What is IAM Access Analyzer and How to Use it
 Eyal Katz
Eyal Katz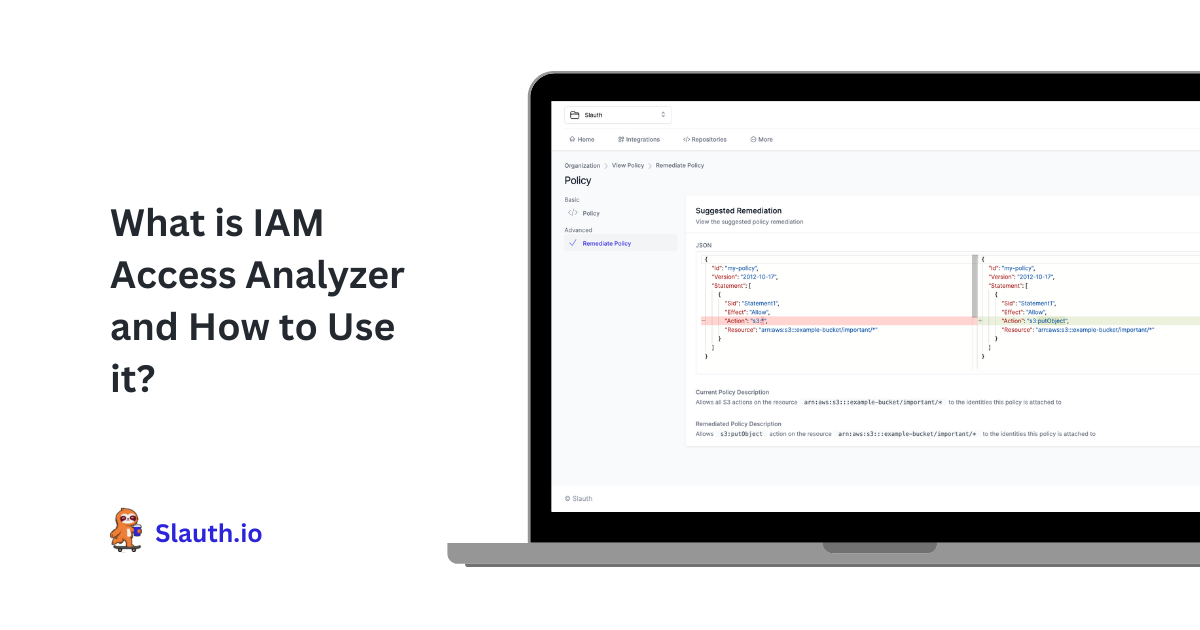
Do you know who’s accessing your resources? If you don’t, chances are your IAM policies need some revision. IAM policies can appear opaque and hard to comprehend, so creating and reviewing them is understandably off-putting.
But when the smallest security gap can expose your entire organization to million-dollar attacks, you need to eat the frog. Or let IAM tools eat the frog for you. 44% of companies believe implementing IAM solutions would enable them to close current security gaps.
To help its users close their security gaps, AWS created Access Analyzer, allowing you to generate, validate and review IAM policies in your AWS account. This article provides a step-by-step tutorial on using IAM Access Analyzer, discussing its benefits and limitations.
Exploring IAM Access Analyzer
The IAM Access Analyzer is a tool from AWS that helps you keep your IAM Roles secure. It scans your IAM policies for overly generous access with external entities, suggests possible changes to your policy definition, and can even generate new policies for a resource based on CloudTrail logs.
Access to external identities should be limited when designing and monitoring your cloud infrastructure. Every access point is a possible vector of attack, so you want to remove any unnecessary permissions and keep your policies within the principle of least privilege.
Access Analyzer enables this by automatically monitoring your organization or account for lax external sharing, informing you, and facilitating the creation of a new, safer policy. As a result, you can see issues as soon as they occur and fix them rapidly across your entire estate, optimizing your overall cloud identity management strategy.
What are external identities?
External identities are resources that are outside your zone of trust. The zone of trust is your organization or account that you associate with the Access Analyzer. All resources within your account/organization are considered trusted and not flagged. Access Analyzer works by picking up resources outside your trusted circle that still have access.
How IAM Access Analyzer Works
The tool has three primary features:
Automatic Scans - When set up, it automatically scans your account for resources shared with external entities. All these potential security risks are listed as "findings" on the Access Analyzer page on the console for you to review. As you create new policies or edit old ones, Access Analyzer will also detect and scan these.
Policy Validation - All the insecure policies flagged by the scan can be edited and checked within the tool. As you edit the policy, it suggests changes per the syntax of the policy grammar and security best practices. This way, you can easily create new guidelines that are more secure than before.
Policy Generation - Access Analyzer can also automatically generate new policies based on the logs on AWS CloudTrail. You can specify the date range of the activity to analyze, edit and validate these generated policies and apply them to your resources.
