Operating System
 Narottam Choudhary
Narottam Choudhary
An operating system is the software that manages computer hardware and software resources and provides common services for computer programs. It is the most important type of system software in a computer system.
Examples of operating systems are Windows, Linux, and Mac OS.
Operating system in the easiest way:
An operating system is the software that tells your computer how to work. It manages all of the different parts of your computer and makes sure they all work together.
Without an operating system, your computer would be just a bunch of useless parts.
Why Use an Operating System?
The operating system helps in improving the computer software as well as hardware. Without OS, it became very difficult for any application to be user-friendly. Operating System provides a user with an interface that makes any application attractive and user-friendly. The operating System comes with a large number of device drivers that makes OS services reachable to the hardware environment. Each and every application present in the system requires the Operating System. The operating system works as a communication channel between system hardware and system software. The operating system helps interact an application with the hardware part without knowing about the actual hardware configuration. It is one of the most important parts of the system and hence it is present in every device, whether large or small device.
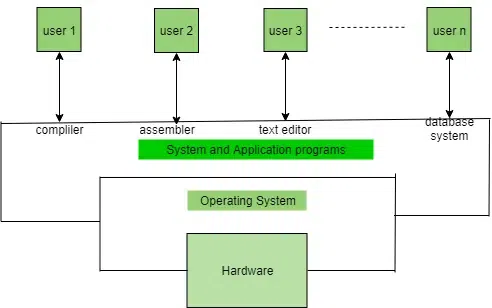
Functions of the Operating System
Resource Management: The operating system manages and allocates memory, CPU time, and other hardware resources among the various programs and processes running on the computer.
Process Management: The operating system is responsible for starting, stopping, and managing processes and programs. It also controls the scheduling of processes and allocates resources to them.
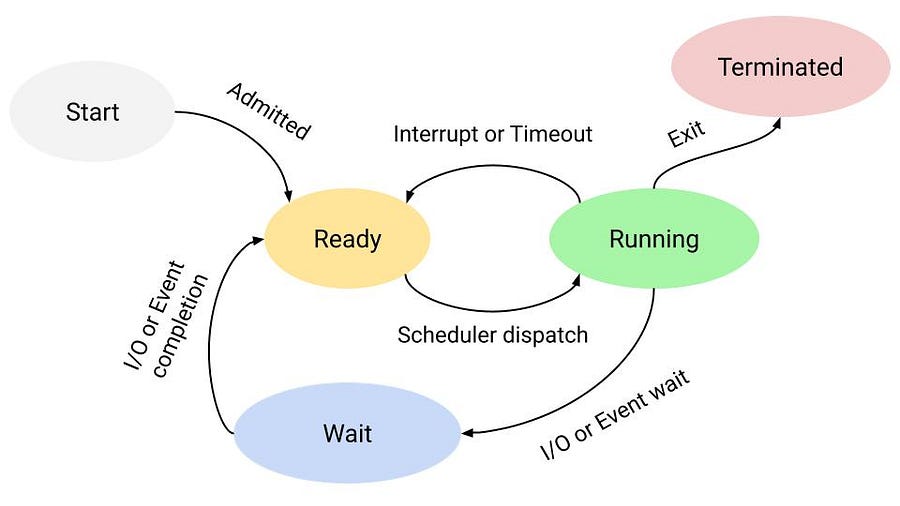
Memory Management: The operating system manages the computer’s primary memory(RAM, Cache) and provides mechanisms for optimizing memory usage.

Security: The operating system provides a secure environment for the user, applications, and data by implementing security policies and mechanisms such as access controls and encryption.
Job Accounting: It keeps track of time and resources used by various jobs or users.
File Management: The operating system is responsible for organizing and managing the file system, including the creation, deletion, and manipulation of files and directories.

Device Management: The operating system manages input/output devices such as printers, keyboards, mice, and displays. It provides the necessary drivers and interfaces to enable communication between the devices and the computer.
Networking: The operating system provides networking capabilities such as establishing and managing network connections, handling network protocols, and sharing resources such as printers and files over a network.
User Interface: The operating system provides a user interface that enables users to interact with the computer system. This can be a Graphical User Interface (GUI), a Command-Line Interface (CLI), or a combination of both.

Backup and Recovery: The operating system provides mechanisms for backing up data and recovering it in case of system failures, errors, or disasters.
Virtualization: The operating system provides virtualization capabilities that allow multiple operating systems or applications to run on a single physical machine. This can enable efficient use of resources and flexibility in managing workloads.
Performance Monitoring: The operating system provides tools for monitoring and optimizing system performance, including identifying bottlenecks, optimizing resource usage, and analyzing system logs and metrics.
