Understanding the OSI Model
 Ajay Ravi
Ajay Ravi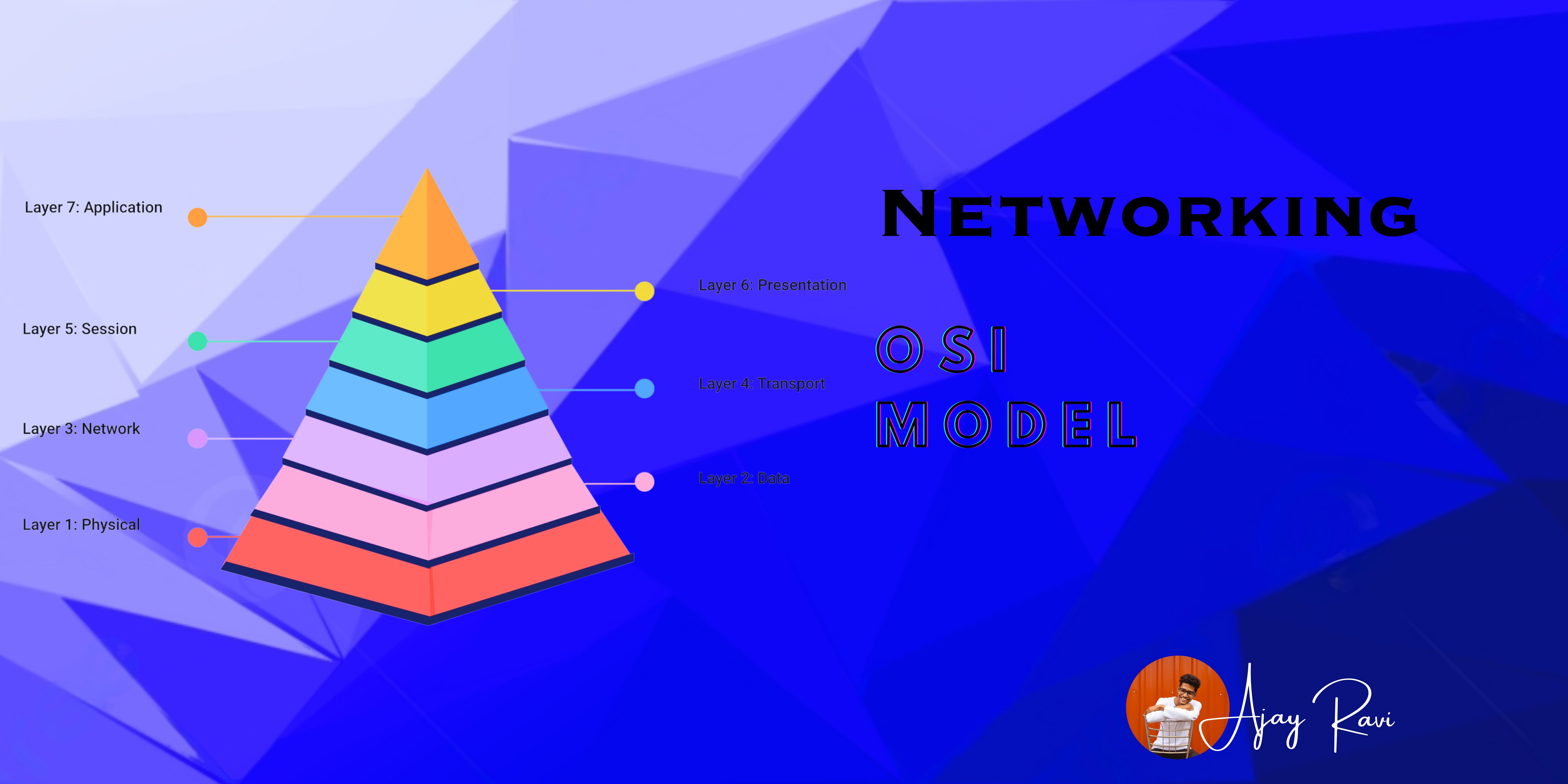
Introduction
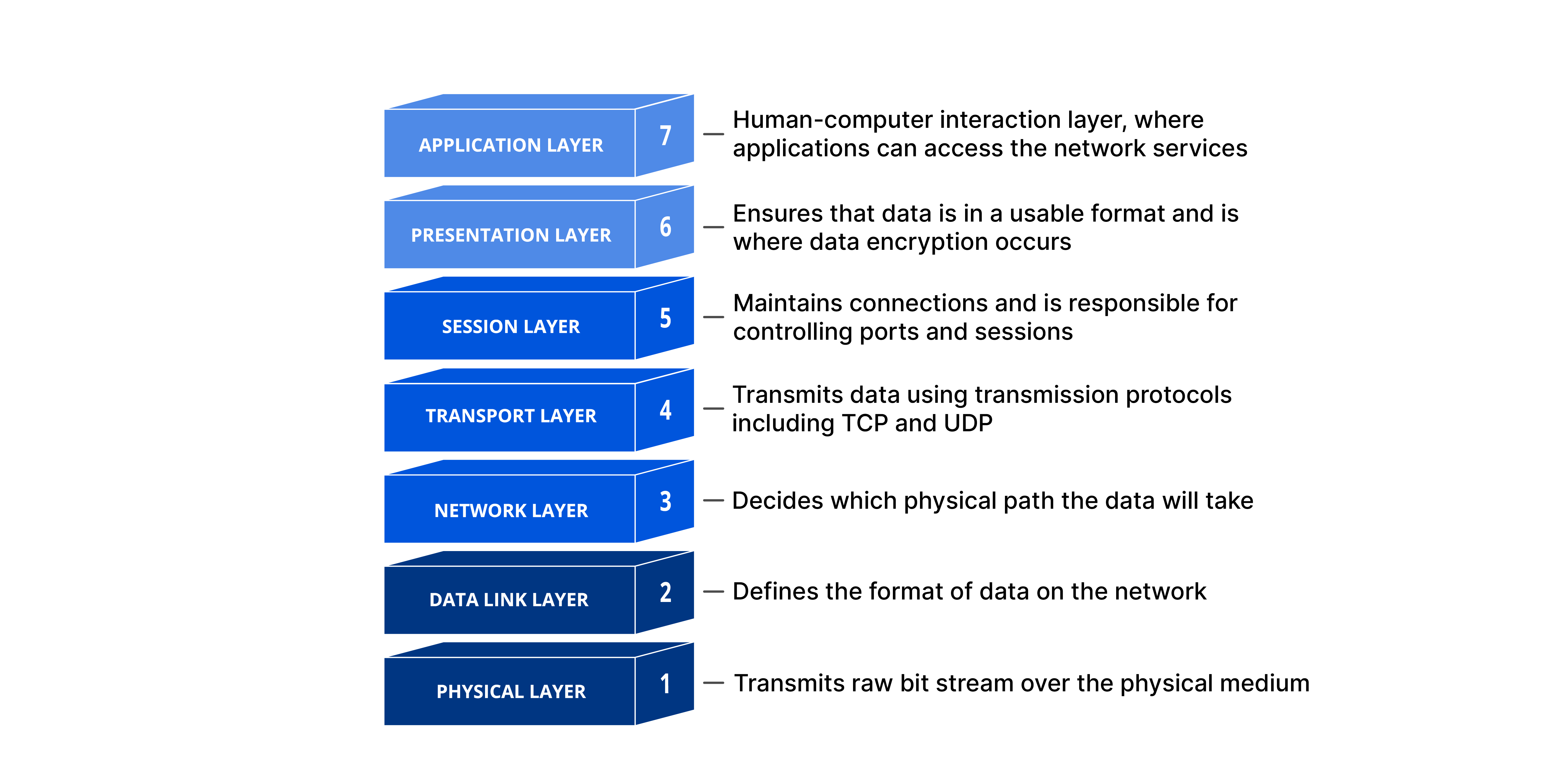
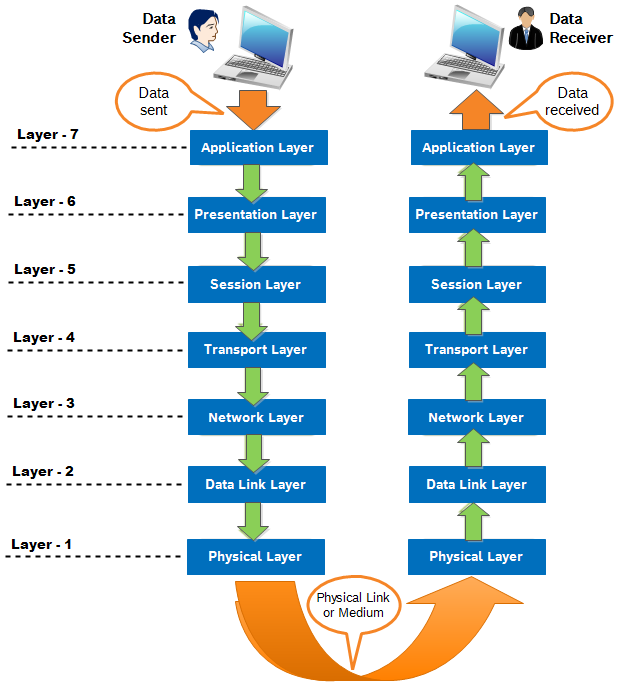
In the world of computer networking, the OSI (Open Systems Interconnection) model plays a crucial role in ensuring seamless communication between devices. Developed by the International Organization for Standardization (ISO) in 1984, this 7-layer architecture provides a standardized framework for transmitting data from one person to another across the globe. Each layer in the OSI model has specific functionalities, and they work collaboratively to facilitate the smooth flow of information.
