Foundational Knowledge In Cybersecurity
 Benjamin Ololade Adedokun
Benjamin Ololade Adedokun
Introduction
You did well if you chose Cybersecurity Analyst as your preferred role or are presently working there. Cybersecurity analysts, in case you didn't know, are frequently the first line of defence against cybercrime. Isn't this incredible? As a cybersecurity fellow, there are some terms you always encounter in the field.
This article focuses on phrases that you will come across practically every day as a cybersecurity analyst. As a result, you must understand what each is about. The purpose of this essay is not for you to memorise the definitions or examples; rather, it is for you to be familiar with those terms because you will see and use them daily.
What exactly is cybersecurity? What exactly are cyber threats?
Before we get into that, it's vital to have an understanding of what data and information are because you are working with them throughout your cybersecurity Career
Both are the basis for many things in the cybersecurity field and being able to distinguish them is of great Importance.
Data vs Information
Data: Raw, unprocessed numbers, facts, or symbols that represent different kinds of information are referred to as data. It is the fundamental component of knowledge. Data might contain things like usernames, passwords, IP addresses, log entries, file contents, network packets, etc. in the context of cybersecurity. To transform data into relevant information, it is frequently necessary to arrange and interpret it.
Information: Processing and interpreting data to give it context, relevance, and meaning for people or systems results in information. In the context of cybersecurity, data would be studied and processed, and insights would be drawn from the analysis and comprehension of the data.
Note: Intelligence is the basis of your decision after viewing information and is the decision-making component of information.
Consider a cybersecurity expert, for instance, who is studying log data from numerous systems and devices. Timestamps, IP addresses, and event descriptions may be included in the gathered raw log entries (data). The analyst can spot patterns of suspicious activity, such as numerous failed login attempts coming from a specific IP address in a short period of time, by correlating and evaluating this data. The analyst can take the necessary measures to stop a potential security compromise thanks to this information.
Cybersecurity and Cybersecurity Analyst
The goal of the technical field known as cybersecurity is to protect computers, servers, mobile devices, electronic systems, networks, and data against malicious assaults and other cyber threats.
Consequently, who is a cybersecurity Analyst?
A Cybersecurity Analyst is a professional tasked with preventing cyber risks, loss, theft, and unauthorised access to an organization's computer systems, networks, and data.
Cyber dangers and unauthorised access are a cybersecurity analyst's headaches. Protecting the organization's hardware, software, data, and networks against theft, loss, or unauthorised access is your responsibility as a cybersecurity analyst.
Technical terms in Cybersecurity
Further, we need to define a few technical words used in the subject of cyber security, such as:
Threat actors
Assets
Vulnerabilities
Threats
Risks
Event
Exploit
Incident
Intrusion
Exposure
Threat Intelligence
Risk Management
Vulnerability Management
Threat actors: Actors who pose a threat to computer systems, networks, and assets or who want to learn more about their vulnerabilities are referred to as threat actors. Threat actors are frequently categorised according to their intentions. There is a link in one of my posts where you can learn more about threat actors. It goes into great detail about what hackers and threat actors are. Threat actors x Hackers.
Assets: We must first comprehend why threats are present and why cybersecurity defence is crucial before we can explore the threats that the analyst must neutralise in the realm of cybersecurity. Why do threat actors continually want to break into networks? Whom are they pursuing? The definition of assets will provide the answers to each of these queries. Anything that has value to a business or organisation is considered an asset. For instance, Google Cloud stores the information of many users, including perhaps your old photos or documents that you'd prefer to keep private, which must be handled carefully, maintained safely, and kept out of the hands of unauthorised parties to prevent leaks. These documents are assets. Do you now know what an Asset is to a cybersecurity analyst?
Vulnerability: Any flaw in the system that could be used to access it or hurt it. Hackers and cybercriminals may target these weaknesses and exploit them through weak spots. Examples include the use of flawed algorithms or ineffective password management.
Threats: Anything that can damage assets by exploiting weaknesses is considered a threat. Malware, DoS (denial of service), DDoS (distributed denial of service), social engineering, etc. may all fall under this category.
