Part 1: Manually Create Custom VPC
 TheAwsDev
TheAwsDev
Welcome to the first part of an ongoing mini-series which will result in the creation of network infrastructure for a multi-tier application:
We will manually configure a custom VPC, secure the network environment and add logging & auto remediation.
Part 1: Manually Configure a VPC
Part 2: Secure the Network Environment
Part 3: Launching Servers, Adding Logging/Auto Remediation
Our task today will be for the following scenario:
Scenario: Provision a small VPC for a client application that has a web server and app server. The client would like 1024 ip address reserved for future use and would like to make use of two availability zones for high availability.
Plan Architecture
We will plan our subnet CIDR blocks so that there are no overlapping IP addresses based on client specifications.
A subnet CIDR reservation is a range of IPv4 or IPv6 addresses that you set aside so that AWS can't assign them to your network interfaces. This enables you to specify IPv4 or IPv6 prefixes for use with your network interfaces.
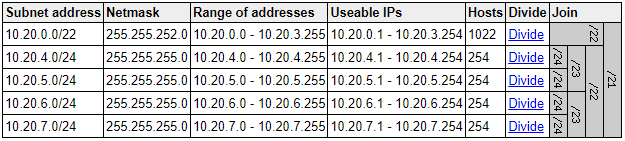
VPC Size: Small (2,046 Ip's)
Subnets:
1024 IP address reserved (/22)
2 Public Subnets of 254 (/24) in two different AZ's.
2 Private Subnets of 254 (/24) in two different AZ's.
Internet Gateway
NAT Gateway
Route Tables
The name of our project is SmallProjectA and we will utilize 10.20.0.0/21 (2048 ip addresses) as our CIDR block range.
Visual of our architecture
Let's get started:
Create VPC
A virtual private cloud (VPC) is a virtual network dedicated to your AWS account. It is logically isolated from other virtual networks in the AWS Cloud. You can launch your AWS resources, such as Amazon EC2 instances, into your VPC.
In the top left of the AWS Console click on search and enter VPC - Click VPC:
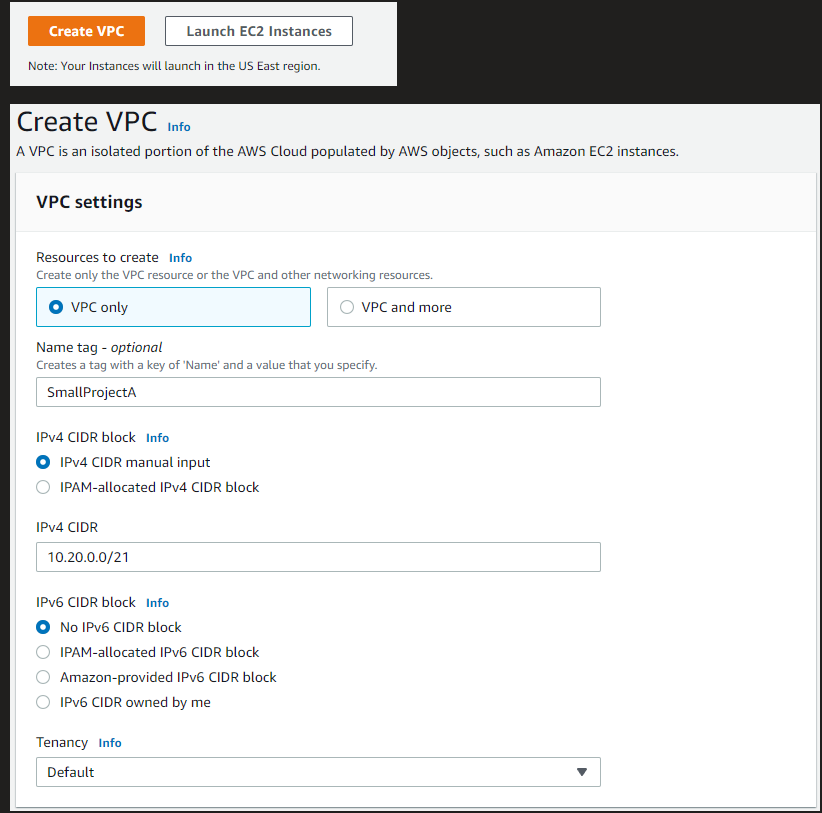
In the Create VPC screen enter the following:
VPC Only, SmallProjectA, 10.20.0.0/21 Ipv4 CIDR
No Ipv6 CIDR and Default tenancy:
Scroll to the bottom and click Create VPC:
Create Subnets
A subnet is a range of IP addresses in your VPC. You can launch AWS resources into a specified subnet. Use a public subnet for resources that must be connected to the Internet, and a private subnet for resources that won't be connected to the internet.
