Automate F5 BIG-IP On-Prem using Terraform Cloud with GitHub
 Sebastian Maniak
Sebastian Maniak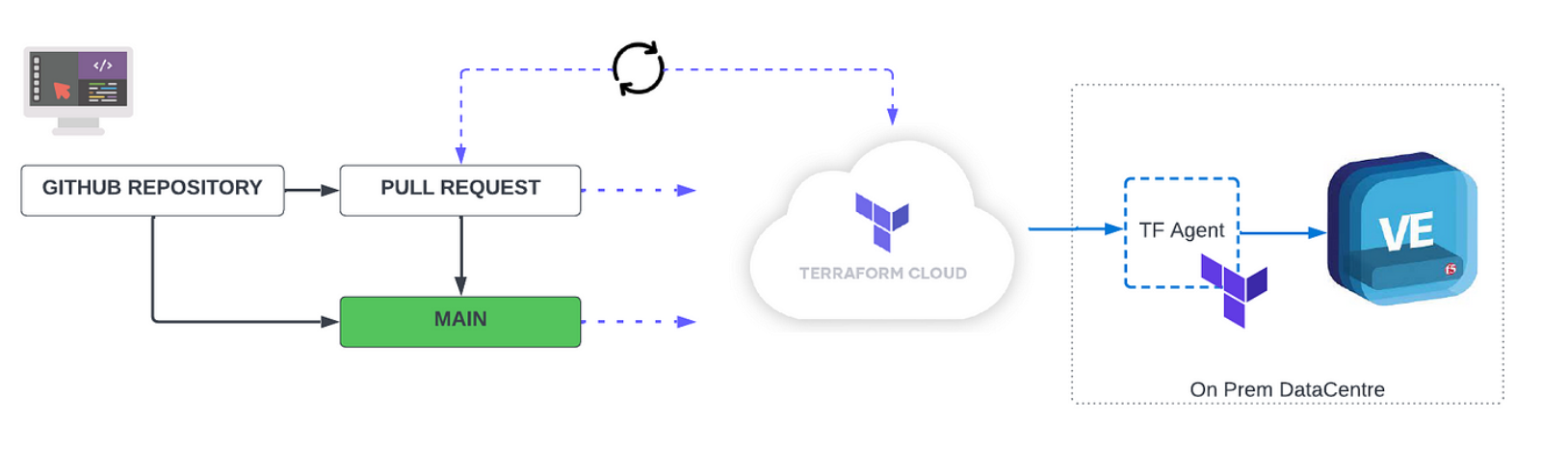
The following guide will assist your organization in effectively automating and managing F5 BIG-IP, whether on-premises or in the cloud.
Prerequisites
The first step is to ensure that you have the appropriate setup in place to fully utilize Terraform Cloud and GitHub Actions.
For this tutorial, you will need:
A Terraform Cloud account (Business Account)
F5 Deployed (either in the cloud or on-prem) — for this guide I am just using an F5 on-prem
Using the F5 Automation Toolchain
F5 Automation Toolchain
There are many automation tools that can be used to deploy an F5 on-prem and in the cloud. The F5 Automation Toolchain is a set of automation tools that make it faster and easier to deploy and configure F5 application services via a simple yet powerful declarative interface. It includes
F5 Declarative Onboarding for layer 1–3 device provisioning
F5 Application Services 3 Extension for layer 4–7 configuration
Telemetry Streaming for aggregating, normalizing, and forwarding app statistics and events to 3rd-party analytics.
The toolchain enables developers to programmatically extend F5 application services — and integrate with CI/CD toolchains, orchestration systems, and 3rd-party ecosystems.
Start Bootstrap F5 Automation Toolchain
First thing I need to do is to bootstrap the F5, here is the github repo I have to help you boot strap your F5 BIGIP.
GitHub - maniak-academy/f5-bootstrap: Simple bootstap guide to install RPM packages on F5
The following code provides you an example on how to Bootstrap your f5 using terraform. There are many automation tools…
If you take a look at my code below, you will need to edit the password/bigip management to meet your F5 requirements.
terraform {
required_providers {
bigip = {
source = "F5Networks/bigip"
version = "1.13.1"
}
}
}provider "bigip" {
address = var.bigipmgmt
username = var.bigipmgmtuser
password = var.bigippass
}// Using provisioner to download and install do rpm on bigip, pass arguments as BIG-IP IP address, credentials
// Use this provisioner for first time to download and install do rpm on bigipresource "null_resource" "install_do" {
provisioner "local-exec" {
command = "./install-do-rpm.sh 192.168.86.46 admin:W3lcome098!"
