What happens when you type https://www.google.com in your browser and press Enter?
 Rodgers Mogaka
Rodgers Mogaka
"Have you ever wondered what happens behind the scenes when you type 'https://www.google.com' into your browser and press Enter?" It's a trip full of interesting digital subtleties, similar to the inner workings of a well-oiled machine. In this post, we'll walk through each stage of the process, revealing the alchemy that transforms a simple keystroke into the Google homepage.
- DNS request
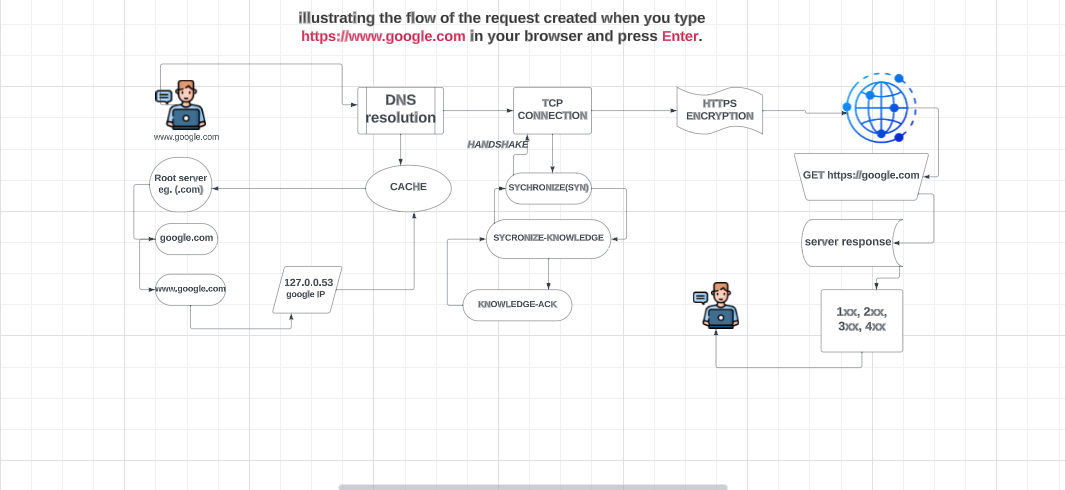
When you type "https://www.google.com" into your browser's address bar and press Enter, the DNS (Domain Name System) resolution procedure begins. DNS functions as the internet's phone book, converting user-friendly domain names like "www.google.com" into IP addresses, which are the real numerical numbers used by computers on the internet.
Let's break down what happens during the DNS request step by step:
Local DNS Cache Check: Before attempting to access a website, your computer checks its local DNS cache to determine whether it has a record of the IP address connected to "www.google.com." It saves time by avoiding the need to ask external DNS servers if the address is available locally.
Recursive DNS Server: Your computer contacts a recursive DNS server if the address is not in the local cache or has expired. Usually, your Internet service provider (ISP) offers this server or you have it set up in your network settings. It is in charge of domain name resolution.
If the recursive DNS server does not know the IP address, it requests one of the root DNS servers. These root servers store information about top-level domains such as ".com," ".org," and so on. The root server answers by directing the request to the authoritative DNS server for the ".com" domain.
TLD DNS Server: The recursive DNS server now queries the top-level domain (TLD) DNS server responsible for ".com." This server has information about the authoritative DNS server for "google.com".
Last but not least, the authoritative DNS server for "google.com" is queried. This server is home to the IP address associated with "www.google.com."
Answer to Your Computer: The IP address of "www.google.com" is returned to your computer over the same chain.
Local Cache Update: The IP address of "www.google.com" is added to your computer's local DNS cache, allowing subsequent queries to the same domain to be resolved more rapidly.
- TCP/IP
Now let's delve into the TCP/IP (Transmission Control Protocol/Internet Protocol). Once the DNS resolution procedure (described before) finds the IP address associated with "https://www.google.com," your browser is equipped with this critical information. The next step is to establish a TCP/IP connection or a handshake to Google's web servers:
Request to Establish Connection: Your browser sends a TCP/IP request to the IP address of Google's servers on port 443. Port 443 is the default port for HTTPS, the secure version of HTTP (Hypertext Transfer Protocol.
