What is LDAP Injection
 Han
HanDefinition
LDAP (Lightweight Directory Access Protocol) injection is a security vulnerability that occurs when user-input data is used in LDAP queries without proper validation or sanitization. This can lead to unauthorized access or manipulation of data within an LDAP directory.
List of Vulnerable Points
Anywhere user input is used for authentication
Login identifiers, passwords
Vulnerability Verification Method
- Verify if manipulated LDAP queries are inserted and executed in user input values.
USERNAME>(&)
LDAP (Lightweight Directory Access Protocol)
LDAP is a protocol used to implement network directory services, used to store and retrieve directory information such as users, groups, and devices.
What is LDAP(Lightweight Directory Access Protocol)
Network Directory Services
Network directory services are systems designed to centrally manage information such as users, resources, and services in a computer network. The primary purpose is to efficiently perform user identification, authentication, authorization management, resource retrieval, and access.
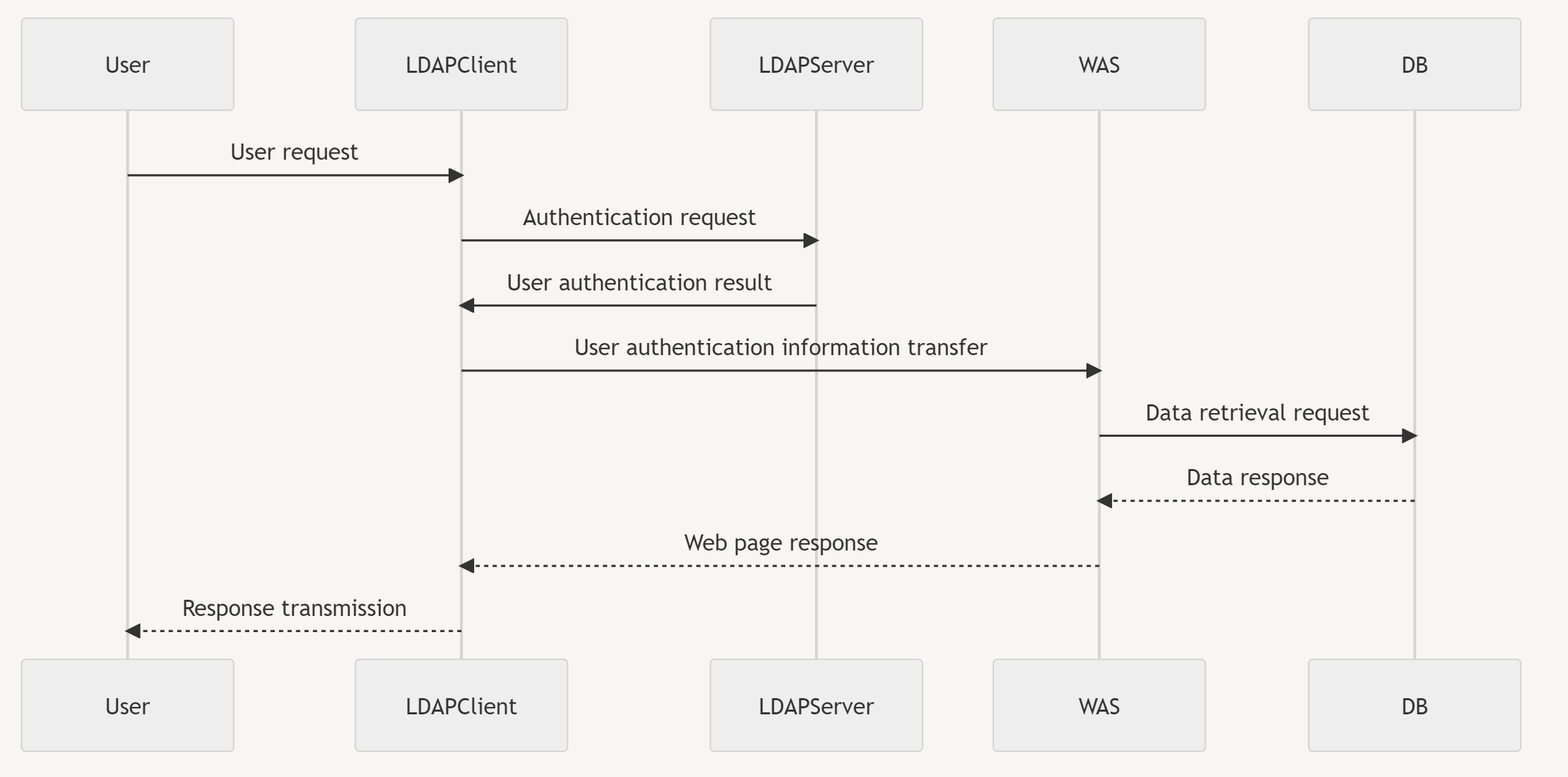
LDAP, LDAP Server, WAS, DB Structure
Attack Method
Attack Scenario
The attacker manipulates malicious LDAP queries and passes them to a vulnerable application.
The application uses user input for LDAP queries without proper validation.
The manipulated LDAP query is executed, resulting in unauthorized access or data manipulation within the LDAP directory.
