Exploring the Need for a Widely Adopted API Protocol in the Cyber Industry
 Daniel Haven
Daniel Haven
The cyber industry's rapid growth has revolutionized how we live and work, ushering in a new era of connectivity and digital innovation. However, despite the industry's advancements, a widely adopted API (Application Programming Interface) protocol specifically designed for the cyber domain is noticeably absent.
The Power of Established Protocols
Several industries have successfully embraced standardized API protocols, leading to improved interoperability, seamless integration, and accelerated innovation. Let's take a closer look at some widely adopted examples:
1. LTI (Learning Tools Interoperability)
LTI has revolutionized the education technology sector by enabling learning management systems (LMS) and educational tools to communicate and integrate effortlessly. This standard has nurtured a dynamic ecosystem of educational applications, empowering educators and students with a diverse range of tools and resources.
2. HL7 (Health Level Seven)
In the healthcare industry, HL7 plays a crucial role in facilitating electronic health information exchange. This standardized protocol ensures interoperability between various healthcare systems, enabling efficient and secure sharing of patient data. HL7 has been instrumental in advancing healthcare delivery and enabling collaborative care.
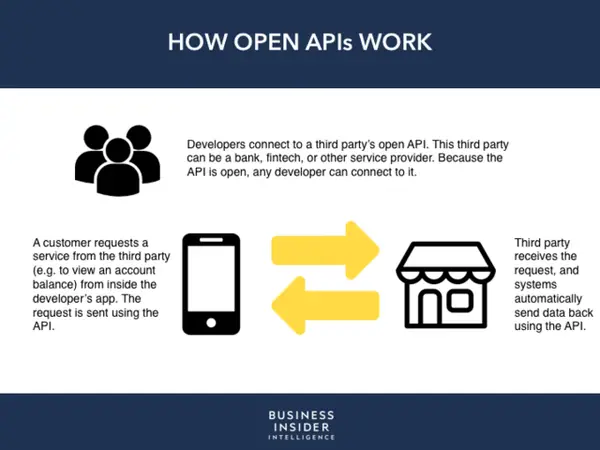
3. Open Banking APIs
Open Banking APIs have transformed the financial industry by enabling secure and standardized access to customer data. These APIs have empowered customers with greater control over their financial information and facilitated the emergence of innovative fintech services. The standardized protocols have fostered competition and improved customer experiences across the financial landscape.
The Cyber Industry's API Protocol Gap
Despite the success of established API protocols in other domains, the cyber industry still needs a widely, universally adopted protocol. This gap can be attributed to several factors:
1. Heterogeneous Landscape
The cyber industry encompasses diverse sectors, including cybersecurity, network infrastructure, cloud services, and more. This landscape's complex and heterogeneous nature makes it challenging to develop a one-size-fits-all API protocol that effectively meets the diverse requirements and intricacies of each sector.
2. Rapidly Evolving Threat Landscape
Cybersecurity is an ever-evolving field, with new threats and vulnerabilities constantly emerging. Developing a standardized API protocol amidst this dynamic landscape presents a significant challenge. Striking a balance between flexibility and security becomes crucial to ensure the protocol's longevity and effectiveness.
3. Lack of Collaboration and Standardization
Unlike other sectors, the cyber industry has seen limited collaboration and standardization efforts regarding API protocols. The absence of a unified approach impedes interoperability, stifles innovation, and hampers the industry's ability to respond collectively to emerging challenges.
The Potential Benefits of Dedicated API Protocols
While the absence of a widely adopted API protocol in the cyber industry presents challenges, there are several potential benefits to examine :
1. Enhanced Interoperability
A dedicated API protocol would facilitate seamless integration between different cybersecurity solutions, allowing organizations to leverage multiple tools more effectively. This interoperability would streamline workflows, improve incident response, and enhance overall cybersecurity posture.
2. Accelerated Innovation
A standardized API protocol could foster a vibrant ecosystem of cybersecurity applications and services. Developers could build on a shared foundation, accelerating the creation of innovative solutions to address emerging threats. Collaboration and knowledge sharing would thrive within a standardized framework.
3. Improved Threat Intelligence Sharing
An efficient and secure exchange of threat intelligence is vital in the fight against cyber threats. A widely adopted API protocol would enable standardized threat intelligence sharing across organizations and sectors, bolstering collective defense and enabling proactive threat mitigation.
The Potential Drawbacks of Dedicated API Protocols
1. Security Concerns
Standardized API protocols inherently pose security risks. A single vulnerability or flaw in the protocol could have far-reaching consequences, potentially exposing critical systems and sensitive data to cyberattacks. Developing a secure and resilient protocol would be paramount to mitigate these risks effectively.
2. Compatibility Challenges
Introducing a new API protocol would require compatibility with existing systems and technologies. Organizations heavily invested in legacy infrastructure may face challenges in adopting and transitioning to the new protocol. The need for backward compatibility and seamless migration paths must be addressed to minimize disruption and facilitate a smooth transition for organizations relying on legacy infrastructure.
3. Balancing Flexibility and Standardization
The cyber industry thrives on flexibility and adaptability to address evolving threats. Striking a balance between a standardized API protocol and the need for customization and flexibility could be a significant challenge. Finding the right level of standardization without stifling innovation and hindering unique solutions is a delicate task.
Let’s pave the way for a standardized API protocol
As the cyber industry continues to grow and evolve, the absence of a widely adopted API protocol becomes increasingly conspicuous. While other industries have successfully embraced standardized protocols such as LTI, HL7, and Open Banking APIs, the cyber industry faces unique challenges that hinder the development of a unified protocol.
Nonetheless, the benefits of enhanced interoperability, accelerated innovation, and improved threat intelligence sharing make a strong case for pursuing a dedicated API protocol. By addressing the industry's specific needs, fostering collaboration, and prioritizing security, the cyber industry can pave the way for a standardized API protocol that empowers organizations to safeguard the digital landscape confidently.
What are your thoughts on the need for a widely adopted API protocol in the cyber industry? How do you envision the benefits and challenges of such a protocol?
Share your insights and join the discussion below.
From real-time IAM Policy generation to rightsizing permissions based on your code and direct IaC recommendations, Slauth.io works to save time and reduce your organization's attack surfaces. Learn more about our automated IAM policy creation for your AWS services today.
Subscribe to my newsletter
Read articles from Daniel Haven directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
