Open Policy Agent (OPA) in Terraform (IaC)
 Jayakumar Sakthivel
Jayakumar Sakthivel
What is OPA?
The Open Policy Agent (OPA) is a general-purpose policy engine that can assess Rego-expressed rules using information compiled in JSON format from various sources. A policy's enforcement may make use of an evaluation's findings.
It offers an integrated framework for policy enforcement and may be used with a variety of technologies and platforms, such as Kubernetes, Terraform, and others. The strength of OPA lies in its policy language and the virtual document it creates to assess Rego's rules. When OPA runs, it uses JSON data and Rego policies to analyze rules and determine each rule's response value based on a query.
What is Rego?
The OPA policy is written in the Rego dialect. Rego is declarative, allowing policy authors to concentrate on the results that queries should yield rather than the process of running queries. In comparison to the equivalent in an imperative language, these queries are shorter and simpler.
OPA flow in terraform
OPA serves as a gate before it provisions any infrastructure, making it very simple for teams to find compliance problems as soon as possible.
The following workflow uses OPA to check the validity of the pipeline's provided Terraform (TF) code:
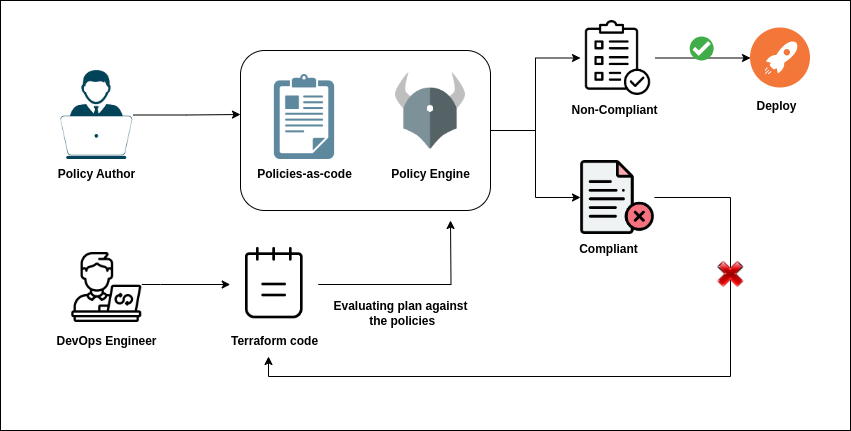
Why should we use OPA in Terraform?
Security Policy Enforcement: For instance, you can impose rules about open ports, network access restrictions, encryption options, or IAM permissions.
Compliance Validation: It verifies infrastructure settings to ensure they adhere to internal and external standards, including PCI DSS, HIPAA, GDPR, and sector-specific criteria.
Resource Tagging: It upholds resource tagging rules to guarantee that all Terraform-provisioned resources are accurately marked for accounting, tracking, and organizational needs.
Immutable Infrastructure: Aids in preventing modifications to important resources or configurations after provisioning through immutable infrastructure practices.
Approval Workflows: It makes it possible to implement approval workflows, which demand further verification or consent before enabling certain alterations to be made to critical infrastructure.
Secrets Management: Enforces policies for secrets management, safeguarding sensitive data like API keys or passwords from exposure in Terraform configurations.
Implementation
Step 1: Let’s try to create an EC2 instance with the tag Name, and it should have some value. Copy this code and create a main.tf file
provider "aws" {
region = "us-east-1" # Change to your desired AWS region
}
resource "aws_instance" "example" {
ami = "ami-0c55b159cbfafe1f0"
instance_type = "t2.micro"
tags = {
Name = "ExampleInstance" # Change the value of 'Name' tag as needed
}
}
Step 2: Create a test.rego file using the below code
package main
# Define a default rule that denies provisioning by default
default allow = false
# Allow provisioning only if 'Name' tag is specified for the EC2 instance
allow {
input.resource == "aws_instance"
input.action == "create"
contains_tag_name
}
contains_tag_name {
# This helper rule checks if the EC2 instance tags contain the 'Name' tag
tags := input.attributes.tags
contains_name := {tag | tag := tags[_]; tag.Key == "Name"}
count(contains_name) > 0
}
Step 3: Add one more file input.json using the code below. When we execute the Terraform plan, we will receive this JSON output.
We must keep that strategy. JSON to compare it to the rego policy, allowing the plan to be validated.
{
"resource": "aws_instance",
"action": "create",
"attributes": {
"tags": [
{
"Key": "Name",
"Value": "ExampleInstance"
}
]
}
}
Note: Ensure that all of your files are located in the same directory.
Step 4: Use that rego policy to evaluate the terraform code by passing this command.
opa eval --format pretty --data main.rego --input input.json "data.main.allow"
If you enter the tag "Name" in input.json, this command will return true.
Summary
In this blog post, we explored the powerful combination of Open Policy Agent (OPA) and Terraform for enhancing infrastructure provisioning and policy enforcement. OPA serves as a gatekeeper, ensuring that the Terraform code aligns with defined policies and compliance standards.
I'm excited to begin this fantastic journey with you! To remain updated, follow me.
Subscribe to my newsletter
Read articles from Jayakumar Sakthivel directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jayakumar Sakthivel
Jayakumar Sakthivel
As a DevOps Engineer, I specialize in streamlining and automating software delivery processes utilizing advanced tools like Git, Terraform, Docker, and Kubernetes. I possess extensive experience managing cloud services from major providers like Amazon, Google, and Azure. I excel at architecting secure CI/CD pipelines, integrating top-of-the-line security tools like Snyk and Checkmarx to ensure the delivery of secure and reliable software products. In addition, I have a deep understanding of monitoring tools like Prometheus, Grafana, and ELK, which enable me to optimize performance and simplify cloud migration journeys. With my broad expertise and skills, I am well-equipped to help organizations achieve their software delivery and cloud management objectives.