Walkthrough on How to Manage Role Based Access Control (RBAC)
 Orintunsin ayotunde
Orintunsin ayotunde
Introduction - In today's digital landscape, data security and privacy are paramount concerns for organizations and individuals alike. Whether you're running a small blog or managing a complex enterprise system, controlling who has access to your resources is crucial. This is where Role-Based Access Control (RBAC) comes into play.
RBAC is a widely adopted access control model that helps you manage access efficiently and securely. It provides a structured framework for assigning and controlling permissions within an organization's systems and applications. In this blog post, we'll take a closer look at RBAC and guide you through the fundamentals of implementing and managing access using this powerful approach. This blog post aims to demonstrate the process of role assignment, viewing activity logs, and removing role assignments on Azure portal
STEP 1 - Sign in to Azure: Log in to your Azure portal (https://portal.azure.com).

STEP 2 - Create a Resource: Click on the "+ Create a resource" button on the Azure portal's dashboard.
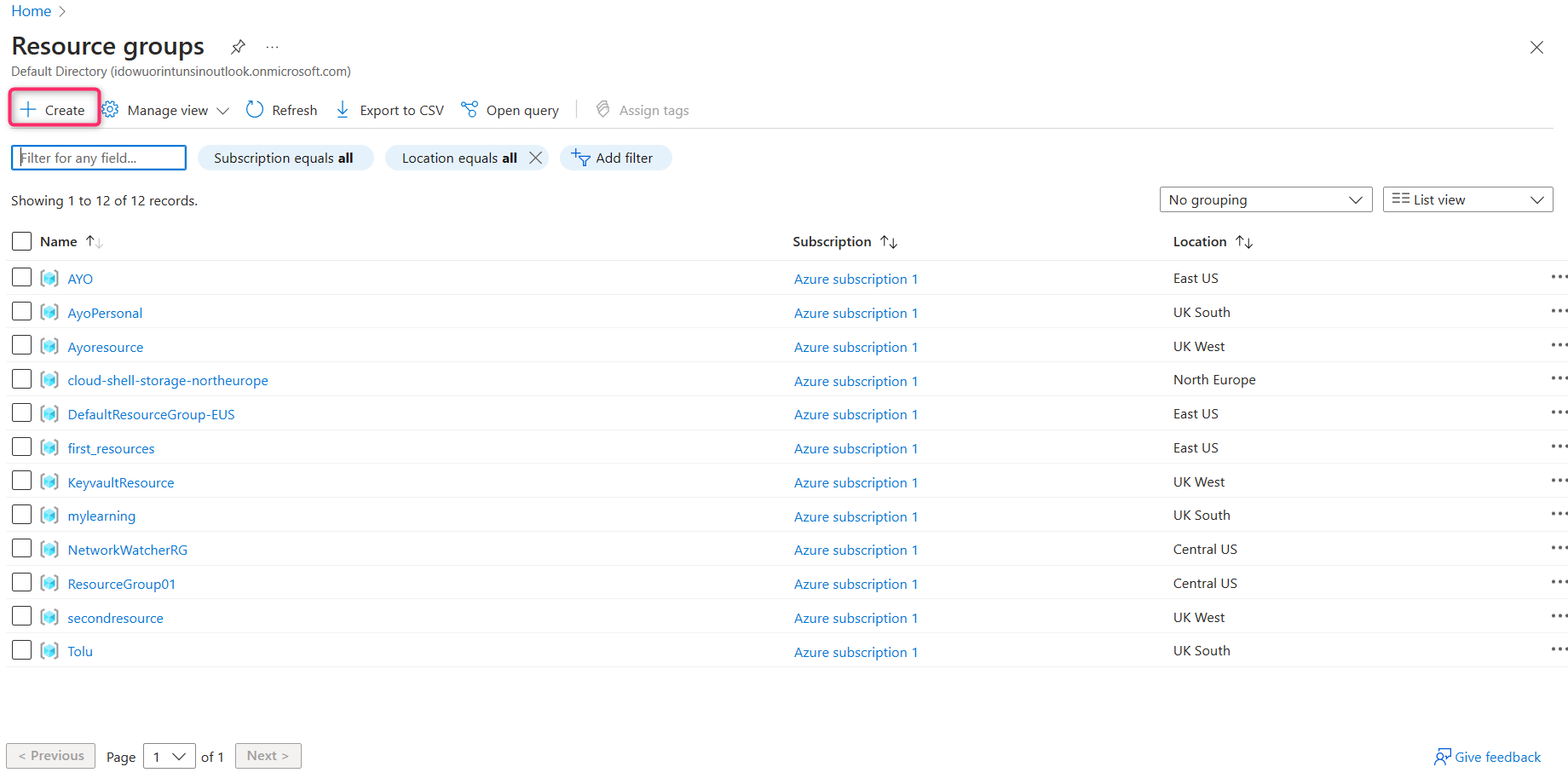
STEP 3 - Fill in the project details and select your subscription, resource group and the appropriate region.
