Understanding Farcaster: Part 1; Identity Generation and Authentication
 Aditi Polkam
Aditi Polkam
In the digital age, social media has become an integral part of our lives, transforming the way we interact, share, and perceive the world around us. However, the traditional landscape of social media has its fair share of challenges, including data privacy concerns, content manipulation, and the dominance of a few centralized platforms. But what if there was a way to revolutionize this system? Enter decentralized social media – a groundbreaking concept that has the power to reshape how we handle social identity and content across multiple platforms.
The decentralized approach to social media promises to foster an unprecedented level of transparency, privacy, and autonomy for users, heralding a new era of digital interaction. While decentralized social media holds great promise, it also comes with its fair share of challenges.
Identity Verification Across Platforms
Authentication of Messages
Content Availability Across Platforms
Consistency in Rules and Moderation
Creation of trustworthy identities
Remembering a long and complex wallet address can indeed be quite challenging for users in the realm of decentralized finance and blockchain-based platforms. As we seek more user-friendly solutions, the idea of adopting a naming system akin to domain names and IP addresses holds considerable promise. However, we must tread carefully, as this approach presents a unique challenge - the possibility of identity squatting and impersonation.
Users could have a personalized and easy-to-remember username, like @yourname, associated with their wallet address. This would undoubtedly enhance the overall user experience, promoting broader adoption of decentralized applications and platforms. Yet, the catch lies in ensuring the security and authenticity of these usernames. In a decentralized system, there's no central authority governing username allocation, making it susceptible to identity theft and malicious actors. Imagine a scenario where someone manages to secure a coveted username like @twitter. They could potentially exploit this privileged position, masquerading as Twitter's official account and misleading users for malicious purposes. This could lead to scams, misinformation, and significant reputational damage to legitimate entities.
How does Farcaster come into the picture?
By leveraging blockchain technology, Farcaster introduces a secure and privacy-centric approach, empowering users with full control over their digital identities. Below are some of the key benefits Farcaster brings to the world of decentralized social identities:
Self-Sovereign Identities owned and controlled by users.
Unique Farcaster ID (FID) upon registration for ensuring seamless interactions across various decentralized applications without the need for repetitive account creation.
Human-Readable Farcaster Name (Fname) associated with FID simplifies the process of identification and enhances user experience.
Enhanced Security with Signers eliminating the need for users to expose their custody address's private key.
Account Recovery by setting up a designated recovery address to regain control of the accounts in case of compromise or loss of access.
Farcaster promotes interoperability among decentralized applications, enabling users to seamlessly navigate various platforms with a single set of credentials and data availability amongst various platforms.
Farcaster Identities
Farcaster maintains a dual identification system comprising a primary identifier known as the Farcaster ID (FID) and a secondary identifier known as the Farcaster Name (FName).
Farcaster ID (FID): The Farcaster ID issued by the ID Registry serves as the primary and fundamental identifier for users within the decentralized ecosystem. It is a cryptographically secure and globally unique identifier assigned to each user upon registration. The FID plays a critical role in facilitating secure transactions, interactions, and record-keeping on the Farcaster network. By using cryptographic techniques, the FID ensures that users can be identified and verified without relying on a central authority, maintaining the core principles of decentralization.
Farcaster Name (FName): Recognizing the challenge of remembering long and complex FIDs, Farcaster introduces Farcaster Name (FName) as a user-friendly, human-readable alternative. This FName issued by the Name Registry allows users to create personalized and memorable names associated with their FIDs. For example, a user with FID "0x1a2b3c4d5e6f" could choose the FName "@username" for easier identification by other users on the platform. To ensure the integrity and security of the FName system, Farcaster employs a partially centralized service responsible for the allocation and management of FNames. This authority follows stringent protocols to prevent misuse, cyber-squatting, or impersonation. The allocation process is designed to be transparent, fair, and safeguarded against abuse, while also protecting the privacy of users' underlying FIDs.
Farcaster Authentication
Authentication in web3 decentralized applications (dApps) operates on a fairly simple and secure premise. When using web3 dApps, the apps request users to sign messages using their private keys through their wallets. This process is fundamental to proving ownership and control over a specific blockchain address.
However, introducing third-party social media apps into the equation adds a layer of complexity and potential risk that users must be cautious about. These apps may request users to load their private keys into the application to facilitate the signing process. Doing so poses significant dangers, as sharing private keys with third-party services compromises the security of the user's funds and identity.
The Farcaster protocol introduces a novel approach to message signing by creating a separate signer public-private key pair. Now whenever the sender wants to send a message the social media app signs it using the signer already created. This innovative method enhances security and privacy by eliminating the need to use the sender's private key for signing messages. Consequently, the public address associated with the sender is now referred to as the "custody address."