- In the left hand navigation pane of the VPC Dashboard, click Subnets.
- In the subnets dashboard, at the top right, click Create subnet:
On the Create subnet screen, select the recently created SmallProjectA V
PC:
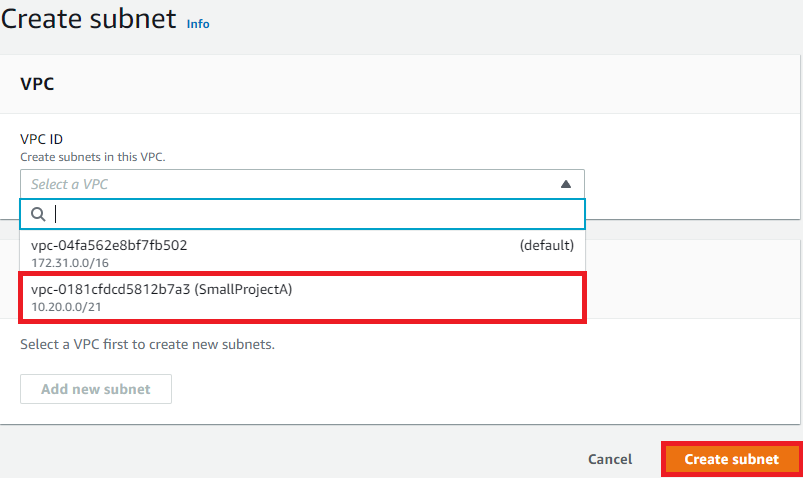
Once you select the SmallProjectA VPC, the Subnet settings screen will appear.
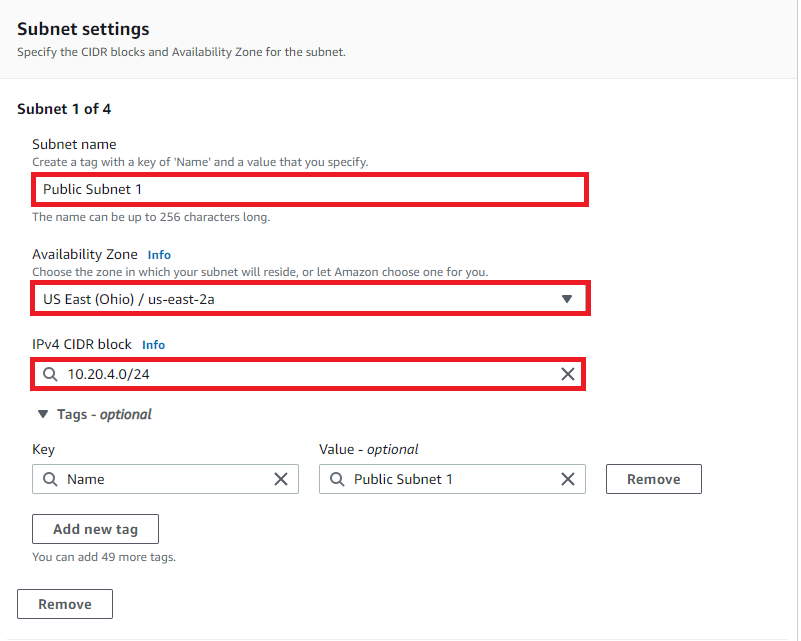
Populate the fields to create Public Subnet 1, Public Subnet 2, Private Subnet 1 & Private Subnet 2.