An Azure subscription is your passport to the powerful and versatile Microsoft Azure cloud platform. It's more than just an access key; it's your gateway to a world of computing resources, services, and solutions. With an Azure subscription, you gain the ability to harness the cloud's potential, enabling you to build, deploy, and manage applications, store data, and scale your infrastructure securely and efficiently. This introduction will unravel the key components and benefits of an Azure subscription, providing you with a foundational understanding of how it can empower your digital endeavours.
Choosing a distinctive and easily recognizable name for your Resource group is crucial. Lastly the Azure Regions are geographically dispersed data center locations that provide cloud services. These regions ensure data residency, high availability, and low-latency access, allowing businesses to deploy and scale their applications and services globally while adhering to compliance and performance requirements. Understanding Azure Regions is vital for optimizing cloud infrastructure and ensuring data sovereignty, as each region may offer unique services and capabilities tailored to specific needs
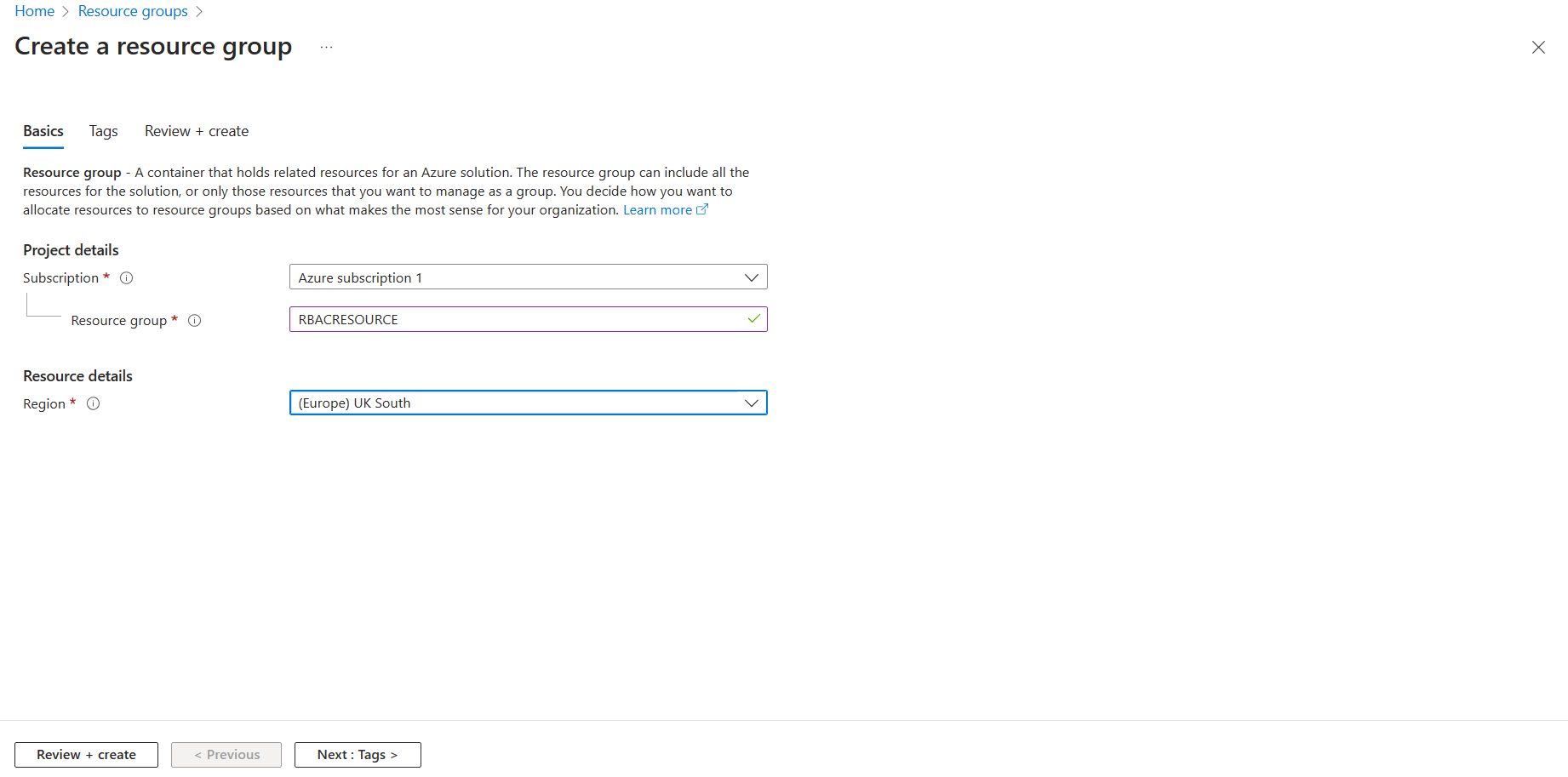
STEP 4 - Once the resource group has been created, click on access control (IAM).