Limitations of Access Analyzer
Access Analyzer only works in a single region and within a single account or organization, so you are automatically restricted. You must create multiple Access Analyzers to cover all your regions and accounts to get complete visibility over your infrastructure, which can quickly become cumbersome.
As of July 2023, Access Analyzer only supports 12 of the most common AWS resource types. These are:
Amazon Simple Storage Service buckets
AWS Identity and Access Management roles
AWS Key Management Service keys
AWS Lambda functions and layers
Amazon Simple Queue Service queues
AWS Secrets Manager secrets
Amazon Simple Notification Service topics
Amazon Elastic Block Store volume snapshots
Amazon Relational Database Service DB snapshots
Amazon Relational Database Service DB cluster snapshots
Amazon Elastic Container Registry repositories
Amazon Elastic File System file systems
It won’t check any insecure policies for unsupported resource types, meaning you may have many coverage gaps that need to be closed with the support of other tools. Lastly, Access Analyzer specifically analyzes access policies based on CloudTrail logs, so everything is dependent on your CloudTrail tool and how well it tracks activity. Ideally, you would need a complete overview of activity in your systems (actual API calls) to understand identities’ behavior and create policies based on that.
Machine Identities in Access Analyzer
Your machines link to an identity that includes all its associated policies. Access Analyzer can only analyze the identities for a handful of resource types, so its utility is immediately limited. If you use resource types outside the list supported by the tool, consider using a third-party service like Slauth.io to automate the creation of IAM policies based on real-time API calls from end-to-end tests to AWS.
How to use the IAM Access Analyzer
The rest of this article walks through the features of the Analyzer and how to use them from the AWS Console. In addition to the console, you can use some parts of the tool via the AWS CLI or API.
1. Identifying resources shared with external identities
You should first scan your account or organization to know which identities connect to external entities. The scan uses logical reasoning to find these security flaws rather than a black-box machine learning algorithm that can hallucinate or make unexpected errors. It adds every policy that allows access to external entities to a list of findings, which includes more information about the entity and its access type.
Once the scan is complete, you can review the findings and decide whether the behavior is intended. To keep the policy as is, you can archive the discovery so that it won't appear in the following scan (as long as it remains unedited). If the permissions are unintended, you can move on to generating and editing a better policy.
You can find Access Analyzer scans on the AWS IAM Dashboard under "Access Reports.”
2. Refining and validating permission
Once you have scanned your account and found insecure policies, you may want to fix them. You can start afresh and generate a new policy (see the next section) or simply edit your existing definition following best practices.
Access Analyzer supports this by making suggestions about your policy grammar and security practices. The tool makes over 100 checks to ensure that your policy is valid and secure, including the presence of wildcards ("*" which means "any"), invalid dates, or unnecessary/empty lines.
You can use this feature by creating or editing a policy in the Policy Editor in the AWS Console. You should use the JSON editor (not the Visual editor), and the suggestions will appear below your definition and inline.
3. Generating a policy
If you'd like to create a policy based on real-world use, you can use Access Analyzer to generate a definition based on the least-privilege approach automatically. The service reads your CloudTrail logs to determine performed actions and to build a policy that allows only those actions in the future. You can change the relevant time the generator considers or the logs you want the generator to analyze.
Once you have generated the policy definition, you can check that the given permissions are what you need. Often, you will need to customize the policy to fit your real-world use case. CloudTrail logs are insufficient to generate accurate and secure policies automatically.
Tools like Slauth.io analyze resources across your entire AWS environment, gaining granular insights to create policies that reflect genuine behavior while considering the Least Privilege approach. The more accurately your IAM policies reflect the access needs of your identities, the more valuable time you save in not having to deal with team silos or update policies frequently.
4. Reviewing access before (and after) deployment
When drafting policies, you should review the access granted to external entities before deployment. Access Analyzer can analyze your policies before saving the changes by finding external access and presenting its findings for review.
When editing a policy with the JSON editor for a specific resource, you will see a "Preview external access" button below the link. Simply choose the Access Analyzer you would like to use and click “Preview.”
Coupled with ongoing monitoring, this tool provides continuous security over your IAM policies.
Should I use Access Analyzer?
Yes. Access Analyzer is handy when drafting, editing, and monitoring your IAM policies. It can help you find potential red flags, refine your policies to make them more secure, and continuously monitor your new policies to ensure they are compliant. It is also (note the emphasis here) FREE.
However, it still needs to be designed, used, monitored, and checked by humans, which comes with its flaws. Slauth.io makes IAM policy generation for machine identities easier, stronger, and more accurate. Our IAM Policy Copilot solution tracks real-time API activity to automatically create policies based on actual usage and based on the least privilege principle.
No more guesswork, time wasted, and insecure policies that need constant updating. If you want to give Slauth.io a try, join our waiting list!
Subscribe to my newsletter
Read articles from Eyal Katz directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