}
}resource "time_sleep" "wait_30_seconds" {
depends_on = [null_resource.install_do]
create_duration = "15s"
}resource "null_resource" "install_as3" {
provisioner "local-exec" {
command = "./install-as3-rpm.sh 192.168.86.46 admin:W3lcome098!"
}
}
Setup Terraform Cloud
What is Terraform Cloud
Terraform Cloud is HashiCorp’s managed service offering*. It eliminates the need for unnecessary tooling and documentation for practitioners, teams, and organizations to use Terraform in production. Provision infrastructure in a remote environment that is optimized for the Terraform workflow.*
The Setup Terraform Cloud repo
You can take a look at my github repo that outlines how I build my repo and F5 DO. https://github.com/maniak-academy/f5-tf-bigip-nonprod
First, create a new Terraform Cloud workspace named f5-tf-bigip-nonprod
Go to the Create a new Workspace page and select “API-driven workflow”. Name your workspace f5-tf-bigip-nonprod and click "Create workspace".
Next, add the following as Environment Variables for your f5-tf-bigip-nonprod workspace with their respective values from the access credentials file you downloaded from AWS earlier.
bigipmgmt
bigipmgmtuser
bigippass
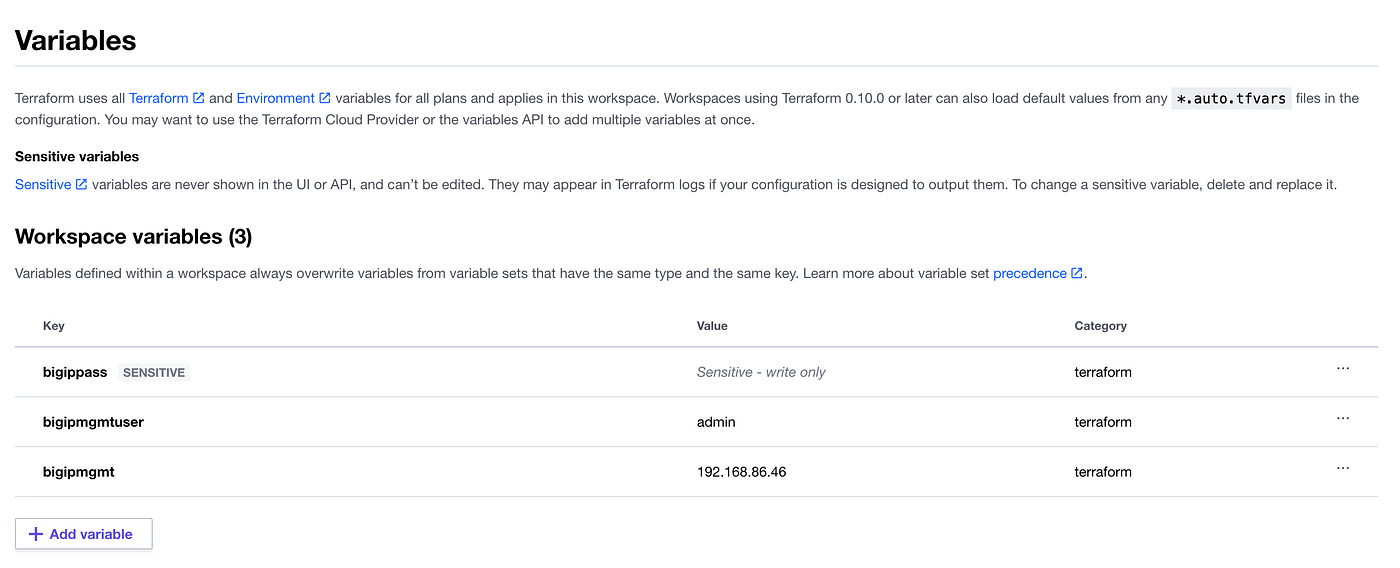
Mark bigippass value as sensitive. Terraform Cloud will use these credentials to authenticate to F5 BIGIP.
Finally, go to the Tokens page in your Terraform Cloud User Settings. Click on “Create an API token” and generate an API token named GitHub Actions.
Save this token in a safe place. You will add it to GitHub later as a secret, so the Actions workflow can authenticate to Terraform Cloud.
Set up a GitHub repository
You can fork my repo here https://github.com/maniak-academy/f5-tf-bigip-nonprod or you can create your own.
In your repo repository, navigate to “Settings” > “Secrets” > “Actions”. Create a new secret named TF_API_TOKEN, setting the Terraform Cloud API token you created in the previous step as the value.
