What is SSH and SCP Protocol? A Complete Guide
 Rahul Ajit Goraksha
Rahul Ajit Goraksha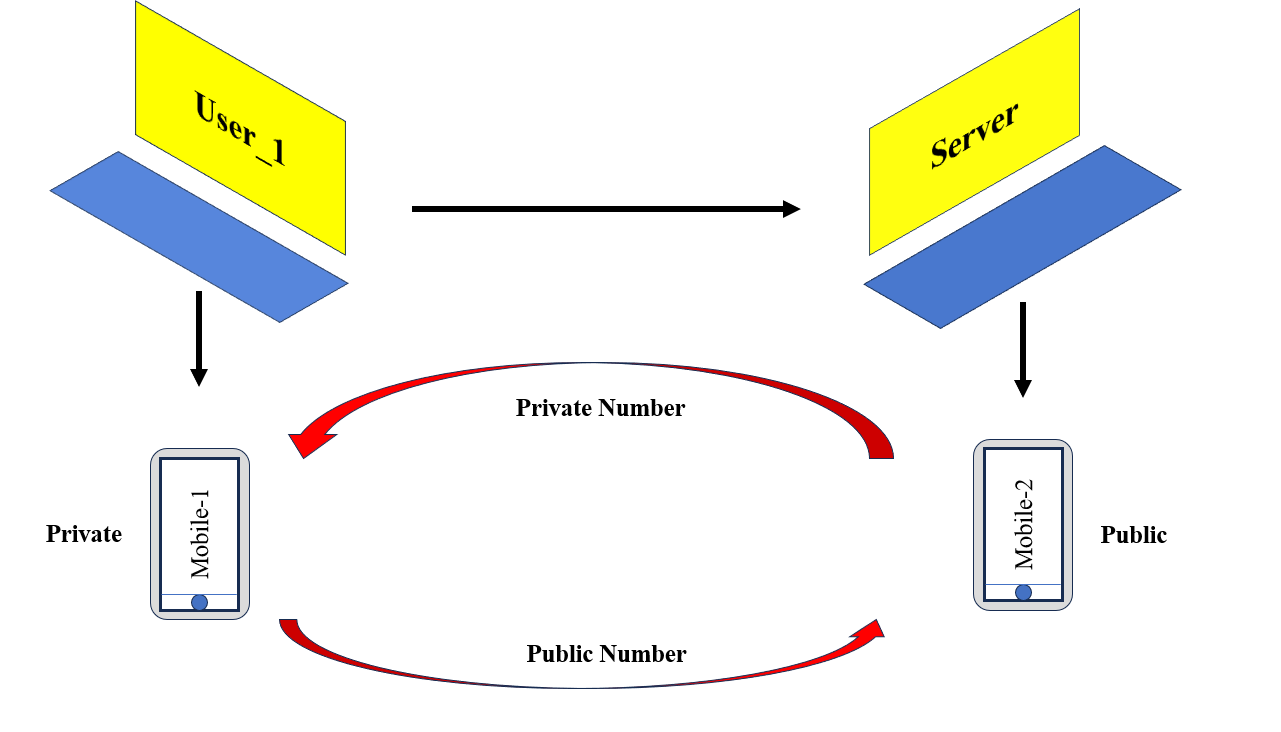
written By: Rahul Goraksha
In this blog, we will look at the fundamentals of SSH and SCP, their functions, and their importance in today's digital world.
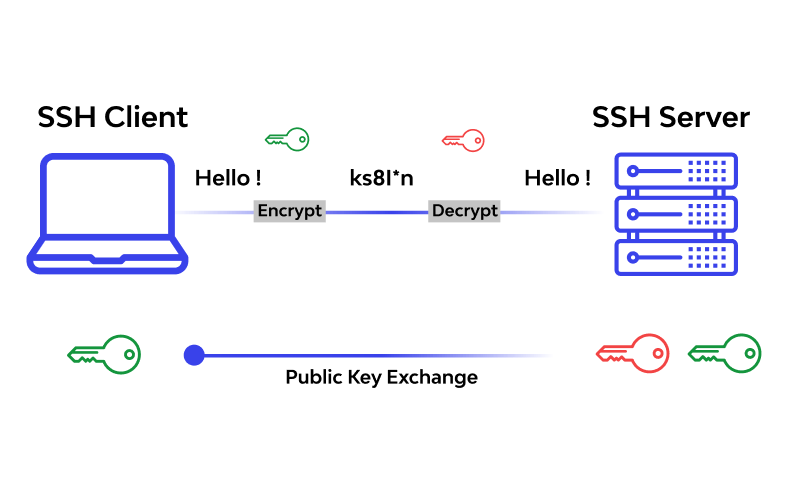
Figure 1: Schematic Diagram of SSH Protocol
What is Linux?
Linux is a free open-source operating system (OS) that provides more security than many operating systems and does not require antivirus software for protection.
So, let's first understand the layers of Linux Architecture:
It mainly consists of four layers which are Hardware, Kernel, Shell, and Application.
