Inside the Network Layer
 Samiksha Kute
Samiksha Kute
Understanding how data travels through the internet is like peeling back the layers of an onion. In this blog, we'll focus on one of those layers, the Network Layer. We'll explore how routers guide data packets to their destinations and how IP addresses help in this journey. Plus, we'll uncover the secrets of subnetting and middle boxes like firewalls and NAT that keep our online world safe and efficient.
Network Layer
In the Network Layer, we work with routers, which play a crucial role in facilitating data transfer from one part of the network to another. Let's explore how this process happens.
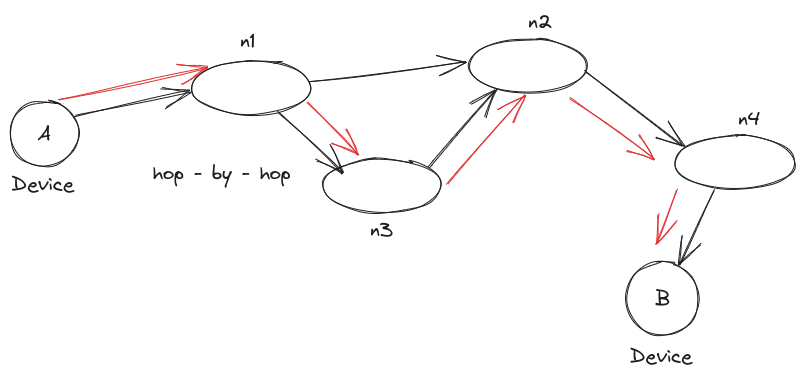
Imagine you want to send data from computer A to computer B. Between these computers, multiple routers are interconnected. Each router in the figure representing the entire Internet has its own unique network address. This network address is essential for enabling the routing of data packets across the network.
When a data packet is sent, it contains the network layer address of the destination and the information we want to transmit. The router that receives this packet, say Network 1 (n1), checks its routing table or forwarding table (a part of the routing table). This table contains information about various destination addresses.
Using the forwarding table, the router determines the next hop or the next router the packet should be sent to in order to reach its final destination. This process is known as hop-by-hop forwarding, where the packet traverses from one router to another until it reaches the correct router that can deliver it to the intended recipient.
Let's take an example: If n1 router receives a packet and realizes it's not meant for its own network layer address, it will consult its forwarding table to identify the appropriate next router to forward the packet. This process continues until the packet reaches the correct router that can deliver it to the intended destination.
Inside each router, there are both forwarding tables and routing tables. The routing table may contain multiple paths to various destinations, while the forwarding table holds only one path, making it faster to process.
Every router in the network has its own unique network layer address, while each device connected to the network has its own MAC address. When we talk about IP addresses, they consist of four parts. For example, in the IP address 192.168.2.30, the "192.168.2" part represents the network address, indicating the network in which the device resides, and the ".30" part represents the device address within that network.
This is how routing takes place in the Network Layer, ensuring that data packets are efficiently delivered across interconnected routers to reach their intended destinations.
Control Plane
You may wonder who creates the routing tables and adds destination addresses to routers. How does a router know where to forward data packets and such? The answer lies in the control plane.
The control plane is responsible for building these routing tables, and we can think of every router as a node in a graph, where the links between routers represent the edges.
There are two types of routers used to create these tables:
Static routing: This involves adding addresses manually, which can be time-consuming and not adaptive to network changes.
Dynamic routing: This method evolves based on changes in the network. It uses path-finding algorithms, such as Dijkstra's or OSPF (Open Shortest Path First), to determine the best routes dynamically.
Now, let's delve into protocols:
IP (Internet Protocol)
IP resides in the network layer and handles routing, control plane operations, and mainly deals with IP addresses. Devices connected to the IP network are known as IP hosts.
IPv4
IPv4 uses 32-bit numbers divided into 4 octets (words).
For example, an IP address like 5.6.9.14 consists of four 8-bit numbers, totaling 32 bits.
IPv4 uniquely defines servers, clients, nodes, or routers.
IPv6
- IPv6 is considered the future as it addresses the potential exhaustion of IPv4 addresses. IPv6 uses 128 bits, offering a significantly larger address space.