For the first Subnet Setting enter:
- Public Subnet 1, us-east-2a & CIDR block 10.20.4.0/24
Click Add Subnet:
For the second subnet setting:
- Enter Public Subnet 2, us-east-2b & CIDR block 10.20.5.0/24
Click Add new subnet:
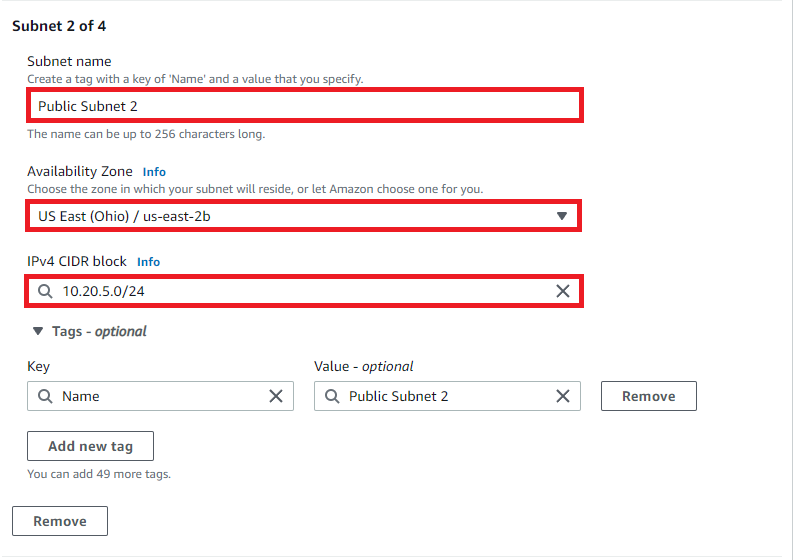
For the third subnet setting:
- Enter Private Subnet 1, us-east-2a & CIDR block 10.20.6.0/24
Click Add new subnet:
For the fourth subnet setting:
- Enter Private Subnet 2, us-east-2b & CIDR block 10.20.7.0/24
Click Create Subnet once completed:
Create Internet Gateway
An internet gateway enables resources in your public subnets (such as EC2 instances) to connect to the internet if the resource has a public IPv4 address
In the left-hand navigation pane of the VPC Dashboard click Internet Gateways:
Click Create internet gateway in the proceeding screen at the top right.
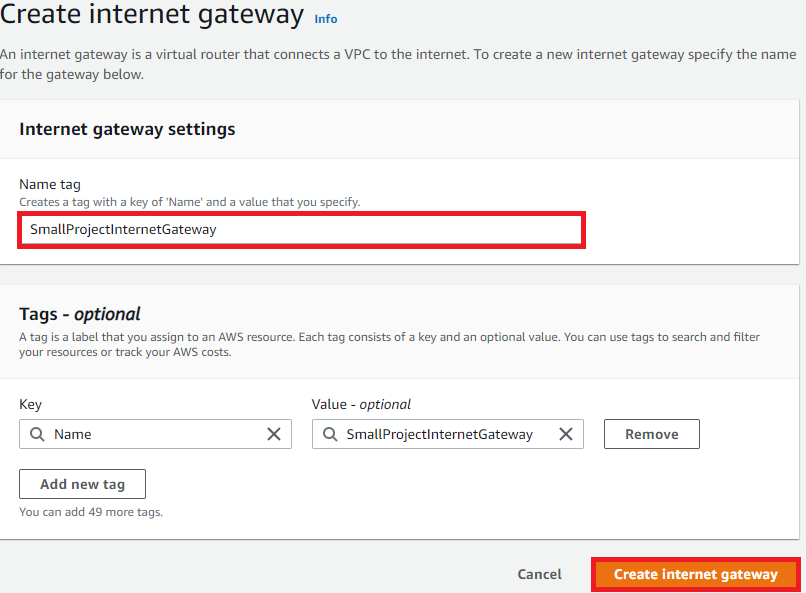
In Create internet gateway
- Enter SmallProjectInternetGateway as the name tag and select Create internet gateway:
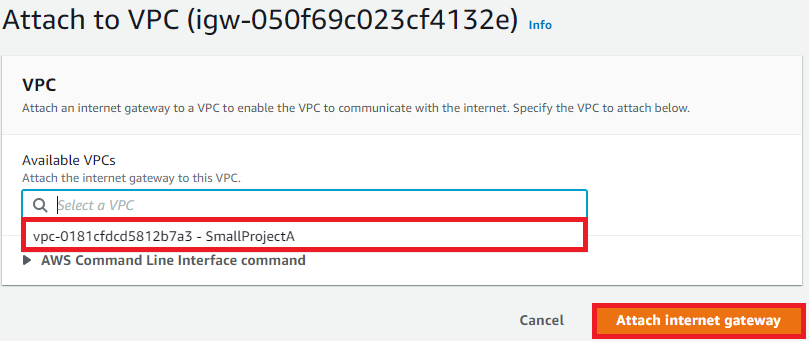
Once created, there will be a green banner at the top of the screen - Select Attach to a VPC:
- Attach to SmallProjectA:
Create NAT Gateway & Elastic IP
Instances in private subnets can connect to the internet through a public NAT gateway, but cannot receive unsolicited inbound connections from the internet. You create a public NAT gateway in a public subnet and must associate an elastic IP address with the NAT gateway at creation. You route traffic from the NAT gateway to the internet gateway for the VPC.

