Symmetric and asymmetric encryption
 Tejaswi Kasat
Tejaswi Kasat
Encryption is the process of converting readable data to an unreadable format using a mathematical algorithm. It is extremely useful to keep the integrity of data. This process is widely used across most of the domains existing today. From processing a single request-response from a server to encrypting large files, all processes use some form of encryption to prevent them from accessing and modifying by malicious users.
A simple encryption example
As an example, you are Mr. X and you have a friend Mr. Y. You want to pass a message to Mr. Y. This message is very confidential and it contains very secret information. You decided to send this information via a document through the country post. Posts are handled by people and since this information is very confidential, any person in between has their eyes on it. If you just put it in the envelope and mail it, some person with malicious intentions can read it in between. So, you decided to use a mathematical formula to change the way it is written. For example, as a simple method, you replaced each alphabet by adding 5 to it. So, the word HELLO will be converted to MJPPT. Only you and the receiver know how to convert it back to the original message. So, if any person in between reads this information, he won’t be able to understand it and the data will stay safe from leakage.
This example shows a very simple form of encryption. This method is not at all safe as anyone can detect it easily. When we talk about computers, they can process much more complicated mathematical algorithms with ease. In this article, we won’t be covering encryption algorithms, however, we will cover a high-level overview of types.
Types of encryptions
There are three types of encryptions widely used. These are as below:
Symmetric encryption — Uses a single key.
Asymmetric encryption — Uses a key pair.
Hash functions — Keyless.
We will focus on the first two types only in this article. But before diving deep into these topics, what is the key exactly? So, a key is a string of random characters which can be used to encrypt and decrypt data by using some algorithms. This key is similar to what you use in your house. A door locked with a key can be opened via the same key only. Similarly, a file encrypted via a key can be decrypted via the same key only.
Symmetric encryption
Symmetric encryption is a type of encryption that uses a single key only. The information can be encrypted and decrypted by the same key only. Let’s understand this by an example.
You are Mr. X and you want to send some information to your friend Mr. Y. Again this information is confidential and you don’t want any malicious user to look into this information. So, you created a 256-bit long key and gave this key to your friend by meeting him privately. And now, you use some algorithm to encrypt the confidential data and send this data to your friend. Upon receiving it, your friend can decrypt this data using the key you shared and read the confidential information. Any malicious user in between was unable to read this data since it was encrypted by a key only both of you possess. And since the key is so long, it is near impossible to guess this long key (as of today).
Quantum computers will have the power to generate and guess this long key. They will be powerful enough to depreciate most of the encryption algorithms we use today. They will have the power to even break the blockchain integrity.
An illustration of symmetric encryption is as follows:
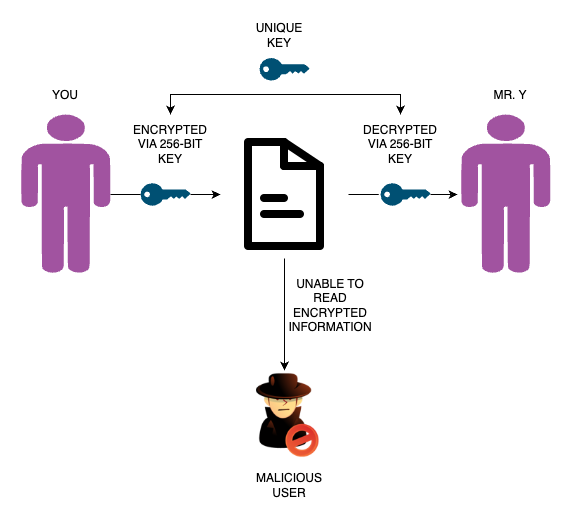
Fig. 1 — Symmetric encryption
This method of encryption is not 100 percent secure. The reason is, you still have to share the key with the recipient, so you both can encrypt and decrypt. There might be a chance that someone can steal your keys while you’re sharing them.
Some commonly used algorithms for symmetric encryption are AES, DES, 3DES, IDEA, etc.
Asymmetric encryption
As you have seen previously that in the symmetric algorithm, you have to share your secret key with the recipient to decrypt the data and there is still a chance that your keys might get stolen while the transfer is happening. So, how can we avoid the procedure of sharing keys? The answer is asymmetric encryption.
Asymmetric encryption uses a key pair — a public key and a private key. The reason why these two keys are called a key pair is that they both are generated together and the data encrypted by a public key can only be decrypted by its respective private key. Similarly, data encrypted by a private key can only be decrypted by its public key. Using asymmetric encryption can eliminate the need for sharing of confidential keys.
As the name suggests, public keys are meant to be public. This means you can publish this key over the internet and anyone can view it. Private keys are meant to be private. This means they should not be shared, or transferred to anyone. This should stay with you locally, secured within your system.
Let’s take an example. You want to receive some confidential information from your friend whose security is extremely important. You don’t want to share keys as they can be stolen. So, you decided to use asymmetric encryption for this process. You generated a public-private key pair and published the public key. Your friend used that public key to encrypt the data he wants to send you. Now, as per the concept, any information which is encrypted via a public key can only be decrypted by the respective private key. Since only you will have that private key, only you can decrypt this information. In a similar scenario, when you want to send some confidential information to your friend, you used his generated public key for encrypting that information, and your friend decrypted it using his private key. An illustration of the same is shown in Fig. 2.
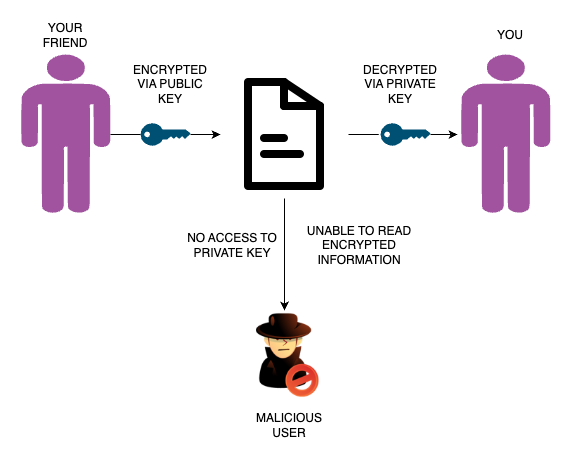
Fig 2 — Asymmetric Encryption
This type of encryption is widely used. Some practical uses are as follows:
Passwordless authentication: While using passwordless authentication, the server challenges you with information encrypted by your public key and you have to decrypt it via your private key. If you can decrypt it, your authentication will be successful. Common examples are logging into a server using SSH, setting up GitHub passwordless authentication, etc.
TLS handshake: TLS handshake uses asymmetric encryption techniques to validate if data received from the server is coming from an authentic server and to encrypt further data exchanged between client and server.
Digital signatures: The digest hashes are encrypted by private keys and then decrypted by public keys to validate the authenticity.
Zero trust: Asymmetric encryption is widely used for implementing zero trust in private networks.
Some commonly used algorithms for implementing asymmetric encryption are RSA, ECC, DSA, etc.
You can follow me on LinkedIn here.
Subscribe to my newsletter
Read articles from Tejaswi Kasat directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Tejaswi Kasat
Tejaswi Kasat
I am a senior software engineer driving business success through innovative software solutions and cloud technologies. I am passionate about building scalable applications and leveraging cloud platforms for seamless deployment and performance optimization