Attack Process
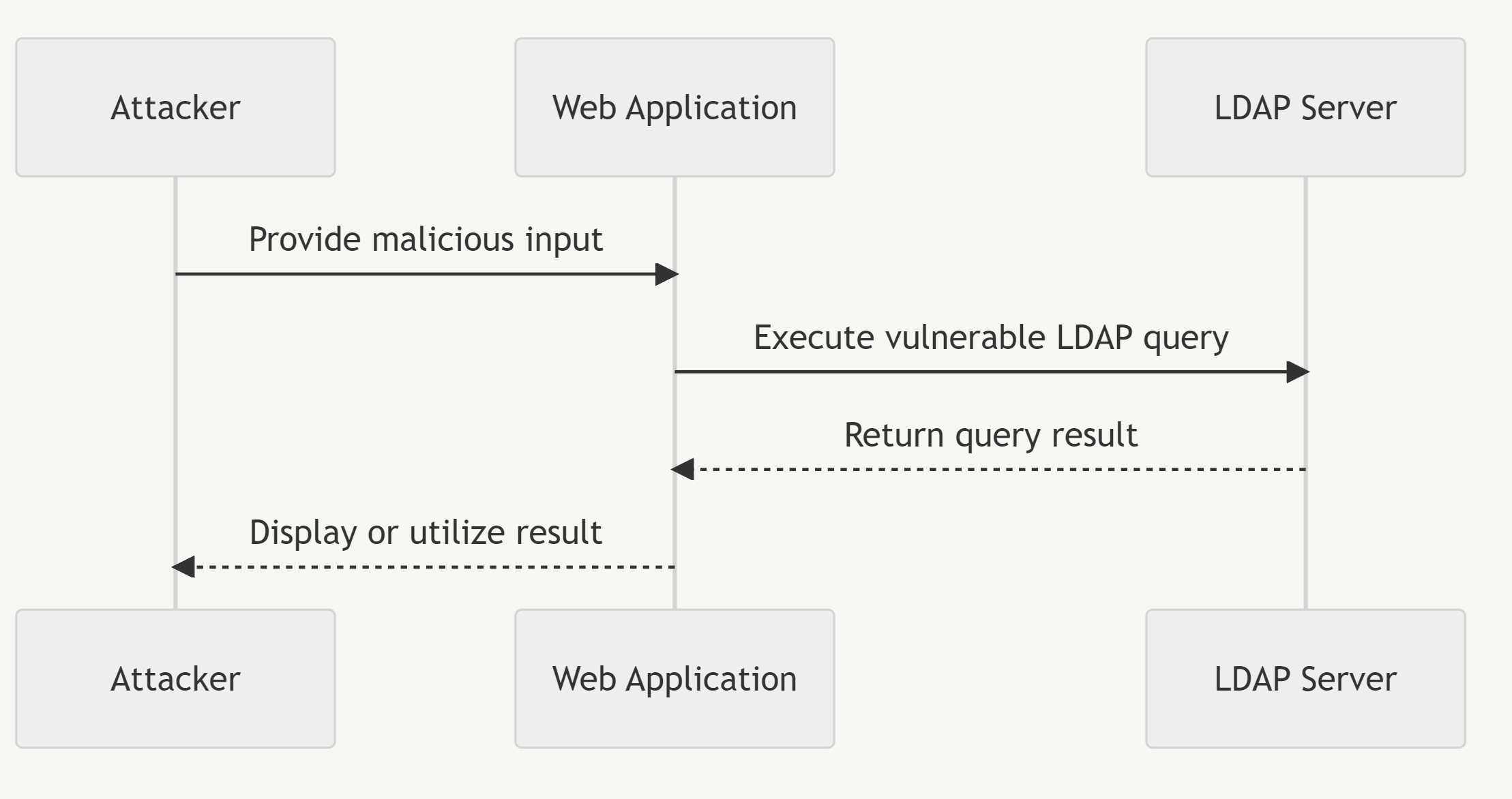
Detailed Process Explanation
The attacker provides malicious input, passing it to the application.
The application executes the vulnerable LDAP query without proper user input validation.
The vulnerable LDAP query is sent to and executed by the LDAP server.
The LDAP server processes the query and returns the result to the application.
The application displays the result to the user or utilizes it for other purposes.
Mitigation Strategies
Use prepared statements.
Implement whitelist-based filtering to allow only alphanumeric characters (a-z, A-Z, 0-9).
Minimize access permissions to the LDAP server, restricting application accounts to the least necessary privileges.
Apply rulesets to web firewalls to filter LDAP-related special characters.
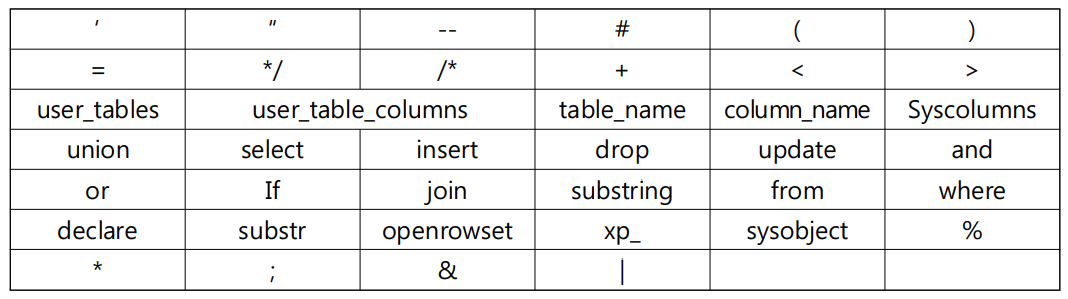
Target filtering:
Subscribe to my newsletter
Read articles from Han directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
