IPsec VPN: Understanding IKE Phase 2 Quick mode
 Jitin Tyagi
Jitin TyagiTable of contents

Prerequisites:
IPsec VPN: Understanding the IKE Phase 1 Main Mode
IKE Phase 2 | Quick mode
IKE phase 2 tunnel is also referred to as IPsec tunnel.
This tunnel will be used to protect user data and there is only 1 mode to build this tunnel and i.e. Quick mode.
Negotiation for the Phase 2 tunnel happens within the protection of our IKE Phase 1 tunnel so everything is encrypted and only the hash of the message contents (payloads & message ID) can be seen.
Only 3 messages are sent for Phase 2 tunnel negotiation.
It is unidirectional.

IKE Phase 2 parameters & payloads
The VPN peers will negotiate several parameters as follows:
| Parameter | Description |
| IPsec protocol | AH or ESP |
| Encapsulation mode | Transport or Tunnel mode |
| Encryption algorithm | DES, 3DES or AES |
| Authentication algorithm | MD5 or SHA |
| Lifetime | Validity of the IKE phase 2 tunnel & also the rekey timer |
| DH Exchange | It is optional i.e it is exchanged only if PFS is enabled |
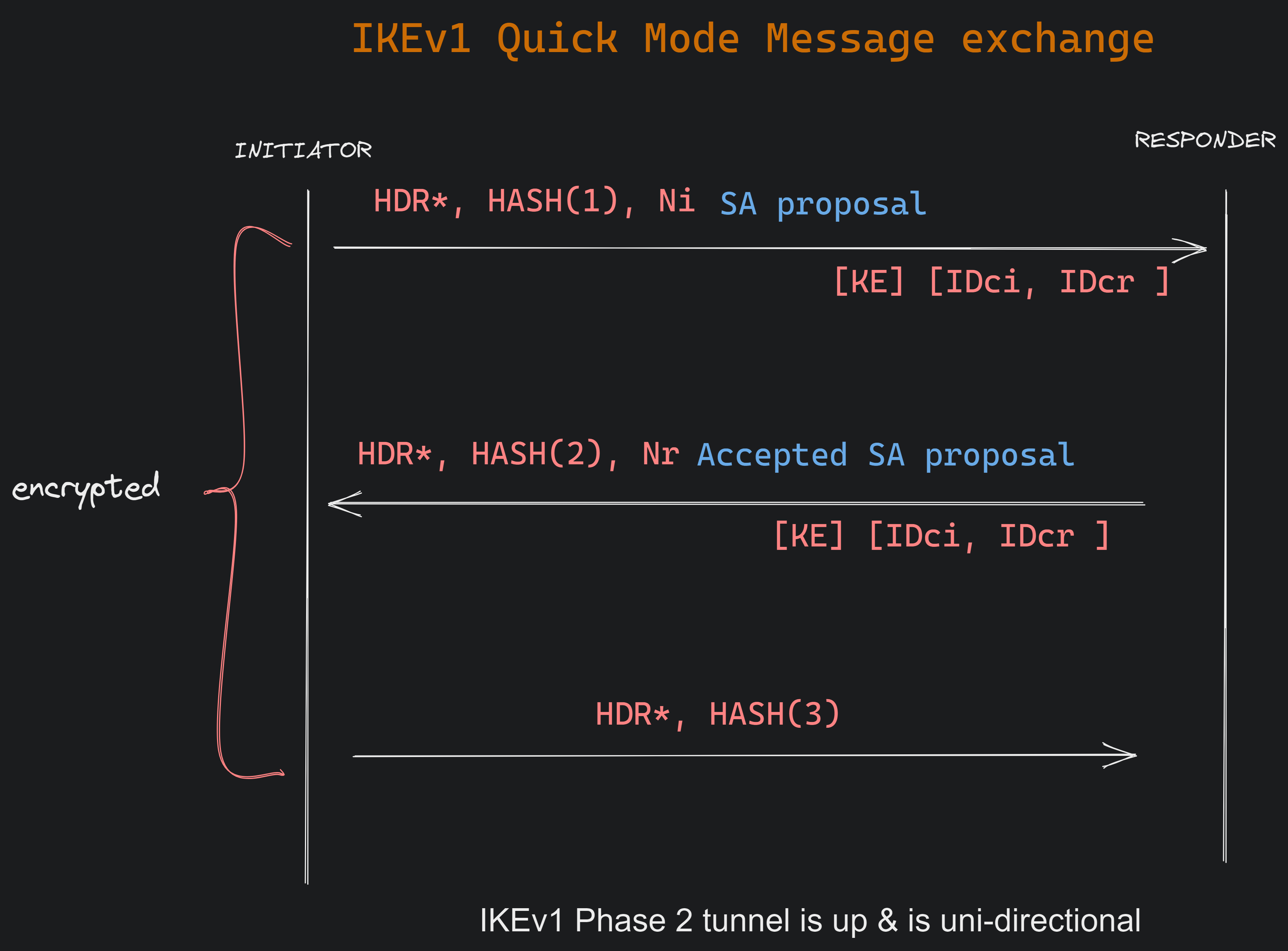
Where:
HASH(1) = prf(SKEYID_a, M-ID | SA | Ni [ | KE ] [ | IDci | IDcr )
HASH(2) = prf(SKEYID_a, M-ID | Ni_b | SA | Nr [ | KE ] [ | IDci | IDcr )
HASH(3) = prf(SKEYID_a, 0 | M-ID | Ni_b | Nr_b)
HASH(1) is the prf over the following parameters:
M-ID = message-id from the ISAKMP header but excluding any padding added for encryption
SA = security associations sent as a proposal.
