What is Azure Governance
 krishana jupudi
krishana jupudiIntroduction:
When using Microsoft Azure, it is crucial to have the appropriate cloud governance in place. The advantages and benefits of the cloud are numerous.
Azure Management Areas:
the procedures and duties necessary to maintain your business applications, as well as the resources that back them up. The platform provides a wide range of tools and services that can completely manage your cloud environment.
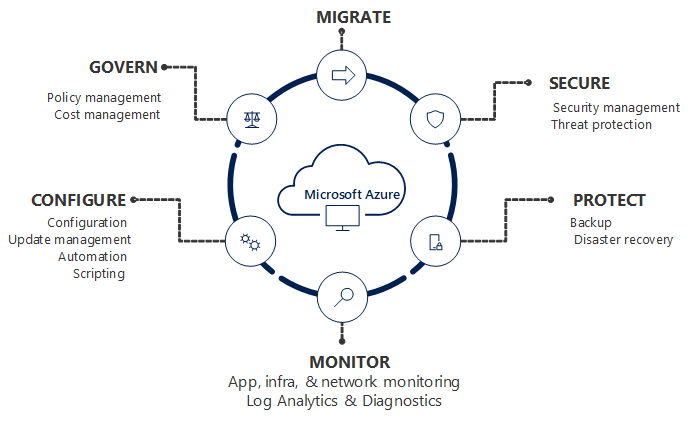
The structure known as "governance" establishes the goals and responsibilities that guide how your organization performs its operations.
By combining several services and capabilities, Azure governance enables you to manage all of your Azure resources at scale while adhering to control policies.
It functions with various subscriptions and resource groupings.
Here Role-Based Access Control (RBAC), policies, and management groups are the foundations of this system.
The procedures and systems are in place to keep your apps and resources under control and
they serve as your organization's strategic priorities when planning your activities.
The security teams aiming to manage their cloud have them as their primary emphasis. It can be difficult to grant access to an increasing number of technology resources while also keeping an eye on compliance and security threats.
Azure Governance Framework:
promote security precautions for Microsoft Azure cloud usage. The policies, techniques, configurations, and procedures required to safeguard data and identities in the cloud environment are frequently outlined in the cloud security guidelines.
Because of the cloud's size, problems and complexity will only continue to expand exponentially.
One of the key components of your cloud governance strategy is security. When managing your data, you want to enforce the least access for everyone. You can develop and configure your security policy using Azure Policy to adhere to the least access principle.
This security policy's resulting security rules are automatically applied to your environment, and both newly added and already used resources are audited.
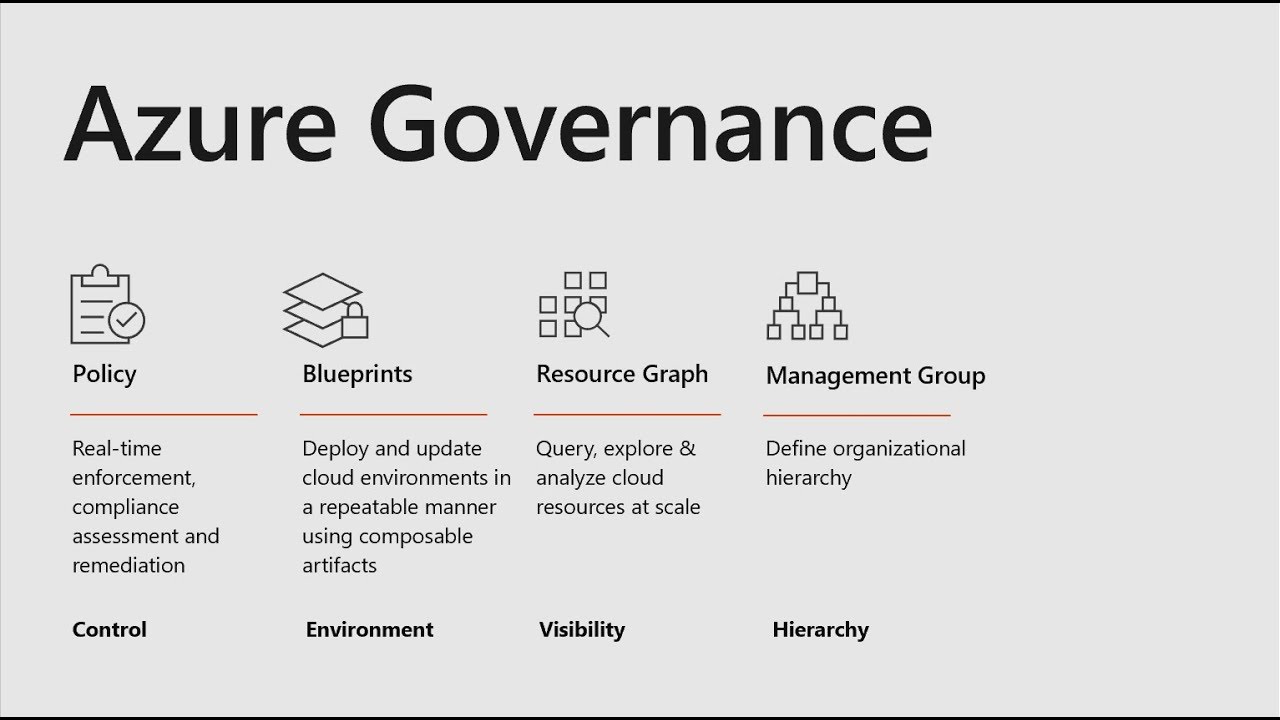
Services:
1. Management Groups 2. RBAC & Identity base 3.Azure Blueprint
4. Azure Policy 5. Resource Groups 6. Naming convention
Management Groups: This border made it possible for businesses to "separate" resources via several subscriptions. Organizations can divide based on dev/test and production environments, employ dedicated subscriptions for a particular application workload, or subscribe geographically. No matter what kind of subscriptions you may have, management groups give you management at scale.