Next in your repo you will need to setup GitHub Actions, navigate to the “Actions” tab and enable this pre-configured workflow by clicking “I understand my workflows, go ahead and enable them.”
Here is a copy of my GitHub Actions file https://github.com/maniak-academy/f5-tf-bigip-nonprod/blob/main/.github/workflows/terraform.yml
Setup Terraform Agent On-Prem
Since I am managing my F5 BIGIP on-prem I deployed a Terraform Agent in my datacenter to securely communicate with my F5 BIGIP and Terraform Cloud.
What is a Terraform Agent:
Terraform Cloud Agents allow Terraform Cloud to communicate with isolated, private, or on-premises infrastructure. By deploying lightweight agents within a specific network segment, you can establish a simple connection between your environment and Terraform Cloud which allows for provisioning operations and management. This is useful for on-premises infrastructure types such as vSphere, Nutanix, OpenStack, enterprise networking providers, and anything you might have in a protected enclave.
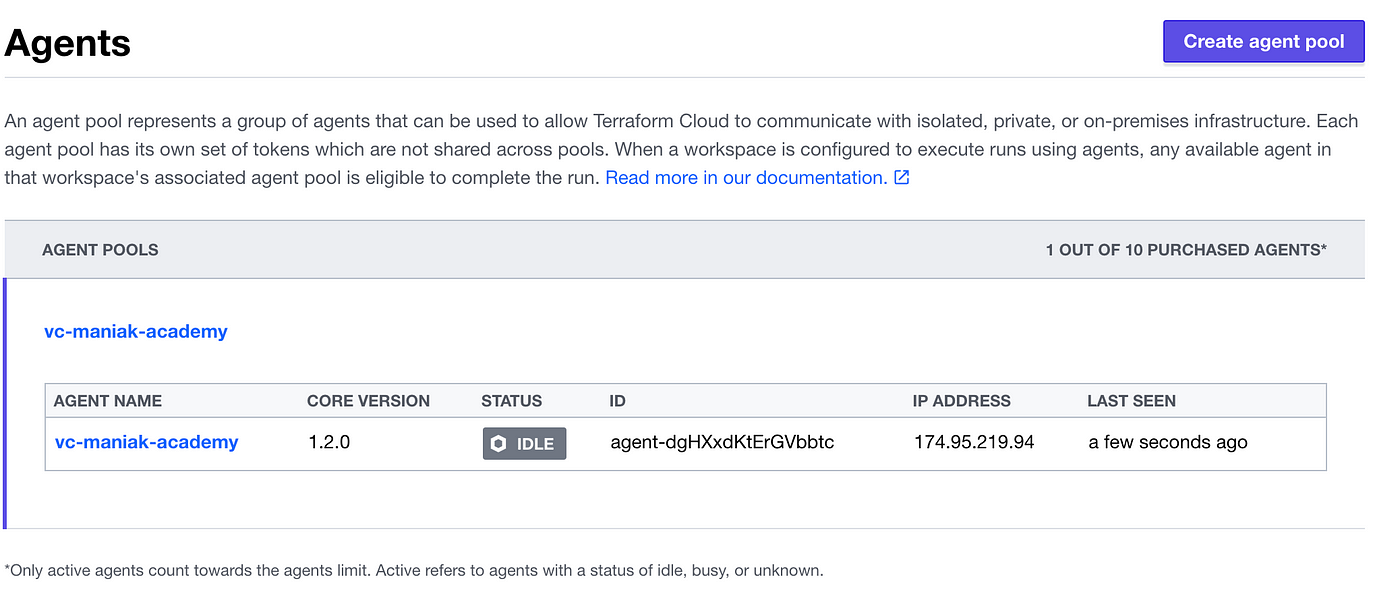
Here is a screenshot of my agent. You can follow this guide to setup your agent inside your data center https://www.terraform.io/cloud-docs/agents
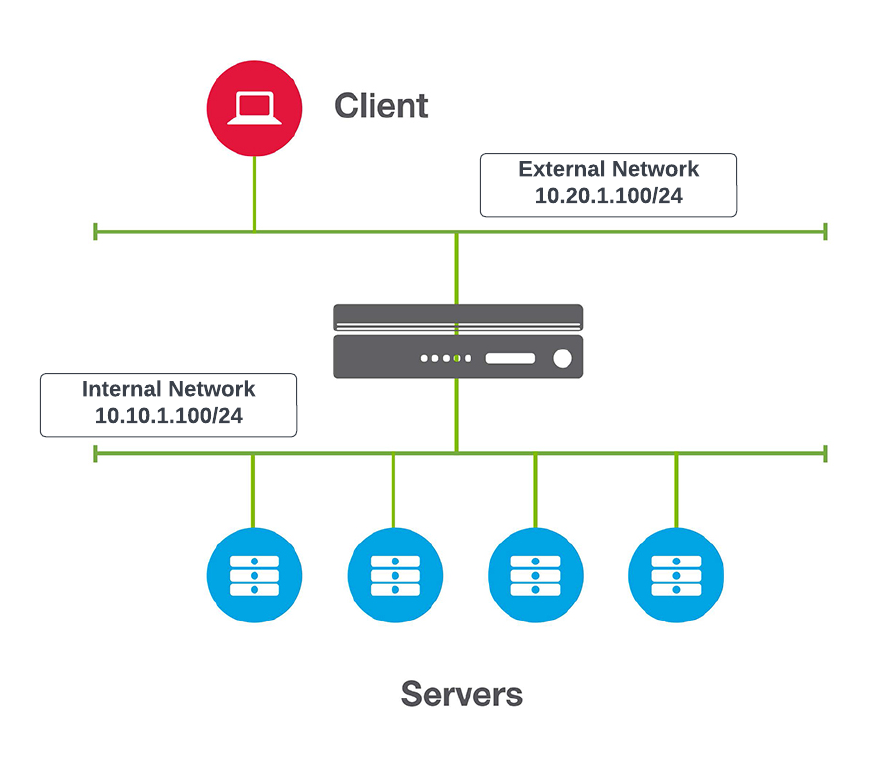
F5 Configuration
As I mentioned above we are going to be using F5 Declarative Onboarding for layer 1–3 device provisioning. We will be editing the bigip.tpl file and we can are going to be passing variables using the terraform data source template_file.