Ni = Nonce of Initiator which is just a random number used once.
KE = Key exchange payload
IDci = client ID of the initiator
IDcr = client ID of responder
HASH(2) is identical to HASH(1) except the initiator's nonce-- Ni is added after M-ID but before the complete message. The addition of the nonce to HASH(2) is for liveliness proof.
HASH(3) is the prf over the following parameters:
value zero represented as a single octet,
M-ID = message id
Ni_b = Nonce of Initiator
Nr_b = Nonce of responder
Pseudo-Random Function | PRF
PRF uses an algorithm to generate pseudo-random content utilizing certain parameters/arguments for the creation of keying material and can be calculated:
Periodically - after a negotiated interval of time i.e. the lifetime value negotiated in Quick mode messages 1 and 2.
Triggered - required re-keying event or for integrity check function.
Perfect Forward Secrecy | PFS
In IKE Phase 1, DH key values are exchanged to derive a DH shared secret. Further, this shared secret along with the SKEYID is used to generate session keys to encrypt 5th and 6th Main mode messages and also the IKE Phase 2 messages.
When using pre-shared keys:
SKEYID = prf(pre-shared-key, Ni_b | Nr_b)
The SKEYID value along with the DH Shared Secret (and a few other values) are used to create three session keys:
| Key name | Key variable | Description |
| Derivative key | SKEYID_d | handed over to IPsec to create its own Secret Keys |
| Authentication key | SKEYID_a | used by ISAKMP in its HMAC |
| Encryption key | SKEYID_e | used by ISAKMP to symmetrically encrypt anything ISAKMP wants to securely to the other peer |
The above keys are derived as follows:
SKEYID_d = prf(SKEYID, g^xy | CKY-I | CKY-R | 0)
SKEYID_a = prf(SKEYID, SKEYID_d | g^xy | CKY-I | CKY-R | 1)
SKEYID_e = prf(SKEYID, SKEYID_a | g^xy | CKY-I | CKY-R | 2)
Without PFS
If PFS is disabled then additional DH Key Exchange payloads are not exchanged during Phase 2 or Quick mode message exchange and the keying material is defined as:
KEYMAT = prf(SKEYID_d, protocol | SPI | Ni_b | Nr_b).
With PFS
If PFS is enabled then additional DH Key Exchange payloads are exchanged and the keying material is defined as:
KEYMAT = prf(SKEYID_d, g^xy | protocol | SPI | Ni_b | Nr_b)
where g^xy is the DH shared secret from the temporary or short-lived DH key exchange of this Quick Mode.
So when PFS is enabled, the keying material is defined using both:
SKEYID_d = Derived session key from Phase 1
g^xy = DH shared secret made using forced key exchange in Phase 2 / Quick mode.
NOTE: In either case, "protocol" and "SPI" are from the ISAKMP Proposal Payload that contained the negotiated Transform set.
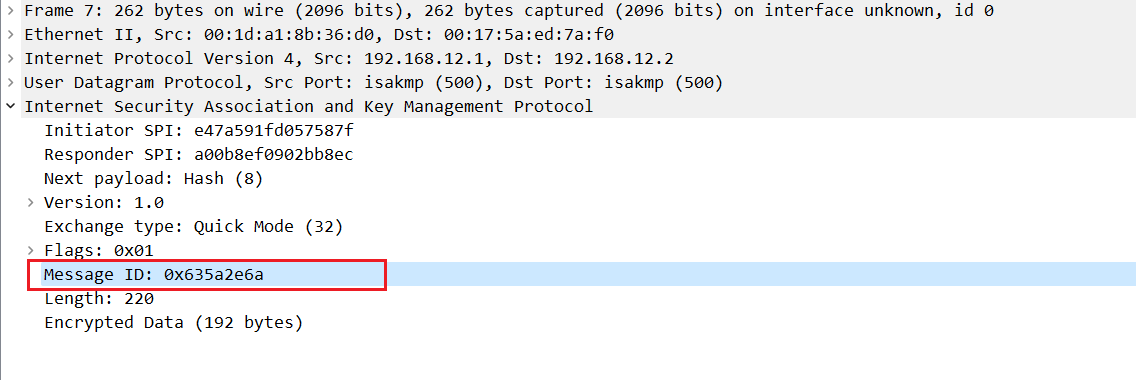
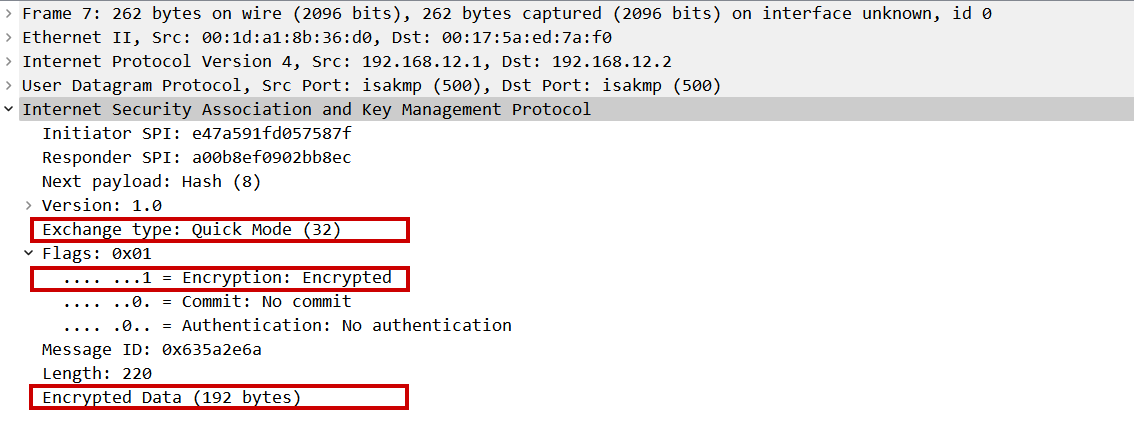
Packet capture analysis
Spoiler: Nothing much to see here as these messages are encrypted.