Time-Sharing: The operating system enables multiple users to share a computer system and its resources simultaneously by providing time-sharing mechanisms that allocate resources fairly and efficiently.
System Calls: The operating system provides a set of system calls that enable applications to interact with the operating system and access its resources. System calls provide a standardized interface between applications and the operating system, enabling portability and compatibility across different hardware and software platforms.
Error-detecting Aids: These contain methods that include the production of dumps, traces, error messages, and other debugging and error-detecting methods.
Objectives of Operating Systems
Convenient to use
User Friendly
Easy Access
Management of Resources
Controls and Monitoring
Fair Sharing of Resources
Types of Operating Systems
Batch Operating System: This type of operating system does not interact with the computer directly. There is an operator that takes similar jobs having the same requirements and groups them into batches. It is the responsibility of the operator to sort jobs with similar needs.
.webp)
Advantages
The following are the advantages of Batch Operating System:
Processors of the batch systems are aware of the time duration of the job even when it is present in the queue.
Batch systems can be shared by multiple users.
There I very less idle time of the batch system.
It enables us to manage the efficiently large load of work.
Disadvantages
The following are the disadvantages of Batch Operating System:
It is very difficult to debug the batch systems
It proves to be costly sometimes
If any job fails, then it is difficult to predict the time
Examples of Batch Operating Systems: Payroll Systems, Bank Statements, etc.
Time-sharing Operating System: Each task is given some time to execute so that all the tasks work smoothly. Each user gets the time of the CPU as they use a single system. These systems are also known as Multitasking Systems. The task can be from a single user or different users also. The time that each task gets to execute is called quantum. After this time interval is over OS switches over to the next task.

Advantages of Time-Sharing OS
The time-sharing operating system has the following advantages:
It provides a quick response
Reduces CPU idle time
All the tasks are given a specific time
Less probability of duplication of software
Improves response time
Easy to use and user friendly
Disadvantages of Time-Sharing OS
Below are some disadvantages of the time-sharing operating system, such as:
It consumes many resources
Requires high specification of hardware
It has a problem of reliability
An issue with the security and integrity of user programs and data
Probability of data communication problem
Examples of Time-Sharing OS with explanation
IBM VM/CMS
TSO (Time Sharing Option)
Windows Terminal Services
Real-time Operating System: Real-time operating systems (RTOS) are used in environments where a large number of events, mostly external to the computer system, must be accepted and processed in a short time or within certain deadlines. such applications are industrial control, telephone switching equipment, flight control, and real-time simulations. With an RTOS, the processing time is measured in tenths of seconds. This system is time-bound and has a fixed deadline. The processing in this type of system must occur within the specified constraints. Otherwise, This will lead to system failure.
Examples of the real-time operating systems: Airline traffic control systems, Command Control Systems, Airlines reservation system, Heart Pacemaker, Network Multimedia Systems, Robot etc.
The real-time operating systems can be of 3 types –
| Feature | Hard RTOS | Soft RTOS | Firm RTOS |
| Deadline guarantees | All deadlines must be met | All deadlines are attempted to be met but some can be missed | Critical deadlines must be met, some non-critical deadlines can be missed |
| Safety and reliability | Critical | Important but not critical | Important but not critical |
| Performance | Not as critical as safety and reliability | Important | Important |
| Typical applications | Aircraft control systems, medical devices, industrial automation systems | Multimedia systems, consumer electronics | Automotive systems, telecommunications systems |
| Hardware requirements | More powerful hardware required | Less powerful hardware required | Less powerful hardware required than hard RTOSs |
| Cost and complexity | More complex and expensive to implement and maintain | Less complex and expensive to implement and maintain than hard RTOSs | Less complex and expensive to implement and maintain than hard RTOSs |
Examples of Operating Systems
Windows (GUI-based, PC)
GNU/Linux (Personal, Workstations, ISP, File, and print server, Three-tier client/Server)
macOS (Macintosh), used for Apple’s personal computers and workstations (MacBook, iMac).
Android (Google’s Operating System for smartphones/tablets/smartwatches)
iOS (Apple’s OS for iPhone, iPad, and iPod Touch)
History Of OS
No OS – (0s to 1940s) –
Before the 1940s, computers didn't have operating systems. Users had to manually type instructions in machine language (0s and 1s), which was incredibly challenging, time-consuming, and not user-friendly. It required a deep understanding of the machine's language and was difficult for most people to implement even simple tasks.
Batch Processing Systems -(1940s to 1950s):
Over time, batch-processing systems emerged. Users could write their programs on punch cards and hand them to computer operators. The operators would then group similar jobs into batches and feed them to the CPU one at a time. The CPU executed the jobs in each batch sequentially, one after the other.