Using Infrastructure as Code allows us to build a base configuration across our organization to ensure consistency, security and best practices.
data "template_file" "init" {
template = file("bigip.tpl")
vars = {
HOSTNAME = "bigip-nonprod.maniak.academy"
DNS_ADDRESS = "1.1.1.1"
NTP_ADDRESS = "8.8.8.8"
GUEST_PASSWORD = "W3lcome098!"
EXTERNAL_ADDRESS = "10.100.2.100/24"
EXTERNAL_VLAN_ID = "1"
INTERNAL_ADDRESS = "10.100.1.100/24"
INTERNAL_VLAN_ID = "2"
DEFAULT_ROUTE = "10.100.1.1"
}
}
When we commit the changes we will deploy an F5 BIG-IP that is ready to be used and consumed to load balance and secure applications.
Next step is to create a new branch and commit and push the changes to the main branch.
Create pull request
Next step is to create a new branch.
git checkout -b 'update-tfc-backend'
Edit the main.tf to include you Terraform Cloud organization and workspace you created earlier.
terraform {
cloud {
organization = "sebbycorp"workspaces {
name = "f5-tf-bigip-nonprod"
}
}
required_providers {
bigip = {
source = "F5Networks/bigip"
version = "1.13.1"
}
}
}
Prepare to add your changes to your forked repository.
git add main.tf
Commit these changes with a message.
git commit -m ‘Point backend to correct TFC org and workspace’
Push these changes.
git push
Next, generate a pull request from the update-tfc-backend branch.
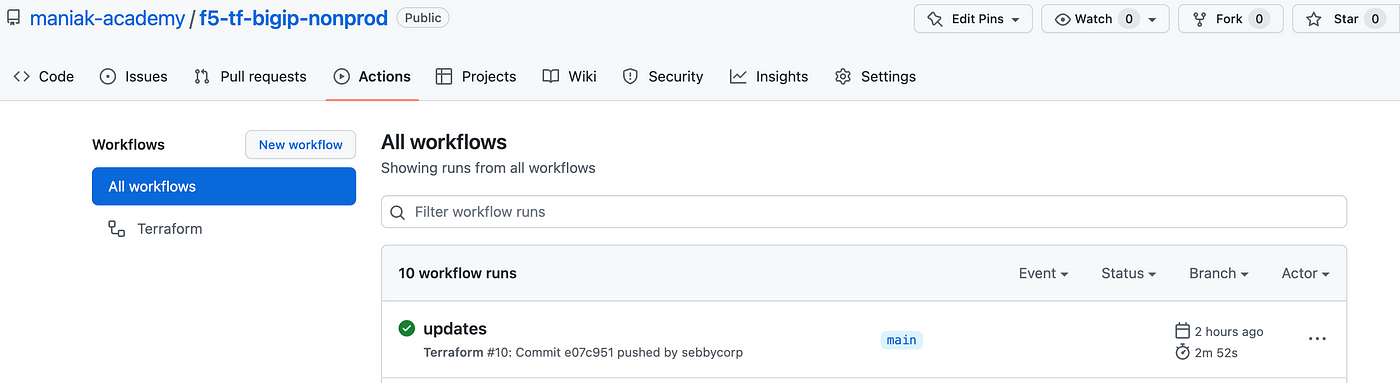
GitHub Actions Trigger
Navigate to your pull request. Your PR will trigger the Terraform Actions workflow. When the workflow completes, it will add a comment with the outcome of each step and a speculative plan.