Before creating the NAT Gateway, we will allocate an Elastic IP.
In the left-hand navigation pane of the VPC Dashboard, click Elastic IPs:
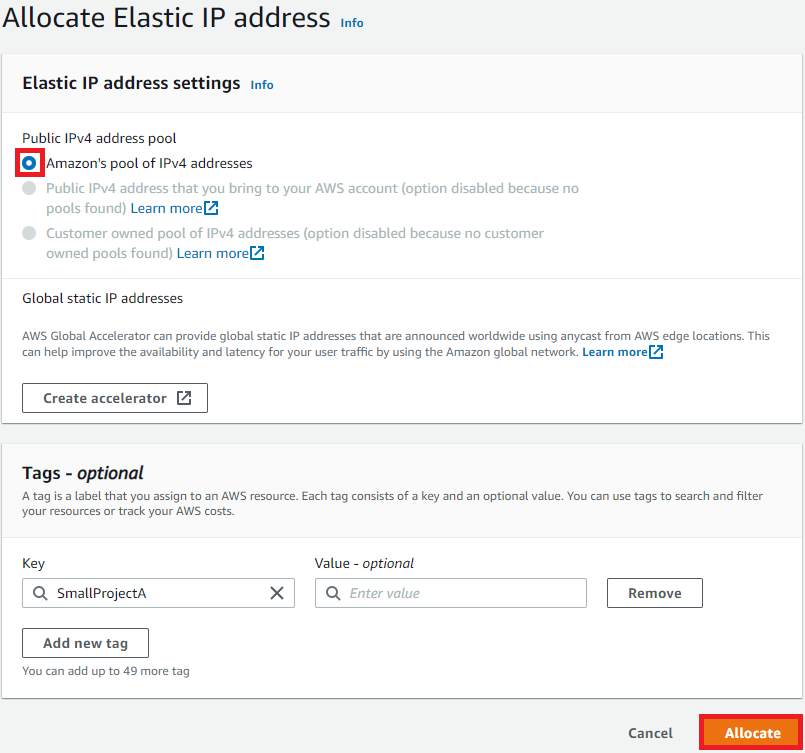
In the Elastic IP address dashboard, at the top right, click Allocate Elastic IP address:
Allocate Elastic IP address via Amazon's pool of Ipv4 addresses and select Allocate:

- In the left-hand navigation pane of the VPC dashboard, click NAT gateways:
In the NAT Gateway dashboard, at the top right, click Create NAT Gateway:
In the Create NAT gateway screen
Enter SmallProjectNATGateway as the name
Subnet: Public Subnet 1
Connectivity Type: Public
Elastic IP that we just generated
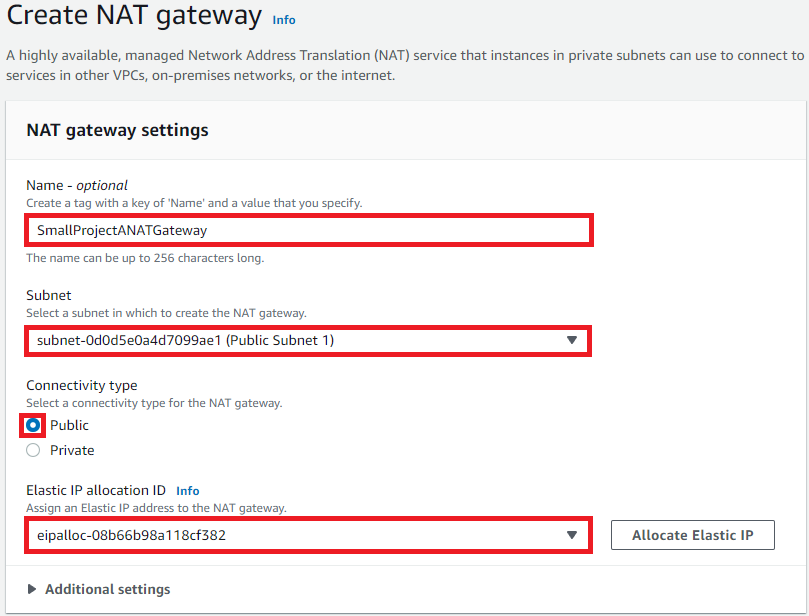
- Click Create NAT Gateway
Configure Route Tables and Routes
A route table contains a set of rules called routes which determine where traffic is directed. Each subnet in a VPC must be associated with a route table.
