What is SNMP? | SNMP Ports - Protocols & Versions.
 Atul Sharma
Atul Sharma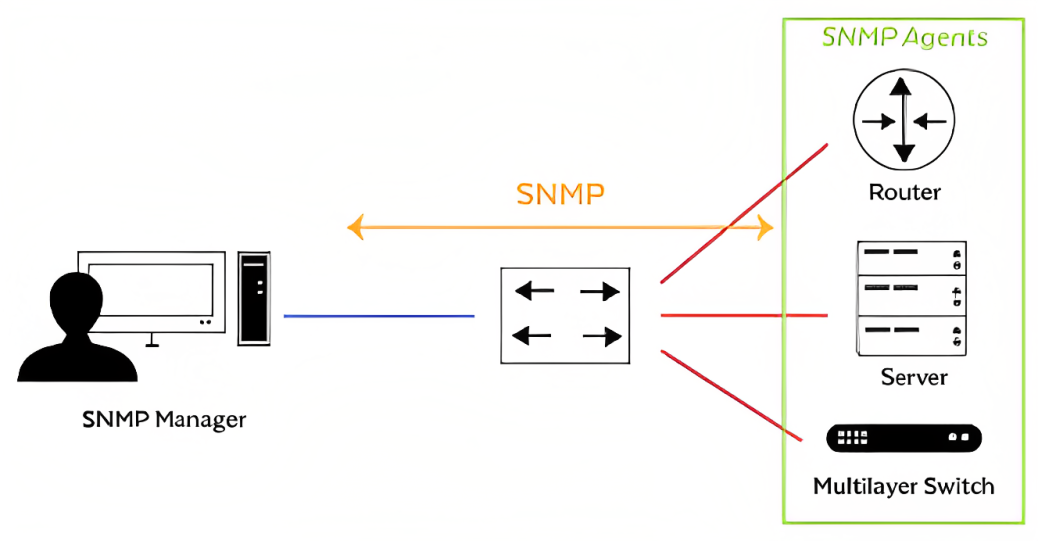
Introduction
In the world of networking, efficient management and monitoring are essential to keep systems running smoothly. One critical tool that helps achieve this is SNMP, or Simple Network Management Protocol. In this tutorial, we will explore the fundamentals of SNMP, its components, and how it can be used to enhance network performance and reliability.
Section 1: Understanding SNMP Basics
SNMP is a widely used protocol that enables network administrators to manage and monitor devices on a network. It operates on the application layer of the TCP/IP protocol stack and allows for the exchange of management information between network devices and a central management system.
SNMP Architecture
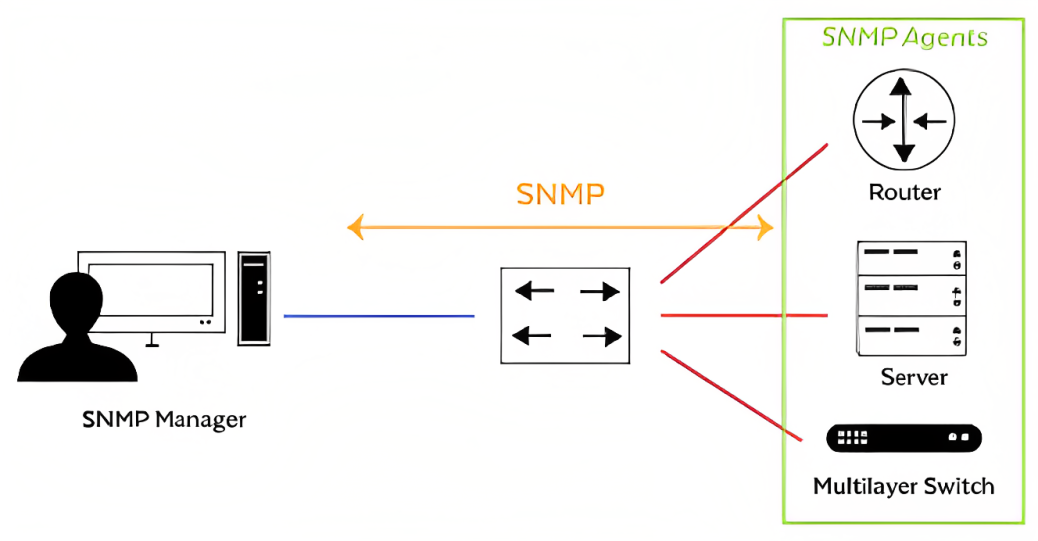
The SNMP architecture consists of three main components: managed devices, agents, and network management systems (NMS).
Managed Devices: These are the network devices that are monitored and managed using SNMP. Examples include routers, switches, servers, and printers.