All subscriptions- however, must have trust for the same Azure Active Directory (Azure AD) tenant within a single management group.
Despite being excellent management tools, Azure Policy and Initiative were tied to a single subscription. When administrators wanted to replicate security policy settings across many subscriptions, it was difficult to handle in bigger systems. An Azure Policy and Initiative cross-subscription assignment is exactly what management
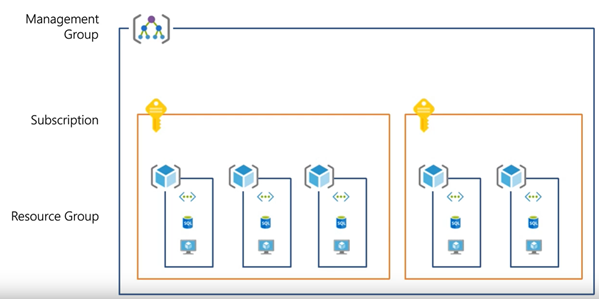
Source: https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/govern/guides/complex/
RBAC & Identity base: Role-based access control (Azure RBAC) is heavily used by Azure itself to regulate who may do what on the platform.
"who" could be a user from another Azure Active Directory tenant, a member of a group from your Active Directory, or a non-person identity like a registered service principal.
If you can't find the precise role mapping for the unique needs of your organization in the almost 100 (no.of)distinct roles offered by RBAC, you can develop bespoke roles.
Azure Blueprint: Azure Blueprints give cloud teams the ability to create a set of reusables, repeatable instructions for deployment and setup that adhere to organizational standards, rules, controls, and needs.
Azure Blueprints orchestrates the whole deployment life cycle of resources by relying on a combination of roles, controls, and infrastructure as code.
Azure resources serve as the foundation for everything, including dynamic names that are fixed once they are generated. A fixed namespace domain is where other services are deployed, hence it's critical to establish naming rules.
Azure Policy: This is a real framework for governance, management, and control.
Policies - that detail the prerequisites you want to impose for Azure resources before they can be deployed.
For example, you might have specific resource naming standards you want to impose to optimize your asset management and CMDB regulations. Alternatively, you might only allow certain virtual machine sizes in your subscription to keep costs under control.
You can implement multiple policies simultaneously by grouping them into Azure policy initiatives. The policies must be given a scope after they have been defined. This scope may be a subscription, a collection of resources, or a single resource.
The implementation of tags is something that many businesses find advantageous. A tag is similar to a label that is put on a Resource Group or specific resources, like a cost center or business unit. These tags enable a billing administrator to see exactly what a resource is used for or to which cost center it belongs.
Resource Groups: Microsoft generally does not enforce where resources should go or how you should arrange your resource groups. While some organizations create resource groups based on workloads or location, others define resource groups according to resource types.
The location must be specified for every resource because the majority of the platform's resources are region-specific. When a Resource Group is located in one place while containing resources in another, complexity results. Although perfectly legal, this could result in outages if the Azure region the Resource Group is in becomes unreachable. Although the resources are still there, you are unable to alter them.
Naming Convention: Azure resources serve as the foundation for everything, including dynamic names that are fixed once they are generated. It's critical to have naming rules because other services are implemented in a set namespace domain.
Common Issues:
-Unforeseen cloud expenses
-Insecurity
-Absence of controls
-Inconsistency in the resources
-Ineffective administration of non-person identities
Azure Security tips:
-Do your research before moving
-Recognise controls and regulatory compliance
-Use real-time observation/ Monitoring
-Implement effective identity controls
Conclusion
By using Azure Governance, we can handle all environmental concerns, finances, and regulations effectively and efficiently while also accelerating processes. We have control over all access rights using.
Thank You!
Hope this will be helpful to you.
Subscribe to my newsletter
Read articles from krishana jupudi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