Risks: Anything that endangers the assets' confidentiality, integrity, or accessibility is a risk. This will involve violating standard body norms and data breaches.
Event: This is any observable occurrence in a network or system. An example is a user logging into the network
Exploit: It represents a particular attack. Such attacks leverage vulnerabilities in systems or networks. e.g., If a company's admin's account uses a weak password because they do not have a password policy in place, a threat actor might use a brute force attack to guess the admin's password and have access to sensitive information or even the Company's database. The weak password is a vulnerability and the act of the threat actor having unauthorised access to the database is the exploit
Incident: It is a kind of event that could negatively affect the CIA triad (Confidentiality, integrity, and Availability) of information, regardless of the state.
Intrusion: A security event, or combination of events that is often an intentional security incident in which an intruder attempts to gain access to a system or piece of information.
Exposure: This is a mistake that can be exploited by a threat actor. In cybersecurity, exposure refers to the state of being vulnerable or at risk of a security breach or cyber attack. It refers to situations where a system, network, application, or piece of data is accessible to potential threats without adequate protection, increasing the likelihood of unauthorised access, data breaches, or other security incidents. e.g., An organisation that deals with sensitive data but does not encrypt the data. This could encourage hackers to intercept the data in transit.
Threat Intelligence: Threat intelligence is the knowledge and understanding that have been gained about existing or anticipated cyber hazards, vulnerabilities, and threats in the digital environment. To proactively fight against and successfully handle security crises, entails gathering, analysing, and comprehending data about various cybersecurity risks and threat actors. Threat intelligence is a crucial element in cybersecurity decision-making, incident response, and risk management. It helps organisations stay ahead of cyber threats, enhances their security posture, and enables them to respond rapidly to emerging threats and incidents. e.g., Malware Analysis and OSINT (Open Source Intelligence)
Risk Management: Organisations employ a systematic and proactive strategy called risk management to find, evaluate, manage, and keep an eye on any potential risks that might influence their goals or operations. Various threats and vulnerabilities are analysed, and strategies are put into place to lessen the possibility and impact of unfavourable events.
Vulnerability Management: The process of locating, analysing, and resolving weaknesses or vulnerabilities in computer systems, networks, software, and applications is known as vulnerability management. Before an attacker uses them to jeopardise the security of an organization's digital assets or data, vulnerability management seeks to proactively identify these holes. Identifying Vulnerabilities and mitigating them.
Vulnerability management can be explained simply as routinely inspecting your home for unlocked doors or windows to ensure criminals couldn't enter. You can stop fraudsters from obtaining unauthorised access to your digital systems and safeguard your information from potential dangers by identifying and repairing these weak points. It's crucial to maintaining the safety and security of your online experience.
Security Principle: CIA Triad
As a cybersecurity analyst, it is your responsibility to uphold the following principles: availability (ensuring that whatever information is under your watch is accessible to authorised people), integrity (ensuring that the data or information is not compromised, can always be trusted to be true, and has not been corrupted), and confidentiality (ensuring that it is only accessible by authorised people).
One of the fundamentals of everything done in Cybersecurity is called the CIA Triad (add an image). It contains the three core principles that guide the protection of Information and data. Each letter in the acronym “CIA” stands for a specific principle.
