Day 4 of #TerraWeek - Terraform State Management
 Vedant Adhe
Vedant AdheIntroduction
In this blog post, we are going to explore the subject of managing the Terraform state. We will discuss the importance of state file methods, for storing them and take a look at remote state management options such, as Terraform Cloud AWS S3 and HashiCorp Consul.
Understanding Terraform State
Terraform state plays a pivotal role in Terraform's infrastructure management process. This state file is formatted in JSON and serves as a repository for the current state of your infrastructure. It encapsulates crucial information such as resource metadata and configuration data. When you apply modifications to your infrastructure, Terraform relies on the state file to discern which resources require creation, modification, or removal.
Managing the state effectively is essential for ensuring that your infrastructure is consistent, reliable, and secure. Proper state management allows you to:
Track changes to your infrastructure over time
Share state information with team members
Roll back changes in case of errors or issues
Prevent conflicts and inconsistencies in your infrastructure
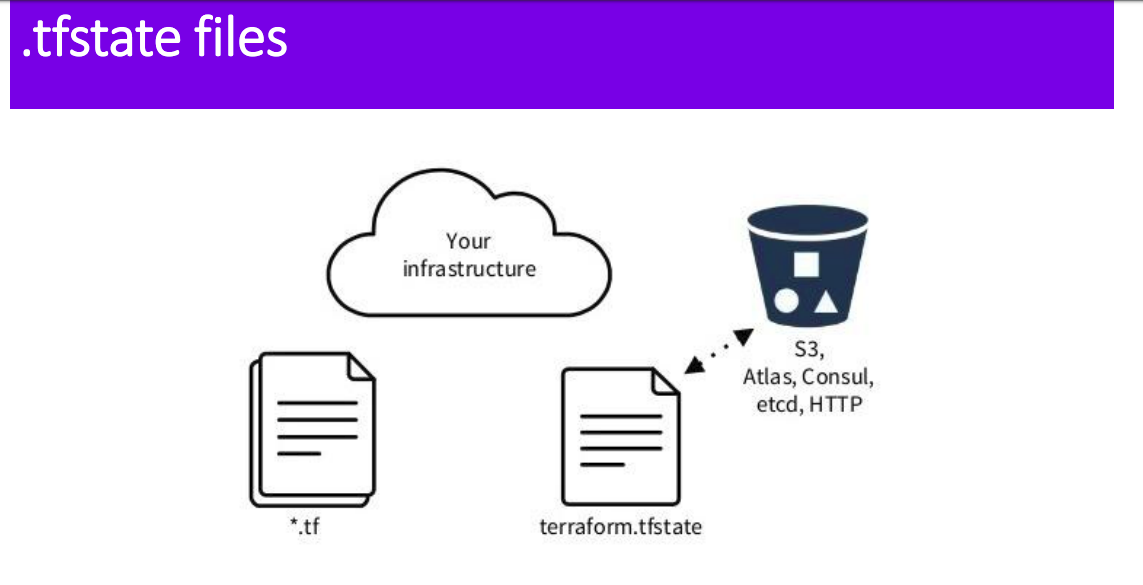
Storing State Files: Local vs. Remote
When working with Terraform, you have the option to store your state files either locally or remotely. Each approach has its advantages and considerations, and the choice depends on your specific project requirements and team collaboration needs. Let's explore the differences between these two storage options:
Local State: By default, Terraform stores the state file locally in a file named terraform.tf state. Local state storage is simple and easy to set up, making it a good option for small projects or individual developers. However, local state storage can be problematic for larger teams or projects, as it can lead to conflicts and inconsistencies when multiple team members are working on the same infrastructure.
Remote State: Remote state storage involves storing the state file on a remote backend, such as Terraform Cloud, AWS S3, or HashiCorp Consul. Remote state storage provides several benefits over local state storage, including:
Improved collaboration: Remote state storage allows multiple team members to access and update the state file simultaneously, reducing the risk of conflicts and inconsistencies.