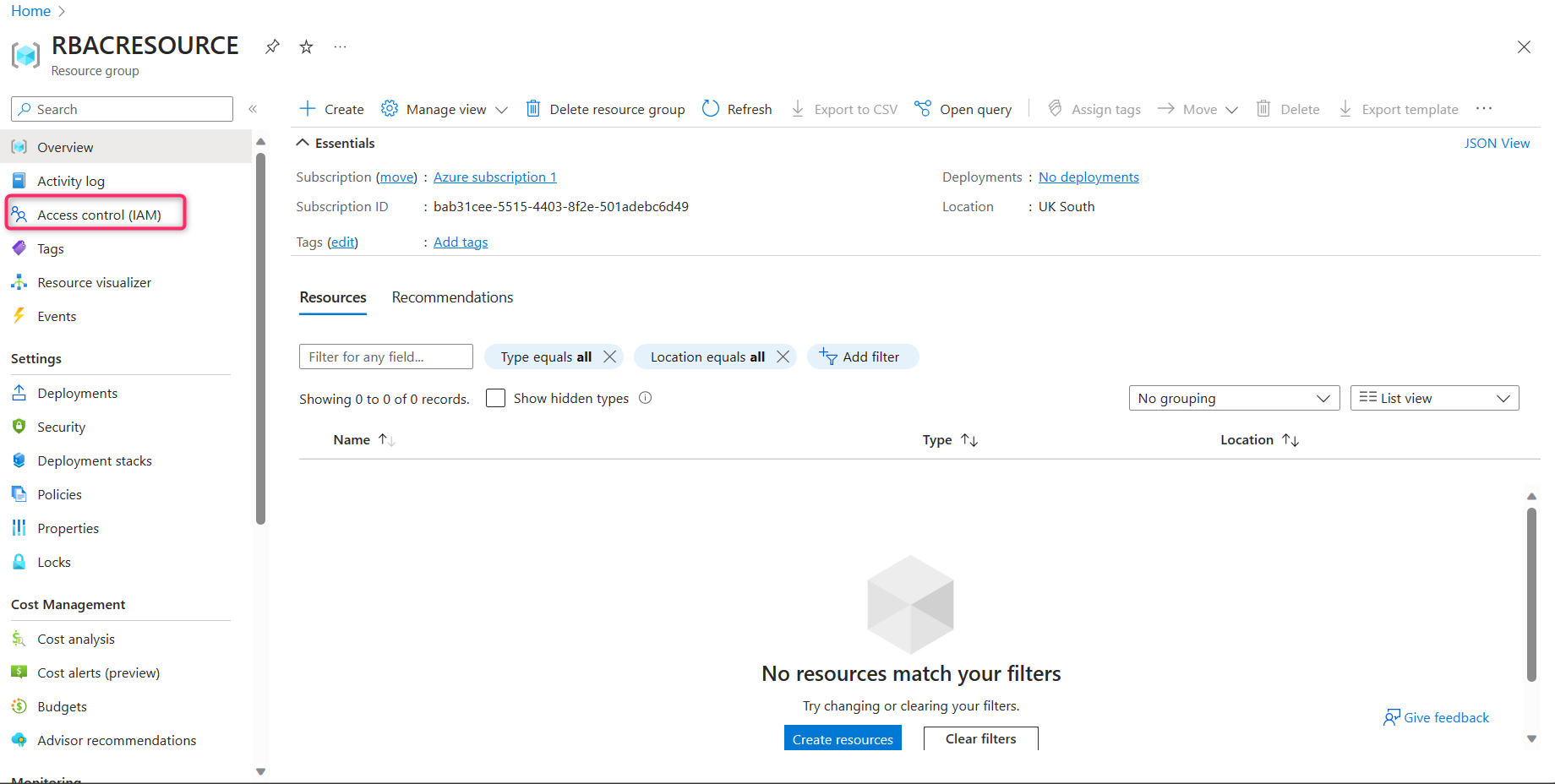
STEP 5 - In the Access Control section, you'll find various choices, such as verifying access, role assignments, roles, denial of assignment, and classic administrators. In this instance, our goal is to 'include' a role. Simply select 'add role assignment'.