Three-Way Handshake: To ensure reliable and orderly communication, a three-way handshake occurs between your browser and the web server:
(i). SYN (Synchronize) Packet: Your browser sends a SYN packet to the server, indicating its intent to establish a connection.
(ii). SYN-ACK (Synchronize-Acknowledge) Packet: The web server responds with a SYN-ACK packet, acknowledging the request and indicating its readiness to establish a connection.
(iii). ACK (Acknowledgment) Packet: Finally, your browser sends an ACK packet to confirm the connection establishment.
Encrypted Data Exchange: Now, any data transmitted between your browser and Google's server, including the HTML, images, and other resources needed to display the Google homepage, is encrypted using the SSL/TLS (Secure Sockets Layer/Transport Layer Security) protocol. This encryption ensures the confidentiality and integrity of the data exchanged.
Encrypted Data Exchange: Any data exchanged between your browser and Google's server is now encrypted using the SSL/TLS (Secure Sockets Layer/Transport Layer Security) protocol, including HTML, pictures, and other resources required to show the Google homepage. This encryption protects the data exchange's secrecy and integrity.
HTTP Request: With the secure connection established, your browser sends an HTTP GET request to the server for the Google homepage.
Server Response: Google's server processes your request, generates the HTML content of the homepage, and sends it back to your browser over the established TCP/IP connection.
Rendering the Page: After receiving the HTML, your browser begins rendering the Google homepage, requesting additional resources such as CSS files and graphics as needed over the same secure TCP/IP connection.
- Firewall
As your browser establishes a connection to Google's servers via the TCP/IP protocol, a crucial element in this process is the firewall. Firewalls act as digital gatekeepers, safeguarding your computer and network from unauthorized access and potential threats. Here's how they fit into the equation:
Traffic Monitoring and Packet Inspection. Firewalls are the vigilant guardians of your network's security. They continuously monitor the flow of incoming and outgoing network traffic, overseeing every data exchange with external servers, including the likes of Google. One of their core functions involves packet inspection, where they scrutinize the tiny units of data, or packets, that constitute your online activities. By analyzing these packets, firewalls can make critical determinations about their safety or potential harm, a pivotal role in safeguarding your digital world.
Rule-Based Filtering and Stateful Inspection. Firewalls operate based on a set of predefined rules, a bit like a traffic cop at a busy intersection. These rules dictate which packets are permitted to pass through and which should be firmly blocked. These rules can be configured with precise criteria, such as source IP addresses, destination ports, or specific types of traffic, such as HTTP or HTTPS. In addition to rule-based filtering, advanced firewalls employ stateful inspection, which enables them to monitor the state of active connections. This means they can distinguish between legitimate responses to your browser's requests and unsolicited incoming traffic, adding an extra layer of security.
Blocking Suspicious Activity and Application Layer Filtering. One of the most critical functions of firewalls is the ability to block suspicious activity. When a packet is flagged as potentially harmful or doesn't align with the firewall's predefined rules, it is promptly blocked from entering your network or reaching your computer. This protective measure serves as a formidable barrier, preventing threats like malware and hackers from gaining unwarranted access. Furthermore, modern firewalls can perform deep packet inspection at the application layer. This means they can delve into the content of data packets, allowing them to identify and block malicious content or specific web requests, adding a sophisticated layer of defense.
Logging, Alerts, and Custom Configuration Firewalls maintain detailed logs of network activity, serving as invaluable tools for administrators to track and investigate unusual or potentially harmful traffic. Additionally, they can generate real-time alerts when suspicious events occur, enabling swift responses to emerging threats. Importantly, firewall settings are highly customizable to tailor the security measures to the specific needs of your network. This customization includes the ability to allow or block access to particular websites, services, or applications, giving you granular control over your network's security.
