Building a Break Glass Solution with HashiCorp Boundary + Vault
 Sebastian Maniak
Sebastian Maniak
What is break glass?
Break Glass accounts are a type of privileged account that is used in emergencies, such as system failures or security breaches. They should be managed in a way that ensures they are only used when necessary, and that their use is auditable and traceable. Here are some best practices for managing Break Glass accounts:
Limit access: Only a small number of trusted individuals should have access to the Break Glass account, and their access should be regularly reviewed.
Establish procedures: Establish clear procedures for using the Break Glass account, including when it can be used, who can use it, and how its use should be reported.
Monitor usage: Monitor and audit the use of the Break Glass account, including who used it and when, and ensure that any suspicious activity is investigated.
Secure the account: Secure the Break Glass account with strong, unique credentials, and ensure that it is protected with multi-factor authentication.
Test regularly: Regularly test the account to ensure that it is functioning correctly and that any issues are identified and resolved.
Have an incident response plan in place: Have an incident response plan in place for when the Break Glass account is used, including procedures for restoring normal operations and identifying the cause of the emergency.
Have an expiration date: Have an expiration date for the account, and make sure to deactivate it once it’s no longer necessary.
When should we use a Break Glass Process?
Break glass is a method of providing temporary, exceptional access rights in emergency situations where normal procedures are not sufficient. It should only be used as a last resort, such as when the helpdesk or system administrator is not available. This method is often used in situations where there are account, authentication, and authorization issues. In certain companies, there may be critical tasks that need to be performed by individuals who are not normally authorized to do so. For example, a junior database admin may need to perform certain tasks of a senior database admin in case of an emergency.
The break glass solution is implemented by having a pre-prepared emergency process that can be quickly accessed without any unnecessary administrative delays.
These accounts and the procedures for accessing them should be well-documented and tested as part of the implementation process. It should be managed carefully to ensure timely access when needed.
How do we start building a Break Glass Architecture?
If we are going to build an environment that manages our Break glass infrastructure we need to ensure we follow the following Principles around zero trust for an identity-aware proxy.
Well, it should follow these Identity-Aware Principles.
Authentication: IAP requires users to authenticate before granting access to an application or resource.
Authorization: IAP uses identity information to determine whether a user is authorized to access an application or resource.
Least privilege: IAP grants users the minimum level of access necessary to perform their job functions.
Auditing and logging: IAP records all access attempts, including successful and unsuccessful ones, for auditing and compliance purposes.
Single Sign-On (SSO): IAP allows users to sign in once and access multiple applications and resources without having to re-enter their credentials.
Secure by default: IAP is designed to be secure by default, with sensible defaults and minimal configuration required.
Scalability: IAP can be used to protect applications and resources of any size, from small projects to large enterprise deployments.
(Adding ) Dynamic or Just-in-time Credentials.
Using HashiCorp Boundary + Vault as a Break Glass solution
Using HashiCorp Boundary and Vault together to implement a break glass solution. By integrating Boundary and Vault, you can use Vault’s authentication and authorization capabilities to control access to internal resources through Boundary.
In this scenario, you would set up a Break Glass policy in Vault that grants a limited set of trusted individuals access to the internal resources in the event of an emergency. This policy would be used to authenticate and authorize the users attempting to access the internal resources via Boundary. Additionally, you could use Vault’s capabilities to rotate the secrets (such as SSL/TLS certificates) that Boundary needs to establish a secure connection automatically.
You could also leverage Vault’s audit logging to track the usage of the break glass policy and create alerts when it’s activated. Additionally, you could set up a role or a user specifically for the break glass account, that way you can track who is using it, and when.
Boundary
Hashicorp Boundary is an open-source tool developed by Hashicorp, that allows users to securely access internal network resources from outside the network. It works by creating a secure connection between the client and the internal resource, using a technique called “jump” servers. This allows users to access internal resources without the need for a VPN or a direct connection.
Boundary uses mutual authentication, meaning that the client and the server must both authenticate each other before the connection is established. It also uses end-to-end encryption to protect the connection and the data being transmitted. Additionally, it integrates with various identity providers such as Okta, Auth0, and more.
Boundary can be used to access a variety of internal resources, such as databases, servers, and applications. It is often used in scenarios where users need to access internal resources from remote locations, such as when working from home or on the road. It also can be used to provide secure access to development, staging, and production environments.
Integrating HashiCorp Boundary with Vault
Hashicorp Boundary can integrate with Hashicorp Vault, which is a tool for securely storing and managing secrets and sensitive data. The integration allows Boundary to use Vault as the identity provider for authentication and authorization.