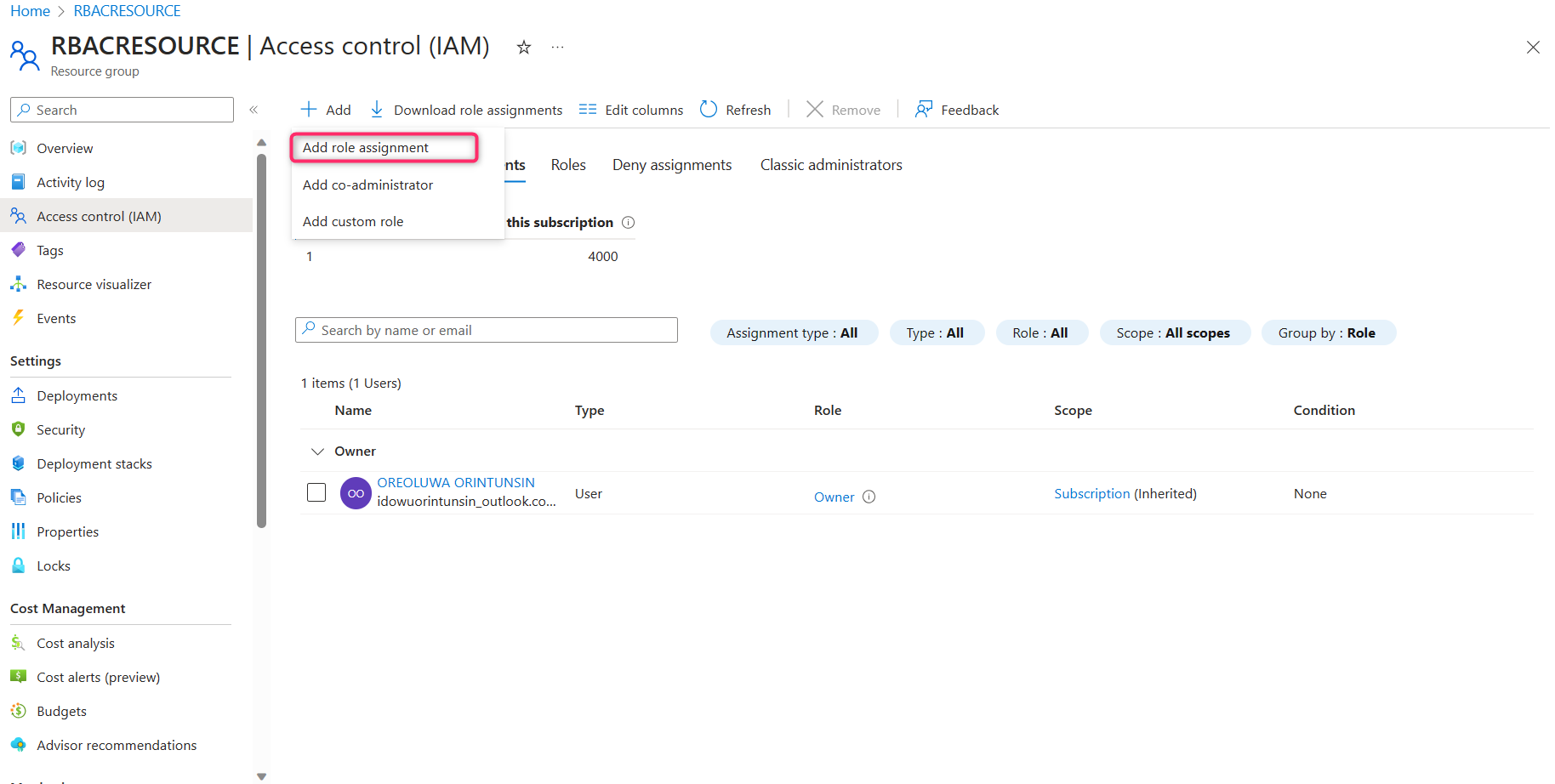
STEP 6 - In this step, we are going to designate a Virtual Machine Contributor. To do this, search for 'Virtual Machine Contributor,' select it, and proceed by clicking 'Next.'