In this section, we will create route tables and routes to the NAT gateway & Internet gateway and associate the Private & Public subnets respectively.
Adding Route Table for Private Subnets
- In the left-hand navigation pane of the VPC dashboard, click Route Tables:
The Route tables dashboard will show all the Route tables in the current region.
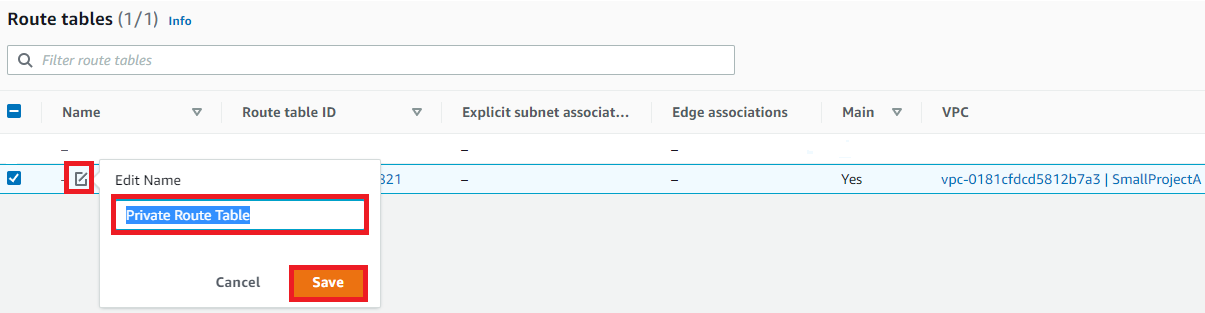
Select the default Route Table for SmallProjectA VPC
- Edit the name of the default Route Table via the Pen icon to: Private Route Table:
- With the Private route table selected, at the top right of the dashboard, click Actions > Edit Routes:
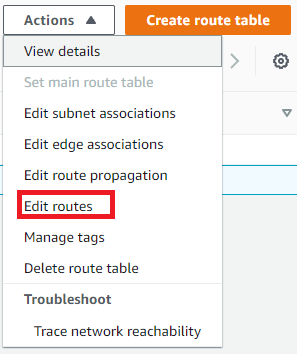
In Edit routes, select add route.