Layer 1 - Physical Layer
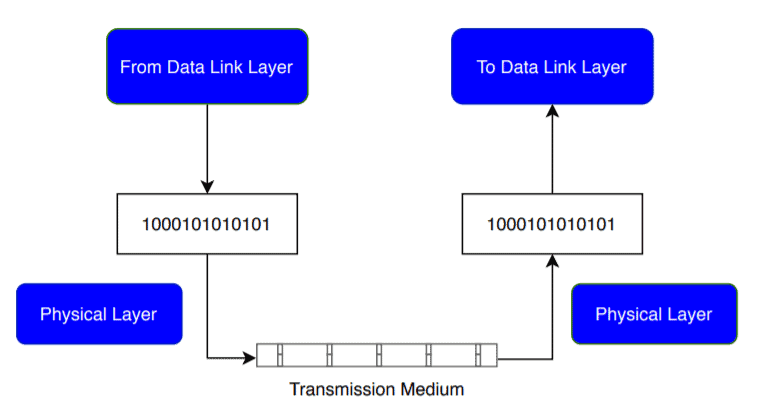
The Physical Layer is the lowest layer of the OSI reference model and is responsible for the actual physical connection between devices. It deals with raw bits, transmitting individual bits from one node to the next. This layer handles bit synchronization, which provides a clock to control synchronization at the bit level for both the sender and receiver. It also defines the transmission rate, specifying the number of bits sent per second. Additionally, the Physical Layer determines the physical topologies of the network (e.g., bus, star, mesh) and the transmission mode, which can be simplex, half-duplex, or full-duplex.
Functions of the Physical Layer
Bit synchronization: Provides clock-based synchronization for precise bit-level communication.
Bit rate control: Defines the transmission rate, i.e., the number of bits sent per second.
Physical topologies: Specifies the arrangement of devices/nodes in the network, such as bus, star, or mesh.
Transmission mode: Defines how data flows between connected devices, including simplex, half-duplex, and full-duplex.
Devices in the Physical Layer
Hub
Repeater
Modem
Cables
Layer 2 - Data Link Layer (DLL)
The Data Link Layer is responsible for the node-to-node delivery of messages over the physical layer. It ensures error-free data transfer from one node to another. The DLL takes data from the Network layer and encapsulates it into frames, which are then transmitted to the physical layer. This layer also adds physical addresses (MAC addresses) of the sender and receiver in the frame's header.
Functions of the Data Link Layer
Framing: Divides data into frames, attaching special bit patterns at the beginning and end for synchronization.
Physical addressing: Adds MAC addresses to the header to identify sender and receiver.
Error control: Detects and retransmits damaged or lost frames for reliable communication.
Flow control: Coordinates the amount of data sent before receiving acknowledgment to avoid data overflow.
Access control: Determines which device has control over the communication channel when shared by multiple devices.