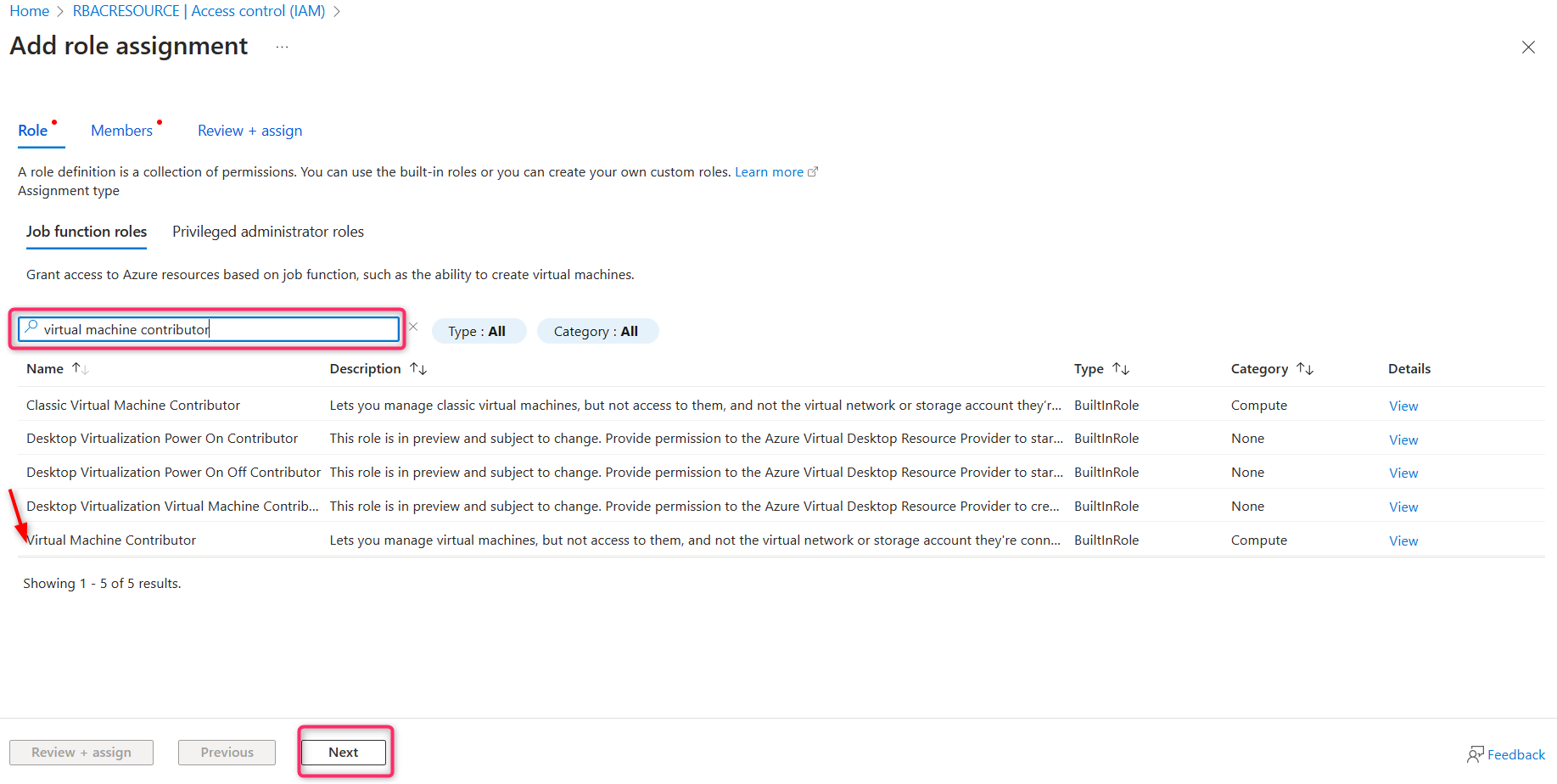
STEP 7 - Assign the role to an individual (using their email address) based on their particular role, whether they are an employee, customer, service