IPv4 vs IPv6
IPv4: 232 ~ 4.3 billion
IPv6: 2128 = 3.4 * 1038
Cons: IPv6 is not backward compatible with IPv4, which means that devices using IPv4 might not directly communicate with devices using IPv6.
Migrating to IPv6 would require significant hardware and infrastructure changes for Internet Service Providers (ISPs) and network operators.
How it is represented?
IPv6 addresses are represented in eight groups of hexadecimal digits, with each group containing 16 bits.
For example: ABFE:F001:3210:9182:0:0:1:3
Previously, we discussed an IPv4 address like 127.0.0.0/8, where "8" represents the subnet prefix length.
Similarly, in IPv6, we can represent a subnet like ABFE:F001:2210:9182::/60.
Regarding the concept of hopping, routers don't serve someone else's traffic directly. The hopping process occurs at the level of ISPs (Internet Service Providers). ISPs manage blocks of IP addresses, not individual addresses.
This practice is known as subnetting. For instance, if we have an IP address like 192.168.2.30, all devices in the same network will start with 192.168.2, which is the subnet ID, leaving the host ID for individual devices.
The Internet Society created classes of IP addresses for this purpose, and there are five classes:
A: 0.0.0.0 - 127.255.255.255
B: 128.0.0.0 - 191.255.255.255
C: 192.0.0.0 - 223.255.255.255
D: 224.0.0.0 - 239.255.255.255 (reserved for multicast groups)
E: 240.0.0.0 - 255.255.255.255 (reserved for experimental purposes)
To help manage IP addresses and determine network boundaries, subnet masks come into play. A subnet mask masks the network part of the IP address, leaving the host part for use.
Let's consider a simple example to understand subnetting and how subnet masks work:
Imagine you have a local network in your home, and you want to divide it into smaller subnetworks to manage devices efficiently. You have the IP address range of 192.168.1.0/24, where the "/24" means that the subnet mask is 255.255.255.0.
With this subnet mask, the first 24 bits of the IP address are dedicated to the network part, and the remaining 8 bits are for the host part.
So, let's assign IP addresses to devices within this network:
Router: 192.168.1.1 (The default gateway for the network)
Laptop 1: 192.168.1.2
Laptop 2: 192.168.1.3
Printer: 192.168.1.4
Smart TV: 192.168.1.5
All these devices belong to the same network because their IP addresses have the same network part (192.168.1). The last part (the host part) differentiates each device.
Now, let's say you want to create two smaller subnetworks to separate certain devices. You decide to use variable length subnetting with a subnet mask of 255.255.255.128 (or /25 in CIDR notation), which gives you two subnets with 128 available addresses in each.
Subnet 1:
Subnet IP range: 192.168.1.0/25
Valid host IP range: 192.168.1.1 to 192.168.1.126
Broadcast address: 192.168.1.127
Subnet 2:
Subnet IP range: 192.168.1.128/25
Valid host IP range: 192.168.1.129 to 192.168.1.254
Broadcast address: 192.168.1.255
Now, you can assign IP addresses to devices in each subnet:
Subnet 1:
Router: 192.168.1.1
Laptop 1: 192.168.1.2
Laptop 2: 192.168.1.3
Subnet 2:
Printer: 192.168.1.130
Smart TV: 192.168.1.131
By subnetting the network, you have separated the devices into two smaller subnetworks, making it easier to manage and control the traffic flow. Each subnet can have its own unique settings and configurations, helping you improve network performance and security.
The Internet Engineering Task Force (IETF) is responsible for assigning IP addresses to ISPs. They no longer concern themselves with classes and instead opt for regional IP address assignments. The reason for this approach is to minimize the number of hops required when finding IP addresses.
Certain IPv4 addresses are reserved and considered special addresses. For instance, the first set of addresses, denoted by 127.0.0.0/8, are reserved for specific purposes like localhost. These addresses are known as loopback addresses. They allow processes running on your machine using the TCP/IP protocol to communicate with each other. In other words, your device can act as both a client and a server, like in the case of localhost. Loopback addresses are always available and can be used without any restrictions. You can have as many loopback addresses as needed for various purposes.