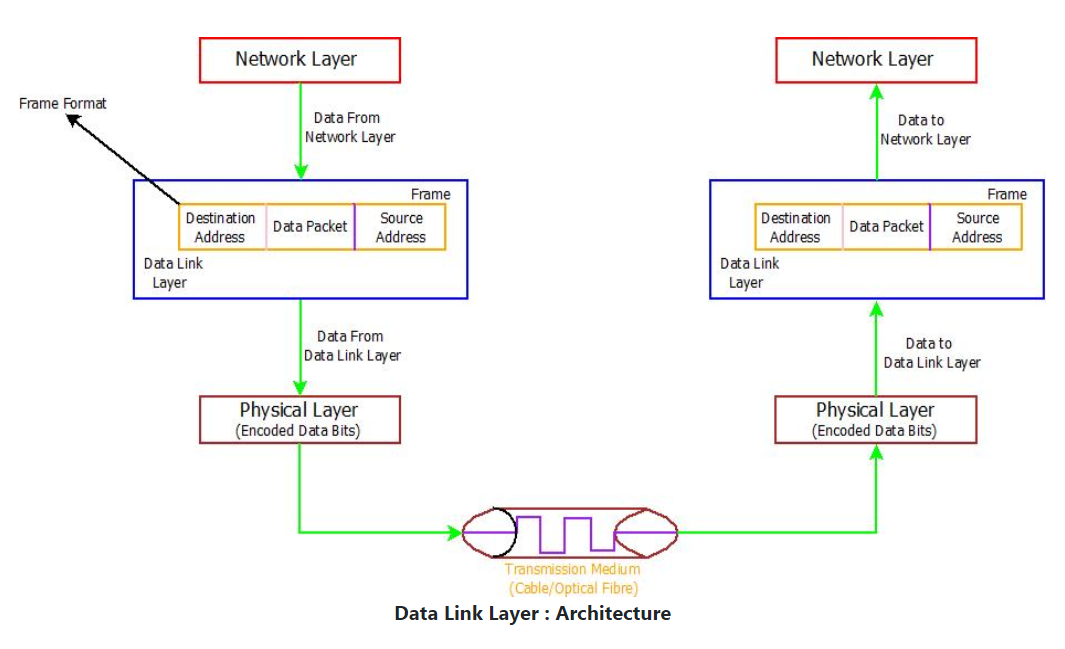
Devices in the Data Link Layer
Network Interface Card (NIC)
Switch
Bridge
Layer 3 - Network Layer
The Network Layer focuses on data transmission between hosts located in different networks. It handles routing, selecting the best path for data to travel, and logical addressing using IP addresses to uniquely identify devices. The Network layer places the sender and receiver's IP addresses in the packet header.
Functions of the Network Layer
Routing: Determines the best route for data transmission from source to destination.
Logical addressing: Assigns IP addresses to identify each device uniquely and universally.
Devices in the Network Layer
Router
Switch
Layer 4 - Transport Layer
The Transport Layer provides end-to-end delivery of complete messages between applications on hosts. It takes data from the Session layer and segments it into smaller units called segments. The Transport layer adds source and destination port numbers to the segment header, ensuring the data reaches the correct application. It handles error control, flow control, and offers two types of services: connection-oriented (reliable) and connectionless (fast).
Functions of the Transport Layer
Segmentation and reassembly: Breaks data into segments and reassembles them at the destination.
Service Point Addressing: Uses port numbers to deliver the data to the correct process/application.
Connection-oriented service: Establishes a reliable connection before data transmission, providing acknowledgment and retransmission for data integrity.
Connectionless service: Directly sends data without establishing a connection, offering faster communication.
Protocols Used in the Transport Layer
TCP (Transmission Control Protocol)
UDP (User Datagram Protocol)
Layer 5 - Session Layer
The Session Layer establishes, maintains, and terminates connections between applications on different hosts. It enables synchronization points in data for proper data transmission and supports half-duplex and full-duplex communication.
Functions of the Session Layer
Session establishment, maintenance, and termination: Allows two processes to establish, use, and terminate a connection.
Synchronization: Adds checkpoints to identify errors and re-synchronize data properly.
Layer 6 - Presentation Layer
The Presentation Layer is responsible for data format translation, encryption, and compression. It translates data from the Application layer into a suitable format for transmission over the network. Encryption ensures secure communication, and compression reduces the amount of data transmitted, optimizing network performance.
Layer 7 - Application Layer
The Application Layer is the topmost layer and is implemented by network applications. It provides a user interface for creating and accessing data. Various applications like web browsers, email clients, and file transfer protocols operate in this layer. It offers services like network virtual terminal, file transfer access and management, mail services, and directory services.
Conclusion
The OSI model is a fundamental reference for computer networking, providing a standardized framework for communication between devices. It consists of seven layers, each with specific functions and responsibilities. While the OSI model serves as a reference model, real-world networking predominantly relies on the TCP/IP model, which closely aligns with how the Internet operates. Understanding the OSI model is essential for network professionals, enabling them to troubleshoot and optimize network communication effectively.
Subscribe to my newsletter
Read articles from Ajay Ravi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ajay Ravi
Ajay Ravi
Unleashing Web Development Superpowers while Diving into the Exciting Realms of Blockchain and DevOps