user, or fit into any other relevant category. You can also add a description, once the description as been added click on 'Next'
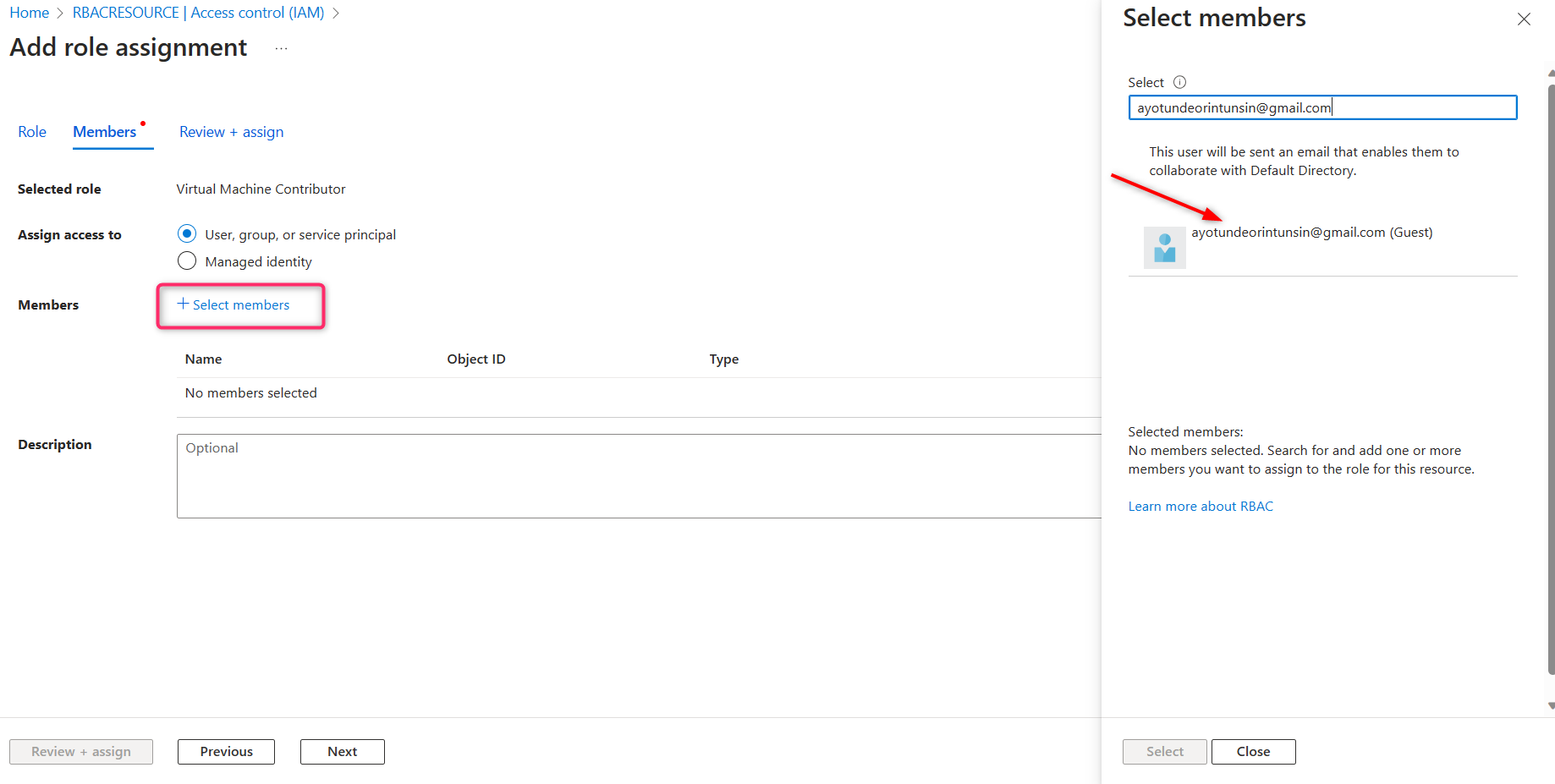
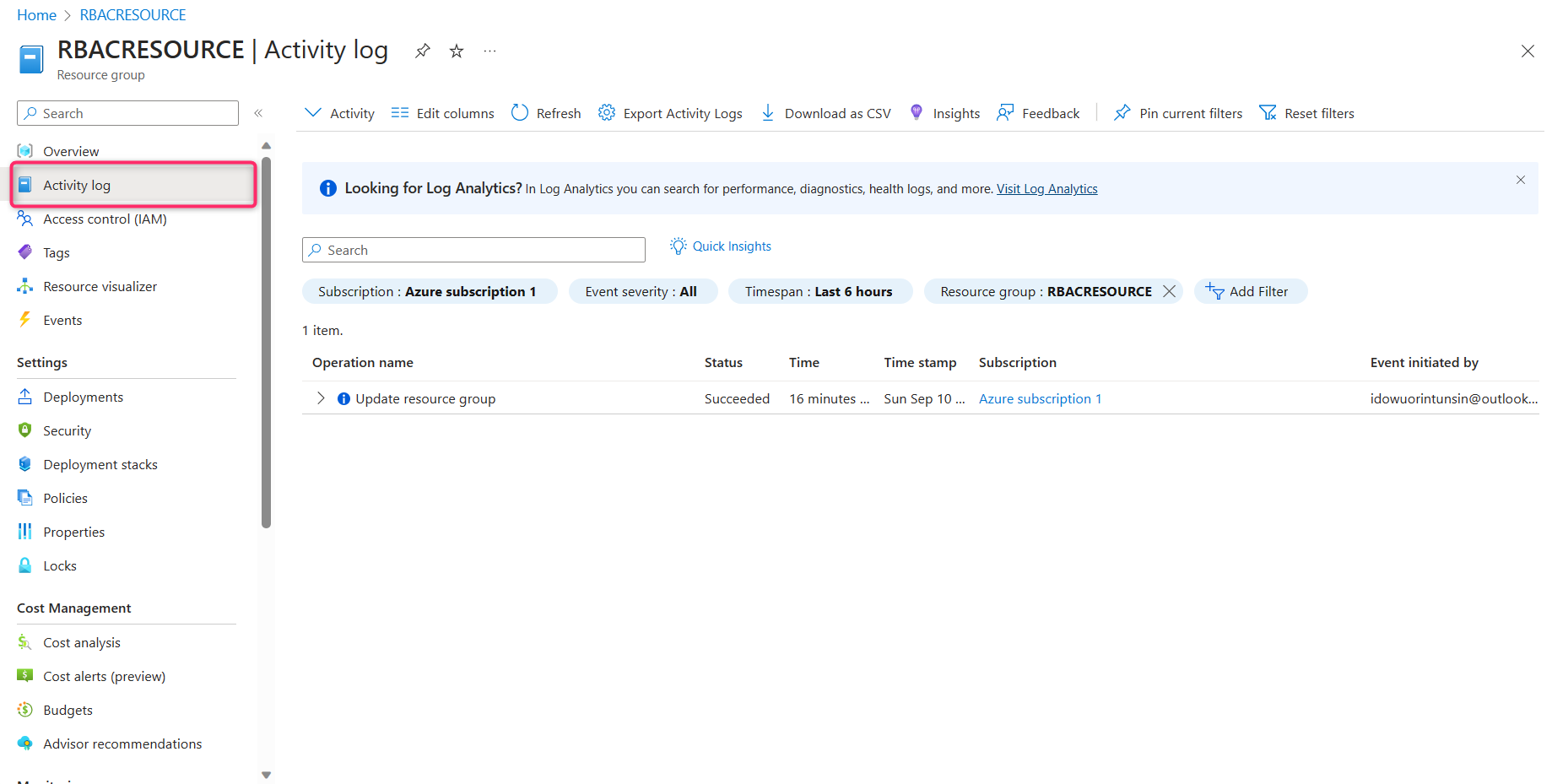
STEP 8 - Check the Activity Log to review the actions performed by your VM contributor. Once the contributor's role has been fulfilled, you can proceed to remove their access.