Agents: Agents are software modules installed on managed devices that collect and store management information. They respond to requests from the NMS by providing data about the device’s status and performance.
Network Management Systems (NMS): The NMS is the central monitoring and management system responsible for collecting and analyzing data from the managed devices. It interacts with agents through SNMP to retrieve information about network devices.
SNMP Versions
There are three main versions of SNMP: SNMPv1, SNMPv2c, and SNMPv3. Each version has its own set of features and security levels.
SNMPv1: The first version of SNMP is relatively simple and lacks advanced security features. It uses community strings for authentication, which are essentially plain text passwords. While easy to implement, SNMPv1 is susceptible to security vulnerabilities.
SNMPv2c: SNMP version 2c introduced several improvements over SNMPv1. It added support for bulk data transfers, enhanced error handling, and more efficient mechanisms for retrieving information. However, it still relies on community strings for authentication.
SNMPv3: SNMP version 3 addressed the security concerns of its predecessors by introducing strong authentication and encryption mechanisms. It supports user-based security model (USM) and provides secure communication between agents and NMS.
Section 2: SNMP Operations
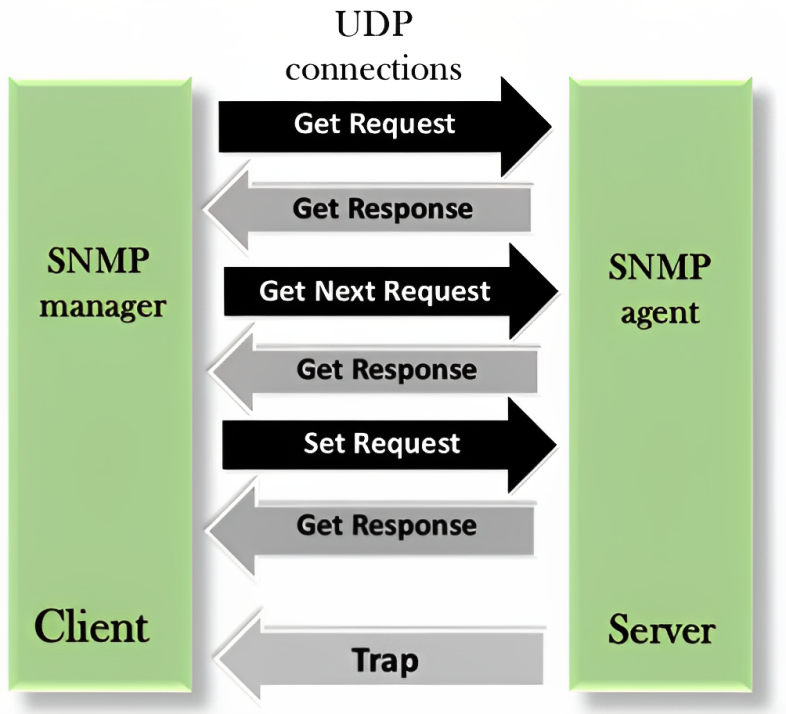
SNMP defines a set of operations that can be performed on managed devices using SNMP messages. These operations include:
Get
The Get operation allows the NMS to retrieve specific information from a managed device. The NMS sends a Get request to the agent, which responds with the requested data if available.
Set
The Set operation enables the NMS to modify specific parameters or settings on a managed device. The NMS sends a Set request to the agent, which applies the requested changes if permitted.
Trap
A Trap is an unsolicited message sent by an agent to the NMS to notify it of an event or condition on the managed device. Traps are used for real-time event monitoring and allow immediate action to be taken.
GetNext
The GetNext operation retrieves the next available variable after a specified variable in the MIB (Management Information Base) tree. It is useful for retrieving multiple variables in a single request.
GetBulk
Introduced in SNMPv2c, the GetBulk operation allows for more efficient retrieval of large amounts of data from a managed device. It reduces the number of requests needed to fetch data by retrieving multiple variables at once.