Versioning and rollback: Many remote backends support versioning, allowing you to track changes to your state file over time and roll back to previous versions if needed.
Security: Storing your state file remotely can help protect sensitive data and ensure that only authorized users can access and modify your infrastructure.
Here's an example of a basic Terraform configuration that uses local state storage:
provider "aws" {
region = "us-east-1"
}
resource "aws_s3_bucket" "my_bucket" {
bucket = "my-s3_example-bucket"
}
Remote State Management Options
There are several remote state management options available for Terraform, including Terraform Cloud, AWS S3, and HashiCorp Consul. Let's explore each of these options in more detail:
Terraform Cloud: Terraform Cloud is a hosted service provided by HashiCorp that offers remote state storage, collaboration features, and other advanced functionality. Terraform Cloud is easy to set up and integrates seamlessly with Terraform, making it an excellent choice for teams looking for a simple and powerful remote state management solution.
- First, sign up for a Terraform Cloud account and create a new workspace. Then, add the following backend block to your Terraform configuration:
terraform {
backend "remote" {
hostname = "app.terraform.io"
organization = "your-organization-name"
workspaces {
name = "your-workspace-name"
}
}
}
provider "aws" {
region = "us-west-2"
}
resource "aws_s3_bucket" "my-bucket" {
bucket = "my-s3_example-bucket"
}
AWS S3: Amazon S3 is a popular object storage service that can be used to store Terraform state files. To use S3 as a remote backend, you'll need to configure the AWS provider in your Terraform configuration and set up an S3 bucket to store your state files. S3 provides robust security, versioning, and access control features, making it a good option for teams working with AWS infrastructure.
- Create an S3 bucket to store your state files and add the following backend block to your Terraform configuration:
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "4.66.1"
}
backend "s3" {
bucket = "your-s3-bucket-name"
key = "terraform.tfstate"
region = "us-east-1"
dynamodb_table = "demo-state_table"
}
}
provider "aws" {
region = "us-east-1"
}
resource "aws_instance" "my_instance" {
ami = "ami-007855ac798b5175e"
instance_type = "t2.micro"
tags = {
Name = "terraweek_instance"
}
}
resource "aws_s3_bucket" "my_bucket" {
bucket = "my-s3-example-bucket"
tags {
Name = "my-s3-example-bucket"
}
}
resource "aws_dynamodb_table" "my_state_table" {
name = demo_state_table_name
billing_mode = "PAY_PER_REQUEST"
hash_key = "LockID"
attribute {
name = "LockID"
type = "S"
}
tags = {
Name = demo_state_table_name
}
}
- By default, AWS S3 does not provide built-in state locking mechanisms. To implement state locking, you can leverage external locking mechanisms like using DynamoDB as a lock table and integrating it with Terraform which are shown above.
HashiCorp Consul: Consul is a distributed key-value store and service discovery tool developed by HashiCorp. Consul can be used as a remote backend for Terraform state storage, providing a highly available and scalable solution for managing state files. Consul is well-suited for large-scale, multi-region infrastructure deployments and can be used in conjunction with other HashiCorp tools like Vault for enhanced security and access control.
- Set up a Consul cluster and add the following backend block to your Terraform configuration:
terraform {
backend "consul" {
address = "your-consul-server-address"
path = "your/consul/path"
}
}
provider "aws" {
region = "us-east-1"
}
resource "aws_s3_bucket" "my_bucket" {
bucket = "my-s3_example-bucket"
}
Conclusion
Terraform state management is a critical aspect of managing your infrastructure with Terraform. Understanding the importance of state, the differences between local and remote state storage, and the various remote state management options available, can help you choose the best solution according to your needs. By implementing effective state management practices, you can ensure that your infrastructure is consistent, reliable, and secure and it allows you to focus on building and deploying your applications with confidence.
LinkedIn (https://www.linkedin.com/in/vedant-adhe-4683b0192/)
GitHub (https://github.com/VedantAdhe)
Subscribe to my newsletter
Read articles from Vedant Adhe directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