Quick mode message 1:
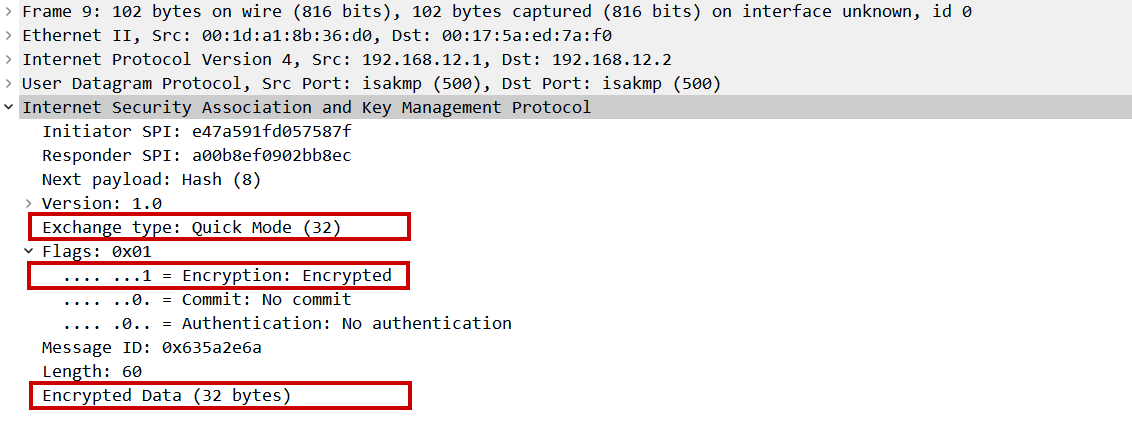
Quick mode message 2:
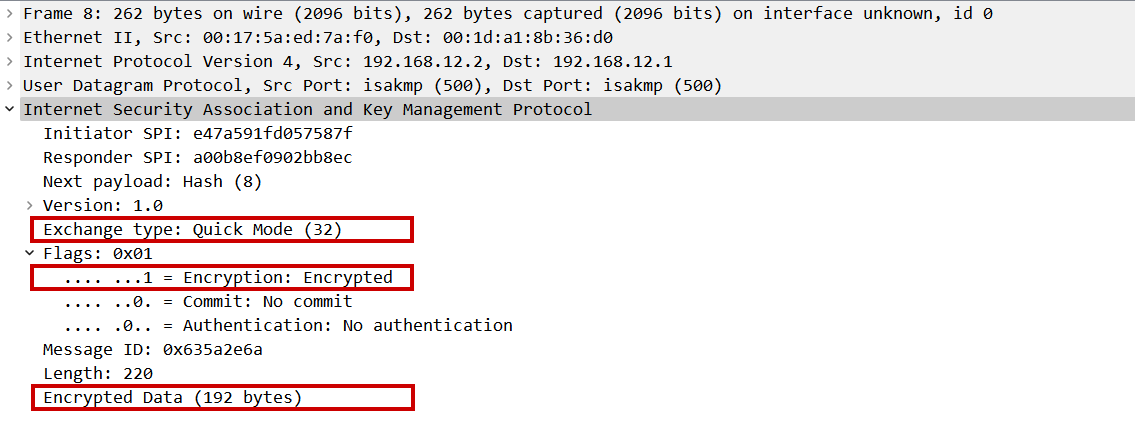
Quick mode message 3:
References:
Subscribe to my newsletter
Read articles from Jitin Tyagi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
Jitin Tyagi
Jitin Tyagi
CCNP SCOR | CCNP ENCOR | CCNA 200-301 | FORTINET NSE-1,2