Section 3: MIB and OID
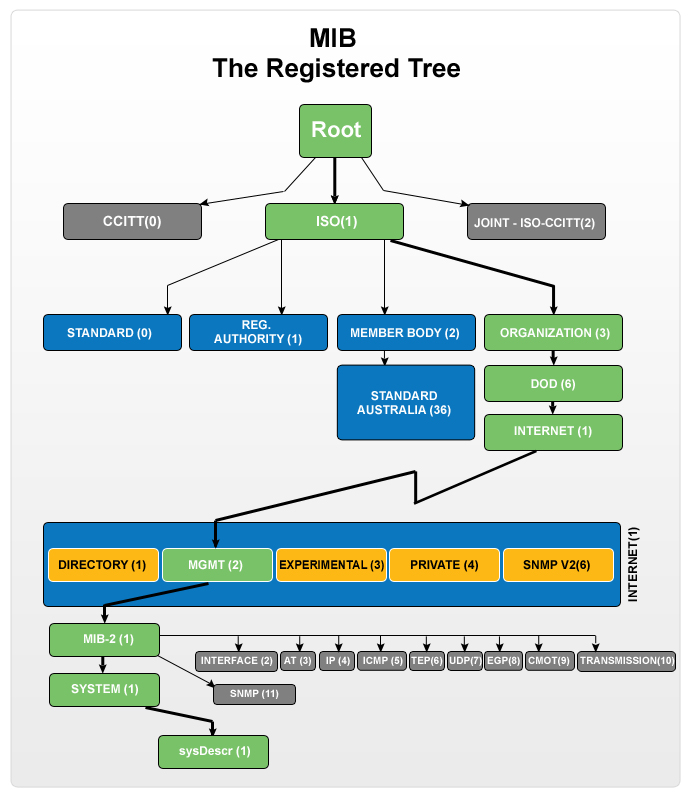
SNMP uses a hierarchical structure called the Management Information Base (MIB) to organize and represent managed device information. Each variable in the MIB tree is assigned a unique identifier called an Object Identifier (OID).
MIB Structure
The MIB structure resembles a tree-like hierarchy with branches representing different aspects of managed devices. The MIB tree is divided into different nodes, each containing related variables.
OID Syntax
OIDs are represented as a series of integers separated by dots. The first number represents the root node, followed by subsequent numbers identifying each node in the hierarchy. For example, 1.3.6.1.2.1 represents a specific OID in the MIB tree.
Section 4: SNMP Tools and Utilities
Several tools and utilities are available to facilitate SNMP management and monitoring tasks. Here are some commonly used ones:
SNMP Managers
SNMP managers are software applications used to monitor and manage network devices using SNMP. They provide a user-friendly interface to view device status, configure parameters, and receive traps.
MIB Browsers
MIB browsers allow users to navigate through the MIB tree and browse the available variables and their values. They provide a graphical representation of the MIB structure, making it easier to locate specific information.
SNMP Agents
SNMP agents are software modules installed on managed devices that collect and store management information. They respond to requests from SNMP managers and provide data about device status and performance.
SNMP Simulators
SNMP simulators simulate network devices for testing purposes. They enable network administrators to perform various SNMP operations without affecting production systems.
Section 5: Best Practices for SNMP Implementation
Implementing SNMP effectively requires following some best practices to ensure security, performance, and reliability:
Secure Community Strings
When using SNMPv1 or SNMPv2c, it is essential to configure secure community strings to prevent unauthorized access to managed devices. Use complex passwords and regularly update them to minimize security risks.
Use SNMPv3 for Enhanced Security
Whenever possible, use SNMP version 3 due to its superior security features. It provides authentication, encryption, and access control mechanisms that protect sensitive data from unauthorized access.
Limit Access Control
Implement access control lists (ACLs) to restrict access to SNMP services only from trusted IP addresses or specific networks. This helps prevent unauthorized users from accessing or modifying device configurations.
Regularly Monitor Performance Metrics
Leverage SNMP monitoring tools to track performance metrics such as CPU usage, memory utilization, network traffic, and interface errors. Analyzing these metrics helps identify bottlenecks and potential issues before they impact network performance.
Keep Firmware/Software Up-to-date
Regularly update device firmware and SNMP software to ensure compatibility with the latest standards and security patches. This helps mitigate potential vulnerabilities and ensures optimal performance.
Conclusion
SNMP is a powerful protocol that plays a crucial role in managing and monitoring network devices effectively. Understanding its basics, operations, MIB structure, and best practices for implementation is key to leveraging its full potential in maintaining stable and secure networks. By following these guidelines, network administrators can streamline their management processes and enhance overall network performance and reliability.
Subscribe to my newsletter
Read articles from Atul Sharma directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Atul Sharma
Atul Sharma
Atul Sharma is a dedicated professional and an expert in the field of networking. With his extensive knowledge and experience, he is a valuable asset to Network Kings. Atul’s passion for networking shines through in his work, as he consistently delivers top-notch solutions and strategies to clients. His ability to simplify complex concepts makes him an excellent educator, enabling him to effectively train and mentor aspiring network professionals. Atul’s commitment to staying up-to-date with the latest industry trends ensures that he is always at the forefront of networking advancements. Whether he is designing network architectures or troubleshooting complex issues, Atul’s attention to detail and problem-solving skills make him a trusted resource for Network Kings and their clients.