Verify the Deployment
In GitHub, go to “Actions”, then select the pull request you just merged.
Then, click on the “Terraform” workflow. Notice how the “Terraform Plan”, “Update Pull Request” and “Terraform Plan Status” steps have been skipped.
Expand the “Terraform Apply” step. Terraform will go and build your F5 BIGIPs.
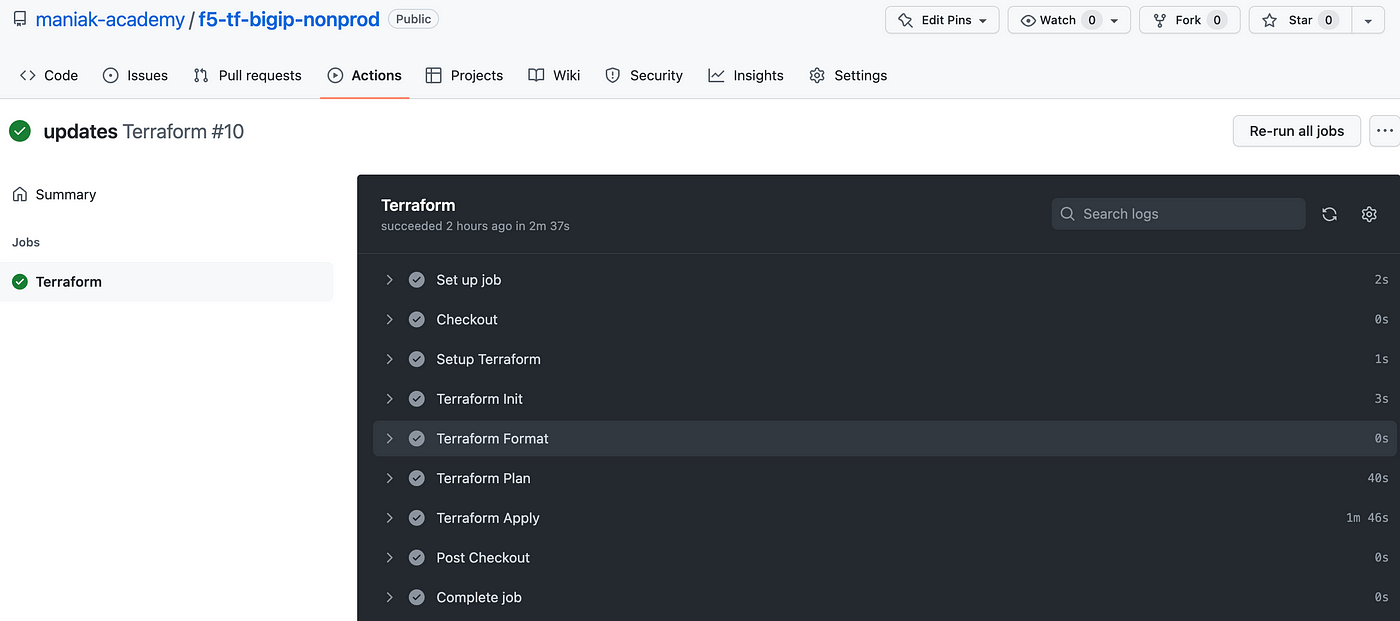
You have successfully set up a complete GitHub Actions workflow to deploy a private on-prem F5 BIGIP within a Terraform Cloud workspace.
Conclusion
The beauty of this solution is the entire build of your F5 is Code. Using the power of Terraform Cloud and the F5 Automation Toolchain allows your organization to delivery and deploy F5s at a quicker rate.
Values of Software Defined Infrastructure:
Software workflows for infrastructure changes to match product:
Versioning
Issue management
Change-logs
Audibility
Benefits of IaC and Software
Testing that building and running the infrastructure works as planned:
Repeatable
Stable
Secure
Visible
Thanks. If you have any question feel free to reach out.
Subscribe to my newsletter
Read articles from Sebastian Maniak directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Sebastian Maniak
Sebastian Maniak
I build, secure and automate infrastructure. | Follow me for daily updates and code examples.