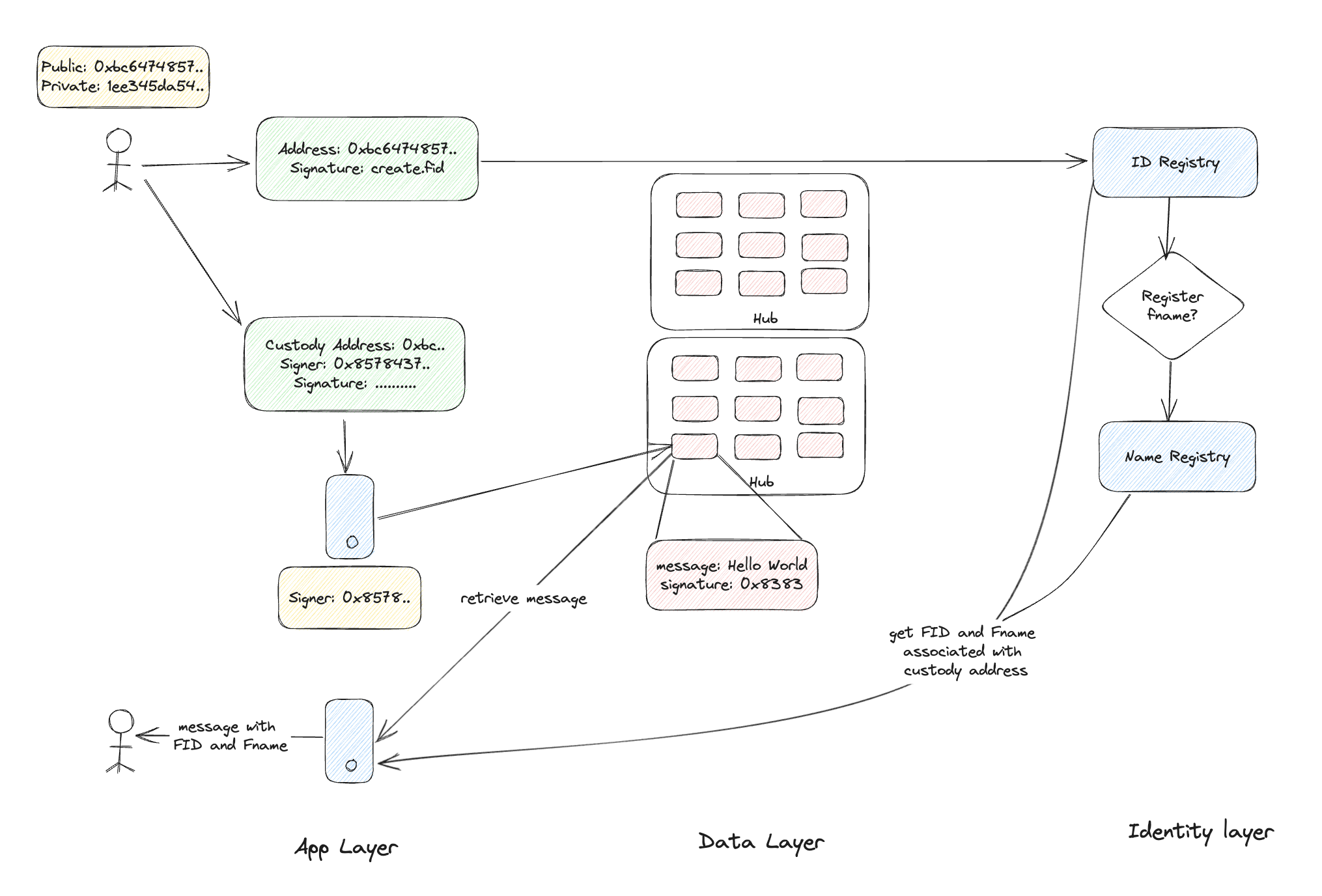
When a user logs into any messaging app built on the Farcaster platform, two essential tasks are initiated to establish their identity and enable secure communication. Firstly, the app generates a unique Farcaster ID (FID) and Farcaster Name (Fname) for the user, utilizing the ID Registry and Name Registry on the Identity Layer. If the user does not already have an FID and Fname, this transaction creates them, ensuring a distinct and verifiable identity within the Farcaster network.
Subsequently, the app generates a new signer on the App Layer for the user. This signer serves as a cryptographic key pair, securely stored locally on the user's device. Its primary function is to sign messages on behalf of the user, providing a secure means of authentication without requiring the user's custody address's private key. Each application within the Farcaster ecosystem generates its own unique signer for the user, maintaining isolation and security between different applications.
Once the messages are signed by the user's signer, they are transmitted to the Farcaster hubs, which operate on the Data Layer of the Farcaster architecture. These hubs play a crucial role in syncing and maintaining a global state of the messages sent and received across the Farcaster network.
Account Recovery with Farcaster
In Farcaster, users have the option to enhance the security of their accounts through the implementation of a recovery address. This recovery address acts as a fail-safe mechanism in case the user's primary custody address is compromised or inaccessible. When a user's account is compromised, the recovery address owner can initiate a transfer of ownership request to reclaim control of the account. However, to prevent any potential malicious actions, Farcaster enforces a 7-day waiting period before the transfer of ownership is completed. This grace period ensures that the request is genuine and not an attempt by unauthorized entities to take control of the account. By introducing this recovery address feature and the waiting period, Farcaster strikes a balance between robust security measures and user-friendly account recovery, safeguarding users' digital assets in the decentralized ecosystem.
Final Thoughts
Farcaster's approach to authentication and identity generation represents a pioneering stride towards enhancing security, privacy, and user experience in the decentralized landscape. By introducing a separate signer public-private key pair, Farcaster eliminates the need for users to expose their custody address's private key during message signing, fortifying the protection of their digital assets.
The implementation of a recovery address further adds a layer of resilience to account security. Users can proactively set a designated recovery address, allowing them to reclaim control of their accounts in the event of compromise or access loss.
In a decentralized world where self-sovereignty is paramount, Farcaster's authentication and identity generation mechanisms set new standards for privacy and control over digital assets.
Subscribe to my newsletter
Read articles from Aditi Polkam directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Aditi Polkam
Aditi Polkam
I write on how to build better backend for your apps