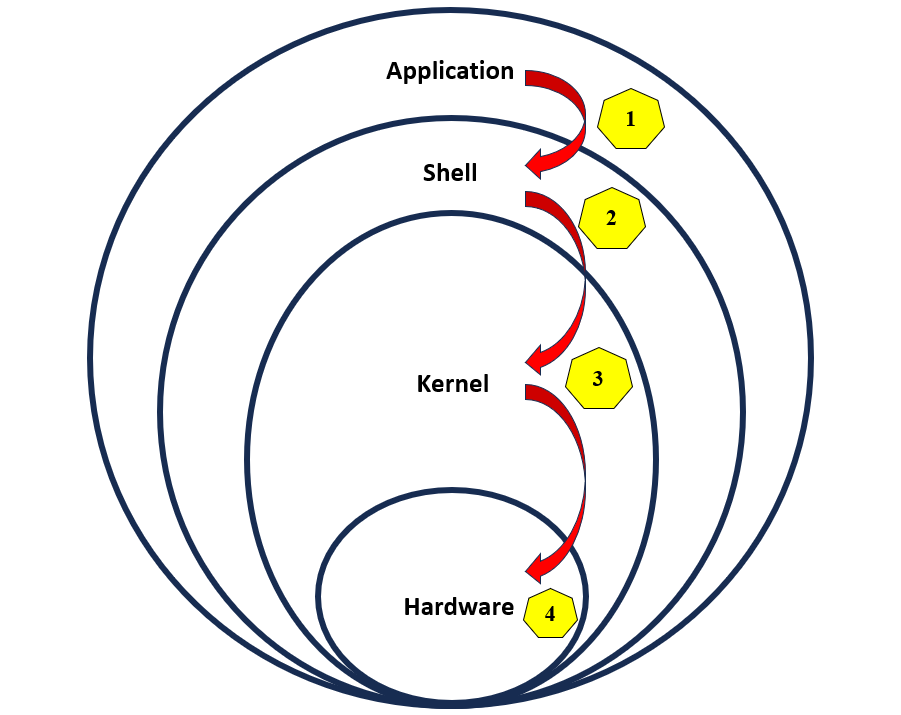
Figure 2: Linux Architecture
Application: There are various applications such as web browsers, media players, etc that users install and tend to use on their Linux systems.
Shell: It is a program that interprets user commands and allows communication between the user and the kernel of the operating system.
Kernel: It mostly acts as a doorway between the Shell and hardware and performs communication between software and hardware components.
Hardware: It mainly use to interact with the real physical world for example print, output, etc.
So After having a thorough understanding of Linux architecture, let's head on to understanding the SSH Protocol
What is SSH Protocol?
SSH stands for secure Shocket shell.
If we want to work with multiple servers, then there will be a Linux Shell, the kernel is already present, so directly connect to the shell and get access to all the servers and perform what you wish.
How do I connect Shell in a very secure manner?
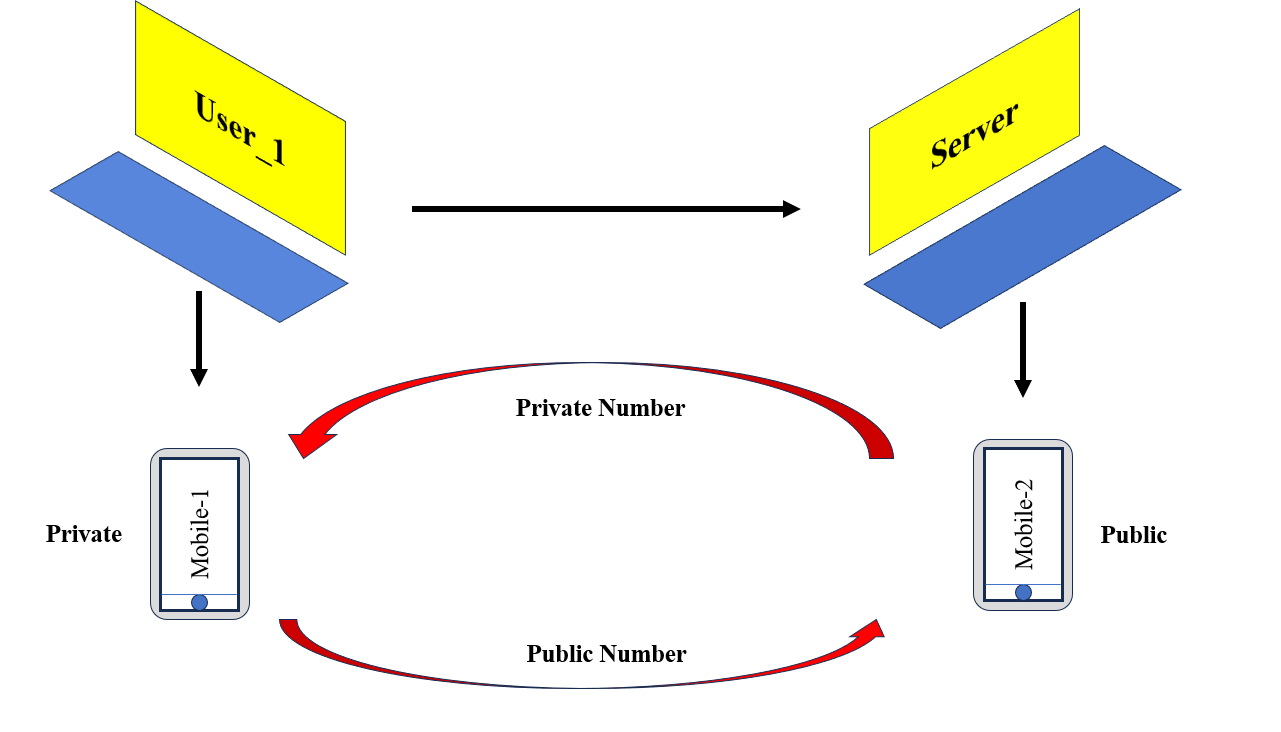
Figure 3: SSH Protocol Explanation
To connect Shell in a very secure manner, there are mainly three major parameters being followed throughout the industry, and those are as follows:
Username, Password
Keys ****{Popular Method}
Role-Based Access Control
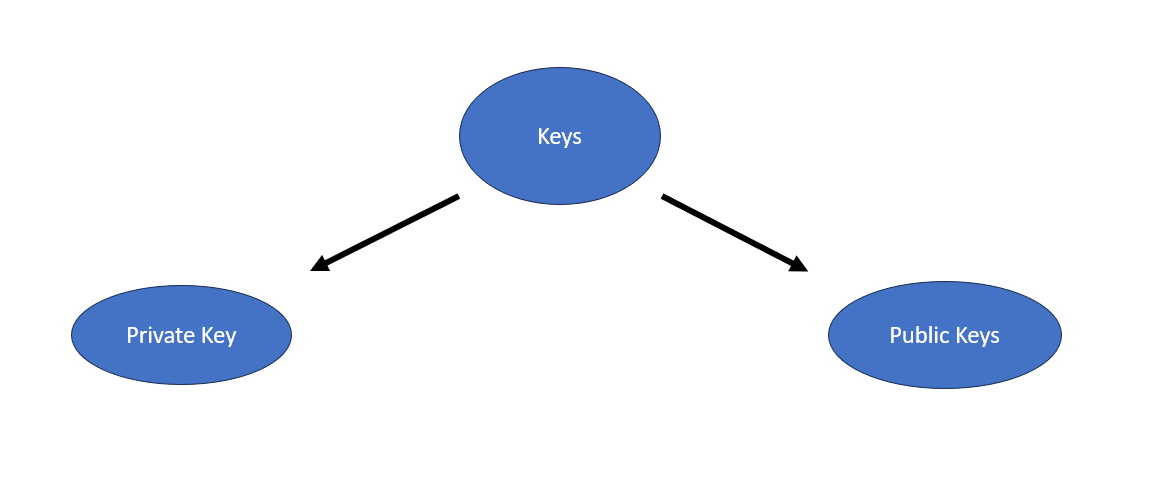
Figure 4: Classification of Keys
Keys have been classified into two categories:
Private Keys: Private keys stay with the user only
Public Keys: Public key is mainly sent to the server
with reference to the above Figure 3 if both private and public keys are paired then only it's possible to generate the keygen
So if we want to connect the Shell securely for that we need to get the private key from the Server and in exchange for that User_1 needs to provide the public key to the Server after getting paired successfully we are good to perform any operations.
