Cyber Security: What is File Upload
 Han
HanDefinition
File upload attacks involve malicious users uploading files to web applications or websites to exploit security vulnerabilities. Typically, web shell files are uploaded.
Cyber Security: What is Web Shell
List of Vulnerable Points
Types of uploadable files
Cases where the uploaded file path is visible and executable
Vulnerability Verification Methods
Boards with file upload functionality
Accessing the user's profile page while logged out
Cyber Security: File Upload Cheet Sheet
Attack Methods
Attack Sequence
The attacker utilizes the web application's file upload functionality to upload a file.
Determine what types of files are allowed (php, png, jpg, etc.).
Verify where the uploaded file is stored on the server and if the file path is exposed.
Check if the exposed path allows access to the file via the GET method.
Use the upload attack to extract desired information.
File Upload Structure
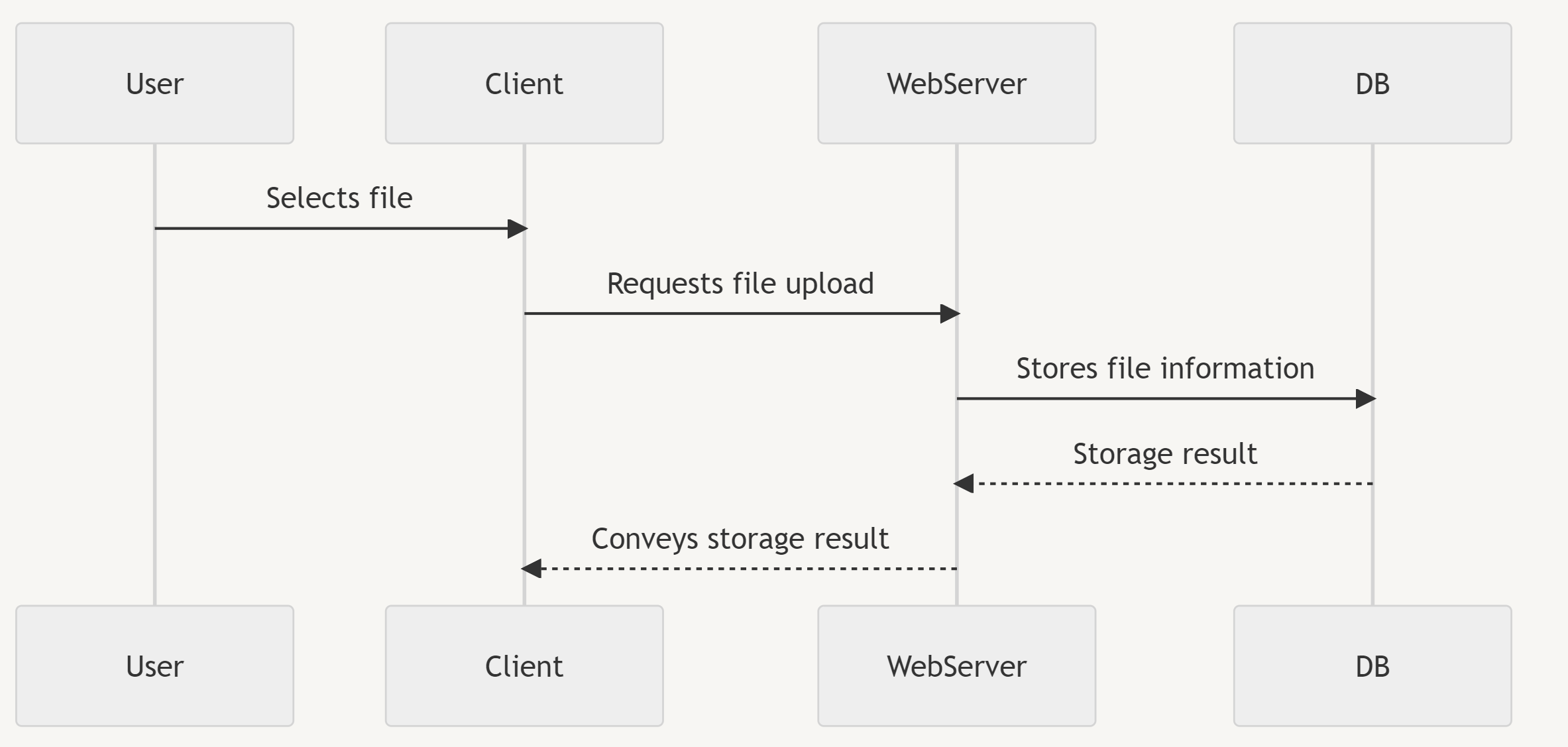
File Upload Attack Process
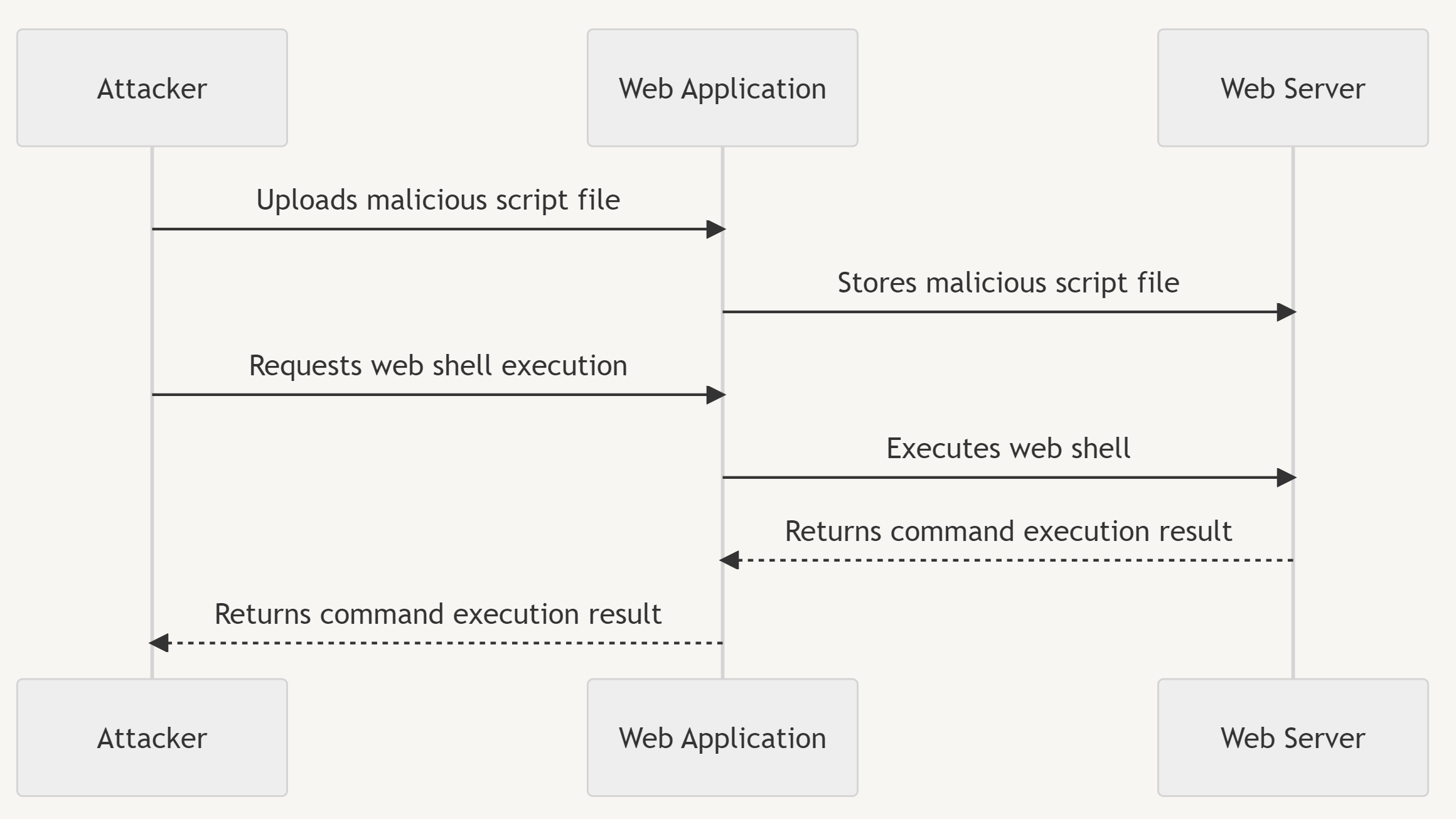
Web Shell File Upload Process
File Selection: Choose a web shell file.
File Upload Request: Server allows php files as web shell files.
File Validation: Passes validation checks.
File Information Storage: Web shell file is stored.
Convey Storage Result: Attacker receives desired information through the web shell.
Countermeasures
Strengthen File Format Validation: Validate the uploaded file's format to only allow approved file types.
File Name Verification: Check file names for validity to block malicious file names.
File Size Limitation: Set file size limits to prevent attackers from uploading large files that could deplete server resources.
Tighten Security Policies: Restrict the storage location and permissions of uploaded files on the server, and strictly apply security policies to disallow uploading executable files.
Post-Upload Event Verification: Validate post-upload events on the server to detect malicious actions and prevent unauthorized access.
Subscribe to my newsletter
Read articles from Han directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
