Mastering API Security: A Comprehensive Guide 🛡️
 muhammad zubair
muhammad zubairTable of contents
- 📚 Module 1: API Security Basics
- 🛠️ Module 2: Tools for API Security
- 🔐 Module 3: Authentication Attacks and Defenses
- 🔓 Module 4: Authorization Attacks and Defenses
- 🔍 Module 5: Input Validation Threats and Defenses
- 🚨 Module 6: Other API Security Threats
- 🛡️ Module 7: Other API Security Defenses
- 🔒 Module 8: Implementing API Security Mechanisms
- 🔐 Module 9: API Security, the DevSecOps Way
- 🔗 Connect with Me!
- 🎉 Conclusion: Your API Security Arsenal
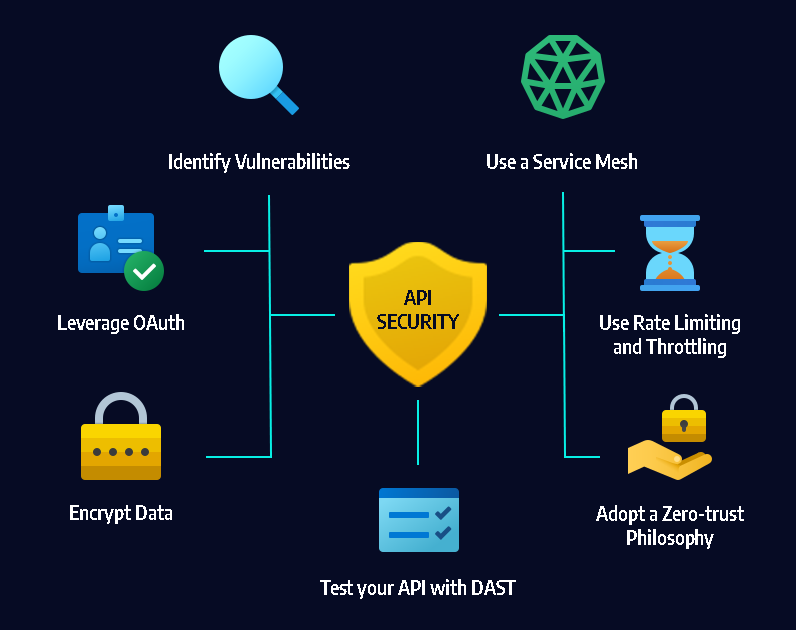
Introduction to Application Programming Interfaces (APIs) has revolutionized how software applications communicate and interact. In today's digital landscape, securing APIs has become paramount to ensure data integrity, user privacy, and overall system robustness. In this guide, we will delve deep into the world of API security, exploring its various dimensions, threats, and defense mechanisms. So, fasten your virtual seatbelts as we embark on this journey to fortify your APIs against cyber adversaries! 🔒
📚 Module 1: API Security Basics
In this module, we laid the foundation by understanding what APIs are, why they're vital, and how they differ from traditional web applications. We explored the architecture of APIs, dissected HTTP requests and responses, and learned the significance of secure API design.
🛠️ Module 2: Tools for API Security
Equipped with the right tools, we ventured into the API landscape. We discovered the crucial components of APIs, from gateways to message queues, and explored tools like cURL, Postman, and OpenAPI for effective API interactions.
🔐 Module 3: Authentication Attacks and Defenses
Authentication forms the bedrock of security, and in this module, we dove into various authentication methods, their vulnerabilities, and the strategies to fortify them. We learned how to thwart brute force attacks, secure password storage, and make OAuth an ally, not a liability.
🔓 Module 4: Authorization Attacks and Defenses
Authorization decides who can access what, making it a critical aspect of API security. We examined different authorization types, potential attacks, and concrete defenses. With OAuth as our shield, we explored token-based authorization workflows.
🔍 Module 5: Input Validation Threats and Defenses
Input validation guards against injection attacks, and in this module, we embraced the best practices. We learned about injection vulnerabilities like XSS and SQLi, and mastered the art of input validation through both client and server-side techniques.
🚨 Module 6: Other API Security Threats
The API landscape is vast, and we navigated through it by understanding the OWASP API Top 10. From broken authentication to improper asset management, we exposed potential vulnerabilities and explored methods to mitigate them.
🛡️ Module 7: Other API Security Defenses
In this module, we fortified our APIs with security headers, CORS implementations, and advanced rate limiting. We embraced the principles of data security, from hashing and encryption to securing data in transit through TLS.
🔒 Module 8: Implementing API Security Mechanisms
A robust API security design is essential, and this module equipped us with the best practices. We examined how to implement authentication, authorization, and rate limiting effectively. Securely storing secrets using Hashicorp Vault became second nature.
🔐 Module 9: API Security, the DevSecOps Way
In the DevSecOps spirit, we integrated security into every step of the development lifecycle. We harnessed the power of the OWASP ASVS framework, automated vulnerability discovery, and learned to address API security at scale.
🔗 Connect with Me!
Join me in the journey to master API security. Let's connect on LinkedIn to stay updated on the latest in cybersecurity and tech: Connect with Muhammad Zubair.
🎉 Conclusion: Your API Security Arsenal
Congratulations! You've completed a comprehensive tour of API security. From understanding the intricacies of authentication and authorization to fortifying your APIs against various threats, you're now equipped with a powerful arsenal to protect digital assets. Remember, API security is a continuous journey, so stay vigilant, stay informed, and keep evolving your defenses. Secure APIs lead to secure applications and a safer digital world. 🛡️🌐 #APISecurityMastery
Subscribe to my newsletter
Read articles from muhammad zubair directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

muhammad zubair
muhammad zubair
I am a Cybersecurity and Cloud Engineer with over 4 years of experience helping businesses improve their security posture and optimize their cloud infrastructure. I have expertise in AWS, Azure, VMware, Veeam, and Kubernetes, and I am passionate about using my skills to help companies achieve their goals.