Security Group AWS NLB (AWS new feature)
 Timur Galeev
Timur Galeev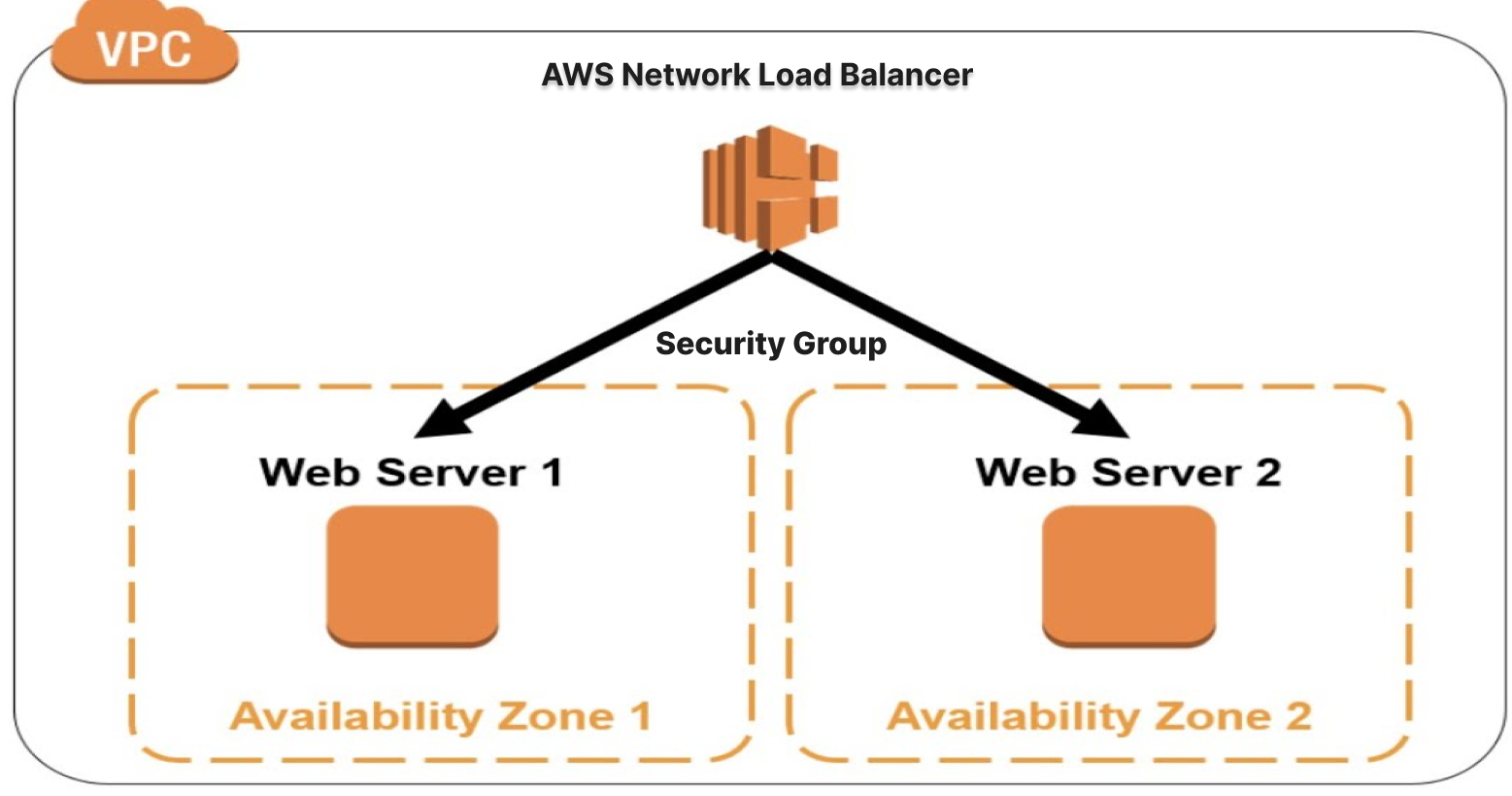
You can now create security groups in AWS Network Load Balancer (AWS NLB)
With this update, you can configure rules to ensure that your NLB only accepts traffic from trusted IP addresses, and centrally enforce access control policies
If you are using EKS just update your LB controller to 2.6.0 version and configure it🫡
Please check out more information here:
https://aws.amazon.com/about-aws/whats-new/2023/08/network-load-balancer-supports-security-groups/
https://docs.aws.amazon.com/elasticloadbalancing/latest/network/introduction.html
Let's jump deep

A crucial aspect of configuring an NLB is setting up security groups to control inbound and outbound traffic to and from the load balancer. A security group acts as a virtual firewall, allowing only specific traffic to reach the NLB based on predefined rules. This article will discuss how to configure security groups for an AWS NLB.
Creating a Security Group for NLB
To create a security group for an NLB, follow these steps:
Log in to the AWS Management Console and navigate to the VPC dashboard.
Click on "Security Groups" in the left-hand menu, then click the "Create security group" button.
Enter a name and description for the security group, select the VPC in which to create it, and click "Create."
Configuring Inbound Rules
Once the security group is created, you need to configure inbound rules to allow traffic to reach the NLB. To do this, follow these steps:
Click on the security group you just created.
Click the "Edit inbound rules" button.
Add a rule for each type of traffic you want to allow, specifying the protocol, port range, and source. For example, if you want to allow HTTP traffic from anywhere, add a rule with the following settings:
Type: Custom TCP Rule
Protocol: TCP
Port range: 80
Source: 0.0.0.0/0 (or a specific IP address or range)
Click "Save rules" to apply the changes.
Configuring Outbound Rules
By default, outbound traffic is allowed from an NLB. However, you can configure outbound rules to restrict the types of traffic that can leave the NLB. To do this, follow these steps:
Click on the security group you just created.
Click the "Edit outbound rules" button.
Add a rule for each type of traffic you want to allow, specifying the protocol, port range, and destination. For example, if you want to allow all outbound traffic, add a rule with the following settings:
Type: Allow All Traffic
Protocol: All
Port range: All
Destination: 0.0.0.0/0 (or a specific IP address or range)
Click "Save rules" to apply the changes.
Best Practices for Configuring Security Groups
When configuring security groups for an AWS NLB, follow these best practices:
Allow only the minimum necessary traffic: Only allow the specific types of traffic that your application requires. This reduces the attack surface and helps prevent unauthorized access.
Use specific sources and destinations: Instead of allowing all traffic from anywhere, specify a specific IP address or range. This provides an additional layer of security.
Use security groups in combination with network ACLs: Security groups and network access control lists (ACLs) work together to provide an additional layer of security. While security groups are stateful, meaning that they track the state of connections and allow return traffic, network ACLs are stateless and do not track the state of connections.
Regularly review security group rules: Regularly review your security group rules to ensure that they still meet your needs and are up-to-date with any changes in your application requirements.
Conclusion
Configuring security groups for an AWS NLB is a crucial aspect of setting up and securing your load balancer. By following the best practices outlined in this article, you can ensure that only the necessary traffic is allowed to reach your NLB and that your application remains secure.
Subscribe to my newsletter
Read articles from Timur Galeev directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Timur Galeev
Timur Galeev
AWS Community Builder / Cloud Architect / IT Lead / MLOps