Multiprogramming Systems -(1950s to 1960s) :
The revolution in operating systems started with multiprogramming. It allowed users to load multiple programs into memory, assigning a specific portion of memory to each. When one program was waiting for time-consuming I/O operations, the OS permitted the CPU to switch to another program (first in the ready queue) for continuous execution, using interrupts to manage the transition.
Time-Sharing Systems -(1960s to 1970s)
Time-sharing systems extended the concept of multiprogramming. They introduced an additional feature to prevent any single program from monopolizing the CPU for an extended period. In time-sharing, the operating system would switch from one program to another after a set time interval, ensuring that each program had regular access to the CPU, promoting fairness and efficient utilization of resources.
Introduction of GUI -(1970s to 1980s)
Over time, Graphical User Interfaces (GUIs) emerged, transforming how people interacted with computers. GUIs made operating systems much more user-friendly by introducing visual elements like icons, menus, and windows.
Networked Systems – (1980s to 1990s)
In the 1980s, computer networks gained immense popularity, leading to the need for specialized operating systems to manage network communication. Operating systems like Novell NetWare and Windows NT were developed to facilitate collaborative work environments, simplifying file sharing and enabling remote access for users. This marked a significant advancement in networking capabilities during that era.
Mobile Operating Systems – (Late 1990s to Early 2000s)
The invention of smartphones brought about a major revolution in the software industry. To manage the complex operations of smartphones, specialized operating systems like iOS and Android were developed. Over time, these operating systems underwent continuous optimization and refinement, becoming increasingly powerful and versatile, and they continue to shape the way we use mobile devices today.
AI Integration – (2010s to ongoing)
As time has progressed, the integration of Artificial Intelligence (AI) into operating systems has become a game-changer. Operating systems now incorporate AI features such as Siri, Google Assistant, and Alexa, enhancing their power and efficiency. These AI elements have given rise to entirely new capabilities like voice commands, predictive text, and personalized recommendations, significantly enriching the user experience and expanding the capabilities of modern operating systems.
System protection
System protection is the process of protecting a computer system from unauthorized access, use, disclosure, disruption, modification, or destruction. It is an important part of cybersecurity and is essential for ensuring the confidentiality, integrity, and availability of computer systems and data.
Operating systems play a key role in system protection by providing a variety of security features, such as:
Authentication: Authentication mechanisms verify the identity of users before they are allowed to access the system.
Authorization: Authorization mechanisms determine what resources and programs users are allowed to access.
Access control lists (ACLs): ACLs specify who is allowed to access a particular resource and what operations they are allowed to perform.
Firewalls: Firewalls monitor and control incoming and outgoing network traffic to protect the system from unauthorized access and attacks.
Antivirus software: Antivirus software detects and removes malware from the system.
Operating system structure
An operating system is a complex software system that is typically composed of the following components:
Kernel: The kernel is the core of the operating system and is responsible for managing the system's hardware and software resources. It also provides a set of system calls that application programs can use to interact with the kernel and the underlying hardware.
Process manager: The process manager is responsible for creating, scheduling, and managing processes. A process is a program that is currently executing.
Memory manager: The memory manager is responsible for allocating and managing memory for processes.
File system: The file system is responsible for organizing and managing files on storage devices.
Device manager: The device manager is responsible for managing peripheral devices such as printers, scanners, and network interfaces.
Operating system services
Operating systems provide a variety of services to application programs, including:
Process management: Operating systems provide services for creating, scheduling, and managing processes.
Memory management: Operating systems provide services for allocating and managing memory for processes.
File system: Operating systems provide services for creating, reading, writing, and deleting files.
Device management: Operating systems provide services for controlling and managing peripheral devices.
Networking: Operating systems provide services for connecting to networks and communicating with other devices on the network.
Security: Operating systems provide services for protecting the system from unauthorized access and malicious software.
Conclusion
In summary, the operating system is a fundamental component of computer systems, acting as the intermediary between hardware and software resources. Over time, it has undergone significant evolution, from early manual input methods to the introduction of graphical user interfaces and mobile operating systems. Key functions like resource management, process control, memory management, and security have made computers more efficient and secure.
Operating systems have adapted to networked environments, facilitating collaboration and remote access. The integration of Artificial Intelligence has ushered in features like voice commands and personalized recommendations, enhancing user experiences. System protection mechanisms ensure the security of computer systems.
Looking ahead, operating systems will continue to evolve, keeping pace with emerging technologies and user needs, remaining at the core of our digital experiences.
Subscribe to my newsletter
Read articles from Narottam Choudhary directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Narottam Choudhary
Narottam Choudhary
Not only Just a Coder Having skills in tech field and Also Having a great touch in music And a Music producer