A Comprehensive Guide to JSON Web Tokens
 Dhanush N
Dhanush N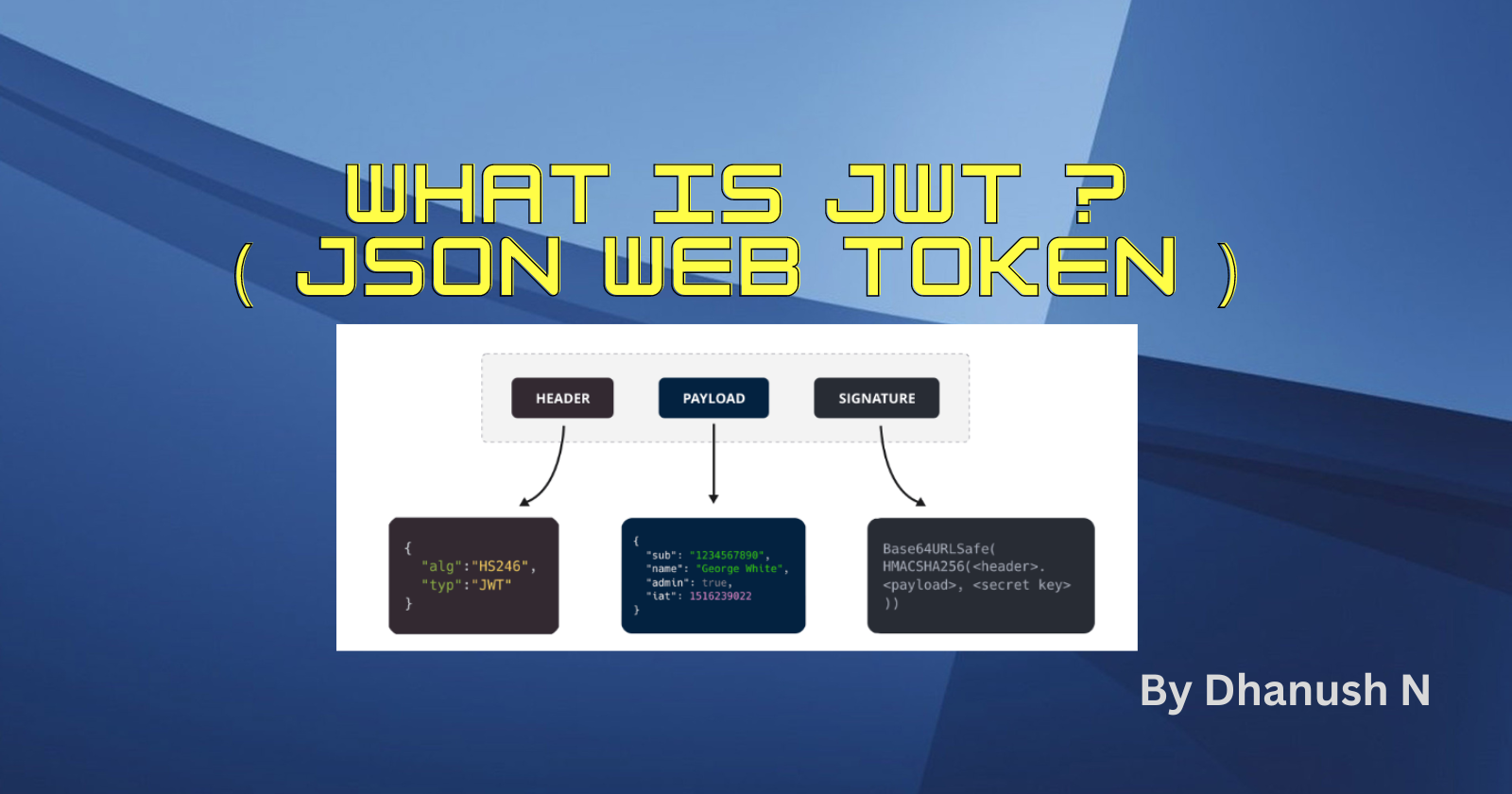
Introduction:
JWT stands for JSON Web Token. JWTs are commonly used for authentication and authorization purposes in modern web applications and APIs.
JWT Parts:
A JWT consists of three parts: a header, a payload, and a signature, which are concatenated and encoded as a single string using Base64URL encoding. Each part contains different types of information
Header: The header typically contains metadata about the type of token and the cryptographic algorithms used for signing or encrypting the token. Common algorithms include HMAC, RSA, or ECDSA.
Payload: The payload, also known as the claims or the body, carries the actual data or claims about the authenticated user or other relevant information. Claims can include standard claims (e.g., issuer, subject, expiration time) and custom claims defined by the application.
Signature: The signature is generated by combining the encoded header, encoded payload and a secret key (public/private key pair) using the specified cryptographic algorithm from the header. The signature allows the recipient of the token to verify its integrity & authenticity
Example 👇
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c
Header: Base64URL encoded header: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9 The header contains information about the cryptographic algorithm used for the signature (in this case, HS256, which is HMAC-SHA256) and the type of the token (JWT).
Payload: Base64URL encoded payload: eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ
Signature: The signature is generated by combining the encoded header, encoded payload, and a secret key using the specified cryptographic algorithm (HS256). The signature ensures the integrity and authenticity of the JWT.
What distinguishes conventional techniques from one another?
In contemporary applications, JWTs are utilized for authentication and authorization for several reasons:
Scalable and stateless: Because JWTs are stateless tokens, servers do not need to maintain session data. As there is no dependency on server-side session management or database lookups, scaling is possible.
Decentralized and Distributed: Since JWTs are self-contained, they can be simply shared across many systems or services. As a result, authentication can be carried out using JWT verification rather than depending on a centralised session stored in flexible and decentralized systems like microservices or APIs.
Cross-Domain and Cross-Platform Compatibility: Because JWTs are built on JSON, they work with a variety of platforms and computer languages. They can be exchanged between systems and domains by being sent as HTTP headers, query parameters, or in the request body.
Fewer Database Lookups: JWTs contain all the information required for session validation or retrieval within the token itself, negating the need for frequent database searches. Decreasing the dependency on database lookups enhances performance.
Granular Authorization and Claims: Fine-grained authorization decisions based on user roles, permissions, or attributes are possible using JWTs' granular authorization and claims features. As a result, further database searches for authorization are no longer necessary.
Security and Integrity: JWTs are digitally signed, guaranteeing the authenticity and security of the token. Trust and security are provided during transmission since the secret key or public key can be used by the recipients to validate the signature.
Conclusion:
While JWTs offer advantages, it's important to consider their suitability for specific use cases. They introduce additional complexity, and proper security measures such as secure key management, token expiration, and revocation mechanisms are essential.
The decision to use JWTs depends on the specific requirements, architecture, and security considerations of an application or system.
Thanks for reading 😃
Connect with me on Twitter, Threads, Instagram, GitHub and subscribe to my YouTube channel ❤️
Subscribe to my newsletter
Read articles from Dhanush N directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Dhanush N
Dhanush N
Experienced Consultant, Full Stack Developer, R&D Engineer who loves to solve puzzles & technology problems by code/