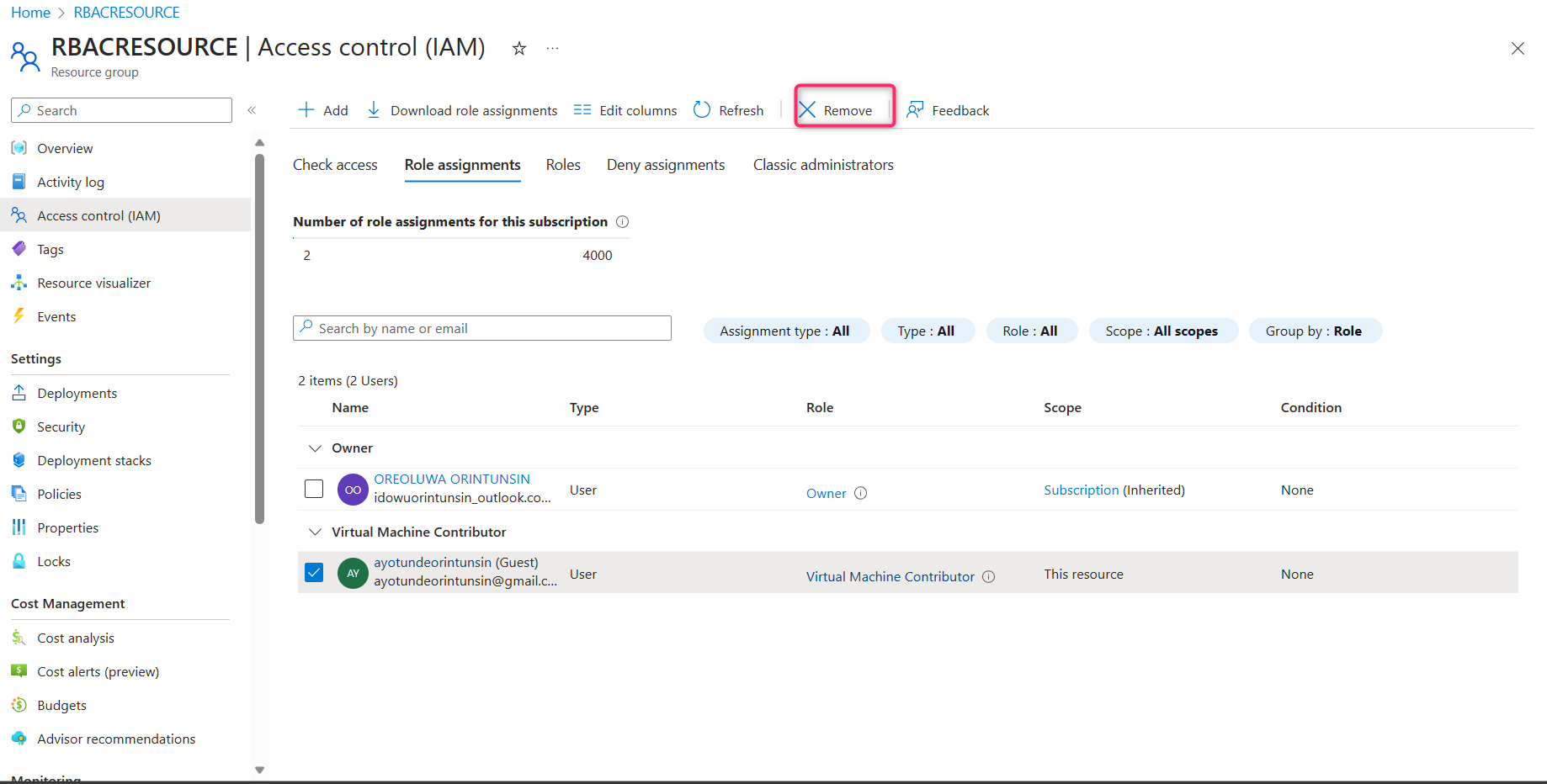
In conclusion, this walkthrough has illuminated the essential aspects of managing Role-Based Access Control (RBAC) effectively. From defining roles and permissions to assigning them based on user roles, we've delved into the core principles of access control. Understanding and implementing RBAC not only enhances security but also streamlines administration, making it adaptable to various organizational needs.
Remember, RBAC is a powerful tool for controlling who can access your resources, and it's vital for ensuring data privacy and compliance. By following these steps and best practices, you can master RBAC and confidently manage access to your systems, whether you're running a small blog or overseeing a complex enterprise environment. Stay vigilant, review regularly, and adapt your access control as your organization evolves for the utmost security and efficiency.
Thank you
Subscribe to my newsletter
Read articles from Orintunsin ayotunde directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
