Managing PAN-OS Panorama with Terraform and Github Actions
 Sebastian Maniak
Sebastian Maniak
As businesses continue to expand their digital footprint, it has become increasingly important to ensure that their network infrastructure is secure and well-managed. One tool that many businesses use to manage their network infrastructure is PAN-OS Panorama, a network security management platform that provides centralized control over multiple firewalls.
In this blog post, we will walk through how to manage PAN-OS Panorama using Terraform and GitHub Actions. Terraform is an open-source infrastructure as code (IaC) tool that enables you to define and provision infrastructure using a simple, declarative language. GitHub Actions is a powerful continuous integration and deployment (CI/CD) tool that makes it easy to automate workflows.
Getting Started
To get started, you’ll need to have a few things set up:
A Github account
A Github repository for your PAN-OS Panorama configuration files
A Terraform Cloud account
An active PAN-OS Panorama environment
Once you have all of these set up, you can start writing your Terraform configuration files.
Writing Terraform Configuration Files
Terraform configuration files are written in Hashicorp Configuration Language (HCL). Here’s an example of what a basic configuration file for PAN-OS Panorama might look like:
provider "panos" {
ip_address = "your.panorama.ip.address"
username = "your.panorama.username"
password = "your.panorama.password"
}
resource "panos_device_group" "example_group" {
name = "example-group"
}
resource "panos_security_rule" "example_rule" {
name = "example-rule"
device_group = "${panos_device_group.example_group.name}"
source_zone = "example-source-zone"
destination_zone = "example-destination-zone"
application = "example-application"
action = "allow"
}
In this example, we’re using the “panos” provider to connect to our PAN-OS Panorama instance. We’re then creating a device group and a security rule using the “panos_device_group” and “panos_security_rule” resources, respectively.
Committing to Github and Setting up Github Actions
Once you have your Terraform configuration files written, you can commit them to your Github repository. From there, you can set up a Github Action to automate the deployment of your infrastructure.
Here’s an example of what your Github Action might look like:
name: Terraform Plan
on:
push:
branches:
- main
jobs:
terraform:
runs-on: ubuntu-latest
steps:
- name: Checkout code
uses: actions/checkout@v2
- name: Terraform Init
uses: hashicorp/setup-terraform@v1
with:
cli_config_credentials_token: ${{ secrets.TF_API_TOKEN }}
- name: Terraform Plan
uses: hashicorp/terraform-github-actions@master
with:
args: |
plan -var-file=variables.tfvars
This Github Action will run every time you push changes to the “main” branch of your repository. It will first check out your code, then initialize Terraform and run a plan. You’ll need to set up a Github secret for your Terraform Cloud API token to use in the cli_config_credentials_token field.
Scenario
In this scenario, we are using Github Actions to manage our PAN-OS Panorama infrastructure using Terraform. Whenever changes are made to the Terraform code in the main branch of the Github repository, Github Actions will automatically run a plan to determine what changes need to be made to the infrastructure. If the plan is successful, Github Actions will then apply the changes to the infrastructure.
Here’s how the process works:
A developer makes changes to the Terraform code in the main branch of the Github repository.
Github detects the changes and triggers a workflow in Github Actions.
Github Actions checks out the code from the main branch and initializes Terraform.
Github Actions runs a Terraform plan to determine what changes need to be made to the infrastructure.
If the plan is successful, Github Actions applies the changes to the infrastructure.