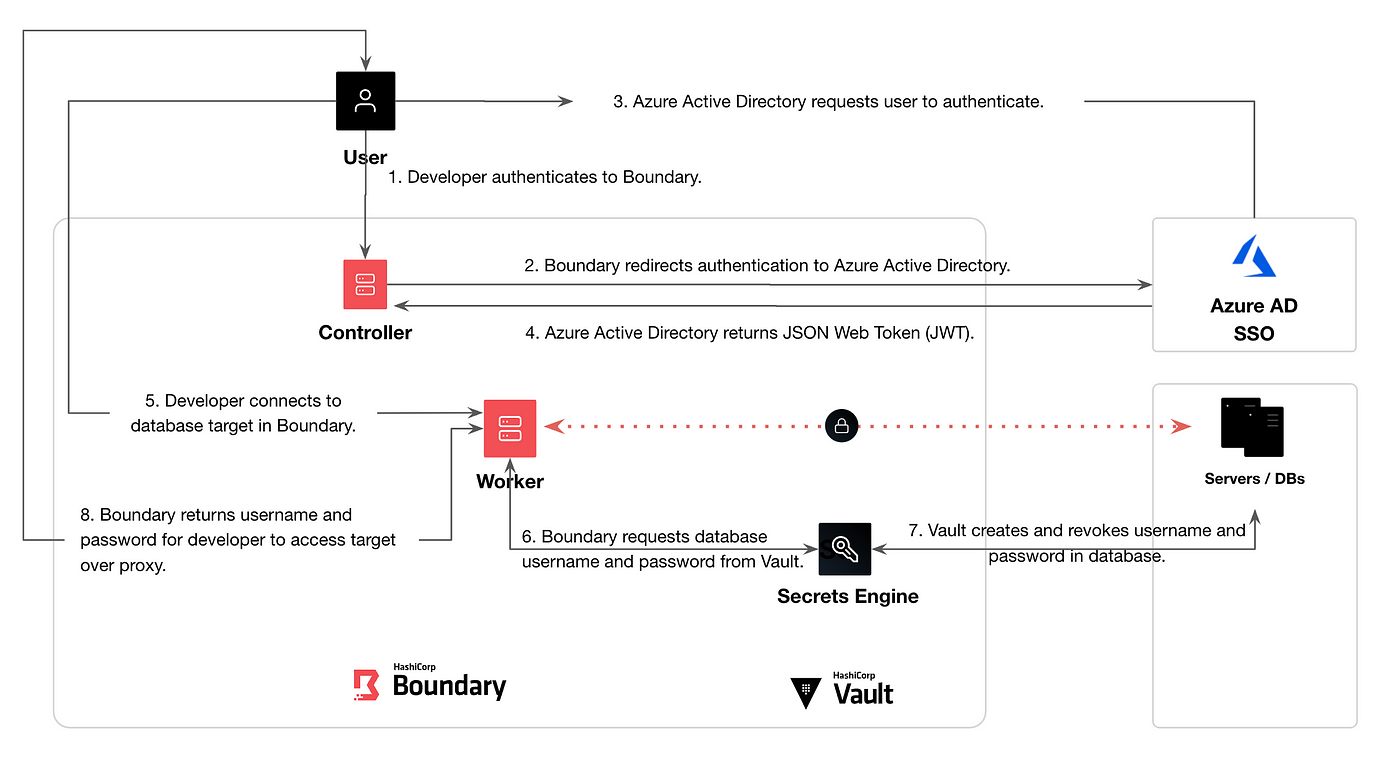
When integrating Boundary with Vault, users can authenticate to Boundary using their Vault credentials, and their access to internal resources is determined by their Vault policy. This allows organizations to use a single source of truth for authentication and authorization, and to centralize the management of access control.
Additionally, Vault can be used to store the secrets that Boundary needs to establish a secure connection, such as SSL/TLS certificates, and to rotate those secrets automatically.
The integration between Boundary and Vault can be achieved through various methods, such as using the Boundary’s API, Terraform, or using the Boundary’s CLI to configure the integration.
In all cases, the integration between Boundary and Vault would typically involve configuring Boundary to use Vault as the identity provider for authentication and authorization. This would allow Boundary to verify the identity of users and to determine their access to internal resources based on their Vault policy. Additionally, the secrets that Boundary needs to establish a secure connection, such as SSL/TLS certificates, can be stored in Vault and rotated automatically.
Subscribe to my newsletter
Read articles from Sebastian Maniak directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Sebastian Maniak
Sebastian Maniak
I build, secure and automate infrastructure. | Follow me for daily updates and code examples.