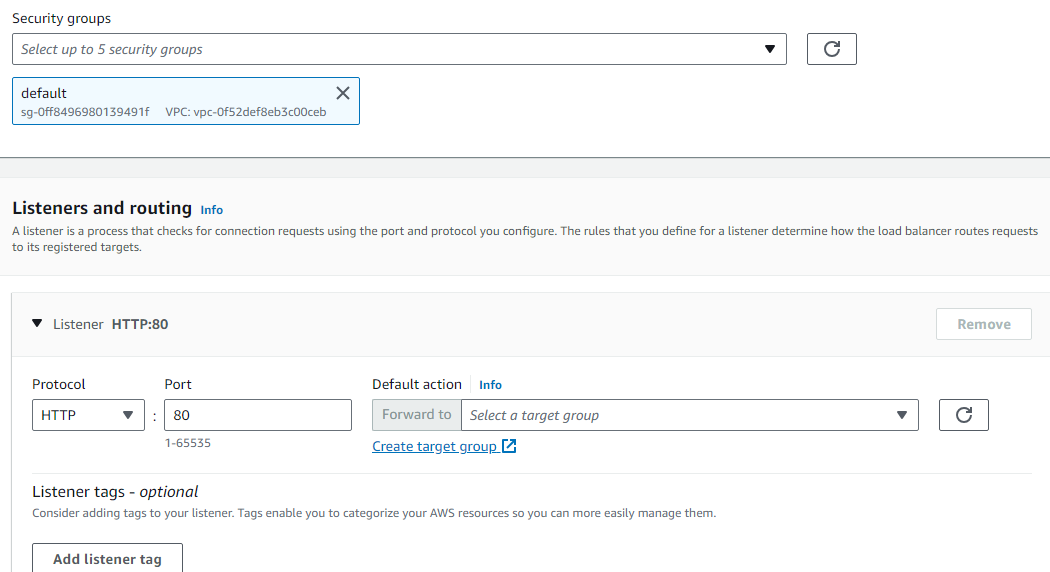
Apply the security group of VPC and LB always listens to port 80
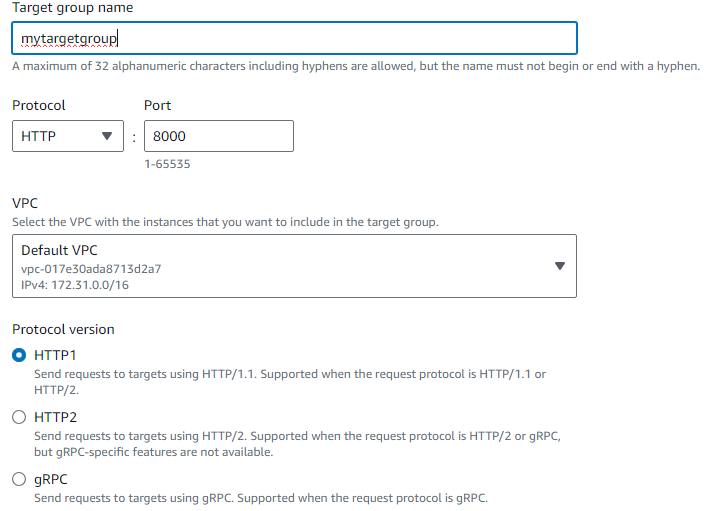
Create a target group of instances

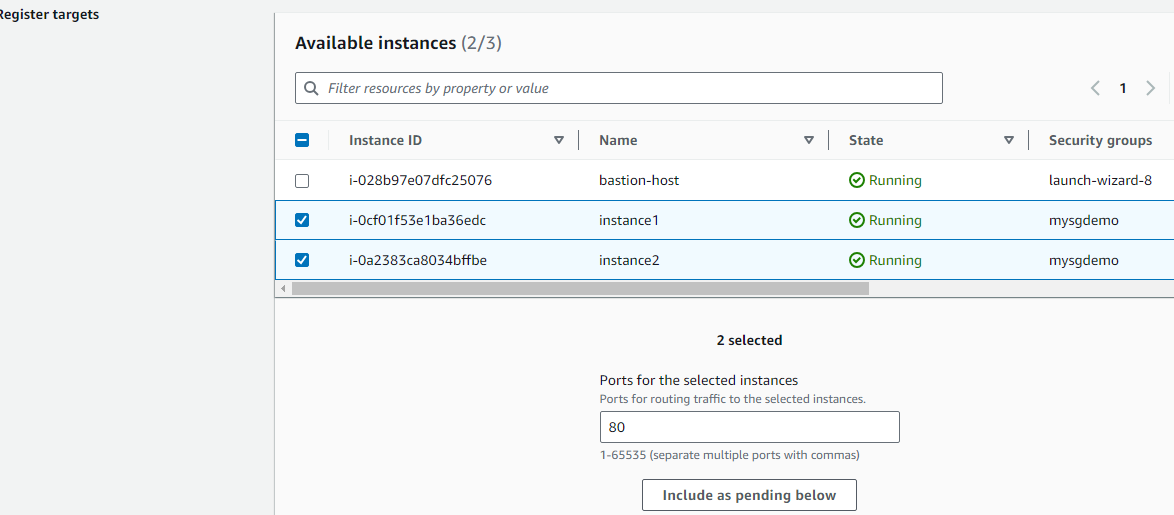
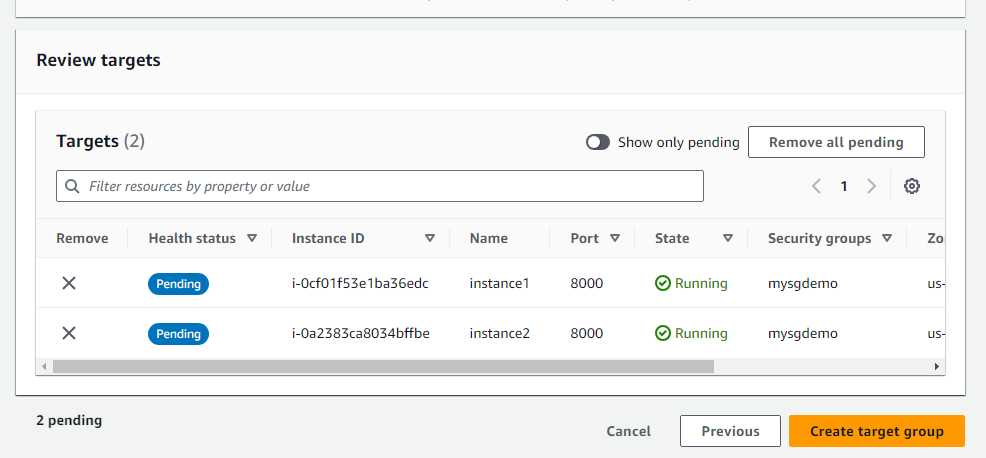
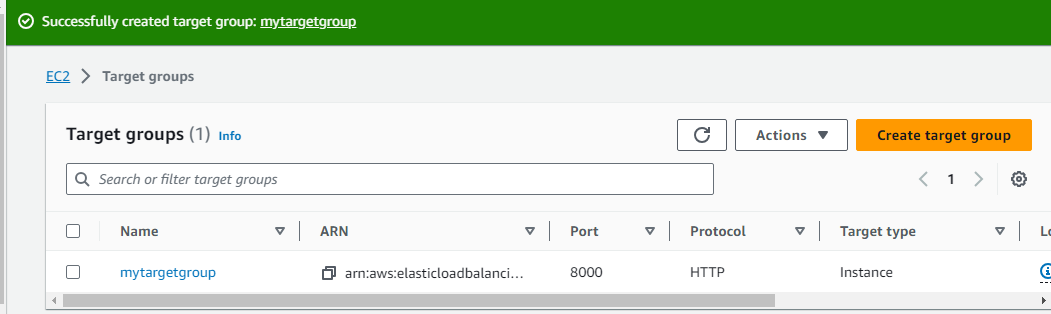
Back to LB and choose the newly created target group
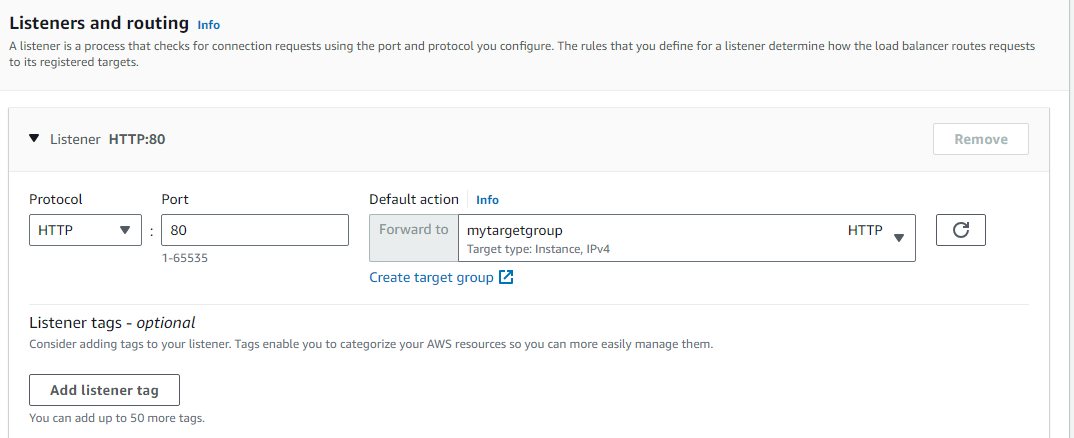

Copy the DNS name of LB and access in browser
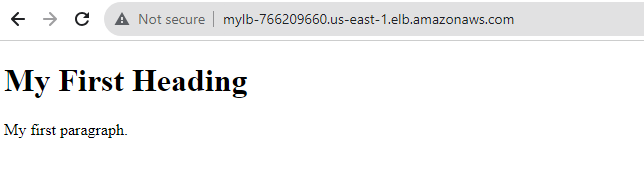
We have only created a python app in instance2 sometimes Lb any direct the traffic to instance1 and the application may not be accessible.
Subscribe to my newsletter
Read articles from Rajendra Thapa directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Rajendra Thapa
Rajendra Thapa
DevOps Engineer