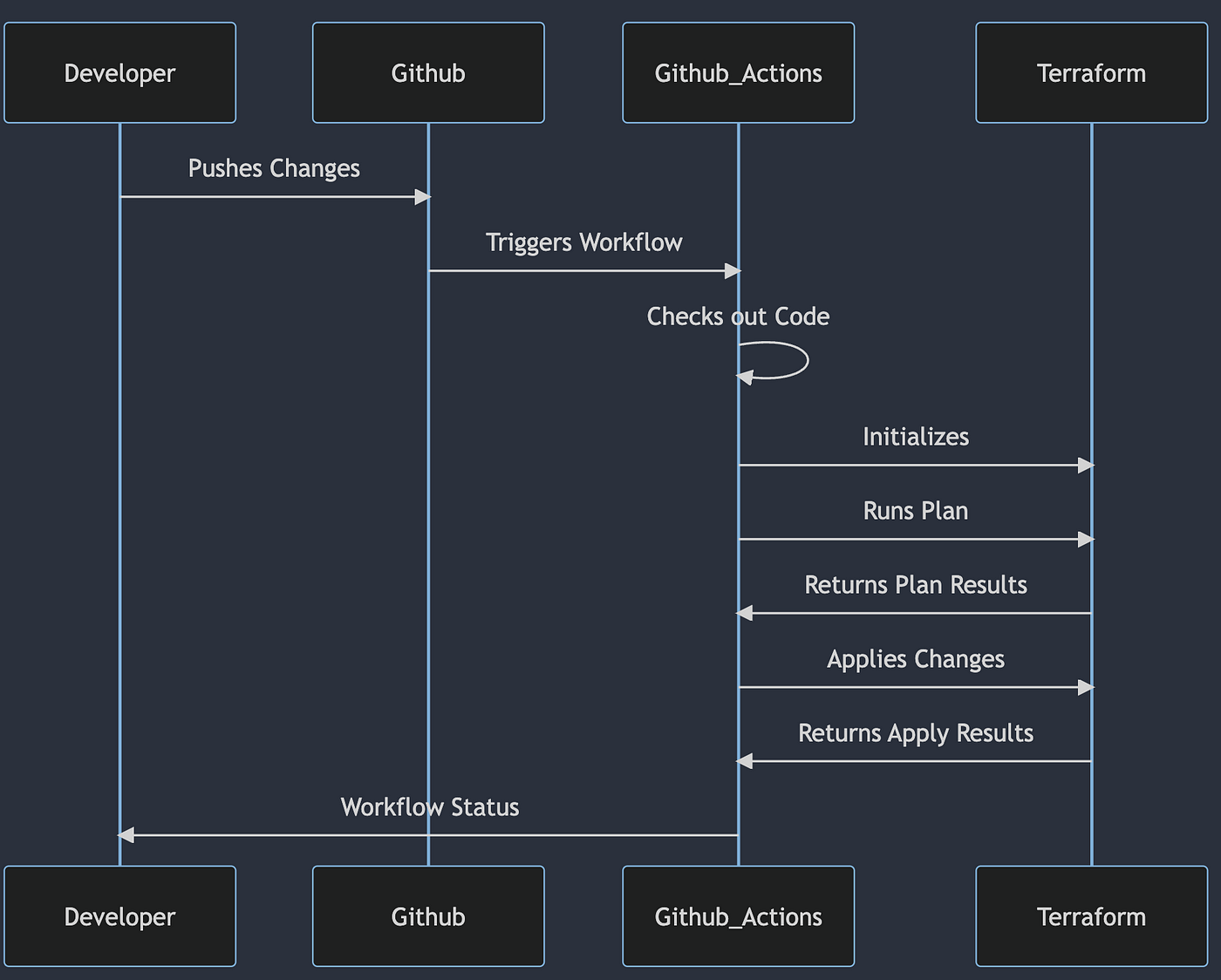
In this sequence diagram, the Developer pushes changes to the main branch of the Github repository, which triggers a workflow in Github Actions. Github Actions then checks out the code, initializes Terraform, and runs a plan to determine what changes need to be made to the infrastructure. If the plan is successful, Github Actions applies the changes to the infrastructure using Terraform. Finally, Github Actions sends a status update to the Developer indicating whether the workflow was successful or not.
Subscribe to my newsletter
Read articles from Sebastian Maniak directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Sebastian Maniak
Sebastian Maniak
I build, secure and automate infrastructure. | Follow me for daily updates and code examples.