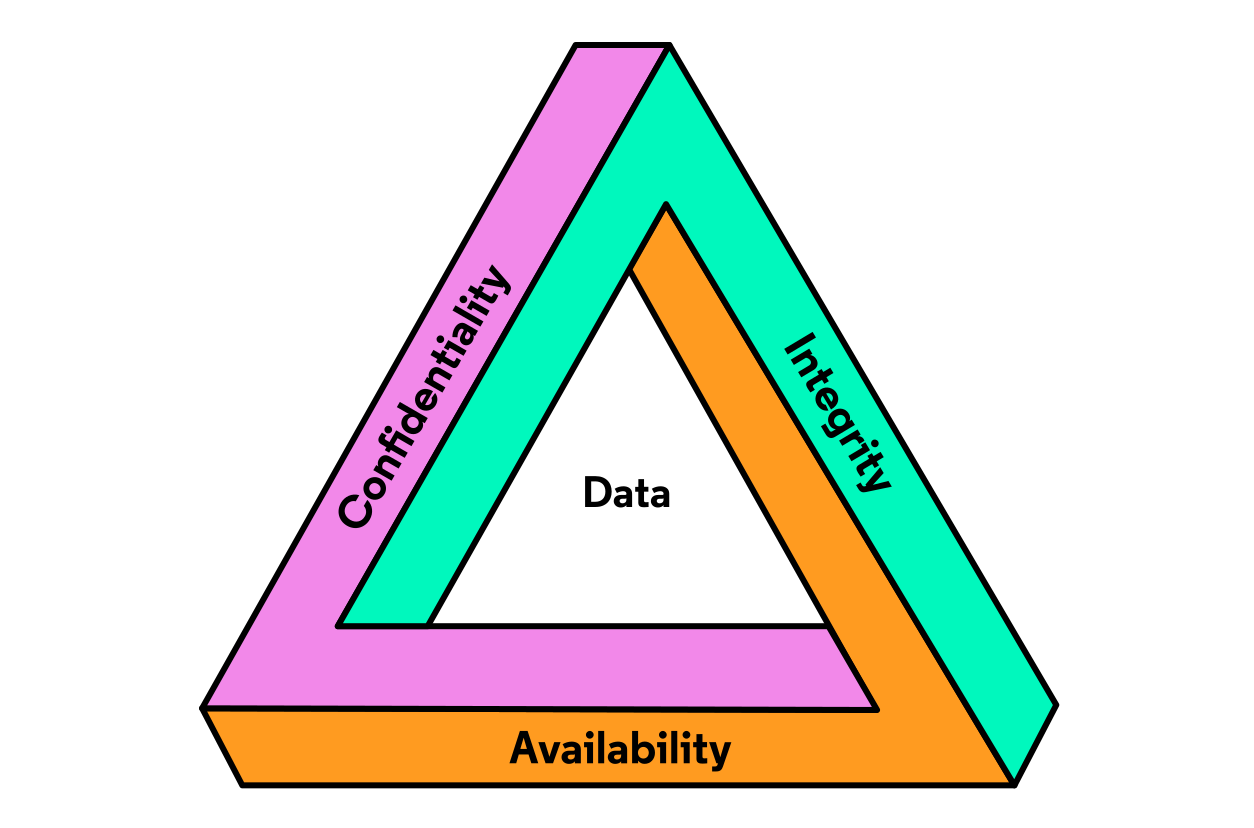
Confidentiality: This refers to the principle of ensuring that only authorised individuals and entities have access to information or data. This is important in safekeeping sensitive information, secrets, PII, etc.
Integrity: This ensures data and information are not modified, tampered with, or altered by authorised individuals. It is the accuracy, consistency, and trustworthiness of data during its entire life cycle.
Availability: It focuses on the accessibility and usability of Information and services by authorised individuals and entities. It includes protecting against downtime and disruptions.
Frameworks: Security frameworks are guidelines used for building plans to mitigate risk and threats to data and privacy. They often serve as references in the defensive and offensive aspects of security.
Playbook: This is also reference-like material. It’s a manual that provides details about any operational action, such as how to respond to a security incident.
Log: This is a record of events that occur within an organization's systems and networks.
To know more about the CIA Triad, check out my detailed article titled "CIA Triad; The Heartbeat of Cybersecurity."
Subscribe to my newsletter
Read articles from Benjamin Ololade Adedokun directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Benjamin Ololade Adedokun
Benjamin Ololade Adedokun
Ololade is a multi-skilled professional with a love for technology and a broad range of abilities. In their role as a developer, they have a talent for writing clean, effective code that realizes creative concepts. A strong level of protection for systems and data is ensured thanks to their skill as cyber security analysts in navigating the complicated terrain of online threats. Technical writers also have the capacity to convey difficult ideas in a clear and succinct manner, opening up technical information to a broad audience. [Name] is a great asset in the field of technology, combining technical prowess with effective communication abilities. He has a strong dedication to excellence and a desire for lifelong learning.