- HTTPS/SSL
As you initiate a connection to "https://www.google.com" using your browser, you're engaging in a secure communication method known as HTTPS (Hypertext Transfer Protocol Secure), and at the heart of this security is the SSL/TLS (Secure Sockets Layer/Transport Layer Security) protocol. Here's how they play pivotal roles in ensuring the safety of your data:
In the realm of web security, HTTPS and SSL/TLS encryption play vital roles. When you visit a website like "https://www.google.com," your browser initiates a secure connection. This process involves encrypting the data exchanged between your browser and the server, rendering it unreadable to potential eavesdroppers. Additionally, an SSL/TLS handshake establishes trust between your browser and the server, using digital certificates to verify their identities, ensuring you connect to an authentic website, not a fraudulent one.
HTTPS/SSL safeguards data integrity by employing cryptographic hash functions to create checksums for each data packet. This ensures that data remains unaltered during transit. It also relies on trusted Certificate Authorities (CAs) to issue digital certificates, vouching for a website's authenticity. Browsers, in turn, trust these CAs and display security indicators like padlocks or "Secure" labels in the address bar when a secure connection is established.
- Load-balancer
Behind the scenes of your web request to "https://www.google.com," a critical component at play is the load balancer. This technology acts as a traffic cop, ensuring that the incoming requests from users like you are distributed efficiently across multiple servers. Here's how it contributes to a seamless web experience:
Their primary goal is to prevent any single server from becoming overwhelmed by distributing incoming web traffic efficiently. This strategy ensures optimal performance by maintaining a balanced load across the servers.
One significant benefit of load balancers is their contribution to improved scalability. They facilitate horizontal scalability, allowing websites to handle a substantial number of simultaneous users. When demand surges, new servers can be seamlessly added to the pool, ensuring that the service remains responsive during peak periods.
Load balancers go beyond traffic distribution; they also actively monitor the health and performance of each server in the pool. This continuous health monitoring allows them to automatically reroute traffic away from servers experiencing issues, preventing disruptions in service and ensuring high availability.
Web server
A web server is the key component responsible for handling your request. When you initiate this action, your browser sends an HTTP or HTTPS request to Google's web server. The web server at "www.google.com" processes your request and delivers the Google homepage, search results, or other content back to your browser. It plays a critical role in hosting, processing, and serving web content to users, ensuring that you receive the web page you requested in response to your action.
Application server
An application server is a specialized software framework or hardware device responsible for managing and executing dynamic web applications. Unlike a web server that primarily serves static web content, an application server handles the dynamic aspects of websites and web applications. It performs tasks such as processing user input, interacting with databases, and generating dynamic web pages in response to user requests.
An application server is responsible for managing any dynamic elements on the Google homepage, such as search queries, personalized content, and user interactions. It works in tandem with the webserver to ensure that the web application functions smoothly, providing users with a dynamic and interactive experience.
Database
A database is a structured and organized collection of data, typically stored electronically on a computer system. Databases are designed to efficiently store, retrieve, and manage data, making them a foundational component of many applications and systems. They provide a structured way to store and organize vast amounts of information, enabling users and applications to access and manipulate data as needed.
Google, for instance, uses databases to store and retrieve search results, user preferences, and other relevant data. When you perform a search on Google, the search engine queries its databases to find and display relevant web pages and information.
Databases come in various types, including relational databases like MySQL and PostgreSQL, NoSQL databases like MongoDB and Cassandra, and specialized databases for different purposes. They are a fundamental part of modern technology, supporting a wide range of applications, from websites and e-commerce platforms to business management systems and much more.
HAPPY CODING!
Subscribe to my newsletter
Read articles from Rodgers Mogaka directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Rodgers Mogaka
Rodgers Mogaka
A Software Developer. Equally proficient in technical writing, distilling complex concepts into clear, user-friendly documentation. Passionate about continuous learning and staying ahead of emerging trends. A collaborative team player dedicated to delivering exceptional solutions.