Enter destination 0.0.0.0/0
Targe: SmallProjectANATGateway
Save changes:
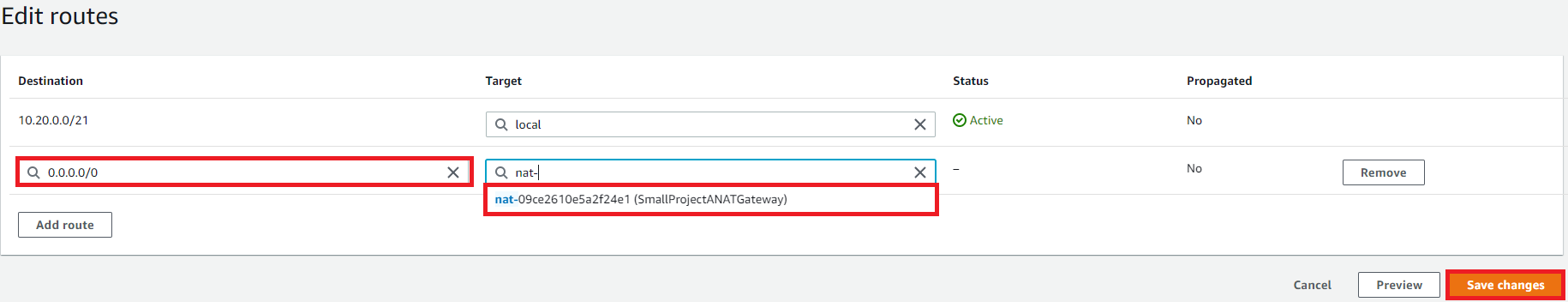
After saving changes, click the Subnet associations tab in the details section at the bottom of the Route tables dashboard (make sure private route table is selected) and select Edit subnet associations:
Select both Private Subnet 1 and Private Subnet 2 and Save associations:
Adding Route Table for Public Subnets
We will now create the Route Tables so that our Public Subnets can access the Internet via the Internet Gateway:
- In left-hand navigation pane of the VPC Dashboard, click Route Tables:
At the top right of the Route Tables dashboard, click Create route table:
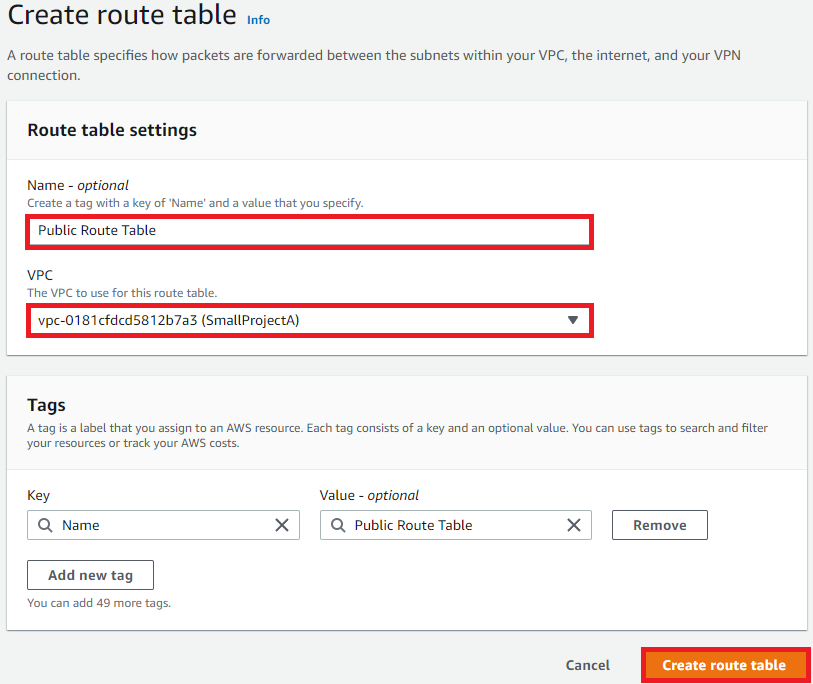
Enter Public Route Table as the name
Select SmallProjectA as the VPC
Click Create route table:
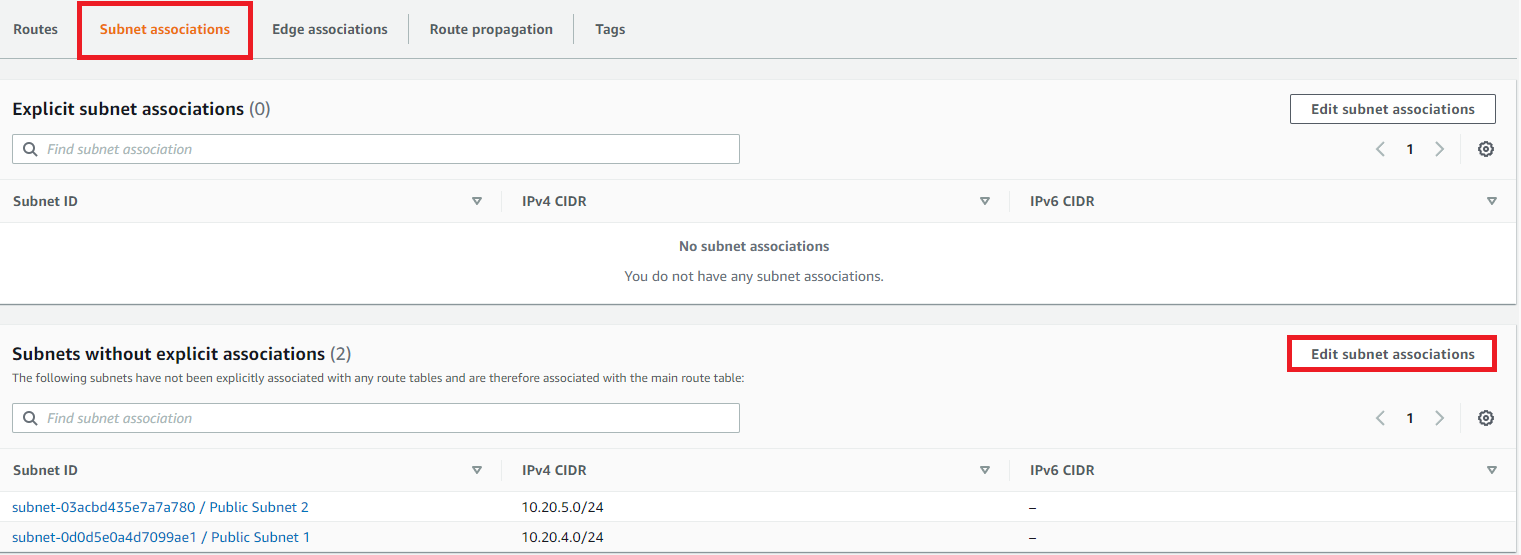
Ensure the newly created Public Route table is selected and in the details section at the bottom:
Click Subnet associations tab
Click edit Subnet associations:
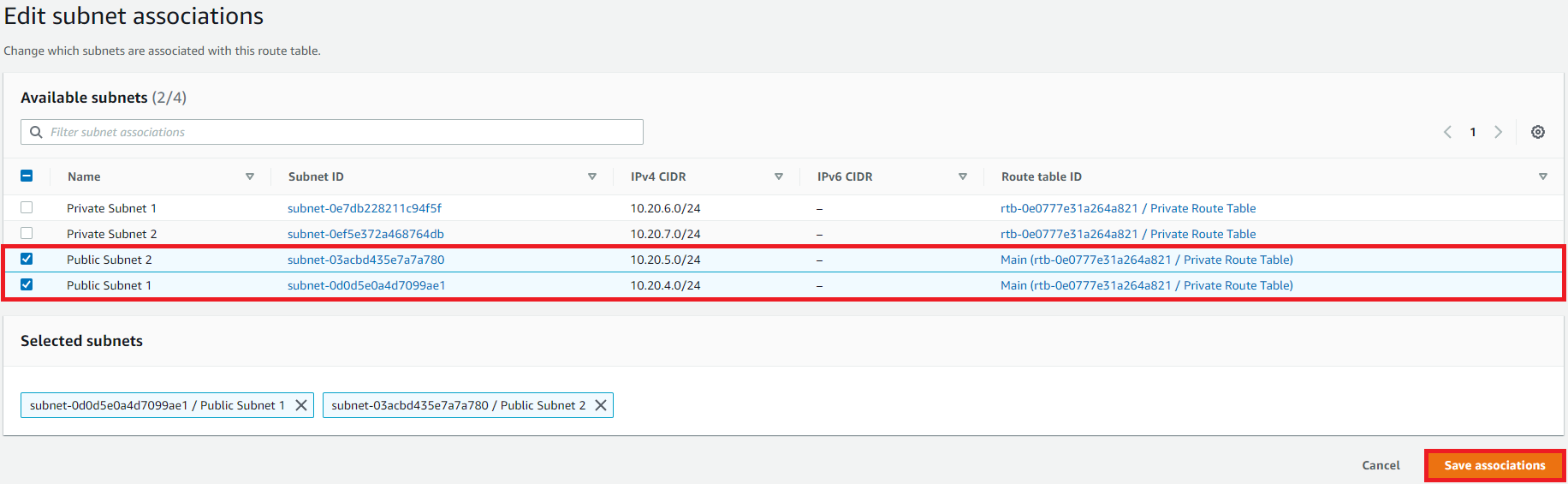
In Edit subnet associations
Select Public Subnet 1
Select Public Subnet 2
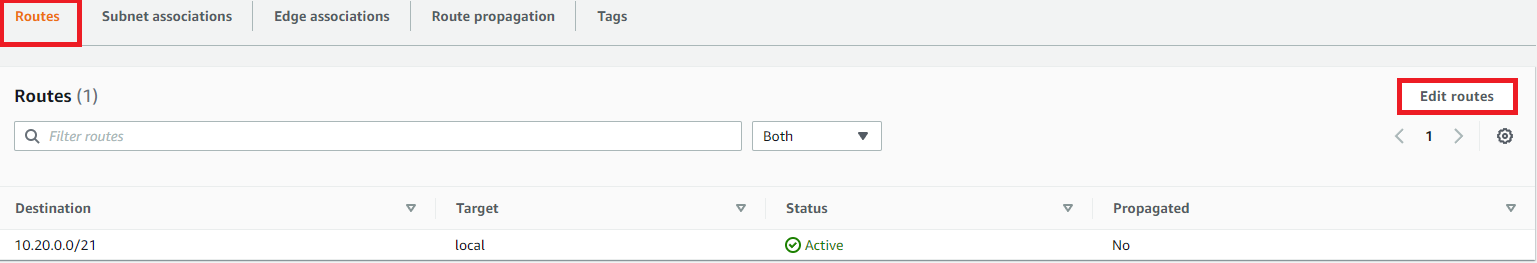
Ensure the Public Route table is selected and select the Routes tab
- Click Edit Routes:
In Edit routes
Click Add route: enter 0.0.0.0/0
Target: SmallProjectInternetGateway
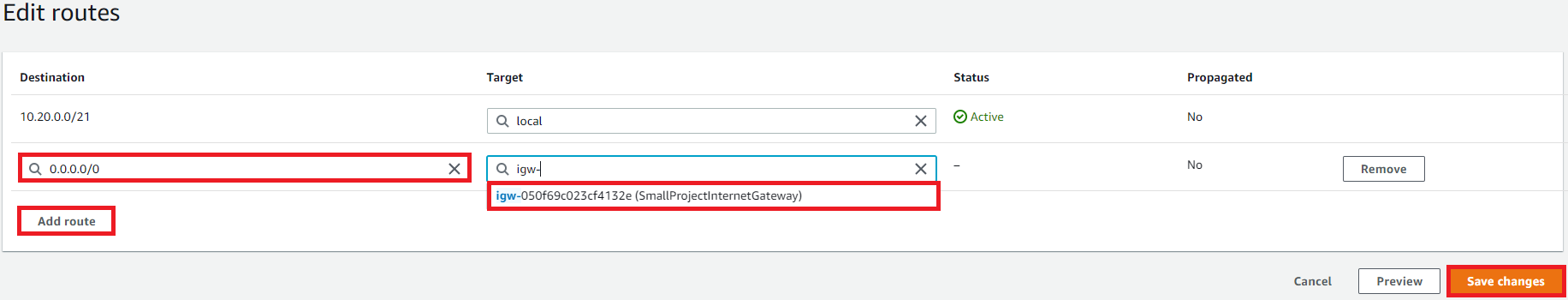

We have accomplished creating a custom VPC that has public and private subnets, an internet gateway and NAT gateway with associated route tables/subnets!!
In part 2 of this series, we will configure our security to secure our network environment. Till next time!
Subscribe to my newsletter
Read articles from TheAwsDev directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

TheAwsDev
TheAwsDev
No matter what field of study you embark on, there must be a phase in which you learn about learning, or rather, learning about how you learn. Throughout my journey into AWS, i've learned about learning (and still learning)...ideas from Richard Feynman and Tony Buzan to Aristotle, learning is ultimately how efficiently you utilize your mind-scape. Tools and techniques are to be explored, discovered or even created. As I journey through learning Cloud Developent, this blog is a tool to become immersed in the process. Hopefully, you will gain something along the way... "The capacity to learn is a gift. To learn is a skill. The willingness to learn is a choice.” - Brian Herbert