Initially, you need to download the private key of a particular server. Then, you have to grant permission to access the private key.
Now let's get hands-on experience by practicing using the below command
Running this command to ensure the private key is not publicly viewable
chmod 400 linux-for-devops.pem
Next, we need to connect our server using its Public DNS
ssh -i privatekey username@host[ipaddress]
You will be connected to a distant server after running this command on your local PC.
What is the SCP Protocol?
SCP stands for "Secure Copy Protocol", In these operations, we securely copy files from a distant server into our local system or vice versa. During this operation, we employ the SCP protocol.
let's understand this protocol with a hands-on example
scp -i "file_name".server DNS name:/path local_dir_path
After executing this task, we get the desired output as required.
Thank you for being a part of this adventure once more. I want to connect with you in future blog postings. Continue to be interested, inspired, and evolving.
Subscribe to my newsletter
Read articles from Rahul Ajit Goraksha directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Rahul Ajit Goraksha
Rahul Ajit Goraksha
Hi, I’m Rahul Goraksha—a Data Scientist and Analyst passionate about solving business challenges through data-driven insights. With expertise in Python, SQL, Tableau, and Power BI, I explore the intersections of analytics, AI, and visualization. On this page, I share articles, tutorials, and personal projects that transform raw data into actionable stories. Whether it’s automating workflows, building predictive models, or designing insightful dashboards, I aim to make complex concepts accessible to everyone. Follow along as I document my journey, share tips, and collaborate with fellow tech enthusiasts to shape the future of data analytics.