"SSH and SCP: Secure Remote Access and File Transfer "
 Subash Neupane
Subash Neupane
SSH and SCP are essential tools for secure remote access and file transfer in IT and system administration. By understanding their fundamentals, adhering to best practices, and staying vigilant about security, you can harness the power of these tools while keeping your systems and data safe from unauthorized access and threats.
Let's learn about SSH and SCP practically by creating the remote system and performing all the commands to make it really practical with the learning.
SSH
SSH is a cryptographic network protocol that establishes secure connections between two computers over an insecure network. It provides a safe way to log into remote servers and execute commands, manage network devices, and securely transfer data. SSH is known as " Secure Shell".
Why do we need SSH?
Secure Shell (SSH) is a crucial technology in the world of information technology for several essential reasons:
Secure Remote Access
Authentication
Data Security
Tunneling and Port Forwarding
Remote Management
Cross Platform Compatibility
Scripting and Automation
Let's try to use SSH practically
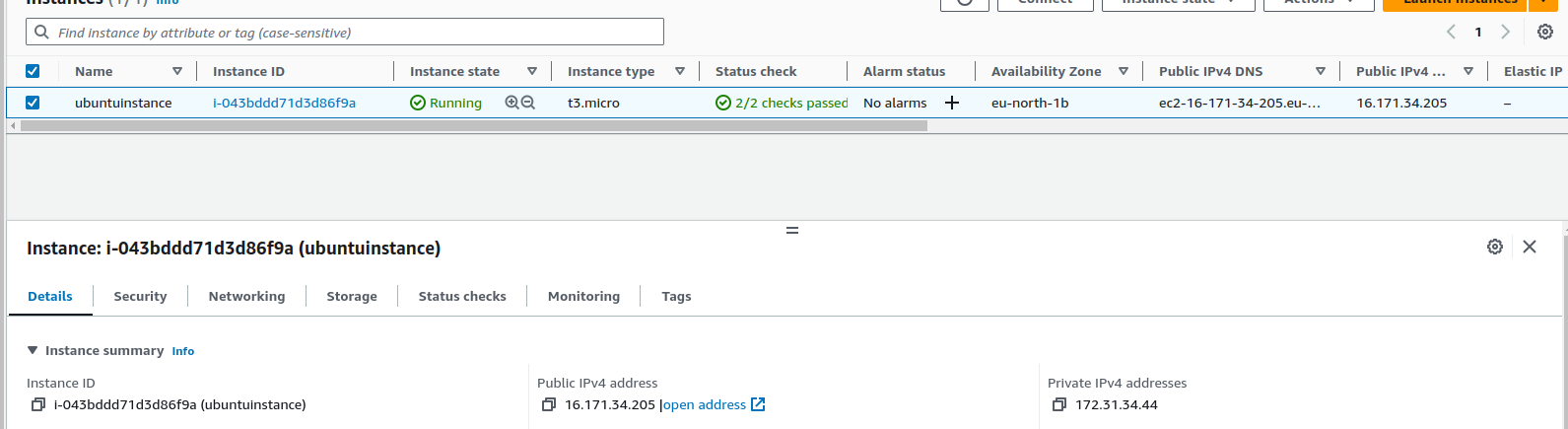
I have created an instance in the AWS cloud for the demo purpose. Using the ssh command we will connect to this remote instance from the terminal in our system.
Basic Syntax for SSH connection:
ssh -i private_key_path username@host

Here we can see that using SSH command we are connected to the remote ec2 instance which is in the cloud. It can also be verified by seeing the command prompt which changed from subash@subash07: (local) to ubuntu@ip-172-31-34-44 (remote)
SCP
SCP, or Secure Copy, is a command-line utility for securely copying files and directories between hosts over an SSH connection. It uses the same authentication and security as SSH to ensure the confidentiality and integrity of the transferred data.
Key characteristics:
Secure: SCP encrypts the data while it is being transferred, making it hard to intercept and tamper with.
Recursive Copy: SCP has the ability to recursively copy directories and their contents.
Preservation of Attributes: SCP keeps track of file attributes like timestamps and permissions.
Basic SCP Syntax
scp [options] private_key_path source_File destination_user@hostname:file_path
example:
scp -i ~/Downloads/test-vm.pem abc.txt ubuntu@16.171.34.205:~
# "~" represent the home directory path in the remote machine
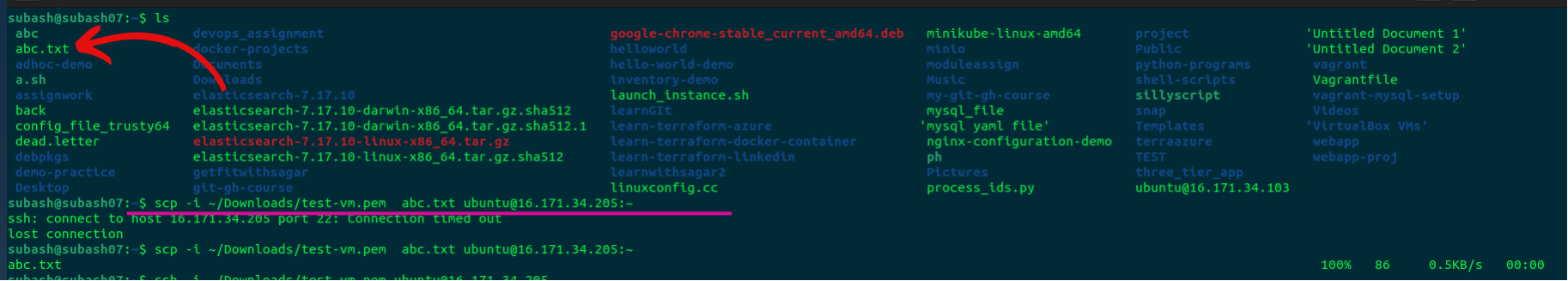
Here we copied a file named abc.txt which is in our local machine, using the scp command we copied the local file to the remote machine.
We once again log into the remote machine (ec2 instance) to check whether it is copied or not.

We can see our text file "abc.txt" in the ec2 instance which is successfully copied using SCP.
Happy Learning!!
Subscribe to my newsletter
Read articles from Subash Neupane directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Subash Neupane
Subash Neupane
Computer Science graduate