Packets
In addition to the actual data being sent, a packet consists of a 20-byte header. This header contains important information such as the IP version, total length of the packet, identification number, flags, protocols, source and destination addresses, and the Time to Live (TTL).
The TTL, which stands for "Time to Live," is a critical part of the packet header. It represents the maximum number of hops (routers) the packet can travel through the network before it is discarded or dropped.
In the example given, if the packet cannot reach its intended destination within 116 hops, the packet will be dropped.
Middle Boxes
In addition to end systems (computers) and routers, there's another type of device called middle boxes that work with the packets traveling through the network. These middle boxes play a role in allowing, rejecting, or modifying packets as needed.
Think of middle boxes as extra helpers that interact with the IP packets in the network layer, though they can also be found in the transport layer. An example of a middle box is a Firewall.
Firewall
Firewalls come in two types:
The first type is connected to the global network, meaning it interacts with packets going to and coming from the internet.
The second type is connected to a trusted network, such as your home or office network.
Firewalls provide filters that control the flow of packets based on various criteria, like source and destination addresses, port numbers, flags, and protocols.
There are two main types of firewalls based on how they operate:
Stateless firewalls do not maintain any memory about previous packets they've seen. Each packet is treated independently.
Stateful firewalls, on the other hand, remember the state of previously seen packets and can use that information to make more informed decisions about incoming packets. This memory storage allows them to be more efficient in processing packets.
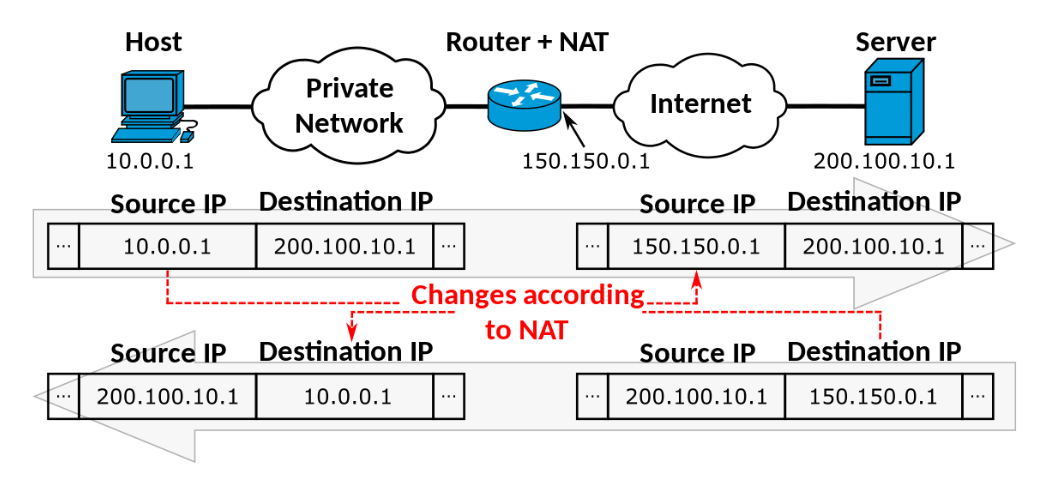
NAT - Network Address Translation Another essential middlebox is NAT.
Network Address Translation (NAT) is like a translator for computer networks. It helps devices in your home network talk to each other and connect to the internet.
In your home network, each device has a special address known as a private IP address. However, these private addresses are not unique worldwide. When a device wants to access the internet, NAT changes its private IP address into a single public IP address that the internet understands.
NAT is necessary because there aren't enough public IP addresses to go around. With NAT, multiple devices can use the same public IP address, saving space and allowing them to access the internet together. It also adds a layer of protection by keeping private IP addresses hidden from the internet, making it harder for attackers to target individual devices.
For more information, you can visit: https://en.wikipedia.org/wiki/Network_address_translation
That's it. Thank you for reading. I hope this article was helpful. Check out the complete Computer Networking Series for more such content 👇
Let's get connected:
Subscribe to my newsletter
Read articles from Samiksha Kute directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Samiksha Kute
Samiksha Kute
Passionate Learner!